Energy Theft Detection in Smart Grids: Taxonomy,Comparative Analysis, Challenges, and Future Research Directions
Mohsin Ahmed, Abid Khan, Mansoor Ahmed, Mouzna Tahir, Gwanggil Jeon,Giancarlo Fortino,, and Francesco Piccialli,
Abstract—Electricity theft is one of the major issues in developing countries which is affecting their economy badly.Especially with the introduction of emerging technologies, this issue became more complicated. Though many new energy theft detection (ETD) techniques have been proposed by utilising different data mining (DM) techniques, state & network (S&N)based techniques, and game theory (GT) techniques. Here, a detailed survey is presented where many state-of-the-art ETD techniques are studied and analysed for their strengths and limitations. Three levels of taxonomy are presented to classify state-of-the-art ETD techniques. Different types and ways of energy theft and their consequences are studied and summarised and different parameters to benchmark the performance of proposed techniques are extracted from literature. The challenges of different ETD techniques and their mitigation are suggested for future work. It is observed that the literature on ETD lacks knowledge management techniques that can be more effective,not only for ETD but also for theft tracking. This can help in the prevention of energy theft, in the future, as well as for ETD.
I. INTRODUCTION
THE smart city infrastructure and its services are dealing with complex challenges to comply with the necessities of residents, due to the exponential growth in the human population. It is very problematic to find a smarter way to overcome the issues of traffic congestion, waste management,increased energy consumption, and over-consumption of resources. Technology has been evolved in its way to give ease to humans and introduced the concept of the smart city where everything is interconnected with each other. Typically,it consists of smart services, smart transport, smart healthcare,smart surveillance, smart building, and smart distribution of electricity and water. A smart grid (SG) is an essential part of a smart city that is concerned with the smart management of electricity generation, transmission, distribution, and control.SG records all actions of its users – i.e., energy consumers and staff working at SG –, improves the utilisation of electricity resources and provides a long-term viable power system.These features make it of high quality, minimise overall losses, and maximise the security to ensure the safe supply of power [1]. SG also reduces the environment’s pollution by controlling carbon emissions. Smart city and SG combinedly utilise the smart service and advanced electrical engineering,assisted by information and communication technology (ICT),for effective management of complex infrastructure. There are some shared principles for the interaction between smart city and SG, such as integration, intelligent inter-connectivity, and end-user elements of the SG. Where the SG is providing ease to its stakeholders, at the same time it is giving birth to some new potential challenges. One of the crucial challenges is a threat to the security and privacy of SG, which ultimately leads to electricity theft. If fraudulent users get access to the private data of the consumers, they could use it in a wrong way and affect the lives of consumers. There is a strong need to provide a security mechanism to continue the operations of SG. Otherwise, there could be chances to shut it down. This could make its consumers face a shortage of electricity that will disturb normal life activities, such as the halt of heating systems, unavailability of online payment systems, and many others. Many researchers have shown their interest in providing security to the SG infrastructure by identifying the malicious users and zero errors of the system [2]. In this paper, we have studied and investigated the existing state-ofthe-art energy theft detection (ETD) techniques that have been implemented in SG. We introduced a new taxonomy to classify them, summarised their strengths and weaknesses,and provided future directions to redirect the research community to the right and effective way.
Advanced metering infrastructure (AMI) revolutionised the mechanism of electricity generation, transmission, distribution, and consumption. The deployment of SM is emerging and they are replacing electromagnetic meters (EM). One of the main drawbacks of EM is that they can easily tamper with different methods [3]. Greeret al.[4] presented research,according to which, the market of smart grid (SG) will be grown to $50.65 billion by 2022. An Indian study [5] showed that there will be more than 52 million SM in 2012 and figures will reach 2 billion by 2030. However, the above-mentioned three major aspects of electricity, i.e., generation, transmission, and distribution, involve many operational losses. These losses are mainly classified as technical losses (TL) and nontechnical losses (NTL). The TL involve in transmission &distribution (T&D) due to energy dissipation in conductors,transmission line’s equipment, transformer, sub-transmission line, and distribution line. While on the other hand, the NTL is associated with energy theft. Energy theft is a worldwide phenomenon, and there are different types and ways of energy thefts [6]. This includes meter tampering, meter malfunctioning, taping electricity from a feeder, rigging from the transmission, billing irregularities, i.e., billing alteration and unpaid bills, cyber tampering, and other physical methods[7]. Though, TL cannot be stopped as they are due to technical energy dissipation. However, the identification and controlling of fraudulent consumers can minimise NTL.
Many studies have been performed to analyse the consequences of energy theft. PennEnergy [8] recorded that there is a loss of almost 96 billion US dollars every year due to energy theft and ranked energy to the third number as the most stolen item in the world. Only in the USA, per year amount of energy theft reached 6 billion US dollars. World Bank reported that energy theft is impacting gross domestic product (GDP) of various countries highly with a value of 1.2%. Gaur and Gupta [9] performed an empirical analysis from 2005 to 2009, and found that 20% of the generated amount of electricity is being lost in India. Another Indian research [10] focused on the financial sustainability of electricity and found that the accumulated losses have been reached 2.5% of Indian GDP, which showed a loss of 14.8 billion US dollars. The latest survey [11] showed that the transmission & distribution losses (T&DL) are up to 27%,which is the highest in the world. A reason behind this increased percentage is the utilisation of old and outdated technologies. After India, there comes Korea with 12.5%,Taiwan (a city of China) with 9%, the USA with 8%, and Japan with 7% T&DLs. Energy theft also resulted in the death of energy thieves in some cases. Tayloret al.[12] performed a retrospective study where they found 8 death cases from January 1981 to December 2001. Electricity frauds cannot be eliminated. However, they can be detected and precautionary measures can be taken for them [13]. Various ETD techniques have been introduced and tested in various environments, i.e.,simulation and real-time implementation. DM is broadly used to reveal those customers who are stealing energy from utility companies. The major practices performed in DM techniques are support vector machine (SVM), extreme learning machine(ELM), artificial neural network (ANN), optimum path forest(OPF), naïve Bayesian (NB), decision tree (DT) fuzzy clustering, k-means clustering, spatial clustering, and pear-topear computing. There are also some ensemble learning techniques such that gradient boosting (GB) which classify energy customers. In these techniques, the customers are classified as regular and fraudulent customers on the base of their load-profiles and some other factors. One of the major drawbacks of such techniques is that they require customer’s data in detail, which is mostly not available. Moreover, the available data is not realistic. The S&N-based techniques are also introduced for ETD such as state-estimation, phasor measurement, sensor monitoring, and physical monitoring(PhM) which involve network topology and different sensors at energy transmission and DS as well as in SM too. The implementation of such network systems is infeasible because they completely depend on network parameters that are usually unavailable.
Though, the evolution in technology introduced lots of new and evolutionary techniques that tried to tackle the problem of energy theft. However, this rapid development also opened new ways for fraudulent customers. Moreover, in some cases,evolution is itself a kind of obstacle or challenge in ETD, such as the availability of detailed network parameters in network& state-based techniques. In this research work, we are aimed to provide a detailed survey of existing ETD techniques to date by exploring their functionality, strengths, and limitations. Moreover, we are also going to identify different types of energy theft and try to give some future directions for upcoming practitioners to set their effort in the right direction.
A. Existing Surveys
Jianget al.[14] focused on the issues that occur during the theft detection in SG. They illustrated energy theft behaviour in SG by presenting an attack tree-based threat model. They summarised existing ETD techniques and classified them into three categories, such as classification, state estimation (SE),and GT techniques. They did a discussion on the literature and performed comparative analysis. They also presented challenges and future directions to guide the new researchers.Jumaleet al.[15] studied different ETD methodologies and provided an overview of them. But, neither they concluded their overview nor they extracted challenges and future directions from their survey. They even did not classify existing literature to understand it easily. Czechowski and Kosek [6] presented a short overview of the most common and frequently used energy theft techniques and the hazards which prompt the fraudsters to do so. They also over-viewed the detecting mechanisms shortly and summarised the legal aspects of energy theft in the different countries of the world.Their main focus was on the techniques which are used in the theft and its detection where the consumers use regular EM.
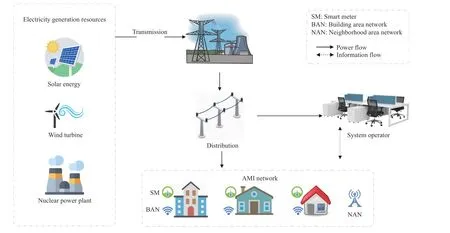
Fig. 1. Smart grid architecture.
Viegaset al.[16] reviewed the main NTL detection techniques and their limitations, since 2000. They proposed a topology to categorise existing solutions and classified them as Theoretical Studies, Hardware Solutions, and Nonhardware Solutions. They found that non-hardware solutions got researchers’ attention as they got 72 studies among the total selected studies, i.e., 103. They also found that most of the Non-hardware studies are strongly based on the data which is usually not available. Missinis and Hatziargyriou [17] categorised existing state-of-the-art ETD detection techniques, especially focused on NTL, in three classes such as network-oriented, data-oriented, and hybrid techniques.Besides the classification, authors majorly focused on the ETD algorithms, metrics that were used to evaluate the different properties used in the algorithms, and the efficiency of the detection systems. They also defined the data types that were used by these algorithms and specific features extracted from these data types. In the end, they performed a qualitative analysis of state-of-the-art NTL detection techniques by focusing on data variety, data quality, performance, and cost issues and efficiency of the systems, i.e., system response time. The key contributions of this paper are:
1) We defined a taxonomy where we classified ETD techniques on the basis of the nature of algorithms and the internal functionality of techniques.
2) We identified factors that affect energy consumption patterns of consumers and highlighted those factors which are not implemented yet.
3) We identified types, reasons, and effects and consequences of energy theft from literature.
4) We identified major attributes that should be considered while proposing a new technique for ETD.
5) We identified evaluation criteria, used in the literature,and highlighted those which are widely used by other authors.
6) We performed a comparative analysis of existing ETD techniques based on their performances.
The rest of the paper is organised as following: Section II briefly introduces smart grid system model. Sections III and IV describe energy theft in smart grid and energy theft detection techniques in smart grid. Section V shows comparative analysis of ETD techniques. Sections VI–VIII show discussion, challenges and future directions, and conclusion, respectively.
II. SMART GRID SYSTEM MODEL
The SG is a revolutionised form of the typical grid system.It helps to improve the efficiency of the grid system, and it also addresses the sustainability and security of the grid [18].AMI network is an important component of the SG that enables two-way communication between the service providers and service consumers. The SM is installed on the consumer’s end through which the utility communicates with the consumer. The SG’s architecture is shown in the Fig. 1.
In SG, transmission stations (TS) get the energy from sources of generation and transmit it to the distribution stations (DS). From the DS, it is distributed among its customers (i.e., commercial and non-commercial). Each AMI network is responsible for covering an area to fetch electricity consumption data and send it to the utility. The utility use this fine-grained data to handle many of the operations of SG,such as handling of demand-response level, bills computation by dynamic pricing, and etc [18], [19].
