A survey on joint-operation application for unmanned swarm formations under a complex confrontation environment
ZHANG Jialong, HAN Kun, ZHANG Pu, HOU Zhongxi, and YE Lei,*
1.Unit 63768 of the PLA, Xi’an 710200, China; 2.School of Automation, Northwestern Polytechnical University, Xi’an 710072,China; 3.Test and Training Base, National University of Defense Technology, Xi’an 710100, China; 4.School of Automation and Information Engineering, Xi’an University of Technology, Xi’an 710048, China
Abstract: With the rapid development of informatization, autonomy and intelligence, unmanned swarm formation intelligent operations will become the main combat mode of future wars.Typical unmanned swarm formations such as ground-based directed energy weapon formations, space-based kinetic energy weapon formations, and sea-based carrier-based formations have become the trump card for winning future wars.In a complex confrontation environment, these sophisticated weapon formation systems can precisely strike mobile threat group targets,making them extreme deterrents in joint combat applications.Based on this, first, this paper provides a comprehensive summary of the outstanding advantages, strategic position and combat style of unmanned clusters in joint warfare to highlight their important position in future warfare.Second, a detailed analysis of the technological breakthroughs in four key areas, situational awareness, heterogeneous coordination, mixed combat, and intelligent assessment of typical unmanned aerial vehicle (UAV)swarms in joint warfare, is presented.An in-depth analysis of the UAV swarm communication networking operating mechanism during joint warfare is provided to lay the theoretical foundation for subsequent cooperative tracking and control.Then, an indepth analysis of the shut-in technology requirements of UAV clusters in joint warfare is provided to lay a theoretical foundation for subsequent cooperative tracking control.Finally, the technical requirements of UAV clusters in joint warfare are analysed in depth so the key technologies can form a closed-loop kill chain system and provide theoretical references for the study of intelligent command operations.
Keywords: unmanned swarm, operation style, weapon formation system, mobile group target, joint operation.
1.Introduction
With the rapid development of computer, unmanned system formations not only enable multiple unmanned aerial vehicles to identify, monitor, track and strike targets but also to perform tasks such as surveying, patrolling, and search and rescue with no dead ends and zero casualties,under all-around and all-weather conditions.Based on this, unmanned system formations have broad application prospects in both civilian and military fields and are also a hotspot and difficulty in existing research.Meanwhile, they are also a major national strategic need.In particular, in the military field, with their unique advantages, a large number of high-precision weapons and equipment have emerged in the arms race of various countries, becoming sharp weapons for solid border garrisons.In documents such as the “Comprehensive Roadmap for Unmanned Systems for Fiscal Years 2017 to 2042” and the “U.S.Artificial Intelligence Plan: The First Annual Report”, the U.S.military detailed the development status and development plan for artificial intelligence and will promote the development of artificial intelligence to the national strategic level [1].For intelligent warfare, the U.S.Defense Advanced Research Projects Agency (DARPA) proposed the concept of a“mosaic station”, which aims to create an adaptive “kill net” composed of different combat functional units based on advanced computer technologies and network technologies.Moreover, the U.S.Air Force took the lead in writing “Joint All-Domain Operations” into its doctrine in March 2020 to explore how the Air Force can play a role in Joint All-Domain Operations.
With the development of artificial intelligence technologies represented by machine learning and autonomous operations and the vigorous promotion and application of UAV swarm projects, UAV swarm operations have an increasing impact on future battlefield offense and defence, and they have become the current air defence operation.Therefore, increasingly significant realistic threats and difficult problems urgently need to be solved [2].In addition, UAV swarm operations rely on decentralized and distributed organizational methods to form unique combat advantages that a single combat platform does not have, such as economic advantages, quantitative advantages, coordination and intelligence advantages, and speed advantages, making UAV swarm operations one of the most promising combat styles for future intelligent warfare [3].
Unmanned system formations, with their advantages of a large combat radius, long cruising distance, outstanding combat effect, and strong penetration and strike capability, are widely used in cyber warfare in complex confrontation battlefield environments.Their typical behaviours include collaborative detection, detection and early warning, offensive and defensive assault and strategic support.Unmanned systems can achieve local and global optimal performance through a coupling mechanism among units [4].Then, the realization and completion of a single unmanned system function plays a decisive role in the performance of the entire formation system.
The fault-tolerant control of an unmanned system is particularly important.Through the adjustment of controller parameters, a faulty system can maintain satisfactory performance or at least achieve acceptable performance indicators.After more than 30 years of development, many achievements have emerged in this field[5–8].Among them, online fault-tolerant control strategy application is more effective [9–12].In joint operations,unmanned swarm formation change control and cooperative obstacle avoidance control are two key factors in winning a war, as discussed in the following:
(i) Formation change control.UAV swarm formation reconfiguration, formation change and formation keeping play a pivotal role in reconnaissance and tracking tasks.Many experts and scholars in related fields conducted indepth research on UAV formation control problems from theory to experiment [13].In [14–17], optimal control methods, graph theory methods, guiding vector methods,and artificial potential field methods were used to solve the formation control problem.In [18], a new objective function was designed based on an optimal control trajectory planning algorithm for combinatorial optimization so that the UAV search process can reach the global optimum.In [19], the author conducted research on formation keeping and formation reconfiguration, designed a distributed feedback controller, and used a virtual simulation platform to simulate and verify the effectiveness of the designed controller [13].In [20], the author proposed a short-range formation maintenance strategy for robots based on a leader-following formation control method combined with the principle of successive substitutions in the same row and the inwards retraction of the last row in an army’s rapid march.In [21], considering the limited ability of UAV formation perception and the insufficiency of formation control methods, a rule-based formation control method was proposed to solve the UAV formation control problem.In [22], the author designed a distributed feedback optimization controller for UAV formation shape keeping and formation reconstruction problems and performed flight control simulations for triangular and linear formation acceleration and turning scenarios.The effectiveness of the designed controller is proven using a Lyapunov function method.Stipanovic et al.[23] designed a feedback controller for each UAV and adopted a distributed overlapping control technique to transform a dispersed UAV formation into the desired formation.At the same time, Xu et al.[24] used a model prediction method to solve the formation control problem, and the basic idea was to use a rolling optimization algorithm [13].In [25], an adaptive hierarchical formation shape control method was proposed for an uncertain nonuniform nonlinear agent model described by Eulerian-Lagrange (EL) dynamics [13].In the same period, Wu et al.[26] used a rolling-time domain control method to study complex UAV formation control.Wang et al.[27]proposed a multi-UAV formation control method based on a hierarchical mechanism and a model predictive control method.A backstepping control method was first proposed by Cheng [28] and was used to solve nonlinear formation model control problems.Qu et al.[29,30]applied the leader-following control strategy to UAV formation control to solve the problem of multiaircraft formation control.In [31], to solve the problem of a fighter formation reaching the target point after avoiding obstacles while manoeuvering in a simulated battlefield environment, combined with an idea based on a behaviour method, the leader-following algorithm was improved,and the fighter group was controlled.An R&D team at West Virginia University [32] proposed a virtual leader method.They regard a UAV as a rigid body, and each UAV maintains a predetermined formation and tracks a fixed point.Brad et al.[33] adopted a behaviourbased control method and proposed the concept of the formation geometric centre.In [34], to address the problem of formation preservation during multi-UAV formation flight, the author proposed a leader-following consensus control protocol with a second-order nonlinear switching topology to achieve cooperative formation flight [13].
