Age of Information for Short-Packet Covert Communication with Time Modulated Retrodirective Array
Ma Yue ,Ma Ruiqian ,Lin Zhi ,Yang Weiwei ,Cai Yueming ,Miao Chen ,Wu Wen
1 Key Laboratory of Near-Range RF Sensing ICs&Microsystems(NJUST),Ministry of Education,School of Electronic and Optical Engineering,Nanjing University of Science and Technology,Nanjing 210094,China
2 College of Electronic Engineering,National University of Defense Technology,Hefei 230037,China
3 College of Communications Engineering,Army Engineering University of PLA,Nanjing 210007,China
Abstract: In this paper,the covert age of information (CAoI),which characterizes the timeliness and covertness performance of communication,is frist investigated in the short-packet covert communication with time modulated retrodirective array (TMRDA).Specifcially,the TMRDA is designed to maximize the antenna gain in the target direction while the side lobe is suffciiently suppressed.On this basis,the covertness constraint and CAoI are derived in closed form.To facilitate the covert transmission design,the transmit power and block-length are jointly optimized to minimize the CAoI,which demonstrates the trade-off between covertness and timelessness.Our results illustrate that there exists an optimal block-length that yields the minimum CAoI,and the presented optimization results can achieve enhanced performance compared with the fxied block-length case.Additionally,we observe that smaller beam pointing error at Bob leads to improvements in CAoI.
Keywords: age of information;covert communication;retrodirective array;time modulation
I.INTRODUCTION
1.1 Background
With the proliferation of wireless devices,ensuring secure communication has become increasingly critical,especially with the emergence of the Internet of Things(IoT)in various domains[1-5].While existing research on wireless communication security primarily focuses on protecting communication content from eavesdropping through encryption[6,7]and physical layer security (PLS) [8-12].However,there are situations where privacy of communication behavior is also important,necessitating the need for covert transmission of private messages.For instance,in scenarios such as military reconnaissance signaling in battlefeilds,private e-health signal transmission in public spaces,and confdiential fniancial data messaging,it is crucial to ensure not only the security of the transmitted information but also the covertness of the transmission behavior itself.
Covert communication has emerged as a prominent communication technology and has attracted substantial research and application interest in recent decades[13].The history of covert communication can be traced back to the Cold War era,and with advancements in technology,it has found expanding applications in various domains including military,security,and the IoT [14].One of the key advantages of covert communication lies in its ability to provide higher levels of security compared to traditional secure communications methods[15].By operating under the surveillance,covert communication offers an additional layer of protection against detection [16].The pioneer work [17] was a groundbreaking study that unveiled the square root limit of covert transmission over an additive white gussian noise (AWGN)channel.After that signifciant progress has been made in the information theory of covert communication,researchers have extensively investigated various aspects of covert communication,including different channel models[14-16],different uncertainty sources[18-20],and multiple networks [21-24].To enhance the performance of covert communications,multiple antenna technology (MAT) [13,25] has been introduced and utilized via exploiting spatial degrees of freedom.However,this introduction also leads to an increased workload for pilot interaction,which may not be adaptable in situations with limited energy and high real-time requirements.The emergence of time modulated reconfgiurable array (TMRDA) [26] can potentially solve this problem.TMRDA enables the incident signal to be returned along its original path,facilitating automatic tracking and reducing the burden of multiple pilot interactions.On the other hand,in situations where delay is critical and energy resources are limited,it is more practical to adopt the short-packet communication [27].Against this background,in this work,we investigate the short-packet covert communication with TMRDA.