The new SG architecture shut the doors for traditional energy theft, like meter tampering and line-hooking [20].However, it opened new doors for fraudulent customers that are a serious cybersecurity threat. For example, a customer hacks the AMI network and manipulates (reduces) the consumed amount of energy [21]. In this way, he steals energy from the utility. Where it causes financial losses, it also disturbs the integrity of SG. A hacker can not only change the consumption of others but can also get their personal information.
III. ENERGY THEFT IN SMART GRIDS
The utilities have been facing different threats, issues, and challenges. Energy theft is one of the key challenges that is a criminal practice. Energy theft is the utilisation of energy without paying its price. This could be done in different ways,such as meter tampering, feeder bypassing, billing irregularities, etc. Where the technology changed many aspects of life, it also enhanced metering infrastructure and introduced SG. However, the implementation of information and communication technologies enabled cyber-attacks to steal energy.
A. Types of Energy Theft
Researchers have identified different types of energy theft.We have identified them from the literature and summarised all of them. They are given below:
1) Meter Tampering/Malfunctioning:
● Disturb meter efficiency:Highly viscous fluid, a strong magnet, or something is inserted into the meter to slow down its speed [22], so the meter does not count all consumption. A powerful blow to the meter can also permanently disturb the disk rotation [23].
● Tamper meter wires:The voltage wires of the electricity meter or insulation on secondary side wires are tapped to alter the measured amount of current [24].
● Ends shortening:Both ends of the meter are partially disconnected. All current does not flow through the meter, and the meter does not record full energy consumption [25].
2) Feeder Tapping:
● Illegal or unauthorised connections:In this type of energy theft, the home load is directly connected to the transmission line [26].
● Use single-phase from three-phase supply:It is a skilful technique in which the neutral is disconnected from the transmission and a separate neutral is used as a returning path.The voltage consumption becomes zero and the meter records null energy consumption [27].
3) Billing Irregularities:
● Unpaid bills:Fraudulent customers make illicit payments to the officials (from the utility) to not disconnect their electricity supply for not paying bills [28].
● Billing alterations:Fraudulent customers make illicit payments to the officials (from the utility) and ask them to record wrong meter readings to generate the bills [28].
4) Cyber-Attacks:
● False data injection (FDI):Variables, that carry the values of energy consumption, are manipulated to bypass the existing bad measurement detection (BMD) methods [29].
B. Consequences of Energy Theft
There are lots of consequences of energy theft that have been discussed in the literature. One of the straight forward consequence is that the utility companies are affected due to stolen energy. There are certain other stakeholders which are affected, listed below:
1) Utility Companies:Utility companies are directly affected by energy theft as they receive less revenue against the provided amount of energy. So, they run under the loss.
2) Power Supply Quality:The power supply system is overloaded to comply with the needs of customers. This overloading causes quality deterioration, i.e., sometimes people face load shading because of the imbalance between demand and supply.
3) Fair Consumers:As utility companies run under the loss,they increase the overall billing amount through which fair consumers have to pay extra for their consumption.
4) Government:Utilities, running through loss, are unable to invest in the propagation of countries’ economies.Moreover, where the government provides free electricity to the farmers, the stolen energy from those platforms also affects government assets.
C. Evaluation Criteria for ETD Techniques
There are many evaluation criteria, used to measure the performance of ETD techniques. However, there is not any single parameter used by all researchers. The most used evaluation criterion is the detection rate (DR) that is used by almost all of the researchers except few ones. All of the evaluation criteria are listed below.
1) DR:It is the proportion of an individual to the whole, by satisfying a particular condition [30]. It is also called classification rate (CR) or hit rate (HR).
2) True Positive Rate (TPR):It represents the percentage of correctly identified anomalous data [30] i.e., data is actually abnormal and identified as abnormal too.
3) False Positive Rate (FPR):Also known as false alarm ratio, is the percentage of incorrectly identified anomalous data [30], i.e., data is actually normal but identified as abnormal.
4) False Negative Rate:It represents the percentage of incorrectly identified normal data [30], i.e., data is actually abnormal but identified as normal.
5) Recall:It is the ratio of correctly identified anomalous data to the sum of correctly identified anomalous data and incorrectly identified normal data [31].
6) F1 Score:It is also called the F Score or F Measure,which shows the relationship between precision and recall[32], [33].
7) Area Under the Curve (AUC):It is the function of definite integralf(x)between two points [34], i.e.,x=a&x=b.
8) Return on Investment (ROI):It is the efficiency of amount which is being invested [35]. It tells what will be return after the investment of a particular amount.
9) Deployment Cost (DC):It is the cost that is needed to deploy the system.
10) Time Complexity (TC):It is the time that is needed to deploy or execute the system.
11) Privacy Preservation (PP):It is the preservation of the privacy of consumer’s data which is collected by the utilities.
IV. ENERGY THEFT DETECTION TECHNIQUES IN SMART GRID
Energy theft is one of the major parts of NTL in electricity.The involvement of greedy and fraudulent human nature made it more and more crucial to detect. Lots of innovative and novel solutions have introduced with the rapid development in SG. The overview of studies, included in this survey, is presented in Tables I–III.
Here, in Fig. 2, we are introducing our taxonomy of ETD techniques to explore and analyse them easily. We classified them as DM Techniques, S&N-based techniques, and GT techniques.
A. Data Mining (DM) Techniques
DM techniques are widely utilised techniques for the identification of fraudsters that are specifically based on machine learning (ML). These techniques are also used for consumers’ characterisation and tariff planning, house size of customers, and many more. They could be divided into classification and clustering techniques.
1) Classification Techniques:Classification techniques are supervised ML techniques that use labelled data. Two steps are involved: learning and classification. For ETD, all of the load-profiles are classified as fair, fraudulent, or malicious consumers on the basis of their consumption patterns.
Support vector machine (SVM) based techniques:
Vapnik introduced the SVM algorithm in 1965 [118] to construct an optimal decision functionf(x). It is very popular for the classification of load-profiles. Nagiet al.[36] extracted 25 features from load-profiles and classified them with SVM. Further, in [37], they optimised their technique using the genetic algorithm (GA) along with SVM. Though authors successfully detected meter taping and tampering, large historical data required to perform the detection. Moreover,both of the methods are unable to detect FDI. They proposed another SVM method using a structured query language(SQL) to group fraud consumers [38]. This method successfully detected abrupt changes in load profiles. However, meter readings were transformed into average consumption which may deviate from actual consumption. Later on, the author replaced SQL with a fuzzy inference system (FIS) for training and classification [39]. But they only performed pilot testing.Depuruet al.[40] established a dataset to represent loadprofiles and considered consumer’s geographical location,load capacity, and their type to analyse their consumption patterns. However, they did not discuss the calculation and validity of load capacity. Furthermore, they did not consider other attributes like weather/seasons, events, etc. For the detection of illegal consumers, Depuruet al.inspected highperformance computing (HPC) algorithms [119].
Jokaret al.[20] proposed a consumption patterns based energy theft detector (CPBETD) by leveraging multi-class SVM. The transmitted and consumed amount of energy was computed through individual meters to compute the total amount of energy consumption of the neighbourhood. The difference in both calculations was declared as energy theft and a multi-class SVM was trained with historical data to classify the new sample as a tampered record. However, it is infeasible due to the involvement of manual data collection.The sample data was assumed to be fair and honest which can lead to faulty classification. Wuet al.[41] proposed AdaBoost-SVM, where they combined adaptive boosting(AdaBoost) algorithm with SVM. The SVM worked in an iterative way where it kept changing the weights of the training dataset and stopped when reached the threshold value.The authors also focused on the identification of periods of electricity theft by implementing a general regression neural network (GRNN). The experimental results showed that AdaBoost-SVM outperformed GRNN. However, large regression absolute error stopped to minimise the duration of these intervals. This was due to the large forecast span time,weak features selection, and medium-term load forecast.
Extreme learning machine (ELM) based techniques:
Nizaret al.[42] proposed the ELM based approach with the integration of online sequential (OS) algorithm. ELM used load-profile to explore whether the consumer is abnormal or a regular, and OS improved performance and accuracy. Though authors considered the individual impact of different factors.But the performance of the algorithm varied on different weekdays. There is a need to consider more factors like special occasions, events, long vacations, etc. Furthermore, in[43], the authors presented a case study where they compared the performance of their proposed technique with SVM and showed that OS-ELM is superior to SVM. However, these technical approaches could be effectively implemented, only if the proper communication is ensured between the central control station and the appropriate test points. Xueet al.[44]proposed another ELM technique based on one-class-onenetwork (OCON) for identification of FDI. They improved the power system’s resilience with the prediction method, by utilising the relation of supply data in the subnet. The key contribution of this technique was the recovery of the affected data. Authors compared results with ANN and SVM and found SVM outperforming, but its training time was very high. However, the training time for ELM-OCON was very low that made it efficient than both of the others. But, for the recovery of FDI, a large amount of information about network topology required that is normally unavailable.
Artificial neural network (ANN) based techniques:
Munizet al.[45] proposed ANN-based methodology for ETD, consisting of filtering and classification. Both modules are comprised of five neural networks to classify consumers.The experimental results found it worthy for low tension consumers. However, the data was untrustworthy due to visiting employees at the company. Moreover, the system could be needed retraining with time. Depuruet al.[46]proposed an encoding technique to enhance the efficiency of the model. This is the only model that detects energy theft with zero consumption in load-profile. The load-profiles were reduced to one-third of the actual with encoding. However,the encoding technique converted meter data into binary values, so the model is not applicable for a wide range of attacks. Moreover, the authors made assumptions for ETD which can be violated. Bhatet al.[47] studied three deep learning algorithms – convolutional neural network (CNN),long-short-term-memory (LSTM), and autoencoder – on IEEE 123 bus test feeder having for 1 year. The results depicted thatCNN is best among them. However, LSTM and autoencoder outperform CNN, DT, and RF. Huanget al.[48] utilised the feed-forward architecture of ANN by applying three methods:checking the existence of energy theft, detecting fraudsters,and locating theft. However, in the simulations, some fair consumers were also listed as unfair due to the adjustment of the honesty coefficient. Yaoet al.[49] combined CNN along with the Paillier algorithm for ETD while preserving privacy.The main focus of this work was to keep the consumer’s data protected and reduce its disclosure. However, the involvement of online third-party is again a threat to users’ privacy.