(ii) Collaborative obstacle avoidance control.UAV swarm formation, coordinated flight, target tracking, and coordinated strike all need to satisfy the requirement that the relative distance between any two UAVs and between a UAV and obstacle is greater than or equal to a safe distance to ensure the safety of the swarm’s real-time formation change according to the battlefield situation, and ensure the stability of the swarm’s flight formation.For UAV swarm operations, security is a key factor to be considered first, and obstacle avoidance research is particularly important.In recent years, many control algorithms were proposed for the obstacle avoidance problem of multi-UAV formation flight, and good control results were achieved.Control obstacle avoidance algorithms are roughly divided into two categories: rule-based methods and optimization-based methods.Rule-based methods are based on an artificial potential field [35,36].Artificial potential field methods are not only applied to UAV obstacle avoidance but also extended to adaptive robot navigation.The basic principle is that an artificial potential field force moves along the negative gradient direction in a specific compound field.Based on this principle,an artificial potential field obstacle avoidance method was proposed and applied to UAV formation control.Optimization-based approaches use model predictive control (MPC) [37].The main formation control algorithm applies consensus theory to design a control law.Cooperative formation control based on a consensus algorithm is a distributed control method that has the advantage of network structure flexibility [38–41] and realizes multichannel composite control and obstacle avoidance.A consensus algorithm is often used to solve the cooperative control problem of multiagent systems [41–44],which greatly simplifies the problem.For example, a multi-UAV system dynamics model can be simplified to a fourth-order system in the horizontal plane and a secondorder system in the vertical direction [45,46].In practical engineering, many researchers are committed to applying an algorithm to actual UAV formations.For example,Olfati-sabere et al.considered the obstacle avoidance problem in three-dimensional space, proposed a geometric obstacle avoidance cone method, and designed a guidance control law [47].Olfati-sabere et al.used a single sensor in a UAV formation and proposed a visualbased obstacle avoidance system [47].Wei et al.proposed a feasibility study of a self-alarm obstacle avoidance control system based on an obstacle avoidance control algorithm and applied it to a UAV formation [48].Ren proposed a fully automatic multisensor self-obstacle avoidance system that uses geometric obstacle avoidance methods to detect and avoid obstacles, enabling UAVs to generate feasible trajectories in real time [49].The proportion of unmanned systems in future military conflicts will continue to increase.Compared with past wars, the reduction in human participation will be enabled by a large number of unmanned combat platforms.These unmanned systems include unmanned ground stations, airbased platforms, space-based platforms, and sea-based platforms, which have multidomain operation, interoperability and intelligence capabilities.Intelligent unmanned systems must be able to operate in an unmanned swarm cooperative mode, such as the optionally manned combat vehicle (MCV) developed by General Dynamics Ground Systems for the U.S.Army Futures Command and Aerovironment in partnership with Kratos to introduce the spring knife by loading UAVs/cruise missiles into UTAP-22 UAVs to penetrate hundreds of miles behind enemy lines and release Switchblade UAVs to destroy enemy air defence systems or ground troops.Reusable vehicles refer to multipurpose reusable vehicles that can quickly pass through the atmosphere and freely travel between the Earth’s surface and space [50].Under the background of a future great power competition strategy,the U.S.Army must strive to develop disruptive technologies that can “change the rules of the game”, explore new combat styles, continuously develop unmanned ground intelligent combat systems, and improve the ability to deter adversaries and intervene in regional conflicts [51].UAV swarms have strong adaptability and robustness through close cooperation among multiple members and have extremely broad application prospects in both civilian and military fields [52,53].With the gradual improvement of UAV performance, it is possible for a single UAV to perform multiple tasks [54].Additionally, the latest progress and development trend in the research field are as follows:
(i) “Borg in the Sky is one of the U.S.Air Force Research Laboratory’s (AFRL) AI software systems programs” designed to use AI technology in modular UAVs with rapid updates, expendability, autonomy and open architecture.The software system ranges from simple algorithms to flight and control in airspace to more complex AI algorithms that can perform certain tasks, and will be equipped to work with a variety of unmanned aircraft in the future, in concert with other manned fighters,bombers, etc.
(ii) The U.S.AFRL awarded Kratos and General Atomics a $17.7 million contract for the Off-Boarding Sensing Station (OBSS) to develop a loyal wingman-style UAV.The UAS could extend the sensing range of manned fighters and carry additional weapons as forward shooters for manned aircraft.The program is looking for an open architecture system to achieve rapid fielding and low acquisition costs, and the OBSS program will serve as a second demonstration experiment in the expendable vehicle development product line concept.