1.2 Related Works
A great research effort has been made in the covert communication by considering single antenna.In[28],channel inversion power control is adopted to achieve covert communications in Rayleigh fading wireless networks,where the location of transmitter can possibly be hidden from a warden.In [29],the aim is to enhance the timeliness of data collection subject to a covertness constraint in unmanned aerial vehicle (UAV)-aided IoT networks.In this scenario,a UAV is periodically engaged in wireless power transfer,charging an energy-constrained IoT device.Subsequently,the IoT device opportunistically sends its collected data to the UAV.In [30],the investigation of short-packet covert communication with transmission time uncertainty is conducted.The random subslot selection covert transmission scheme is proposed to ensure a higher level of communication covertness by leveraging the random transmission time.The research of short-packet covert communication in interweave cognitive radio networks is conducted in [31].In this scenario,the occasionally idle spectrum is opportunistically accessed by a secondary transmitter under the supervision of a primary transmitter.
Nevertheless,it is important to acknowledge that single antenna system has room for improvement.It presents certain limitations in terms of diversity,security,capacity,and reliability,which should be taken into consideration when selecting a communication system for covert operations.To further enhance performance of covert communication,MAT has been introduced,offering signifciant beneftis such as considerable channel capacity,and robust reliability.MAT can enhance the received signal-to-noise ratio (SNR)[32] and can also be utilized to improve relay performance [33].In [34],the focus is on studying multiantenna aided covert communications in the presence of randomly located wardens and interferers.Both centralized and distributed antenna systems are taken into account in the investigation.Besides,two relay beamforming schemes in a multi-antenna relay network for enhanced communication covertness were proposed[35].Furthermore,Forouzeshet al.[36]employed MRT at Alice to exploit the null space and employ 3D beamforming,resulting in improved transmission performance.However,the use of MAT in covert communications typically necessitates accurate and perfect channel state information(CSI)[37],which introduce added complexity to the network design.Additionally,existing MAT employed in covert communication often involves multiple pilot interactions during the beam training phase,limiting their applicability in scenarios that prioritize strict delay and limited energy.
Fortunately,TMRDA emerges as a promising technology with distinct advantages [26].In contrast to conventional methods,the transmitter does not require prior knowledge of the intended receivers’ location and does not rely on CSI,thereby facilitating automatic tracking and substantially reducing system complexity.In[38],the retrodirective frequency diversity array was proposed for secure IoT communications,as with TMRDA plays to the strengths of the retrospective formation.The value of TMRDA is particularly advantageous in unique scenarios such as battlefeild IoT,where the TMRDA is distinguished by its ability to automatically track the desired receiver in both range and angle directions.This implies that the transmitter does not need to possess any prior knowledge about the intended receiver’s location,and there is no necessity for CSI estimation at the transmitter.Nevertheless,despite the extensive capabilities offered by TMRDA,a state-of-the-art communication technology,there is still a limited understanding of the tactics and methodologies involved in achieving covert communication through TMRDA.
It is worth mentioning that the block-length is always fniite in the practical scenarios,especially in the above mentioned delay-sensitive and energy-limited applications [39].By considering the covert communication with short-packet,it is more challenge for the warden to perform the correct detection due to the f-i nite observation samples.In [40],researchers examined the covert communication with random transmit power in the regime of fniite block-length.They determined the optimal transmit power and block-length that maximize the average effective covert throughput (AECT).Similarly,in [41],they focused on a covert mmWave communication system and studied the beam training duration,training power,and data transmission power that maximize the effective covert throughput.Furthermore,the authors analyzed the covertness performance with fniite block-length [42],considering both conventional and truncated channel inversion power control schemes to hide the transmitter’s location and communication behavior.In addition,the authors investigated covert communication aided by an intelligent reflecting surface [43],where the transmit power and reflect coeffciient were jointly designed to satisfy the block-length constraint.To quantify the timeliness of information transmission,AoI was defnied and introduced in [44].The AoI is a comprehensive metric that can be employed to quantify the information freshness in status updating systems and applications [45].In [46],the requirement of timeliness performance in covert communications was considered for the frist time.By utilizing artifciial noise generated from a full-duplex receiver,a covertness maximization problem was formulated under the constraint of average AoI to optimize the transmit probability of the information signal.In [47],an energy-effciient transmit probabilitypower control scheme was proposed for covert deviceto-device communication,in which average AoI was derived to characterize the freshness of status information.Recently,the covert information freshness in intelligent reflecting surface-aided communications is investigated in [48],and the block-length was optimized to get the improved covert channel quality.In [27],the optimal transmission design that jointly guarantees communication covertness and timeliness of short-packet communications is investigated.