TABLE I OVERVIEW OF EXISTING DATA MINING BASED ENERGY THEFT DETECTION TECHNIQUES
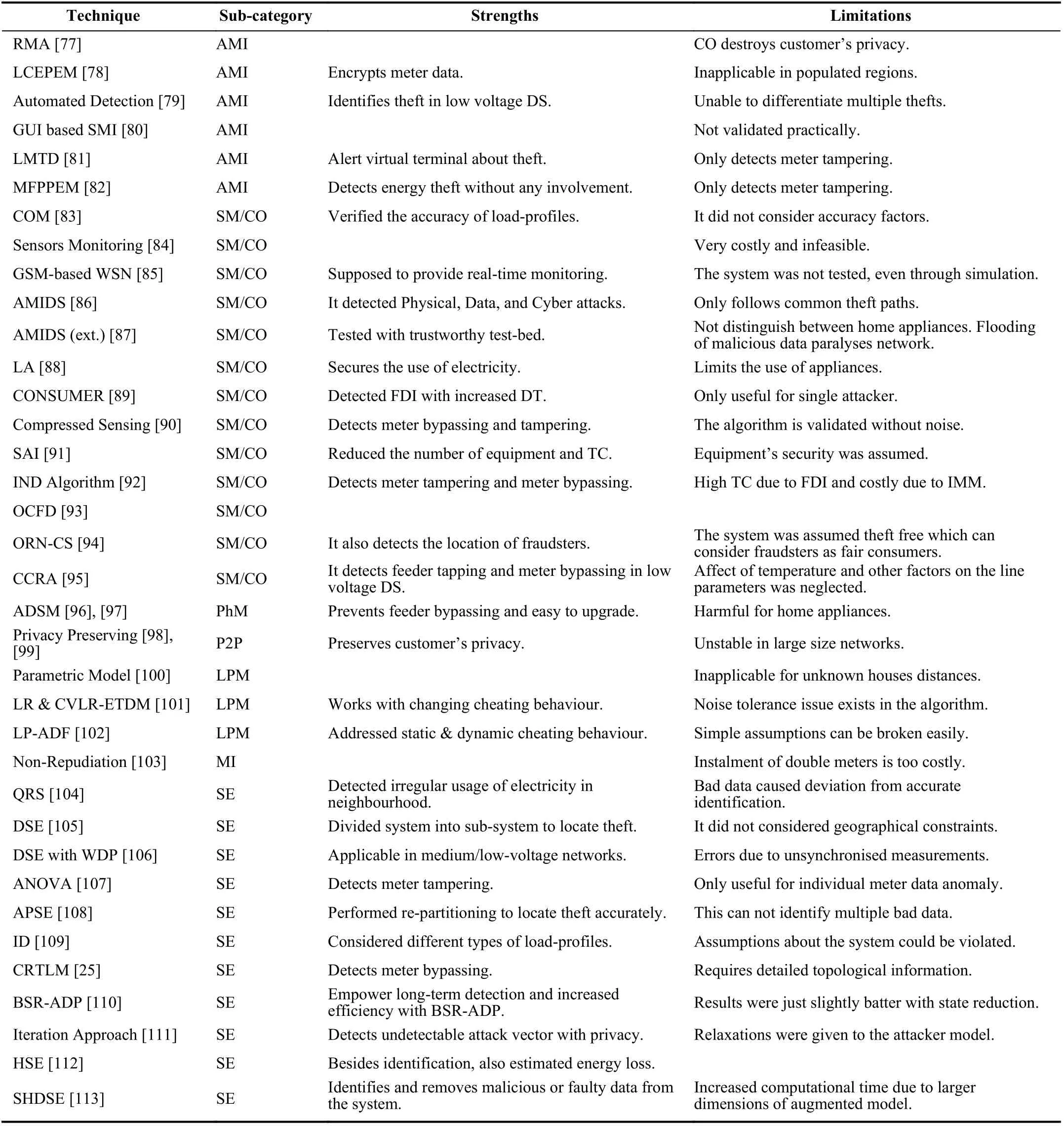
TABLE II OVERVIEW OF EXISTING STATE & NETWORK (S&N) BASED ENERGY THEFT DETECTION TECHNIQUES
Nabilet al.[50] proposed CNN-based PP method for ETD,named privacy-preserving electricity theft detection (PPETD).They enabled SM to send the load-profiles secretly to the system operators (SO) at the utility. They masked the meter readings on consumer’s to make them secret. The masked readings were aggregated to hide individual readings. In this way, detailed consumption patterns can be avoided. But the deployment of CNN is based on the multi-party computation protocols that use binary and arithmetic circuits. So, the computation overhead is too high and such SM can not be cost-effective by having enough resources to perform thesecomputations. Ismailet al.[51] designed and implemented Deep Feed Forward Neural Network-Based Detector, Deep Recurrent Neural Network-Based Detector, and Deep Convolutional-recurrent neural network (RNN) Detector for the detection of unaware cyber-attacks. They found RNN outperforming in terms of high detection rate and low false positive. However, its time complexity for the training is high because it required a large dataset, generated by the combination of three data sources. Souzaet al.[52] presented a multilayer perceptron artificial neural network (MP-ANN)for the identification of fraudulent consumers in the neighbourhood. MP are very much useful in pattern recognition, function approximation, time-series prediction,etc [120]. After detecting the affected transformer, the authors collected load profiles of all the consumers using static state estimation (SSE). Then, they used self-organising maps(SOM) to cluster the load-profiles according to their patterns and then used MP-ANN to identify the fraudsters. In MP
ANN, the number of neurons must be equal to the variables in the input layer and the output layer. So, the authors used two neurons in the output layer as they have to classify the consumers either as honest or fraudulent. Wanget al.[53]proposed a FDI detection approach, based on autoencoder ANN. The classifier was only trained with normal loadprofiles. So, it successfully identified abnormal profiles that deviated from the normal ones. Zhanget al.[54] also focused on the detection of unobservable FDI attack and proposed an adversarial autoencoder (AAE). They adopted generative adversarial network (GAN) using deep learning to detect FDI attack, and autoencoder for the feature’s selection. They established a game between two neural networks, i.e., a generator G and a discriminator D, where G produces fake measurement data samples and D distinguishes between real and fake samples. The proposed method is very straightforward in learning as it only used 2% labelled data to train the model. But, it needs a large amount of historical data to successfully identify the FDI attack.
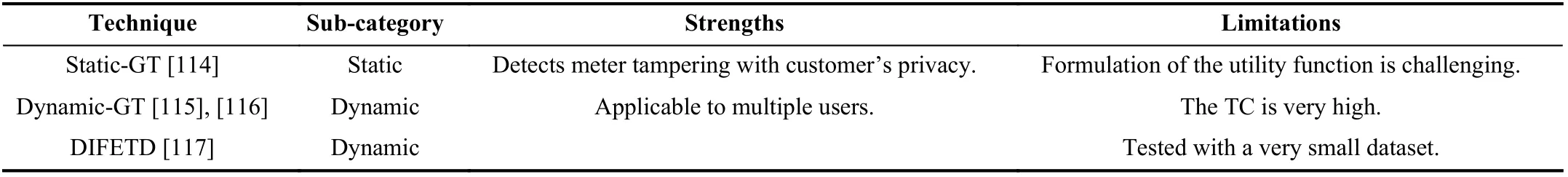
TABLE III OVERVIEW OF EXISTING GAME THEORY-BASED ENERGY THEFT DETECTION TECHNIQUES
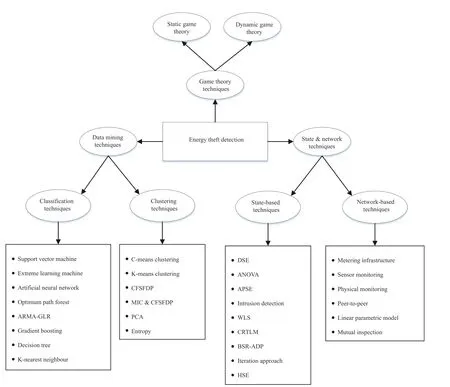
Fig. 2. Taxonomy of ETD techniques.
Optimum path forest (OPF):
Ramoset al.[55] introduced OPF classifier for automatic ETD. First, the classifier was trained with two distinct datasets Bi & Bc, then the pruning algorithm was applied to the classifier. The classifier was tested and uncertainty was significantly reduced while using OPF with pruning.However, it was only useful for commercial consumers with higher consumption. Later on, in [56], they focused on the feature selection of load-profiles, based on harmony search(HS). The OPF was trained and its performance was evaluated for a set of features, and a sub-set was selected with maximum accuracy. In the former study [57], they compared the performance of OPF against different classifiers to benchmark the results and found OPF outperforming with significantly reduced TC. Then, they experimented for feature selection with particle swarm optimisation (PSO), HS, and gravitational search algorithm (GSA). PSO outperformed for features selection, but it lacked in collecting consumption data from multiple sources, which can make the system intelligent [121].Trevizanet al.[58] proposed discrete cosine transform (DCT)and OPF for automatic selection of features. First, a set of labelled inputs was split into training and evaluation, and then the classifier predicted labels form the evaluation subset repeatedly. The main purpose was to increase the success rate of on-site inspection. After that, the system was trained with the newly collected information and gave accurate outcomes.The system was tested on the dataset based on the IEEE 123 Node Test Feeder and considered a seasonal change in loadprofiles. However, test results showed significant inconsistency in performance while applying it to different scenarios. Moreover, the system was not tested with the actual data. In their later work [59], they extended it with the integration of distributed state estimation (DSE) and improved the accuracy of the classifier. Fernandeset al.[60] proposed a probability-based OPF (P-OPF) with supervised learning using a complete & k-neighbourhood graph for the detection of energy theft. P-OPF firstly group trained and tested data and then classified on the base of probability. The proposed technique not only detects fraudulent consumers but also track them in the future. The detection accuracy of the proposed technique was 82.90%. However, it is costly and overflow can occur due to log function in likelihood. Moreover, it also lacks in multi-class classification.
Auto-regressive moving average-generalised likelihood ratio (ARMA-GLR):
Mashima and Cárdenas [61] tried to find the worst possible attacks for each classifier and evaluated each classifier by calculating the cost of these worst attacks. They developed the auto-regressive moving average-generalised likelihood ratio(ARMA-GLR) model where they implemented a new metric to evaluate the classifier’s accuracy. This included two assumptions: firstly, a fact that past data can not always represent future data, secondly, theft data is usually not present for academic studies. Though, On the base of these assumptions, the system achieved a DR of 62% with an FPR of 4.20. But it is not useful when fraudsters change attacking techniques.
Gradient boosting (GB):
Punmiya and Choe [62] proposed a gradient boosting theft detector (GBTD) to improve the performance by reducing TC with the help of engineering features. The authors practically applied the proposed ML algorithm on six different theft cases successfully. But unfortunately, this technique could not be implemented to identify those who are stealing energy through bypassing. Moreover, the GB is based on the iterative fashion which is time-consuming. Dahringer [63] also presented a GBTD based on extreme gradient boosting (XGBoost), light gradient boosting method (LightGBM), and categorical boosting (Cat Boost). First, they pre-processed collected data of SMs. Second, they extracted features, and finally, they performed theft detection using GBTD. The authors claimed to reduce FPR, data storage space, and time complexity.However, they did not implement their proposed method to verify it.