Remark 1 In this paper, the complex confrontation environment refers to the information confrontation in the electromagnetic environment, that is, the presence of all radio waves in a particular spatial and temporal range in the frequency, power electromagnetic field strength into a dense distribution and frequency use, frequency of hostile interference with the nearby frequency intensive high use of high power interference and spectrum allocation use of the formation of the system of electromagnetic power confrontation.
Additionally, the main contributions of the paper are as follows:
(i) For air and space intelligent unmanned system combat research, combat needs as the traction, applicationoriented, the real sense from the test site to the battlefield,from the battlefield feedback test site, practical from the depth of integration of science and technology to carry out unmanned systems in the complex confrontation environment of joint combat application research.
(ii) By analyzing the application analysis of UAV swarms in joint warfare, the key technologies are made to form a closed-loop kill chain system to provide theoretical reference for the study of intelligent command operations.At the same time, it provides theoretical guidance for anti-UAV swarm operations.
2.Key technical fields
With the deep integration of military and civilian and science technology, as well as a country’s promulgation of policies and regulations to vigorously develop an unmanned system industry, the combat effectiveness of unmanned system equipment and long-range joint strikes are significantly improved.Unmanned swarm control technology is particularly important, such as situational awareness technology, data fusion technology, data link transmission technology, intelligent control technology and coordinated strike mode, and effectiveness evaluation methods.Additionally, In the application of unmanned cluster formation warfare, UAV swarm system will face five main problems, as follows: (i) How to quickly reconstruct preset formation in case of failure of one or more UAVs in unmanned swarm; (ii) How to design the control law of collision between drones or incoming targets during high-speed and close-range flight; (iii) How to solve the problem of insufficient robustness of UAV cluster formation with limited time under weak communication; (iv) In the case of multisource disturbance, how to realize the communication delay brought by large-scale information transmission and enhance the anti-interference ability of UAV swarm;(v) How to achieve real-time communication interaction in the process of UAV swarm cooperative flight to ensure safety and stability.However, breakthroughs in these key technologies have the potential to completely change the war situation and protect national and territorial security.Unmanned swarms searching for enemy submarines and targeting incoming threats can spread over large areas to identify and neutralize enemy air-to-surface missiles and other air defences.Although unmanned swarm cooperative system operations represent a cutting-edge technology and a major technological advancement, unlocking the full potential requires technological breakthroughs in four key areas: air and space situational awareness, heterogeneous collaboration, mixed combat, and intelligent assessment, as shown in Fig.1.
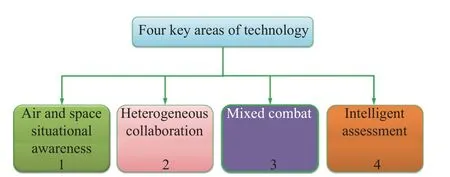
Fig.1 Technology classification of key unmanned swarm system areas
2.1 Air and space situational awareness
The space situational awareness architecture includes a security data collection layer, a security log storage layer,a computing layer, and a presentation layer.The security data collection layer collects security logs and traffic from the original logs and traffic of security devices.The secure data storage layer uses hadhop distributed file system (HDFS) technology to store previously collected data[55].The computing layer mines and analyses the stored data, among which a large number of algorithms emerge,such as deep learning algorithms, unsupervised learning algorithms, clustering algorithms, and other traceability attack chains.Air and space combat situational awareness includes network security situational awareness,communication networking situational awareness and combat situational awareness, among which the communication networking situational awareness of unmanned systems is particularly important.The situational awareness is passed to the processor for analysis, and then instructions are transmitted to actuators to complete the corresponding activities.The primary objects are groundbased resources, space-based platforms and satellites.That is, “uplink”, “downlink”, and “interactive link”.The timely and accurate acquisition of this information requires corresponding algorithms as support, and the execution of these algorithms requires fusion and training through a large amount of original data.For research on air and space situational awareness, the two most important factors are the accurate acquisition of a perception model and the accurate description of interference factors.In particular, the accurate acquisition of a perception model is the key to controlling a spacecraft to achieve preset performance.Based on security situation assessment technology and situation prediction technology, air and space situational awareness modelling is carried out, as shown below [56].
2.1.1 Security situational awareness assessment method
The nature of an object is classified based on the difference from the perceived situation of the other party.To facilitate subsequent calculation, it can be quantified and divided into quantitative index normalization.There are two commonly used methods, namely, (i) after the data processing is normalized, the value is in the interval (0,1);and (ii) dimensional transformation is carried out without dimension.The specific method is as follows:(i) For a small sample size
wherexrepresents the value before conversion,yrepresents the value after conversion,x¯minrepresents the maximum value of the sample, andx¯maxrepresents the minimum value of the sample.
(ii) For a larger sample size
A logarithmic transformation or inverse cotangent transformation is used:y=lgxory=Ptanx, wherePis the weighting fautor.
(iii) For multiobjective mission situational assessment scenarios
UAV swarms utilize the distribution scheme with the maximum benefit at the minimum cost.A schematic diagram of task distribution is shown in Fig.2.

