Privacy-Preserving Protocol for Data Stored in the Cloud
HongyiSu Geng Yang DaweiLi
(College of Computer Science,Nanjing
University of Posts and Telecommunication)
Abstract:Data storage is an important application of cloud computing.With a cloud computing platform,the burden of local data storage can be reduced.However,services and applications in a cloud may come from different providers,and creating an efficient protocol to protect privacy is critical.We propose a verification protocol for cloud database entries that protects against untrusted service providers.Based on identity-based encryption(IBE)for cloud storage,this protocol guards against breaches of privacy in cloud storage.It prevents service providers from easily constructing cloud storage and forging the signature of data owners by secret sharing.Simulation results confirm the availability and efficiency of the proposed protocol.
Keyw ords:privacy;cloud storage;IBE;secret sharing
C loud computing is a new service platform.When data is stored in clouds,the owner no longer has physical possession of the data’s storage.But untrusted service providers have independent administrator authority over the data,and this creates potential security threats.Data integrity is also a security challenge in cloud computing[1].Protecting the privacy of data owners has become a new challenge in cloud computing[2].
In this paper,we propose a privacy-preserving protocol with elliptic curve cryptography and secret sharing.In a given scenario,service providers comprise coordinate servers in which sensitive data(entries of cloud databases)are re-computed with k servers(k is a threshold value).Users also verify the shares from k servers on the condition that they(the users)only rely on the trust of data owners’signatures.
1 Related Work
Identity-Based Encryption(IBE)is a key technique for the proposed protocol.A novel IBEon a bilinear map was proposed in[3].However,it failed in a distributed environment and did not prevent collusion between k dishonest service providers.Joonsang Baek[4]constructed the first identity-based threshold decryption,which is secure against chosen-ciphertext attack.
Baek’s scheme is based on the concept of“federal identity,”introduced by Liang Yan[5],and is a new solution to strengthening cloud security.
Brian Thompson[6]leveraged database entries of data owners as shared secrets.Owner identities can be replaced by database entries and used as owners’signatures.This can prevent disclosure of private information from the identity.Cong Wang[2]introduced a third party auditor(TPA)to audit cloud service providers before a user accesses cloud storage services.TPA guarantees that data integrity will be maintained and service providers will behave ethically.
We use database entries as federal identities to verify service providers’data.We also use threshold encryption on a bilinear map to adapt to distributed cloud storage.
2 The Proposed Model and Protocol
2.1 The Proposed Model
The model we propose aims to protect cloud data against untrusted service providers.This model involves data owners,cloud service providers,and data users,as shown in Fig.1.Data owners store data in the cloud and send every share of data entries to k service providers.Cloud service providers collaboratively store data,especially the shares of cloud databases entries.They have the signature of database entries(shadow secret)from data owners.Data users access data from the service providers and have access to the public information of data owners in order to verify the shares received from service providers.

▲Figure 1.The proposed cloud storage model.
2.2 Process of The Proposed Protocol
The proposed protocol is based on IBE[3]and secret sharing[7].The identity in this protocol is replaced by the entry of cloud databases as a secret to be shared.Strings or multimedia data can be converted by hash functions.A data owner outsources the database(such as m shares of the entry for the database)to m service providers and requires that at least any k servers can reconstruct the entry of the database collaboratively.However,k-1 servers cannot.Shadow secrets are also proposed to verify each share of the entry.Furthermore,the data owner and data user can delegate one of m providers as the primary provider SPuin order to reduce the cost of communication.SPugathers other k-1 shares and shadow secrets and sends k shares to users.This solution requires that should be absolutely trustworthy.Finally,the primary provider(delegated by data users)reconstructs the entry of the database and verifies the shares of other k-1 providers with shadow secrets.
The proposed protocol is implemented in four phases:initialization,distribution,verification,and reconstruction.
(1)Initialization
The proposed modeltakes a security parameter h and chooses a big primer p(h bit)in order to find a hypersingular elliptic curve E/GF(p).The following notations are used:
·l is the length of plaintext,and we use hash function to convert entry x into plaintext
·P is the generator of subgroup(G,+)in E/GF(p)
·q(q>2h)is the order of(G,+)
·G and G*are two(multiplicative)cyclic groups of prime order p
·Zq*denotes the group{0;...;q-1}under addition modulo q
·e:is a bilinear map e:G×G→GF(P2)*
·H1,H2are one-way hash functions

First,a master key s is chosen to compute system public key Ppub=sP.Broadcast system parameters{G,q,P,e,H1,H2,Ppub}are also set for data owners,data users,and service providers.
(2)Distribution
The data owner distributes m shares of the entry E of the database to m service providers along with the verification key.Let E be the entry of database,and use IBEto produce plaintext(c,u),where

The process of distributing shares has the following six steps:
Step1:Execute the function Extract from IBE[3]to compute a key pair<QE,
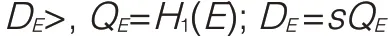
Step2:Randomly choose k coefficients from G*{aj|aj∈G*;j=1,2,…,k-1;ak-1≠0}and compue m shares of De with a polynomial F(x)of order k-1,

Step3:Compute service provider SPi’s shadow secret Si=F(i),then compute yi=e(Si,P),1≤i≤m
Step4:Compute verification key Uj=e