Decision tree (DT):
Jindalet al.[64] presented a DT approach with hybrid SVM, i.e., hybrid decision tree (H-DT). In this top-down scheme, gathered load-profiles were rigorously analysed in two levels. The thefts were detected at multiple levels (i.e.,T&D) by comparing transmitted data with the total consumed data. First, the data were analysed by DT to predict the consumption and then its output was fed as an input to the SVM to classify consumers. The test results showed that without DT, the accuracy of SVM was 87.5% which was increased to 92.5% with the integration of DT. However,some assumptions were made about the system and the technique was applied in those areas where the conventional meters were just replaced with the SM, so those people were not familiar with the energy theft attacks very much.
K-nearest neighbour (KNN):
Azizet al.[65] utilised KNN to identify normal and fraudulent energy consumers. First, they normalised the dataset with the help of Interpolation, empirical mode decomposition (EMD). Then, they extracted the thirteen most important features of the signal to feed the classifier. Once the features are extracted, they implemented KNN on the dataset.They found it outperforming SVM or any other linear regression algorithms because KNN does not require any time for the training. In KNN, the training is done while making predictions about the dataset. Though the authors achieved an accuracy of 91%, the FPR (11.88%) of KNN is higher than the other state-of-the-art classifiers used for ETD. Pedramnia and Shojaei [76] proposed decomposed nearest neighbour(DKNN) to detect FDI attacks in SG. They extracted data properties of load-profiles using the convex optimisation method. However, the proposed technique results in higher accuracy when the no. of nearest neighbours increases. This could probably increase the TC of the FDI detection system.
2) Clustering Techniques:These are also the DM techniques that are based on unsupervised learning. In this type of technique, the data is unlabelled. The population is divided into several groups on the base of similar and dissimilar data points. In the context of ETD, consumers are divided into fair, malicious, fraudulent, etc. on the base of their load-profiles.
Fuzzy c-means clustering:
Angeloset al.[66] proposed c-means fuzzy clustering technique which classified load-profiles using five attributes.First, consumers with similar profiles clustered using c-means clustering. Then, distance measures were normalised and ordered using a fuzzy membership matrix. They derived attributes by analysing real data and validated the algorithm.However, they only fulfilled minimum algorithm requirements and validated algorithm only with abnormal data. Babuet al.[67] also proposed c-means technique, based on three steps: choosing a set of attributes to represent loadprofiles, defining the domain of selected attributes and defining a range for regular consumption, and finally classifying the abnormal patterns by defining a threshold.Though, they considered different factors and validated with real data, by successfully identifying energy thefts. However,they validated with a very small amount of data and did not consider the PP of consumers. Terciyanliet al.[68] proposed a score based computational technique by utilising fuzzy cmeans clustering. The proposed approach comprised of three steps: first, they assigned a score to a meter according to its area. Second, a fuzzy c-means clustering was applied to gather similar consumption profiles. Third, the expected value compared with the real usage and the difference was taken as the final score, used for the detection of fraudsters. Viegas and Vieira [69] also implemented fuzzy c-means clustering and introduced a novelty detection technique. On the base of extracted clusters, they captured the structure as a detection model. They obtained classification criteria on the base of social surveys and validated the algorithm on real data.However, they did not test with the complex attack patterns,and the achieved value of FPR was significantly high.
K-means clustering:
Zhanget al.[70] proposed k-means clustering-based ETD framework for an edge data centre. They trained and utilised variational autoencoder and generative adversarial network(VAE-GAN) for features extraction. Then they implemented k-means clustering on the extracted features to formulate the threshold-based abnormality detector. This abnormality detector identified the abnormal load-profiles on specified abnormality degree. The proposed framework outperformed SVM and significantly reduced computational time, i.e., from 52 minutes 31 seconds for SVM to 1 minute and 13 seconds for the proposed one. However, they assumed that there is a centralised data centre, which has enough resources for the training and utilisation of VAE-GAN.
Density-based spatial clustering of applications with noise (DBSCAN):
The density-based spatial clustering of applications with noise (DBSCAN) is a human intuitive clustering method.Zhenget al.[71] proposed method, named as clustering by fast search & find of density peaks (CFSFDP), by implementing densityClust. They focused on the calculation of local density and distance from the sample with high density. They performed testing on six malicious types and found it outperforming. However, the performance evaluation for each type showed that the technique is inconsistent. In their later work [72], they combined maximum information coefficient (MIC) with CFSFDP to solve the problem of SM tampering. MIC was used to identify the relationship between consumption patterns and NTL. The combined technique gave batter results for mixed types of FDI attack. Singhet al.[73]transformed high dimensional data into low dimensional with the help of PCA. An anomaly score was assigned to the set of variables, for theft detection. The normal and abnormal consumers were separated by using the threshold-based separation method. Though authors considered different types of customers while testing their technique, the FPR was very high. Later on, in [74], the authors extended their work and reconstructed AMI data with the help of PCA and computed relative entropy for theft detection. However, the threshold was derived from the historical data, and the values of TPR and FPR were completely dependent on this threshold.
Singhet al.[75] implemented relative entropy to analyse the variations in consumption patterns of different customers.They computed the difference between two consecutive measurements on the base of the probability function. The control centre recorded consumption patterns, where data was aggregated and sent it to the utility manager or any third-party responsible service provider. The TPR of 90.28% was achieved which depicted the successful implementation of the proposed technique. However, it was assumed that the control centre considered all of the measures to keep customers’ data secure. This assumption could be violated easily because it does not have any empirical validation.
B. State & Network (S&N) Based Techniques
S&N-based techniques give another common solution for ETD in which the DR is improved by monitoring the state.
1) Advanced Metering Infrastructure (AMI):Pasdar and Mirzakuchaki [77] used another remotely monitoring architecture (RMA) based on power line impedance for ETD.The values of transmission line impedance and phase angle at two different frequencies can determine legal and illegal customers along with their location. However, it requires surety of proper communication between the central observer and targeted meter. Zaidiet al.[78] also presented a smart metering infrastructure (SMI) for real-time monitoring, named as low-cost electronic prepaid energy meter (LCEPEM), to eliminate the possibility of overcharging and over billing and making bill payment more convenient. This can surely reduce billing irregularities. The other goal of this SMI was to make the meter tamper-resistant, which is the most common energy theft in Pakistan. However, a multitude of social and economic factors resist this infrastructure in a more populated country or region. Kadureket al.[79] proposed a two-phase method for automated detection of illegal utilisation of energy, i.e., energy theft. The proposed method estimates energy consumption for medium voltage and low voltage MV/LV substations and compares the actual consumption with that estimated consumption values to detect energy theft.It also identifies the location of theft by identifying the point of connection. Though, through simulation, the system gave a 100% DR. But it is only applicable for small DSs, and it was simulated on a small dataset. Moreover, it is unable to identify multiple theft attacks at one point and there is a time delay between request and response from SM, MV/LV substation,and feeder.
Keeet al.[80] introduced a GUI-based novel design of SMI. The proposed method included the energy balance method, SM in AMI, physical detection sensors, and AI algorithms (fuzzy logic & SVM). The three-tier design of the detection algorithm was proposed to enhance the performance.They compared the phase current at the feeder and Low voltage lines to detect theft area. Then applied AI algorithm to find suspicious profiles. The proposed algorithm based on the triangulation technique that facilitated data validation through cross verification from three sources. However, the NTL Status level HIGH and LOW are mentioned but did not discuss their threshold values. Moreover, the performance of this infrastructure was not evaluated practically. Nithinet al.[81] introduced combined SM with load management and theft detection (LMTD). A micro-controller was used to detect meter tampering and alert generation for a virtual terminal,i.e., an intermediate terminal between SM and utility server.However, this theft detection relies on the calculation of each appliance’s resistance which is pretty challenging to calculate because it requires too much detailed information about energy consumers at a very fine grain level. Asket al.[82]proposed a mathematical model for AMI, named multifeatured prepaid-postpaid energy meter (MFPPEM), provided by different features. As soon as the system detects abnormal use, it disconnects the energy supply and notifies the utility company through a signal. However, the ETD module of the proposed system only detects meter tampering.
2) Sensor Monitoring/Central Observer (SM/CO):Bandimet al.[83] utilised a central observer meter (COM) for ETD. A COM was used for a group of customers to compare the transmitted energy with the sum of all meters that were linked to it. Then, the deterministic and static approaches (i.e., matrix inversion, singularity matrix, etc.) were used to identify fraudsters. The proposed technique also used pattern recognition to check either meter readings are inside or outside the accuracy class. However, the safety and reliability of the COM were not considered, and lots of simple assumptions were made about the system, i.e., zero resistance of energy cables and linear independence of equations.Devidas and Ramesh [84] introduced another AMI by proposing a complete architecture for energy distribution.Sensors were placed at every transmission line and DS through which the transmitted amount of energy was measured. Then the consumed amount of energy (measured by SM) was compared with the transmitted amount of energy of a transmission line to detect theft. However, it requires the deployment of lots of sensors at different levels, i.e., T&D level, which is very costly and infeasible. Moreover, the main focus of the proposed system is a single-phase distribution system. Yerraet al.[85] proposed a wireless sensor network(WSN) based ETD technique, communicating through the global system for mobile (GSM). The novel ETD algorithm provided real-time monitoring by using the algebraic sum of powers, with the help of sensors that detected theft using a power mismatch between the source and load. They claimed to detect theft on the DS. But the system was not tested, even though simulated. It’s ineffective in a large-scale environment due to high cost. McLaughlinet al.[86] presented an AMI with two complementary intrusion detection systems: the Cumulative Attestation Kernel ensured upgrade, and Network Intrusion Detection System ensured secure working of the meter. They monitored the energy consumption of each appliance by training the system with its signatures and learning from its daily usage. Appliances were clustered with similar loads to increase efficiency. The system detected physical and cyber-attacks with high accuracy and reduced false positive. But it is cost-ineffective as it requires large scale sensors’ deployment and only followed common theft patterns for physical attacks. They extended their work in [87]by modelling it manually and tried to eliminate FPR to increase its credibility. However, manual modelling is too much time consuming and unsupervised learning can not distinguish between home appliances, especially different versions of the same appliance.