Fig.2 Schematic diagram of cluster combat task assignment
An unmanned swarm takes off from a designated location and arrives at a predetermined combat area to release UAVs to carry out the coordinated operation.During UAV swarm reconnaissance and tracking, tasks are assigned to multiple UAVs, and the UAV assignment results are reflected in two evaluation indicators: the total flight range of all UAVs and the amount of time required to complete reconnaissance and tracking.For the first indicator, the total flight range of each UAV is as follows:
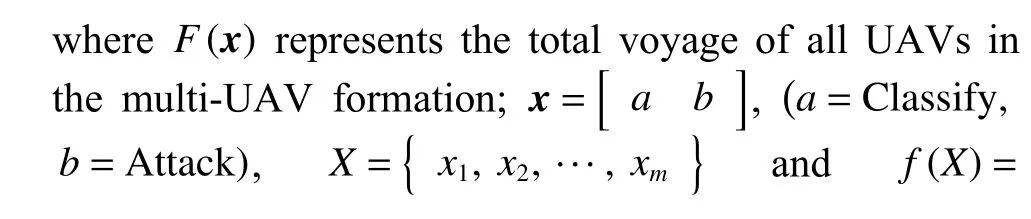
Remark 2 Task assignment in unmanned swarm operations is particularly important in the situational awareness process.Two factors are considered to measure it, namely the total range flown by the unmanned system and the total time to detect the target.When both metrics are minimized, it is a good indication that the solution for this division is optimal and can achieve the maximum efficiency ratio.
2.1.2 Aerospace situation prediction technology
In a complex combat environment, unmanned swarms can predict the situation of the next link through an intelligent algorithm during a fierce confrontation process,which is extremely beneficial to the operation.In situation prediction research, the description of confrontation prediction is transformed into a nonlinear unknown model, its nonlinear term is approximated, and an effective prediction model can be obtained.Existing classic control strategies are network security situation control based on a neural network and optimal control methods based on a double feedback Elman neural network [56].
(i) The nonlinear term in the model can be processed by the typical approximation of a data local regression network, which is a feedforward neural network, and its model is expressed as follows:
wherexCrepresentsthe subsequent layer,arepresents thefeedbackgaincoefficient,x(k)representsthe hidden layer,y(k) represents the output of the output layer,WI1represents theconnection weight matrixbetween thesubsequent la yerand thehiddenlayer,WI2represents the connection weight matrix between the input layer and the hidden layer, andWI3represents the connection weight matrix between the hidden layer and the output layer.
(ii) Optimal control method with a double feedback Elman neural network.Since traditional neural network models are usually based on a gradient descent method,transmission layer error accumulation occurs, which reduces the learning efficiency and eventually leads to the system being in a local minimum state.Therefore, to overcome this shortcoming, a double feedback Elman neural network model is introduced, the subsequent layer unit, output layer feedback and input layer unit are used as the hidden layer input, and a feedback function is added to the input layer node, which effectively reduces and modifies the error generated by the output.Accelerating the learning speed to a certain extent is beneficial to the ability of a neural network to process information,improve efficiency, and help optimize control, thereby providing an accurate basis for the acquisition of a situational awareness model.Therefore, the accuracy of a spatial situational awareness model plays a crucial role in the manipulation, processing and decision-making in a war situation.Meanwhile, as a key space-based asset, satellites face dual network and space security threats, and developing a country’s space strategy faces severe challenges [57].Therefore, research on space situational awareness technology will not only make full use of and protect space resources but also be used for space offensive and defensive applications and better serve national defence modernization.The cyberwarfare flowchart is shown in Fig.3.
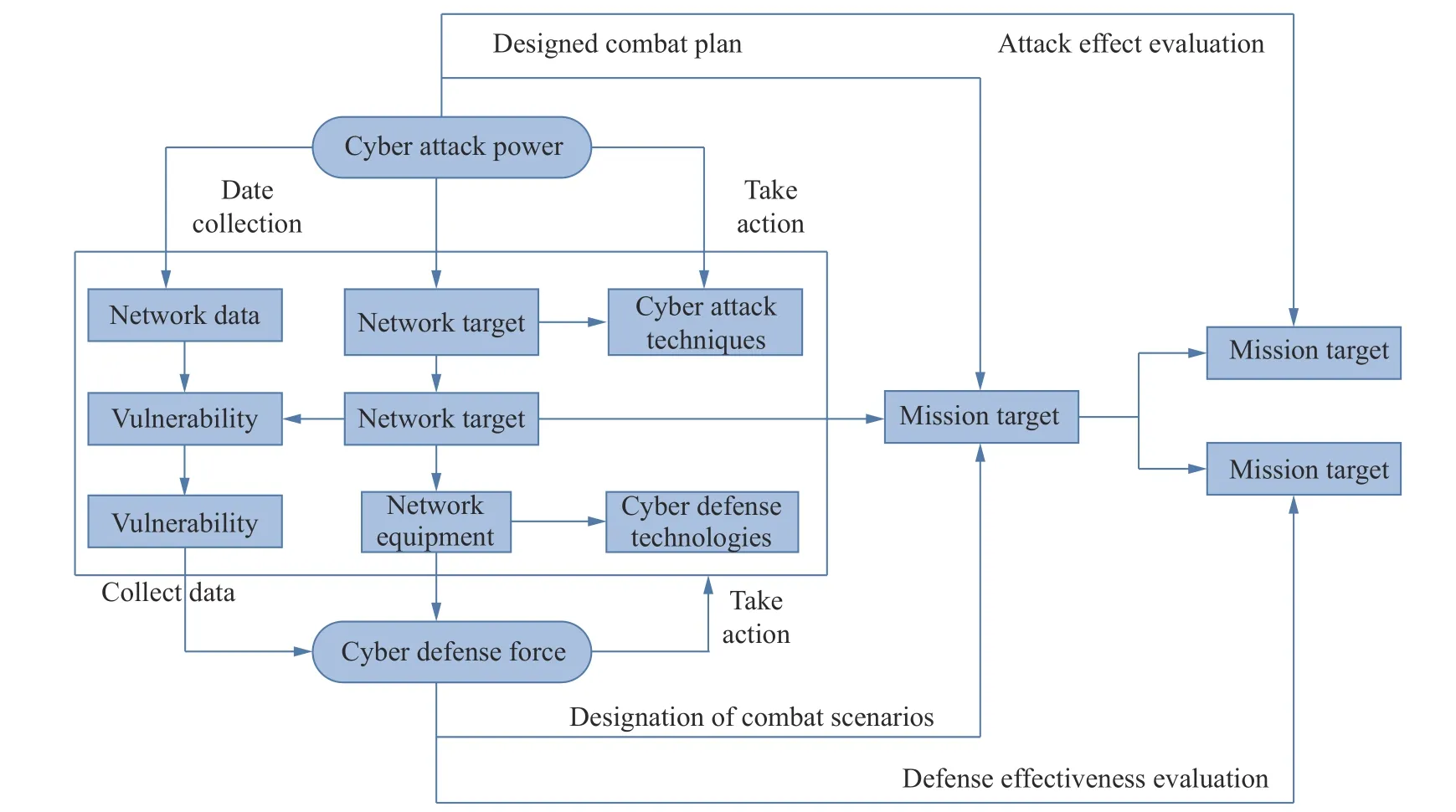
Fig.3 Cyberwarfare flowchart
2.2 Heterogeneous collaboration
For unmanned system formations, the controller design consists of three parts, including a system model, controller design, and stability analysis.These are discussed in the following.