1.3 Motivation and Contributions
In order to mitigate the overhead of multi-antenna pilot interaction,enable signal auto-tracking transmission,and reduce the complexity of MAT,TMRDA has been attracting increasing attention.The application scenarios of TMRDA involving battlefeild IoT and target auto-tracking,where sensors and transmitters should maintain low complexity.Additionally,short-packet communication is well-suited for sensor data transmission in IoT monitoring system[28],and the use of short-packets increases the warden’s uncertainty of its received signals,thereby further hiding the communication behavior and enhancing the covertness performance.However,there are fewer studies related to the evaluation of AoI performance in short-packet covert communication.It is worth mentioning that the timeliness is also an important aspect evaluating the performance of short-packet communication with TMRDA.Nevertheless,the evaluating framework of AoI in the short-packet covert communication with TMRDA needs to be further established and the influence of various parameters on the timeliness performance is unclear.Besides,the design of the parameters for improving the joint performance of covertness and timeliness needs to be further exploited.These factors motivate this work to reconsider the relationship between the communication covertness and timeliness and redesign the transmission.The innovation of this work can be summarized into three main points:
1) We consider a short-packet covert communication system with TMRDA,where the back-haul is performed after that the transmitter receives the data.In order to guarantee the communication covertness,both the transmissions at the two phases are joint hidden against the detection of the warden.Besides,the TMRDA is optimally designed via the proposed Cuckoo Search (CS) algorithm,and thus the antenna gain to the legitimate node is enhanced while the side lobe level (SLL) is signifciantly suppressed.Moreover,considering the non-ideal conditions during the transmission,the impact of the BPE is also examined.
2) Considering the worst-case scenarios for the covert communication with TMRDA,the stricter covertness constraint is derived based on the Kullback-Leibler(KL)divergence.Then,the analytical expression of covert age of information (CAoI) is derived,as a function of transmit power,block-length,and the antenna number of TMRDA.To facilitate the packet transmission design,the optimization problem of minimizing the CAoI is formulated,of which the transmit power and block-length are optimally determined.Our analysis demonstrates that there exist a non-trial tradeoff between the covertness and timeliness via optimizing the transmit power and block-length.
3)The simulations are presented for obtaining more insights on the design of short-packet covert transmission with TMRDA.First,The results highlight the presence of an optimal block-length that achieves the minimum CAoI.Then,it is shown that the CAoI deteriorates as the beam pointing errors(BPE)of the TMRDA increases.Besides,as Bob’s transmit power increases,both the optimal block-length and the fxied block-length make the CAoI performance degrade,and the optimal block-length outperforms the fxied block-length in the interval,which demonstrates the effectiveness of the presented optimization scheme.Moreover,it is shown that the CAoI can be further enhanced by adopting a larger number of antennas at the TMRDA.
Notations: The main symbols used in this paper are listed in Table 1.

Table 1.List of main symbols.
II.SYSTEM MODEL
In this paper,we investigate a specifci communication scenario depicted in Figure 1,where a two-way covert communication is operated between Alice and Bob.Specifcially,when Bob generates a updated packet containsNbits,Bob covertly transmits it to Alice with a fniite block-length,and then Alice replies to Bob.Meanwhile,the warder Willie collects the signal samples and determines whether there exists the transmission or not.Figure 2 illustrates the frame structure of this communication scheme,which consists of two phases.In the frist phase,Bob sends pilot signal and covert information to Alice,and in the second phase,Alice transmits covert information to Bob.This unique scenario deviates from the conventional setup where Bob is an active participant,instead assuming a passive receiver.Such scenarios are commonly encountered in target tracking and battlefeild command applications,which introduces new models and challenges for covertness constraints and timeliness performance optimization.We assume that the blocklength isN.The wireless channels between nodes experience AWGN.Alice employs a TMRDA withMantennas,while both Bob and Willie are equipped with single-antenna systems.