Misraet al.[88] utilised learning automata (LA) for multilevel power management architecture at different levels, i.e.,TS, DS, and main grid station. They tried to estimate the required power by learning from the environment and then compared consumed power with the estimated power to find energy theft. All of the appliances, transmission levels, DSs,and grid stations were assigned access code, and energy was provided on the verification of access code. However, in this architecture, the appliances of one house cannot be used in another house or at any other place without changing the access code. Moreover, this architecture only considered a residential area. If there is any delay in demand response from higher node to sub-node, the meter will be declared as tampered. Lo and Ansari [89] proposed a hybrid framework based on the combination sum of energy profiles(CONSUMER) to detect FDI. For this purpose, they proposed a grid sensor placement algorithm (GSPA) and integrated observability analysis to increase the DR. The proposed system was successful to identify FDI, but it was only useful for a single attacker. Lydiaet al.[90] came up with the idea of compressed sensing with a sparse algorithm to reconstruct the sparse information automatically. Their main focus was meter tampering and meter bypassing. They implemented their technique on IEEE 14, IEEE 30, and IEEE 57 bus systems without noise and achieved the DR of 95.05%. But the proposed technique is costly due to the deployment of sensors.Xiaet al.[91] reduced the monitoring devices and reduced the inspection time by proposing an algorithm, named suspicion assessment-based inspection (SAI). The suspicious users with the highest suspicions were inspected at priority and then performed a comparison between their reported and estimated usages. After malicious users, the rest of the users were inspected using a binary tree strategy. The results showed that the proposed inspection algorithm outperformed, but the assumptions were made about the security of installed equipment that could be broken.
Kimet al.[92] proposed a power distribution network (DN)model based on intermediate monitor meter (IMM) along with unit networks (UNs) to divide complex networks into subnetworks, small and independent, for detection of meter tampering and meter bypassing. They formulated energy theft as a linear equation and proposed an algorithm, named IMMbased NTL detection (IND), to solve it. The simulation showed that the proposed model outperformed with the DR of 99.99%. Two other techniques, Lower-Upper Decomposition and Linear Programming, also outperformed. But they lacked in detecting meter bypassing. However, the performance of the proposed technique was reduced due to FDI. Moreover, it is costly due to the deployment of IMM. Komolafe and Udofia [94] proposed overhead radial network-based central station (ORN-CS) for ETD. The SM will transmit voltage,load-profile, and other parameters to the central station. The meter at DS will transmit the details about terminal voltage and the total current of the transformer. It was assumed that the impedance and power loads are constant in the loadprofile. Voltages at the nodes were calculated using Kirchhoff’s current law (KCL) and resistances were calculated using the voltage-current relationship. The authors achieved an accuracy of 94% while detecting fraudulent consumers. However, the authors assumed that the system was theft free at the start. In this way, fraudsters could be considered fair consumers. Choudhary and Bera [95]presented a central control room-based algorithm (CCRA) to locate energy theft withing low voltage DN. At the central control room, the information about energy consumption was collected and passed to the ETD algorithm. So, the actual voltage drop of a fair consumer was calculated across the DN,and then it was compared with the value of voltage sent by the SM. The simulation results showed that the algorithm even detected partial thefts. However, the algorithm was only designed for the low voltage DN, and the authors neglected the change in different parameters due to temperature and other factors, which always affects the voltage drop.
3) Physical Monitoring (PhM):Zenget al.[93] proposed a new method for ETD in street lamp cables, based on the mechanism of open-circuit fault detection (OCFD). A frequency varying current was sent, and resonant frequency and equivalent capacitance of cables were calculated. Depuruet al.[96], [97] proposed the architectural design of SM(ADSM) based on an external control system, harmonic generator, and filter circuit. If the architecture detects 5% of energy theft, it disconnects all genuine customers and operates a harmonic generator to destroy the appliances that are stealing energy. Authors calculated ROI, i.e., 2.42%, which is an acceptable value for the implementation of the system.However, it damages appliances and can be harmful to fair consumers on its failure.
4) Pear-to-Pear:Salinaset al.[98], [99] presented an ETD technique based on the peer-to-peer computation of energy consumption in the neighbourhood. This technique compares the sum of all SM’s energy consumption in a neighbourhood with the total consumption of collectors and finds out the individual honesty coefficient. If the honesty coefficient is unity then the customer is listed as a fair energy consumer.And if the honesty coefficient is greater than the unity, then the customer is listed as a dishonest or fraudulent energy consumer. One of the major key improvements was the preservation of customer’s privacy. The system showed significant success in small size networks, where the size of the neighbourhood was not very large. However, the system is unstable in large size networks due to its higher execution time and it only detects theft if the submitted record is being tampered, i.e., false data is being injected.
5) Linear Parametric Models (LPM):Weckxet al.[100]proposed a linear equation parametric model that compares measured power at substation by summing up all of the consumed power. Though the simulation-based implementation identified double tapping of the feeder.However, this implementation only considered the radial operated DN and the proposed model is not applicable if the length between houses is unknown. Yipet al.[101] presented a linear regression-based mathematical model for the detection of energy theft and defective meters (LR-ETDM),using anomaly coefficient. They enhanced the LR-ETDM categorical variable (CVLR-ETDM) to identify changed cheating behaviour. However, the noise tolerance issue still exists in the algorithm which needs to be solved in order to get accurate results. In their later work [102], authors adopted linear programming (LP) and presented an anomaly detection framework (ADF) for static cheating behaviour and its enhanced version for dynamic cheating behaviour. However,they made many assumptions about the load-profiles which can be violated, and consequently, the detection of fraudsters can be affected. Furthermore, in [122], they constructed a test rig and compared the performance of their proposed techniques where they found that DR of the linear regressionbased model is comparatively less than ADF, but ADF requires more historical data to perform.
6) Mutual Inspection (MI):Xiaoet al.[103] offered a strategy of mutual inspection to avoid repudiation of meter readings in the SG. In this strategy, a meter was installed at the transmission end to inspect each energy consumer. If there will be a difference in both readings of both meters, i.e., meter at consumer end and meter at the transmission line, the consumer will be listed as fraudulent. Though, this strategy helped in detecting meter tampering and line bypass. But it is highly costly because of the instalment of double meters for each consumer. Many environmental assumptions were made during the simulation of the system.
7) State-Estimation (SE):Loet al.[104] presented a DSE based technique, named quasi-real-time search (QRS), for irregular usage of electricity. However, SE contains bad data tat causes inaccurate detection. Guet al.[105] applied the DSE based technique to detect FDI in distributed power systems. The whole complex system was divided into several sub-systems and a chi-square test was used to detect FDI in each sub-system. But the system was tested on a very smallscale and did not discuss the results. One of the key drawbacks of this article is that the authors tried to compare the results of the chi-square test with the proposed technique,but initially, they claimed to use chi-square in the proposed one. Luanet al.[106] applied DSE with the integration of weight dropped polling (WDP) for multiple DN. The estimated value was compared with the actual measurement and if the difference was more than the threshold value, it was listed as energy theft. However, the network’s latency and asynchronous nature of measurements were not considered that can affect the accuracy. Several measurements are required for the proposed method that is a challenging task.Huanget al.[107] exploited an SE based approach to detect bad data injection (BDI). It consisted of three phases: the first phase focused on the theft occurrence criteria, the second phase described customer’s localisation, and the third phase detected malfunctioning meters. A suspect list of customers was created using the analysis of variance (ANOVA) test. The proposed technique successfully identified meter tampering,with a minimised threshold. However, the method is only useful for the individual meter-data anomaly. Moreover, the experience of the specialist was quantified which is itself very difficult. Liuet al.[108] enhanced SE and introduced a novel method, named adaptive portioning state estimation (APSE),to detect BDI. The system was divided into sub-systems,using a graph-based clustering algorithm. It was updated and re-partitioned with detection results to identify bad data. The system was re-partitioned iteratively unless the bad data was located in a specific region. However, it can not identify multiple BDI. Jokaret al.[109] presented the intrusion detection (ID) technique based on the prediction of AMI data.By utilising a statistical model, they introduced long-term and short-term anomaly detection of consumption patterns to detect energy theft. They simulated the proposed technique on four different types of patterns by assigning them different values and achieved an average accuracy of 94.68%.However, to predict energy consumption, an assumption was made that the energy utilisation of most appliances is constant.Moreover, this ETD technique requires granular data to make a more precise prediction.
Sahooet al.[25] aimed to improve the constant resistance TL model (CRTLM). The values of various resistors were calculated for 30 minutes interval, by considering the atmospheric temperature. If the calculated NTL exceeded the threshold, then it was assumed a theft in the user group. The amount of supplied energy from the DS was compared with the amount of consumed energy to detect energy theft and NTL. The experimental results depicted that the minimum detection scenario is that where at least 10% of the total amount of energy is being stolen. However, this requires detailed topological information about the primary and secondary network. Moreover, the technique was tested only on a small dataset generated through the simulation. Liu and Hu [110] leveraged partially observable Markov decision process (POMDP) and Bollinger-bands to empower long-term detection. To increase efficiency, thy integrated belief-statereduction based adaptive dynamic-programming (BSR-ADP).But mismatch and the average bill increase was slightly greater than without state reduction. The performance of the presented system was not constant while testing on different types of datasets. Liu and Li [111] examined an imperfect FDI attack when there are uncertainties about the network information. However, it was not addressed analytically or statistically that why an incomplete or an imperfect attack will be succeeded. There were lots of relaxations that were given to the attacker and results were inconsistent when there was a small attacking region. Rossoniet al.[112] identified TL &NTL by using hybrid state estimation (HSE) approach. This method was divided into two-steps WLS-SE. First, the detection, identification, and correction of NTL through a geometrically based state estimator. Second, pattern recognition to detect and estimate energy losses with the help of the weight matrix. Once the energy losses were detected,the weight matrix was updated accordingly. The test validation found this method efficient. Kazemiet al.[113]proposed two steps secure hybrid DSE (SHDSE) technique to identify FDI in power systems. An unknown input observer(UIO) makes initial estimates and helps to extract a dynamic model, describing the FDI attack vector, augmented with the system. Then, the Kalman filter (KF) was used for the combined estimation of the system states and the attack vector.
C. Game Theoretic (GT) Techniques
GT techniques are not popular for ETD. In these techniques,a game is played between customers and utilities, to identify energy theft.
1) Static Game Theory (S-GT):Cárdenaset al.[114] came up with a GT technique to detect energy theft. In their method,they established normal consumption patterns of consumers and made an estimate about upcoming consumption patterns.If the normal consumption of a consumer deviates from an estimate consumption pattern then that consumer was listed as a fraudulent consumer. Though they tried to preserve consumer’s privacy by utilising a limited amount of sample,which was enough to identify theft. However, the system was developed by making lots of assumptions and it lacks realistic demand-response constraints. Moreover, the system is only applicable to a single utility source and a single consumer.