(i) System model
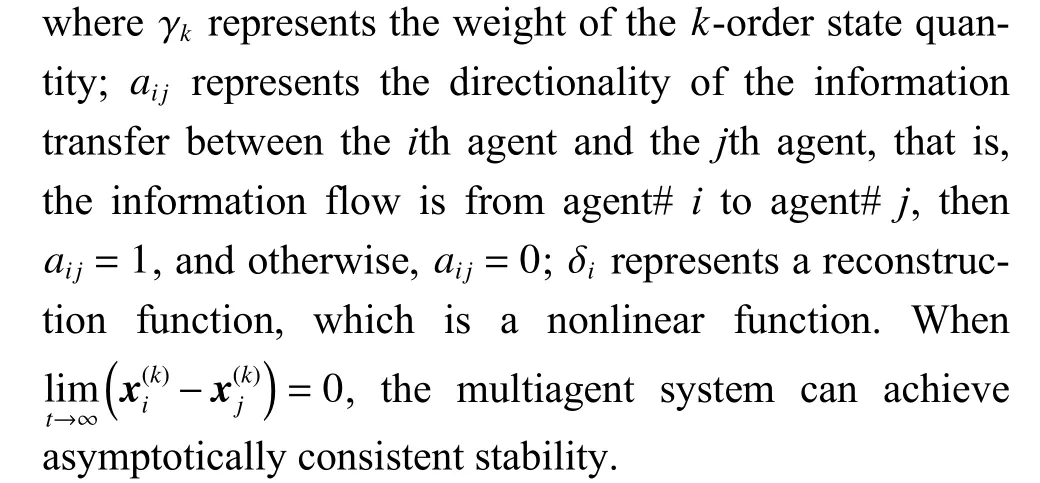
For a high-order system withNagents, cooperative consensus specifies that after timet, the states of any two agents are basically consistent, and the purpose of consensus and stability can be achieved.The model of an unmanned formation system [58] is expressed as follows:

(ii) Control design
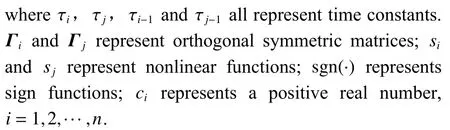
Based on the backstepping technique and related theories, combined with Young’s inequality, the final update law and control law can be obtained, as follows:
(iii) Stability analysis
To verify the effectiveness of the designed controller, a Lyapunov function is constructed, as follows:
Taking the derivative of (10) yields
Combining (8) to (11), we can obtain
Therefore, the designed controller achieves stable states for hypersonic vehicles in complex environments.The proof is complete and the unmanned swarm system controller design is obtained.
Heterogeneous collaborative unmanned swarms can play their respective advantages in complex confrontation environments and greatly improve combat efficiency.Typical heterogeneous collaborative objects are as follows:
(i) Air-to-ground coordination.The main object is the collaboration between UAVs/manned vehicles and ground vehicles (robots), manned aircraft/UAVs and tank groups.The process is that when an incoming target is found, a three-light pod (infrared, visible light,and laser) on a manned aerial vehicle or an UAV finds and identifies the target and transmits the characteristic information of the target back to a ground station, and the ground station responds to the target.The feature information is fused, and the processed target data are fused and sent to a tank.The tank corrects its aiming accuracy according to the target position and attitude data to achieve the expected strike state.Environmental influence, such as the signal to noise ratio, the interference to signal ratio and the vibration of the tank,will produce considerable external interference.An unmanned swarm combat system ground station is shown in Fig.4.

Fig.4 Unmanned swarm combat system ground station
(ii) Air-to-ground coordination.The main object is coordination between UAVs/manned vehicles and longrange launch vehicles, that is, a UAV guides a longrange rocket to attack a mobile group or time-sensitive target, that is, cross-domain and heterogeneous cooperative operations.The key technologies include UAVs/manned aerial vehicles, remote fire, UAV ground stations, command vehicles and targets forming heterogeneous intelligent bodies and a space communication network, and its adaptability, smooth communication and coordination are particularly important.In terms of combat complexity, with an increasing number of UAV sorties, the number of distant fires, the number of UAV ground stations, and the number of command vehicles and targets, it is difficult to identify, track, and target with internal and external disturbances.Meanwhile, the communication link load will also increase so that the accuracy of the weapon load and the platform’s coordinated attack on time-sensitive targets will be reduced.Therefore, multiunit coordination, multiequipment adaptation,and multiperson coordination involve complex systems engineering.The complete process is as follows: i) Formulate a verification and demonstration plan, conduct expert review, and determine the plan after repeated demonstration.ii) In the airspace that has been applied for, plan the UAV flight path, and set its data on the ground station.iii) Load the booster rocket on the UAV,carry it to the designated position, and adjust the throttle to maximize the speed of the UAV’s engine.iv) At a given time, the booster rocket is launched, and the booster has no effect.The manned machine flies into the air, and then the rocket shell falls off.v) The command and control function at the UAV ground station flies according to the designated path plan and at the same time monitors the flight status in real time and controls it in real time.vi) The UAV flies to the designated area,turns on the three-light pod illumination to identify the real target, locates the aiming point, and transmits its position information and speed information back to the ground station.vii) The ground station transmits the information to the long-range launch vehicle and command vehicle, and the commander makes a decision to hit the target.The above is the process of a single drone hitting a target, and multiple UAVs add corresponding processes and communication support equipment.