Figure 1.Covert communication with TMRDA.
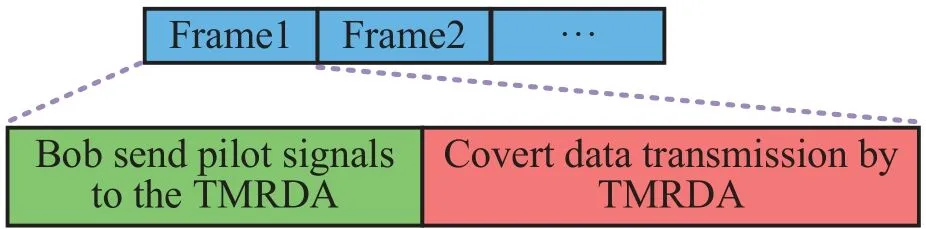
Figure 2.Frame structure of the TMRDA for covert communication.
2.1 The Principle of TMRDA
The structure of a TMRDA withMantennas is illustrated in Figure 3 (a).Each antenna is followed by a 1-bit switch [49] to achieve time modulation.An RF downconversion structure is employed to achieve phase conjugation.The incident signal passes through a downconversion mixer,resulting in an intermediate frequency (IF) signal that has the same frequency as the RF signal but with phase conjugation.This IF signal is then retransmitted through the antennas,thereby enabling retro-directivity.The signal processor serves two purposes in the system: 1) The signal processor controls the switching time of the switches in the TMRDA system.It determines when each switch should be turned on or off to achieve the desired time modulation pattern.By precisely controlling the switching time,the signal processor enables the array to steer the transmitted signal in a specifci direction for retrodirective functionality.2) the signal processor is responsible for processing the received signals.It performs necessary signal processing techniques such as demodulation,flitering,and decoding to extract the information embedded in the received signals.Subsequently,it generates the appropriate response or covert message to be transmitted back to the sender,Alice,in a covert manner.The array factor of a TMRDA withMelement can be expressed as
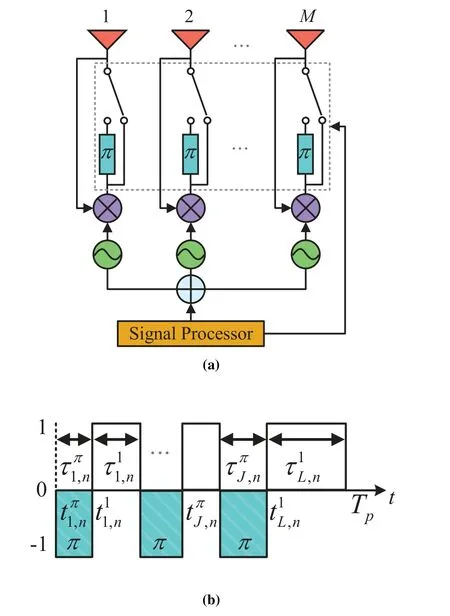
Figure 3.(a)Proposed TMRDA for covert communication;(b)the time switching sequences.
wherekrepresents the wavenumber,f0denotes the primary frequency,θis the incident direction of target in broadside,dis the space of array elements and it is assumed to be half of the wavelength.The time switching scheme in a periodTpis depicted in Figure 3(b),in which state“π”corresponds to a symbol of “-1”.Furthermore,the starting time of each “1”state and its duration arel ∈[1,L],respectively,while the starting time and duration of “-1”state isj ∈[1,J],respectively.Um(t)can be expressed as follows
after the Fourier transform,Um(t)can be denoted as
wherefp=1/Tpis the modulation frequency,am,his the Fourier series coeffciient ofh-th harmonic,which can be expressed as
Then the array factor of the TMRDA can be formulated as follows
By examining (2) to (5),it can be observed that a proper allocation of switching time allows for the design of TMRDA to generate an ideal radiation pattern,and no energy wastage occurs at the RF end.