2) Dynamic Game Theory (D-GT):Liuet al.[115] proposed a dynamic programming-based algorithm for the detection of energy theft for multiple users. The proposed algorithm was iterative and was used to schedule the home appliances independently in each iteration. Real-time pricing and guideline pricing were used. After each iteration, the energy consumption information was shared among users and they rescheduled their appliances to reduce monetary cost. The results of the simulations showed a reduction in monetary cost by 29%. However, they assumed fixed consumption of home appliances and scheduling completely relied on the ordering of appliances. Once an appliance is ordered, its order can not be optimised anymore. Linet al.[116] discussed microdistribution systems (MDS) and presented a non-cooperative game-theory model (NCG) to identify NTL. The probability of normal behaviour, likely fraud, and serious fraud was calculated using a decision model, based on NCG. Aminet al.[123] introduced another GT model to address, diagnose, and solve electricity rigging via cyber or cyber-physical, i.e.,installation of rigging meter or other sensors. The environments of perfect competition and unregulated monopoly were considered. ETD can be performed by observing usage behaviours, i.e., analysing expected and actual behaviours of both, the fair and fraudulent consumers.However, the proposed model was based on assumptions about fraudulent behaviour. Weiet al.[117] proposed a distributed intelligent framework for electricity theft detection(DIFETD) where they used Benford’s law and stackelberg game and detected electricity theft by performing maximum likelihood estimation (MLE). They enhanced the typical GT model and enhanced to facilitate a game between single utility and multiple customers. The likelihood ratio test (LRT) was performed to detect fraudulent customers on the base of the sampling rate and threshold. Though the simulation depicted that the DR of the proposed technique was 95%. However, it was tested with a very small dataset where the theft attacks were not realistic.
V. COMPARATIVE ANALYSIS OF ETD TECHNIQUES
A. Intra-Category Comparison
We have classified existing state-of-the-art ETD techniques in three categories, i.e., DM, S&N, and GT. The DM techniques require fine-grained load-profiles of the consumers to perform classification for fair and fraudulent consumers.The collection of labelled data is very hard because it is mainly required for the classification techniques. The execution time or time complexity of these techniques is pretty much high, as well as they require more resources (i.e.,processing and memory). The S&N techniques require detail information about the network topology. These techniques can be validated through simulation but they are not feasible in real environment because the topological information is not available easily. Though these techniques are efficient in terms of time and resources. But their real-time implementation is a big question. Moreover, these techniques can not be useful for the preservation of consumer’s privacy because the topological variables can not be aggregated. The GT techniques are not used widely for ETD in SG. One of the main reasons behind the in-applicability of GT techniques is that it is very much difficult to capture the actual environment as a game between service provider and service consumers.Because the theft attacks are not completely known to the utilities. There might be several unknown theft attacks through which the consumers steal energy. Then, unknown attacks can never be modelled while capturing the real environment. Hence, when there is a need to select the appropriate ETD technique in SG, one must go through the trade-off between certain parameters. If all of the required parameters of load-profiles are available and utility have enough time to perform theft detection, then they can surely go with the DM techniques (especially with classification techniques as they have less FPR than clustering). And, if utility have enough investment for the deployment of AMI network and have detail topological information of all customers, then they can go with the S&N techniques. In both type of techniques (i.e., DM or S&N), the detail information is mandatory, i.e., load-profile parameters for DM and topological parameters for S&N. But, there is major trade-off between cost & time. If utility have enough time to spend on the detection and it wants to save the money, then it can go with the DM techniques as they are less costly. But, if the utility is short of time and have enough amount of money to spend,they it can go with the S&N techniques as these techniques are more costly because of deployment of AMI network.
B. Inter-Category Comparison
Where all of the ETD techniques detect energy theft, there are also some drawbacks that are attached to all of them. The different architectures, models, and algorithms, used for ETD,lack in certain conditions. The performances of all of the ETD techniques vary in different circumstances and environments.A brief discussion about performance and limitations is given below for all of the classes in which those techniques are classified.
1) Comparison of DM Techniques:DM techniques are broadly used for ETD and their performances are improved with the passage of time. They successfully detected meter tampering and meter bypassing with a significant DR.However, they are unable to detect a communication attack’s vulnerability. Historical data is not available in all cases, so clustering techniques can be applied as they do not require any labelled data. However, clustering techniques require more execution time than classification techniques because they are involved in iterations to sub-divide the system into subsystems.
Classification based ETD Techniques: Various classification techniques have been discussed for ETD. The performance comparison of all those techniques is given in Table IV. It can be found that OPF is the most popular method used for the classification of fair and fraudulent customers. A regression analysis based SVM is the second most popular technique which was used for the classification of energy consumers. The DR is the most widely used parameter to measure the performance of classification techniques. The minimum DR is 60% which was given by one of the initial SVM based methods [38], and the maximum DR is 98.93%which was given by OPF with the integration of PSO [57].However, most of the classification techniques yielded the DR of approximately 90%–100%. Some of the authors used the parameter of FPR to evaluate their performances and few authors also used Recall and F1 Score. However, it can be observed that only four classification techniques considered the PP, which is one of the key drawbacks of classificationtechniques.
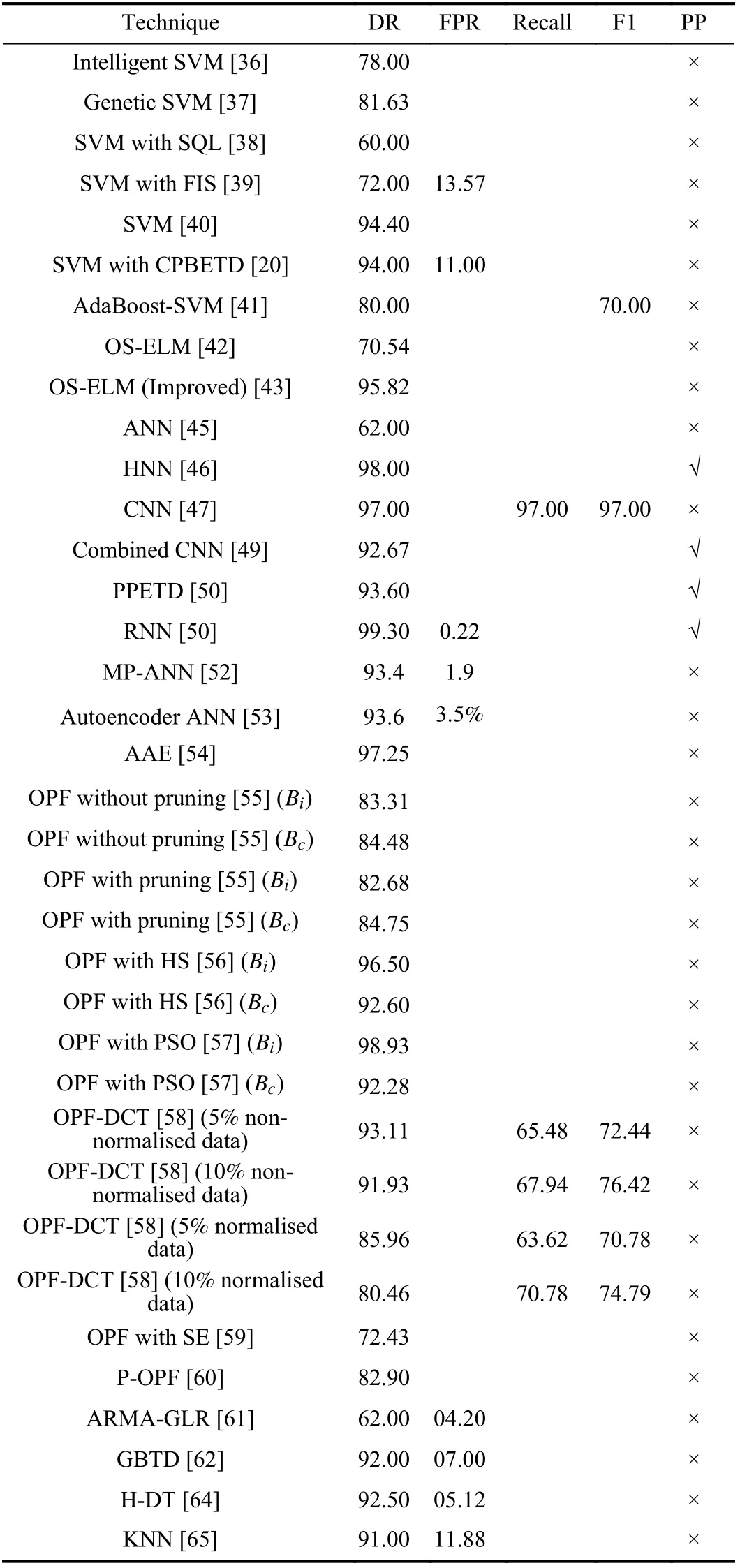
TABLE IV COMPARISON OF CLASSIFICATION BASED ETD TECHNIQUES
Following are the limitations of classification techniques:
● The DR is limited due to a lack of consumption data as historical data is required to train the classifiers.
● There are such algorithms which can generate very low fake measurements that can not be captured by the classification algorithms (i.e., feed-forward neural networks,recurrent neural network, and CNN) [124].
● Historical data is imbalanced which means that the number of data about fair consumers and the number of data about fraudulent consumers is not the same. Mostly, the data about fraudulent consumers is not available. So, it is very difficult to train the classifiers specifically for fraudulent consumers.
● The granular data is not available all the time.
● In many cases, there are zero-day attacks that are not detected yet. So, there is not any historical data about them.
● Mostly, classification techniques lack in detecting FDIs or Cyber thefts where the consumption patterns can be altered with malicious, i.e., cyber-attacks.
● The non-malicious factors can also impact the consumption patterns such as change of appliances, change of residents, special occasions and events, seasonality, etc. During the generation of consumption patterns, if these factors are not identified and utilised properly, the FPR can also be increased and the classifier’s accuracy can be decreased as well.
● Meter bypassing cannot be detected from those energy consumption patterns which are abnormal.
● The computational cost of SVM increases rapidly with the increase in the training dataset. If there is a need to classify consumption patterns into multiple classes then multiple sport vectors are required because SVM is a binary classifier.
● The parameters, which are required to train SVM, are many and evolving from time to time. So, it is very difficult to train SVM with such kind of data.
● In ANN, a number of required neurons and the number of iterations are complicated, as well as complex too, because they are application dependent.
Clustering-based ETD Techniques: The research community is not much interested in unsupervised ML methods to detect energy theft. The performance comparison clustering techniques is presented in Table V which depicts that the DR of the clustering technique is comparatively higher than classification techniques. The DR shows that DBSCAN based techniques outperformed fuzzy c-means and k-means clustering. However, it can be observed that the clustering techniques gave a much higher FPR than classification techniques, which reduces the credibility of clustering algorithms for ETD. Moreover, the performance of these techniques can not be bench-marked because they are highly dependent on the dataset and type of attack. As the dataset and type of attack changes, the performance deviates significantly,as shown by Singhet al.[73], [75]. None of the clustering technique considered preservation of user’s privacy, while detecting energy theft.
Above, in TableV, AT stands for Attack Types, AM stands for Arithmetic Mean, GM stands for Geometric Mean, THD stands for Threshold Dependent, ISSDA stands for Irish social science data archive, and S, M, and L stands for Small,Medium, and Large, respectively.
Following are the limitations of clustering techniques:
● None of the clustering techniques considered the privacy of customers, which is one of the key drawbacks of these techniques.
● The calculation of the neighbourhood’s radius is nontrivial in traditional DBSCAN methods.