(iii) Ground-to-ground coordination.The main objects are the coordination of tanks and reconnaissance robots and the coordination of reconnaissance robots and combat team members.The process is that a reconnaissance robot detects a threat target in front.When encountering a threat target or an incoming target, the robot’s vision sensor detects the threat target or attacks the target, extracts the target data, and transmits the data to the combat team members.The combat team members adjust their paths and speeds, adjust the barrel and aiming point, and then wait for the instructions of a superior.If approved by the superior, the combat team will send rockets, strike the target or intercept the incoming target.Then, the robot will destroy the target and take pictures for data analysis, subsequent strike effect evaluation, and the implementation of the next plan.A diagram of the cooperative operation of heterogeneous agent weapon systems is shown in Fig.5.
2.3 Mixed operations
In recent years, unmanned swarm operations moved from the test site to the battlefield due to their unique advantages.Typical examples of attacks by swarms of UAVs in Russia and Syria and attacks by swarms of UAVs on Saudi oil fields fully reflect swarms of UAVs.The absolute advantage of UAV swarms also significantly demonstrates the diversification and efficiency of UAV swarms in coordinated combat.At present, unmanned swarm formation systems are rarely used in coordinated joint operations and are only used in certain specific fields, such as coordinated reconnaissance and detection of enemy targets.In a complex electronic countermeasure environment, when conventional unmanned swarms attack a target, various sensors and communication links on board will be interfered with so that a node or multiple nodes of the entire unmanned swarm communication network will be attacked, forcing the function of the entire system to change temporarily or permanently, and the fighting effect will not be good.Therefore, unmanned swarms and mixed operations with manned vehicles can give full play to their respective advantages and achieve complementary advantages.That is, manned and unmanned swarms moving to a designated combat area, and commanders and fighters comprehensively evaluating the situation level through their own situational awareness and comprehensive situational awareness display and then taking corresponding measures.For example, in a complex and changeable battlefield environment, to avoid the detection of manned aircraft by enemy radars, the characteristics of forwards manoeuvring group targets or time-sensitive targets are identified by multiple UAVs, and the characteristic target information is fused and transmitted to manned aircraft.The commander and fighter send the target status and position information to a ground station,and the unmanned system ground station charges the personnel and sends the corresponding instructions so that the commander and fighter can control the unmanned system and complete the corresponding instruction.UAV combat is a key research project of the U.S.military in response to high-end wars and maintaining air combat superiority.In addition, the U.S.has successively proposed combat application styles such as loyal wingman,distributed combat systems, coordinated autonomous aerial combat with manned aerial vehicles/UAV, collaborative combat modes in denied environments, swarm operations that can be quickly deployed and recovered,and offensive swarm cities [59].Therefore, mixed operation can not only make full use of an unmanned system to detect and provide target information updates in advance but also provide real-time feedback to manned aircraft.In addition, based on an unmanned system and manmachine coordination, the combat time is shortened, the firepower strike effectiveness of the entire operation is effectively improved, and true “1+1>2” is realized.If anti-UAV weapons, including anti-UAV missiles and electronic jamming, are installed on a UAV, the unmanned swarm system will become a powerful weapon for an anti-UAV system [60].In view of this swarm combat mode, integrating existing intelligent obstacle avoidance algorithms is one way to solve multi-UAV swarm combat.

Fig.5 Diagram of the cooperative operation of heterogeneous agents
In March of the same year, the United States developed a new generation of stealth bombers and the X-47B for manned/unmanned aerial operations.The bomber was delivered in July 2020.This further integrates advanced collaborative control technology and artificial intelligence algorithms, which will greatly improve combat effectiveness and will also form a new combat mode.At the same time, DARPA conducted a second phase of research, including the development and evaluation of tactics and algorithms for increasing swarm autonomy through the improvement and enhancement of unmanned systems platforms.Meanwhile, the tactical background is to use up to 50 UAVs and ground robots to form a swarm to achieve tactical suppression and isolation of the target for 15-30 min within two city blocks.Moreover, compared with leading international scientific and technological teams, there is still no substantial progress in the bottleneck key technology of manned aerial vehicle/UAV swarm cooperative operations in China, and the numerical simulation stage is still stagnant.To realize the application as soon as possible, much scientific research manpower and material investment is required.According to the requirements of combat missions, after a large aircraft carrying multiple UAVs drops UAVs above a designated combat area, the UAV swarm undergoes formation reconstruction, cooperative obstacle avoidance, precise tracking and strike effectiveness evaluation, etc.A new reconnaissance, strike, assessment, planning four-dimensional integrated operations model is based on the combat capability of a single-platform UAV, supported by the interaction and sharing capabilities between clusters, and centred on swarm intelligence, and it has the advantages of invulnerability, low cost, and high distribution.The key technology is summarized into four main contents,namely, cluster control, swarm intelligence, performance evaluation and overall framework, as shown in Fig.6.