2.2 Legitimate Transmission
The communication process between Alice and Bob begins with Bob sending a data packet to Alice,followed by Alice sending a response message.When Alice replies to Bob,the received signals at Bob can be expressed as
wherexab[i]denotes the transmit signal form Alice to Bob,nab[i]~CN(0,σ2)represents the AWGN,σ2denotes the noise power,i=1,2,···,Nis the index of the channel use in one block,dabis the distance between Alice and Bob,θer=|θb-θi| is the BPE when signal transmitted form Alice to Bob,Pais the transmit power at Alice,the null hypothesisH0means that no transmission between Alice and Bob,andH1denotes that Alice transmits the signals to Bob.The SNR at Bob can be deduced as
whereA(t)denotes the start time of last valid packet.It is worth mentioning that the AoI monotonously increases over time and is reset to zero only when a packet is successfully received at Bob.The average AoI represents the integrated area under the AoI curve,averaged over time.This metric signifeis the average duration during which Bob can covertly receive and successfully decode a packet.
2.3 Detection Performance at Willie
The signal from Alice to Willie is expressed as
wherexaw[i]denotes the transmit signal form Alice to Bob,andnaw[i]~CN(0,σ2)represents the AWGN,θawis the angle between Alice and Willie,anddawis the distance between Alice and Willie.
When Bob transmits,the received signals at Alice can be written as
wherexba[i]denotes the transmit signal form Bob to Alice,dis the distance between Bob and Willie,Pbis the trbawnsmit power at Bob,naw[i]~CN(0,σ2)denotes the AWGN.
The overall detection error probability can be expressed as follows:
whereρ0denotes the prior probability that Alice does not transmit,ρ1denotes the prior probability that Alice transmits,andρ0+ρ1=1,PFAdenotes the false alarm probability,and PMDdenotes missed detection probability.
This paper considers Willie has complete knowledge of the transmit powerP,block-lengthL,and prior transmission probabilityρ1.This extensive level of information enables Willie to utilize an optimal statistical hypothesis test,such as the likelihood ratio test(LRT),to discriminate between the null and alternative hypotheses.To achieve covert communication,it is necessary to satisfy[17]
According to the Neyman-Pearson criterion,the optimal detection strategy for Willie is the LRT,which can be expressed as follows:
where⊗denotes Kronecker product,IN×Nis unit matrix ofN×N,Srepresents the diagonal matrix and can be expressed as
andUis the column vector that can be written as
The covariance matrix of P0can be expressed as
Then,the KL divergence can be obtained as follows
where tr(·),dim(·),and |·| denotes the trace,determinant,and the dimension of the matrix,respectively.Besides,µ0=0 andµ1=0 are the mean vector of P0and P1.The following theorem outlines the covertness constraint for the TMRDA schemes.
Theorem 1.In the model under consideration,the covertness constraint can be expressed as
Proof.Typically,the received SNR is low in covert communications[51].Therefore,(18)can be rewritten using an inequality ln(1+x)≥x-x2/2,x ≥0,i.e.,
The packet error probability of short-packet covert communication is given as[52]
2.4 Covert Age of Information
In this work,we assume that Alice periodically generates short-packets within a fxied interval,and the interval is set asT=N/W.However,she only opportunistically transmits these packets to maintain the covert nature of her wireless transmission behavior.Consequently,there is a possibility that some realtime packets may not be transmitted in a timely manner.In addition,the covert outage probabilityPcand packet error probabilityδcan result in the reception of invalid packets at Bob.Here,a valid packet refers to one that has been covertly transmitted and successfully decoded.The CAoI is defnied as the duration since the generation of the most recent valid packet at Alice.The average CAoI in an interval (0,τ) can be expressed as
The CAoI measures the freshness of information when a packet is transmitted.As shown in Figure 4,the CAoI for thei-th valid packet can be expressed asbi-ai.Additionally,the time interval between theith andi+1-th packets is defnied as Ξi=bi+1-bi.Moreover,the sojourn time of thei-th packet is given bybi+1-ai.The closed-form solution for the CAoI in this system can be written as

Figure 4.Covert age of information in TMRDA.