● It is very difficult to infer about features, affecting consumption patterns, through fuzzification.
● The number of attributes is not the same in all cases, i.e.,historical data.
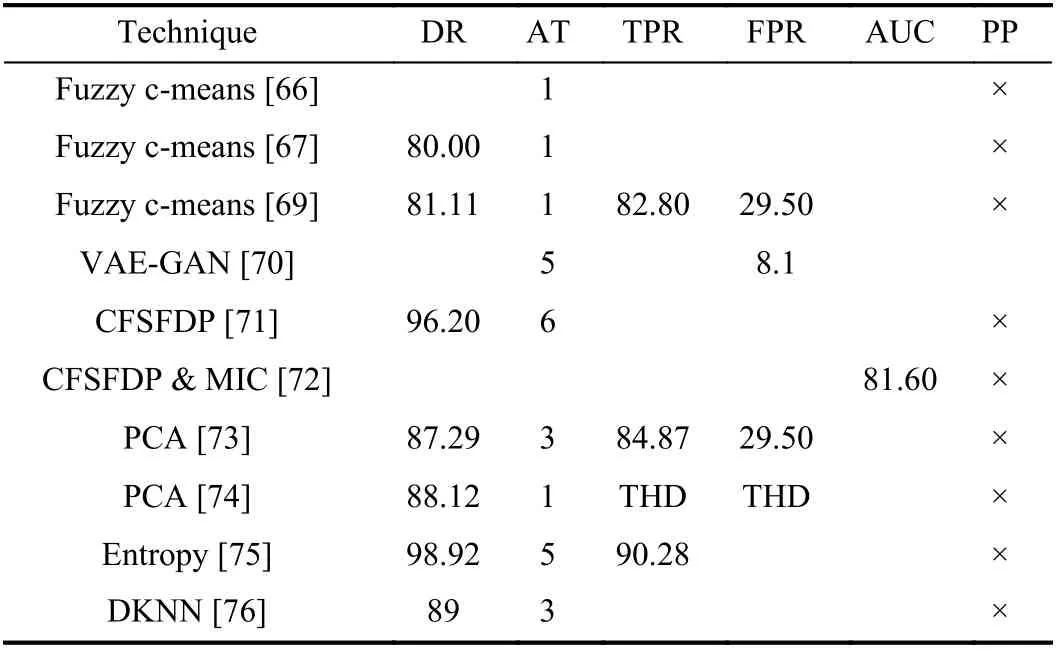
TABLE V COMPARISON OF CLUSTERING-BASED ETD TECHNIQUES
● Clustering techniques are unable to identify BDI and cyber-attacks.
● The execution cost of clustering techniques is high because of their iterative nature.
2) Comparison of S&N-Based Techniques:After the DM techniques, S&N-based techniques are the second most used technique for the detection of energy theft. The comparison of S&N-based techniques is shown in Table VI. It can be observed that the DR of these techniques is comparatively higher than DM techniques. However, there is not any single parameter that is used by all of the S&N-based techniques.Since there is the deployment of sensors and network protocols, so some of the authors evaluated the performance of their proposed techniques by evaluating deployment cost and ROI. However, all of the authors did not consider this aspect to evaluate performance. Moreover, these techniques also considered the privacy of customers more than DM techniques.
Some of the authors used totally different parameters to evaluate the performance of their proposed technique such as Salinaset al.[99] evaluated deployment time, Xiaoet al.[103] used accountability, false alarm rate, and system overhead. Some of the studies also tried to examine their proposed techniques for the minimum amount of identity theft. Sahooet al.[25] successfully identified energy theft when there is at least 10% theft data and Luanet al.[106]found their proposed technique working when 2% of theft data is present in the whole dataset. However, there are lots of S&N-based techniques that did not evaluate their proposed infrastructures and techniques to validate and verify their credibility.
Following are the limitations of S&N-based techniques:
● They require detail topological information about the primary network and as well as secondary network to find out the energy theft, which is not available all the time.
● Some extra investment is involved in SE techniques such as device cost, software and system implementation cost,training and operational cost for the monitoring of the system.
● In SE techniques, fine-grained load profiles are collected by the operators which violate the privacy of customers. It requires some additional steps to overcome this issue which iscostly.
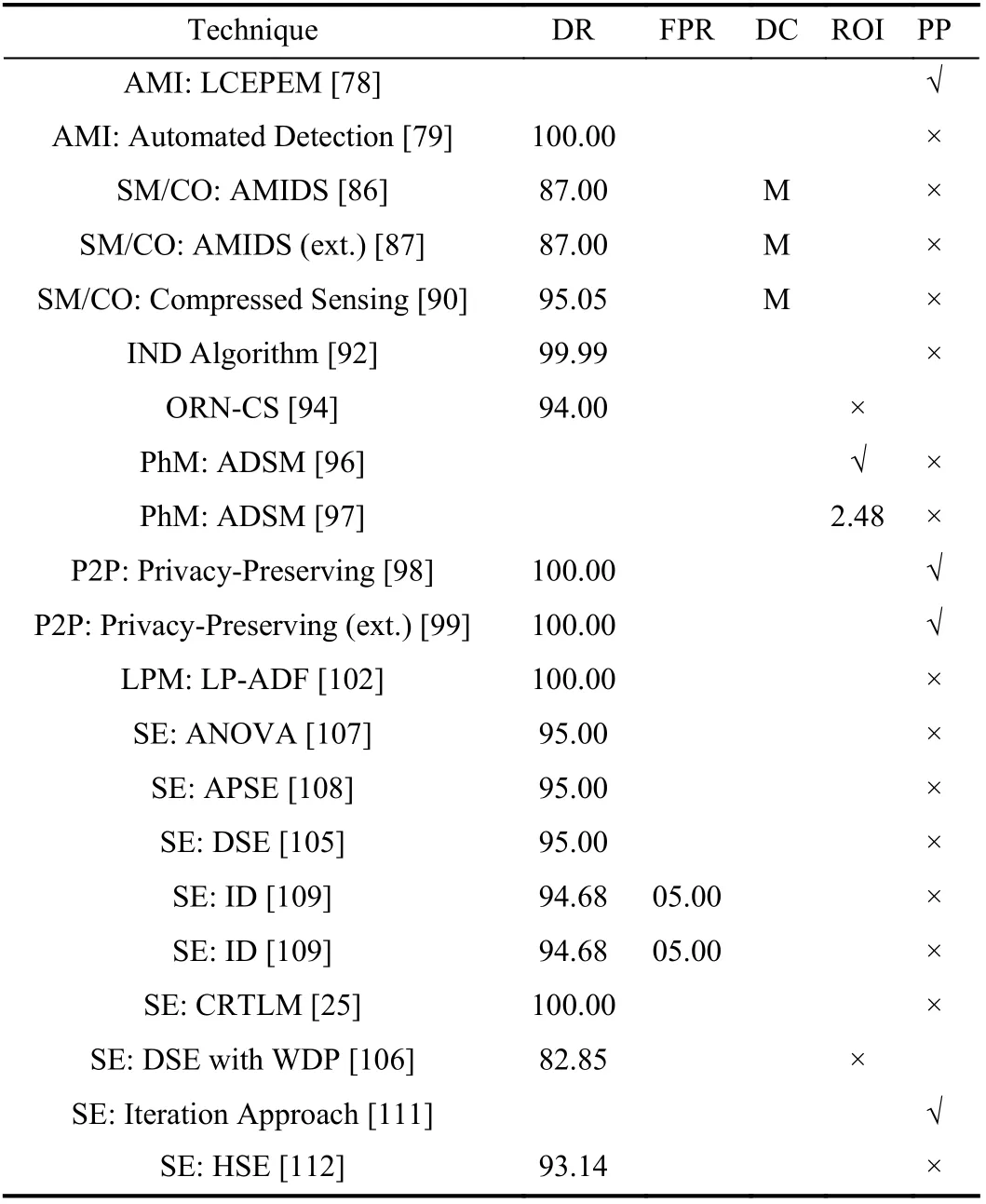
TABLE VI COMPARISON OF S&N-BASED ETD TECHNIQUES
● Where the WSNs are used for the monitoring of customers and detection of energy theft, it also opened new doors for cyber-attacks as well as fault disturbances.
3) Comparison of GT based ETD Techniques:GT models are not widely used for ETD that is why very few studies were found in the literature. The performance comparison of GT techniques is given in Table VII. It can be observed that there is not any common attribute, used by the authors for performance evaluation. Only one study [117] evaluated through DR which was widely used by DM and State and Network-based techniques. One GT technique [114] also considered privacy preservation, but it was a static technique which only considered one customer at one time. None of the GT-based ETD techniques was verified with the realistic dataset. They did not address the real-world complexity of interactions between customers and utility.
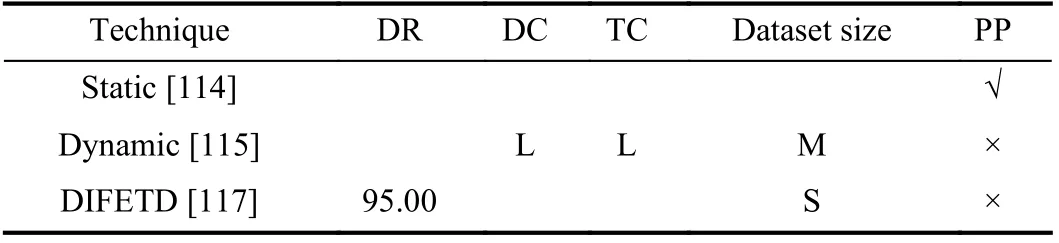
TABLE VII COMPARISON OF GT BASED ETD TECHNIQUES
VI. DISCUSSION
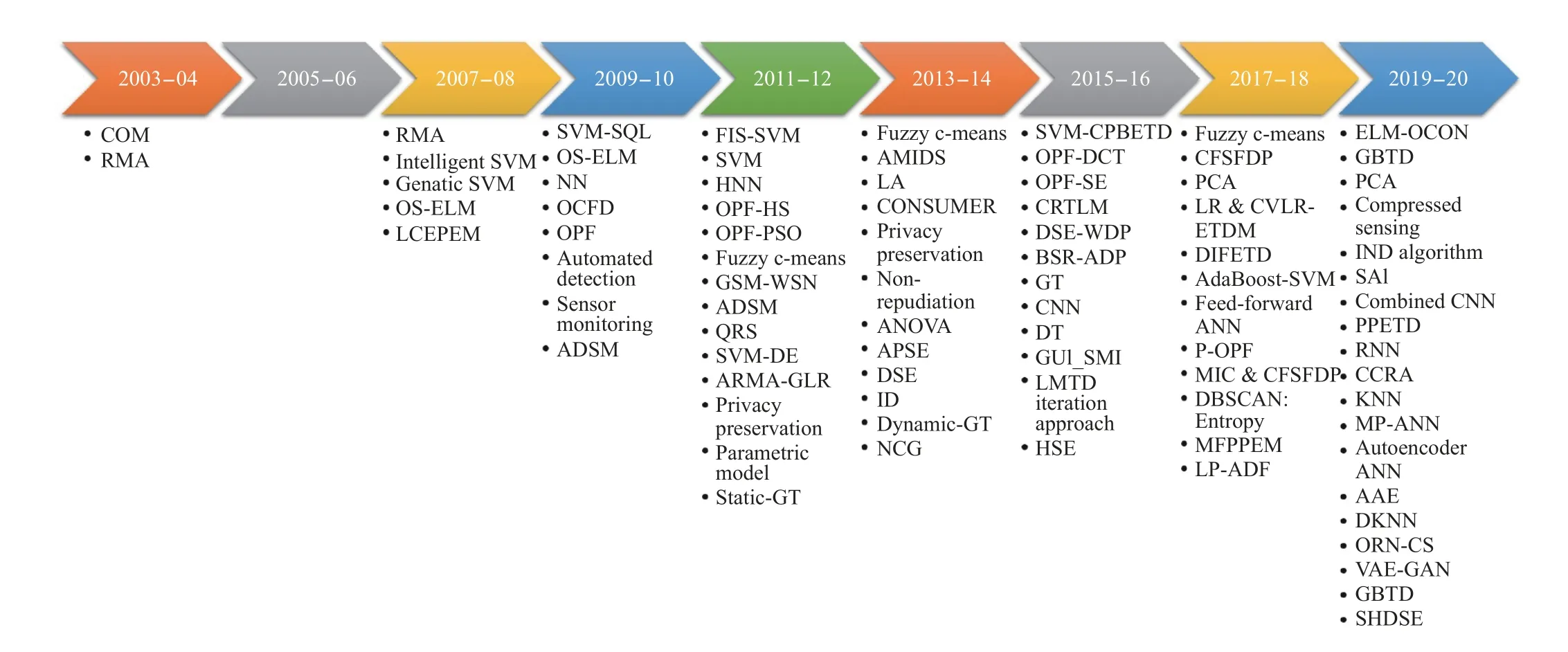
Fig. 3. Timeline of ETD Techniques.