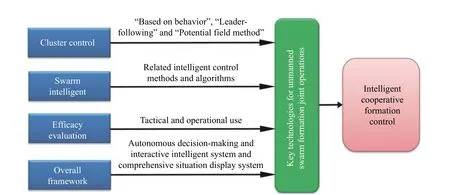
Fig.6 Key UAV swarm cooperative operation technologies
2.4 Intelligent assessment
To effectively improve the ability to win in the combat process, in-depth analysis and repeated deliberation are required for each observation, orientation, decision and action (OODA) link before it can be truly applied to combat.Boyd used complex adaptation theory and cybernetics tools to analyse OODA, stating “There is no need to completely disintegrate the system with a single blow”.Because over time, the effects of an incorrect or slow response are amplified by feedback loops, it is only necessary to create an initial advantage and prevent the enemy from negating that advantage.Therefore, from the point of view of a winning mechanism, conclusions should be drawn from the theory and verified in actual combat, which can better verify the correctness of the theory.For the coordinated operation of unmanned systems, discovery-identification-strike-assessment is the key link in winning a war.Then, the strike assessment is result-oriented, that is, the rationality and effectiveness of the designed combat plan can be better reflected through the strike assessment, as shown in the flow chart in Fig.7.
It can be seen from Fig.7 that it is critical to scientifically evaluate and reasonably improve the implementation plan.At present, intelligence progress has accelerated the technological revolution, making intelligent operations a subversive technological revolution.Strike effectiveness evaluation intelligence makes the task evaluation more efficient and reliable.In multitarget and multitask situations, the amount of target characteristic signal information data is very large.In massive data, it is very difficult to find the true target when relying only on experience and criteria.It is difficult to identify and lock a target quickly and efficiently.Therefore, intelligent algorithms for high-resolution image processing are particularly important.Examples include adaptive neural network algorithms, convolutional neural network algorithms and proportional integral (PI) neural network algorithms.In a complex confrontation environment, intelligent assessment plays a critical role in the entire process of intelligent cluster operations, which lays an important foundation for winning the information war.
3.Communication network disturbance
In joint unmanned swarm formation system operation and a coordinated attack on time-sensitive targets, a smooth communication network is the most important part of winning a war.A communication network is composed of unmanned systems (including space-based weapon systems, sea-based weapon systems, ground-based weapon systems, and air-based weapon systems), corresponding load-bearing command and control platforms and launch platforms, and their corresponding nodes are composed of network nodes.In an entire combat system,combat success or failure is affected by the status of each node in the network and the size of the link signal load.The system networking can be simplified into a network topology structure.If the state of each node or portion of the nodes in the structure is normal, the information transmission direction and signal load of each node will affect the scale and order of the entire graphGand then affect the tracking error of the weapon corresponding to each node, thereby affecting the control accuracy.Typical examples of agent communication networks are shown in Fig.8.

Fig.8 Examples of intelligent agent communication networks
In January 2017, the U.S.AFRL issued a request for information for autonomous networks, which aims to seek network communication technology for the Loyal Wingman autonomous system project to solve the problem of manned/unmanned combat formations.
The Loyal Wingman project was launched by the AFRL in mid-2015.It aims to enable the pilots of fifthgeneration fighters (leader) to control UAVs (follower)and greatly improve the U.S.Air Force’s manned/unmanned aerial coordination combat capability.In March 2016, the AFRL launched a request for a loyal wingman autonomy test, which requires that the autonomous system be able to fully realize the loyal wingman departure from a ground station and complete all basic combat operations without full-time personnel guidance.This autonomous network request for proposals seeks network communication technology for airborne networking in autonomous systems [61–63].
3.1 List of key technical requirements [61]
(i) Autonomous systems have higher requirements on delay, bandwidth, reliability, and quality of service(QoS).The network requirements of autonomous systems are significantly different from current requirements, requiring higher reliability in future high-confrontation environments.Therefore, new network protocols need to be developed to meet the network requirements of autonomous systems.
(ii) Manned/unmanned combat formations need to adopt topological structure and information interaction mode.Current commercial and military network protocols are designed based on unicast or restricted multicast information exchange styles.That is, a client only has a one-way demand for a certain type of information.
(iii) The quality of autonomous systems depends to some extent on the quality of the entire network.Autonomous systems differ in that information needs to be spread from one node to as many nodes as possible.Autonomous systems typically use learning engines.The quantity, quality and timeliness of information of nodes in the network affect the performance of autonomous systems.