whereWdenotes the bandwidth of the system,andProof.Given the presence ofQtime slots between thei-th andi+1-th valid packets,the frist-order moment of Ξiis calculated as follows:
Then,the average arrival rate of valid packet can be written as
Suppose the frist-order moment of interval time ΔTis
Further,the second-order moment of interval time can be deduced as
Utilizing the law of total probability,we can derive the second-order moment of Ξias presented in equation (28).In particular,part (a) of (28) arises from the independence between ΔTmand ΔTl.Additionally,in Figure 4,χirepresents the area of rectangular trapezoids.
By substituting(25) and (29) into(22),we can obtain a closed-form expression for the average CAoI.
It is worth noting that the covertness constraint can also be interpreted asPc ≤ε,wherePcrepresents the covert communication outage probability.This probability denotes the likelihood that the covertness constraint cannot be met.Based on(20),we can derive an upper bound forPc,which is expressed as(30).
III.PROBLEM FORMULATION AND OPTIMIZATION
In this section,we will introduce the optimization of the radiation pattern for TMRDA,as well as the optimization of CAoI.
3.1 Optimization of TMRDA
The ideal array pattern for TMRDA can be achieved by optimizing the switching time based on (5).To ensure that the results meet the desired requirements,optimization objectives are set in algorithms.For this study,the Cuckoo Search(CS)algorithm is chosen due to its superior performance compared to the particle swarm optimization algorithm and its relatively lower complexity[53].The steps of the algorithm is shown in Algorithm 1.It begins with initializing the timeswitching sequences,which undergo adjustments and are inputted into the ftiness function to compute their ftiness values throughout the iterative process.When the number of iterations falls below the designated value ofK,the Le´vy flight mechanism is utilized to explore the solution space while evaluating their ftiness.During this search process,any nest with a lower ftiness level is randomly replaced.As the iterations progress,poor solutions are pruned,and new ones are generated by the algorithm.Finally,the best solution is stored and evaluated.The ftiness function at thei-th step can be expressed as follows:
wherehis the used harmonic for beamforming,ηidenotes system effciiency,andψddenote the optimized and desired SLL,ϕh,iandϕdrepresent the optimized and desired beamwidth,ciis the weighting factor and their sum is 1.

3.2 Optimization of Average CAoI
The block-lengthNplays a crucial role in determining the average CAoI.It is a signifciant factor which influence the packet error probability,delay,and covert outage probability.Therefore,considering the transmit powerPaand prior transmission probabilityρ,the optimization problem for minimizing the average CAoI can be formulated as
According to the Theorem 1,c1can be further rewritten as (33) in next page.Then,we can obtain the following corollaries.
Corollary 1.When a specific N is given,the optimal transmit powerthat maximizes the objective function is existed.
Proof.According to (33),it can be observed that,given a certain value ofPband under the optimalN,a larger value ofPaleads to better average CAoI performance.In this case,a larger value ofPais preferred,and the optimal value can be calculated using the following expression
Corollary 2.As>0,we are able to obtain the following inequation from corollary 1:
Proof.According to (34),the expression inside the root sign must be positive,which can be written as
subsequently(35)proved.
The optimization of equation(32)can be further expressed as:
From(37),it can be inferred that the fnial optimization problem can be tackled using one-dimensional search methods.