We have analysed different ETD techniques deeply and designed a new taxonomy to classify those techniques. We also identified the trend of the research community by observing their interests. The classification of ETD techniques itself depicts that where the interest of the research community lies. A timeline (from 2003 to 2020) is presented in Fig. 3 where the ETD techniques are mapped against the years, in which they were introduced. Years are plotted on thex-axis while the ETD techniques are plotted on they-axis.Initially, it could be observed that S&N based techniques were only the main focus of the researchers. In 2008, researchers’trend diverted towards DM techniques because of the emergence of efficient machine learning algorithms. But, after 2011, researchers found that the FPR of machine learning algorithms is considerably higher than the others. So, S&N based techniques again got researchers’ attention. In DM techniques, firstly, SVM was mainly utilised for the classification of fraudulent customers and after that researcher’s interest was diverted towards ANN and OPF. In S&N based techniques, SE is widely used for the detection of fraudulent customers. One of the main reasons behind the popularity of SE techniques is that it can detect FDI that is done through cyber-attack. Initially, the complete frameworks for SG were proposed in 2003. The main issues with those frameworks were complexity, safety, reliability, and the lack of testing and deployment.
Later on, in the years 2004–2007, authors tried to resolve these issues but the problem was that the data was collected at large intervals, i.e., monthly intervals. Due to these large intervals, the authors were only able to detect the months in which the theft occurred. Moreover, there was physical involvement in the inspection. After that, in 2008–2009, ML techniques were introduced to classify fair and fraudulent consumers. But, due to the unavailability of labelled data and features of load-profiles, average consumption patterns were assumed. Then, in 2010–2011, the sensors-based techniques were used to detect real-time energy theft but their cost prevented their deployment. They were cost-ineffective and there was a possibility of damage to the home appliances due to harmonic instruments. Some researchers also tried to solve the issue of labelled data and proposed algorithms to extract features of consumption profiles. In 2012, different authors proposed network-based techniques in which the main problem was the unavailability of detailed network information. The authors also tried to overcome the issue of PP. They were specifically limited to common types of energy attacks, and solutions were unstable in large networks. A GT technique was also proposed but that was static and based on many assumptions that could be violated. The S&N based techniques, proposed in 2013–2014, tried to overcome the issues faced by previous techniques but they lacked in certain things. First, they involved in manual modelling which is time-consuming. Second, they were dependent on a single source and consumer to detect energy theft, and only detected individual anomaly. Instead of harmonic instruments, they used non-linear load which can also be harmful to the appliances as it can change the characteristics of the current. A D-GT technique was also introduced to overcome the static techniques, but assumptions still existed.
Along with the S&N, in 2015, some classification-based work was also observed that focused on feature extraction.But there was inconsistency due to manual data collection.S&N based techniques faced latency issues and security challenges. In 2016–2017, the DM techniques collected data of smaller intervals, i.e., 5 minutes, but faced memory optimisation issue. Still, the assumptions were made for some features and only considered simple attack patterns due to imbalanced datasets. On the other hand, S&N based techniques still faced the problem with the availability of topological data. Another D-GT technique was proposed to overcome the assumptions, but it was tested with a limited amount of dataset. Recently, the authors tried to solve the problems of feature extraction and assumptions about the features, with the help of DM techniques, by handling an imbalanced dataset. They analysed the components iteratively and extracted them on the base of their importance. But the iterative fashion increased TC and performance was inconsistent for different datasets. This could be due to the threshold that was derived only from the historical data. The S&N based techniques also tried to overcome the issue of topological data by decomposing the network and point out the theft iteratively. But, it also increased the TC and DC considerably due to compressed sensors, and still unable to detect FDI attacks.
Dataset Bench-marking: We observed that there are different types of ETD techniques, i.e., DM techniques, S&Nbased techniques, and GT-based techniques. So, they require different types of datasets for their implementation. E.g., DM techniques require consumer’s load-profiles to detect energy theft, whereas the S&N-based techniques require detailed topological information. So, it is impossible to benchmark a single dataset for all ETD techniques. But, a single dataset could be used as a benchmark inside a single type of ETD technique, i.e., an open-source dataset of consumer’s load profiles could be bench-marked for all DM techniques.Though some open-source datasets are available for everyone,such as data from the Irish commission for energy regulation(CER) [125]. This dataset is used by [50], [52], [62], [69],[71]–[75] However, authors did not follow it and they used the datasets that were available for them.
VII. CHALLENGES AND FUTURE DIRECTIONS
We identified a set of challenges in the field of ETD that could be helpful in future. Besides performance and accuracy,we believe that privacy issues also need serious considerations in future studies in this domain.
● High False Positive Rate:The FPR of most ETD techniques is high that reduced their credibility. There are various factors behind high FPR, such as big data, class imbalance, feature description and selection, and some other non-malicious factors [126]. Only a few classification techniques provided a comparatively low FPR than other DM,S&N, and GT techniques. Especially, the FPR of clustering techniques is much higher than all of the others. Hence, the research community should design or adopt such strategies for ETD that consider the FPR, and bring it down to increase the credibility and reliability of ETD techniques.
● Feasibility Analysis:Another challenge, that is preventing the deployment of ETD techniques, is their feasibility, i.e., analysis of its cost and ROI. The ROI is performed only in very few studies to find out either the deployment of the ETD technique is feasible or not. However,most of the studies lack in the feasibility analysis, and did not give a complete view of the output of the proposed technique.
● Theft Intervals Identification:After detecting fraudsters,it is a challenge to detect the theft intervals in which he stole energy from the utility. Once the interval is detected, the utility can charge him accordingly. To our knowledge, Wuet al.[41] only presented a GRNN to identify such intervals.However, the authors only identified the months in which a customer committed fraud which is not a good approach. It is possible that a customer only stole energy once a month, but he will be listed as fraudulent for a whole month. There is a need to detect theft intervals with a minimised value. This could be done if the consumption patterns are recorded for small intervals, by keeping track of the consumers.
● Energy Theft Tracking and Prevention:It is a wellknown phrase that “prevention is better than cure”. Many of the ETD techniques provided solutions to detect fraudulent customers, but very few of them tried to keep track of fraudulent customers to prevent theft in the future. Only Fernandeset al.[60] provided this mechanism but they lacked in the multi-class classification of fraudulent customers. Here,a good knowledge management technique could be implemented to track and prevent energy theft in the future.
● Privacy Issues:Privacy of customers is one of the main obstacles which prohibit the implementation of AMI. The deployment of SG infrastructure opened doors for cyberattacks [127]. If the utilities fail to provide complete security to their customers, the customers will avoid accepting their infrastructure, as well as services. The insufficient protection against cyber-attacks could cause great damage, as explained and demonstrated in Ukrain regional grid [128]. Till now,there are very few ETD techniques that addressed privacy preservation. Mostly, the data aggregation techniques have been widely used for privacy preservation which requires finegrained data of consumers [129]. However, the researchers mainly focused on improving the DR of their proposed techniques, while working on ETD. It is also observed that the privacy preservation techniques are costly due to the requirement of high computational resources. So, there is a strong need to consider privacy preservation in ETD techniques, as well as their cost.
VIII. CONCLUSION
ETD is one of the most complex and critical problems in AMI. This is because, on the one hand, the enhancement in technology helped utilities to monitor the customers, it also provided directions to fraudulent customers to steal energy with new attack methods. The fraudsters are evolving with evolving technologies. The theft detection became more and more complex with this rapid enhancement of AMI. Different ETD techniques only focused on the specific type of attack method. There is not a single ETD technique that is capable to handle all types of theft attacks. If one technique handles meter tampering and bypassing, then it lacks in the identification of FDI. If it tries to handle the cyber-attacks,then it leaves the door for billing irregularities by utility’s personnel itself. Among different challenges, faced by the research community and utility companies, the customer’s privacy is the key challenge that needs to be handled carefully. In this paper, we have performed a survey in which we have investigated the existing state-of-the-art ETD techniques. We classified them as DM, S&N, and GT techniques and explored them in detail with the help of subcategories. We performed a detailed comparison to find out the outperforming ETD technique. We also listed their challenges and future direction for the research community.
 IEEE/CAA Journal of Automatica Sinica2022年4期
IEEE/CAA Journal of Automatica Sinica2022年4期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- On the System Performance of Mobile Edge Computing in an Uplink NOMA WSN With a Multiantenna Access Point Over Nakagami-m Fading
- Continuous-Time Prediction of Industrial Paste Thickener System With Differential ODE-Net
- Unmanned Aerial Vehicles: Control Methods and Future Challenges
- A Braille Reading System Based on Electrotactile Display With Flexible Electrode Array
- A Short-Term Precipitation Prediction Model Based on Spatiotemporal Convolution Network and Ensemble Empirical Mode Decomposition
- A Sandwich Control System with Dual Stochastic Impulses