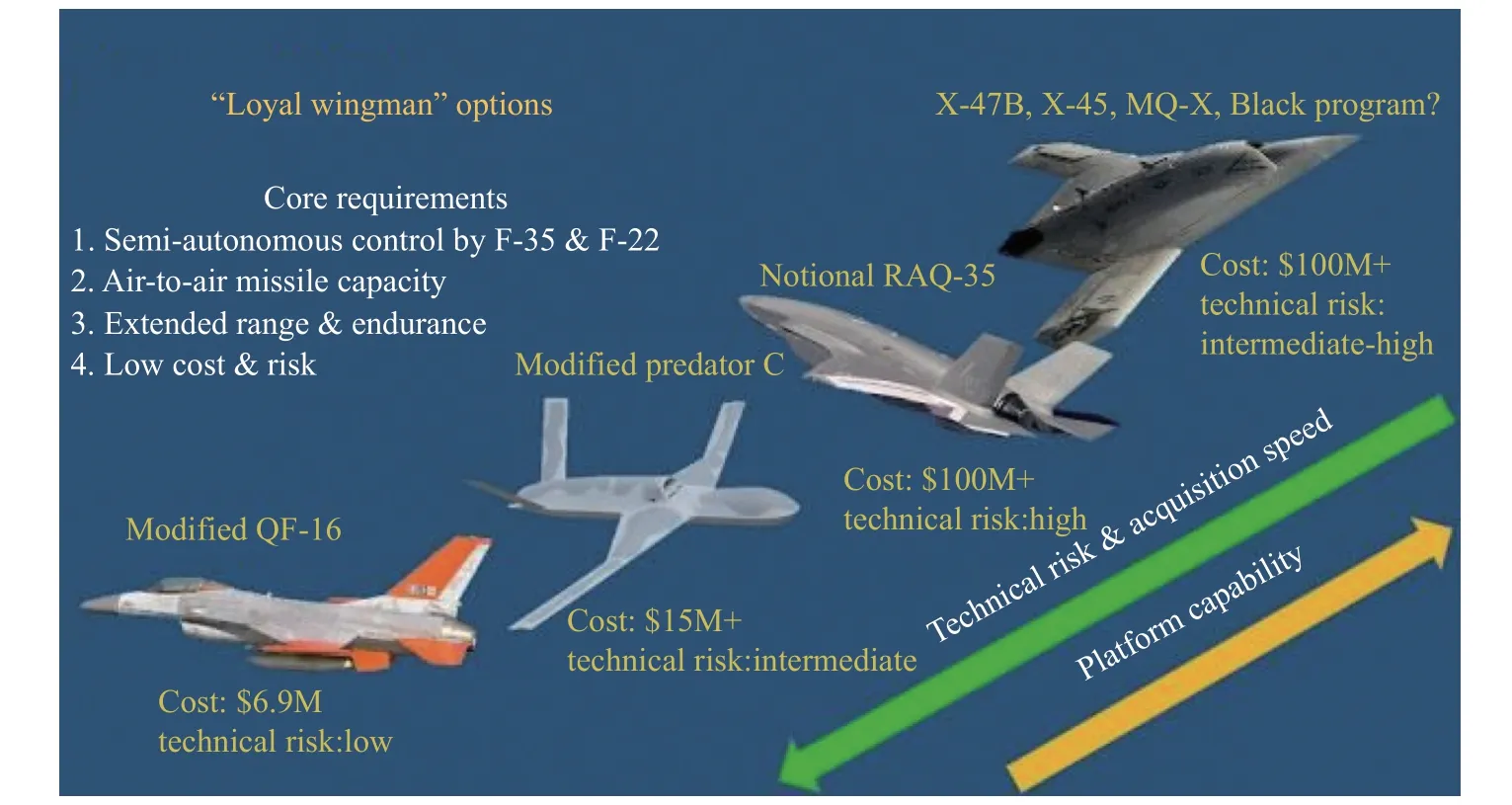
Fig.9 The loyal wingman
(iv) Autonomous systems are affected by size, mass,cost, and more.The networks of unmanned, manned/unmanned formation are highly complex, such as networking between fifth-generation aircraft and small unmanned systems.
3.2 Technical indicators
The U.S.Air Force focuses on solutions at the application, transport, and network layers.To develop the network capabilities of unmanned autonomous systems, the technical goals are as follows:
(i) Application layer: the new application layer protocol needs to meet the application requirements of the autonomous system;
(ii) Transport layer: under the restriction of severe delay, it needs to have congestion control ability to maximize the reliability of end-to-end data transmission.In the case of different needs, it is necessary to share resources through multiple data streams;
(iii) Network layer: this layer includes multipath and/or pathless routing, low-cost routing and network management, flexible service and admission control, and routing in highly dynamic environments.
The loyal wingman is shown in Fig.9.
Additionally, in a communication network, the amount of communication data between nodes or between nodes and the centre is very large, which is affected by the size of the transmission power and the power density to the target.Therefore, before signal transmission, a signal should be quantized so that it can be transmitted to the sensor of each node normally to avoid signal delay, overload and distortion.Therefore, it is necessary to analyse the signal disturbance process because the signal transmission process is susceptible to the influence of the communication link of the weapon system corresponding to the central node of the topology structure and the interference of the corresponding sensors of each node, as shown in the following:
(i) The influence of the communication link, that is, to enter the unmanned system equipment, the ground station of the unmanned system and the terminal of the communication link through wireless means to interfere, disrupt, reduce and damage its electronic information, so that its normal function cannot be restored.Meanwhile, it looks for loopholes in the equipment, injects false data or injects Trojan virus, destroys the communication system,and seizes control of ground communication equipment and communication link terminals.
(ii) Interference of the sensor.For unmanned system equipment sensor electronic countermeasures, the main goal is to interfere, disrupt and prevent the normal operation of various types of sensors carried by weapon equipment.Therefore, it is particularly important for the weapon equipment sensor corresponding to the communication networking node to receive and send information normally.
4.Conclusions and future challenges
In a complex confrontation environment, the intelligent cooperative operation of unmanned swarms is the basis of joint operations.Whether it is the cooperative operation of homogeneous agents or the cooperative operation of heterogeneous agents, it is the cooperation between weapons and equipment or between weapons and commanders.However, cross-domain operations or alldomain joint operations are a new style of future operations.By integrating multidomain combat forces and enhancing combat effectiveness, the combat effect is far greater than that of single-domain operations.This effect is mainly achieved through empowerment, release, and enabling manifestation.For intelligent combat, the accuracy of a model, nonlinearity, and communication overload are all factors that affect the design of the cooperative control law, so scientific problems such as formation change, avoidance, tracking, and cooperative fault tolerance cannot be carried out for the entire unmanned formation system to study in-depth research.Based on this,research into the application of unmanned swarms in cross-regional and intermilitary joint operations in complex confrontation environments is a theoretical weapon for winning wars.Their application to actual combat can effectively stop enemy sabotage attempts and stop deterrence operations to build momentum and test pressure on the system to grasp dominance in the war.
In addition, for combat research on aerospace intelligent unmanned systems, it is necessary to take the combat needs as the traction and the application as the orientation.In a true sense, intelligent operations can move from the test field to the battlefield and then feed back to the test field from the battlefield, effectively carrying out research on joint operations for unmanned systems from the deep integration of theory and technology in complex confrontation environments.
 Journal of Systems Engineering and Electronics2023年6期
Journal of Systems Engineering and Electronics2023年6期
- Journal of Systems Engineering and Electronics的其它文章
- Two-layer formation-containment fault-tolerant control of fixed-wing UAV swarm for dynamic target tracking
- Role-based Bayesian decision framework for autonomous unmanned systems
- Nonlinear direct data-driven control for UAV formation flight system
- Minimum-energy leader-following formation of distributed multiagent systems with communication constraints
- Multicriteria game approach to air-to-air combat tactical decisions for multiple UAVs
- A consensus time synchronization protocol in wireless sensor network