Step5:Send Sito SPiwith a private channel,and broadcast yi,Uj;1≤i≤m,0≤j≤k-1
Step6:Compute Proof for verification key.
After choosing wi∈(G,+),data
owners compute E1i=e(wi,Ppub),E2i==wi-Sicimod q.Owners broadcast PROOFi=(ri,ci),1≤i≤m.
(3)Verification
SPμapplies for other k-1 providers’shadow secrets Siand uses the public information to verify the validity of Siin the following steps:
(a)SPμcollects Ui(0≤i≤k-1),

(b)It verifies E1i=e(ri,Ppub)E2i=eand then H2(E1i+E2i)to compare with cifrom PROOFi=(ri,ci).If the result is equal,Siis proven valid.
(4)Reconstruction
After verification,SPμcollects Sifrom other k-1 service providers.Given the ciphertext<C,U>,SPμuses the following expression to revert to the entry E:

Then following IBE,SPμreduces the entry E:

2.3 Verification of the Proposed Protocol
The proposed protocol is proven correct by calculating Yi,given Ui(0≤i≤k-1).
(1)Verification of the validity of shadow secret Si
The primary provider SPmcollects information set(Ppub,Ui;P,yi;Si)for the verification.
The correctness ofis given below:
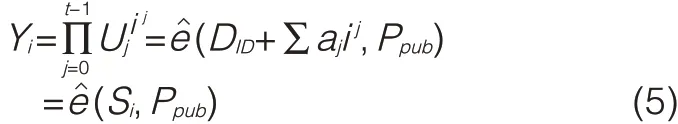
According to Yi,yi,it is easy to prove the correctness of PROOFi=(ri,ci)as follows:

With the computation of ciin PROOFi=(),is equal to ci.PROOFi=(ri,ci)can prove the validity of Si.
(2)Reconstruction of the entry(E)of the database:
After verifying k(threshold value)shadow secrets Si,the primary provider computes a bilinear map with U in the ciphertext and Sj.The correctness is proven as follows:

According to IBE,SPμreverts the entry E=C⊕H2(sum).

▲Figure 2.Comparison on time costof distributing shares.
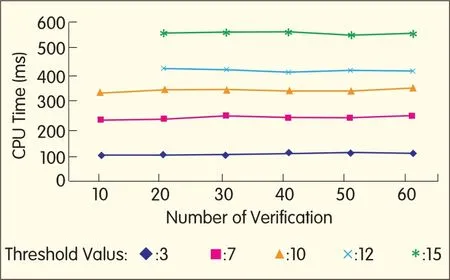
▲Figure 3.Time costof verification.
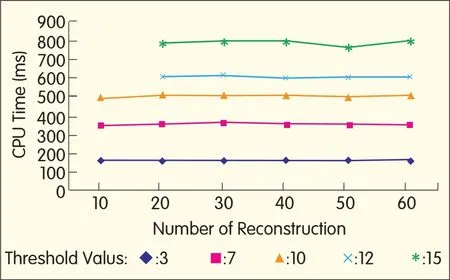
▲Figure 4.Time costof reconstruction.
3 Simulation
The simulation was conducted using C language on a Windows XPsystem running on two 2.0 GHz Intel Core processors each with 2 GB of RAM and a Western Digital 320 GB Serial ATA driver.Multiprecision Integer and Rational Arithmetic C/C++Library(MIRACL)version 5.3 was used.The simulation result is the mean of ten trials.
(1)Cost of Distributing Shares of Secret and Signature by Data Owners
We assess the performance of distributing shares according to two criteria:CPU time and the number of shares distributed.As shown in Fig.2,when the total number of service providers increases(based on different threshold values),the time cost increases.When the threshold value increases,the time cost also increases.So when a data owner distributes shares of database entry and signature,the total number of service providers,as well as the threshold value,needs to be considered.Moreover,in order to guarantee protection against collusion from service providers,the range of the threshold should be considered.A threshold value of half the total number of service providers is a good choice for balancing security and efficiency.
(2)Comparison of the Time Costs of Distribution,Verification,and Reconstruction by Data Users
The time cost of reconstruction and of verification are similar at the same threshold levelregardless of the total number of service providers,as shown in Figs.3 and 4.In the proposed protocol,verification and reconstruction are run by the primary service providers delegated by data users.So the primary service provider can save communication cost by gathering k-1 shares.The figures show that efficiency in verification and reconstruction is greater than that in distribution.
4 Conclusion
In this paper,we propose a privacy-preserving protocol for data storage in the cloud.We focus on stopping data being disclosed by untrusted service providers when data owners distribute their database entries.By using IBEalgorithm and a secret-sharing scheme,the protocol protects against collusion by multiple service providers.The simulations show that regardless of network environment,the proposed protocol is correct and efficient.
- ZTE Communications的其它文章
- RF Technologies and Challenges for Future MBRSystems in Cellular Base Stations
- ZTE Expects Sales Revenues from Enterprise Cloud Computing Products to Exceed$2 billion in 2011
- Broadband Power Amplifiers for Unified Base Stations
- Single Mode DRFilters for Wireless Base Stations
- Design of a Magneto-Electric Dipole Element for Mobile Communication Base Station Antennas
- Advanced Synthesis Techniques for Microwave Filters