IV.SIMULATION RESULTS
4.1 Parameter Setting
In this section,we frist validate the optimization of TMRDA radiation pattern.To ensure CAoI performance of TMRDA within a tolerable BPE range,the parameterϕdis set to 4.2°as an acceptable BPE range[54].Referring to[53],the number of iterations of the CS algorithmKis set as 1000,and the number of antennaMis set as 16.The harmonic index is set ash=0,and the number of host nests in the CS algorithm is set asS=25.The number of time sequences status is set asL=50,and the SLL of optimized beam pattern isψd=-30 dB without prejudice to generality[26].
Based on the performance of TMRDA and in conjunction with relevant reference[17,23],the following parameters are considered for the optimization of the system’s CAoI are set as follows: path attenuation isα=3,the distance between Alice and Bob,Alice and Willie,Bob and Willie aredab=40 m,daw=10 m,anddbw=20 m,respectively.Then the power of noise is set asσ2=-114 dBm,the bandwitdh of system isW=1 MHz,the angle between Alice and Willie isθaw=10°,the minimum and maximum of-length areNmin=100 andNmax=800,respectively.
4.2 TMRDA Pattern Optimization
Figure 5 (a) shows the optimized radiation pattern of TMRDA,where it can be observed that the SLL meets the design requirements,and the beamwidth achieves the desired value.Figure 5 (b) shows the switching time for above array pattern.In the next subsection,we will utilize this radiation pattern as a benchmark to optimize and evaluate the CAoI performance of TMRDA.

Figure 5.(a)Optimized array pattern;(b)The switching sequences in a Tp (yellow means ”1” state,black means”π”state).
4.3 Simulation of Average CAoI
The simulation results in Figure 6 demonstrate that the CAoI initially decreases and then increases with varying values ofN.There exists an optimal value ofNthat leads to the best CAoI performance.Additionally based on Eq.(35),we set different values forPbin our simulations to observe the variations in CAoI.It can be found as the transmit powerPbincreases,the overall CAoI performance gradually deteriorates.
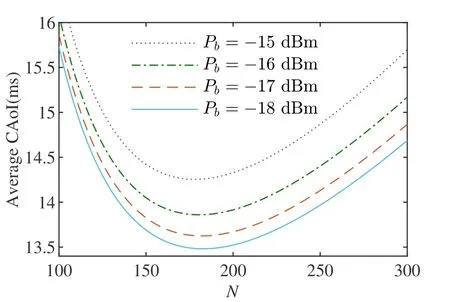
Figure 6.Average CAoI versus N with ρ1=0.5.
The simulation results in Figure 7 illustrate the variation of CAoI performance with respect to BPE for the optimal value ofN.It can be observed that as the BPE increases,the CAoI gradually increases and then sharply escalates.Ideally,the smaller the BPE the smaller the CAoI.In practical scenarios,the BPE is typically less than 3°[54],which satisfeis the minimum requirements for covert communication.

Figure 7.Average CAoI versus BPE with optimal N and Pb=-18 dBm.
Figure 8 shows that asγabincreases,the CAoI gradually improves,indicating that an increase inγabis advantageous for covert communication.Whenγabis less than-14.2 dB,a higher value ofρ1leads to better CAoI performance.On the other hand,whenγabis greater than -12.8 dB,a lower value ofρ1is preferred for improved CAoI performance.Figure 9 gives the change of CAoI versusε,it can be found that the greaterε,the better CAoI.Besides,smallerρ1means better CAoI.
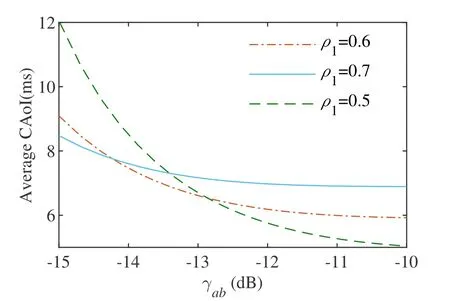
Figure 8.Average CAoI versus γab and Pb=-18 dBm.
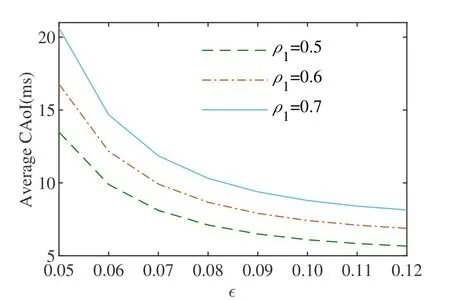
Figure 9.Average CAoI versus ε when Pb=-18 dBm.
We further investigated the impact of the optimal block-length and fxied block-lengths on CAoI performance.As shown in Figure 10,it can be observed that as thePbincreases,the optimal block-length exhibits superior CAoI performance compared to various fxied block-lengths.
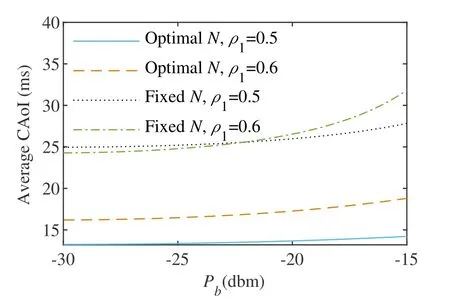
Figure 10.Average CAoI versus Pb with fixed and optimal N.
Lastly,the impact of the number of antennas in TMRDA on CAoI is explored.As the number of antennas increases,different beamforming algorithms exhibit varying effects.To quantitatively evaluate this impact,we select the conventional unidirectional phase center motion(UPCM)[55]as a benchmark for comparison.Additionally,to minimize the influence of side lobe levels,θawis set to 2°.Figure 11 represents the simulation results,demonstrating that with an increasing number of antennasM,the CAoI performance gradually improves.Meanwhile,it is observed that a smaller value ofρ1corresponds to better CAoI performance.However,the impact of differentρ1values on CAoI gradually diminishes asMincreases.
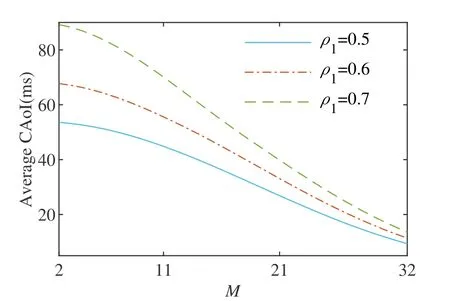
Figure 11.Average CAoI versus M when Pb=-18 dBm.
V.CONCLUSION
In this paper,a novel antenna array,TMRDA,is frist introduced in the short-packet communication to achieve enhanced covertness and timeliness performance.Specifcially,the TMRDA is optimally designed via a CS algorithm to signifciantly suppress the side lobe gain against the warden.Then,the analytical expressions of the covertness constraint and CAoI were derived to characterize the joint performance involving timeliness and covertness.On the basis,the optimal transmit power and block-length were determined to minimize the CAoI.Our results showed that the CAoI with the optimized block-length is smaller than that with a fxied block-length,which demonstrates the effectiveness of the proposed design.Besides,the minimum CAoI deteriorates as the BPE enlarges,and it still can be improved by increasing the number of the antennas at TMRDA.In future work,this study will serve as a foundation for exploring and analyzing the impacts of various channel models on CAoI for short-packet covert communication with TMRDA.Additionally,further investigation will be conducted to explore different time modulation architectures in order to identify potential methods for enhancing covertness performance.
- China Communications的其它文章
- Stochastic Gradient Compression for Federated Learning over Wireless Network
- Joint Task Allocation and Resource Optimization for Blockchain Enabled Collaborative Edge Computing
- The First Verification Test of Space-Ground Collaborative Intelligence via Cloud-Native Satellites
- Distributed Application Addressing in 6G Network
- Integrated Clustering and Routing Design and Triangle Path Optimization for UAV-Assisted Wireless Sensor Networks
- Actor-Critic-Based UAV-Assisted Data Collection in the Wireless Sensor Network

