A Lightweight Three-Factor User Authentication Protocol for the Information Perception of IoT
Liang Kou, Yiqi Shi, Liguo Zhang, Duo Liu, and Qing Yang
Abstract: With the development of computer hardware technology and network technology, the Internet of Things as the extension and expansion of traditional computing network has played an increasingly important role in all professions and trades and has had a tremendous impact on people lifestyle. The information perception of the Internet of Things plays a key role as a link between the computer world and the real world. However, there are potential security threats in the Perceptual Layer Network applied for information perception because Perceptual Layer Network consists of a large number of sensor nodes with weak computing power, limited power supply, and open communication links. We proposed a novel lightweight authentication protocol based on password, smart card and biometric identification that achieves mutual authentication among User, GWN and sensor node. Biometric identification can increase the nonrepudiation feature that increases security. After security analysis and logical proof, the proposed protocol is proven to have a higher reliability and practicality.
Keywords: Authentication, biometrics, smart card, multi-factor.
1 Introduction
Nowadays, IoT (Internet of Things) is gaining widespread attention from governments,enterprises and academics for several reasons. IoT First of all, the IoT is an important part of the new generation of information technology and plays a catalytic role in social development. Second, the application of the IoT will have enormous economic benefits.According to the estimation of relevant experts, the output value of the IoT will reach one trillion level. The Internet of things is mainly composed of perception layer, transport layer and network layer [Sathishkumar and Patel (2014)]. In this paper, we mainly consider the protection of perception data and regard the wireless sensor networks(WSNs) as the perception layer of the IoT. WSNs are the network that consists of large number of sensor nodes in a self-organized manner. The sensor nodes have the following characteristics, such as limited battery capacity, simple CPU, small storage and communication capability which cause the sensor nodes to suffering from various attacks in hostile environment [Lin, Zhu and Zheng (2017); Wu, Yan, Wang et al. (2017)].
There are usually two methods for users to access the perceptual data collected by sensor nodes. One is that the user sends query instructions through the WSNs base station or gateway node, and then gets the perceptual data by the corresponding node. The security of this method is guaranteed by the security strategy of WSNs itself and it suffers from large time delay [Das, Sharma and Chatterjee (2012); Qazi (2004)]. The other is that user obtains the real-time data directly from the sensor nodes independent of base station or gateway node. This method has high real-time performance and is suitable for all kinds of real-time applications, but this method needs to consider the legitimacy of the user's identity in particular.
Identity authentication plays a very important role in ensuring that only legitimate users can access resources or services, and key agreement can guarantee that only legitimate communicators can obtain correct communication content. Due to the poor computing power of sensor nodes, traditional security protocols that require large computing power cannot be directly applied in wireless sensor networks. Therefore a lightweight security protocol is needed to secure the WSNs.
The user authentication protocols mainly compose of two-factor user authentication(based on the password and the smart card) and three-factor user authentication (based on two-factor authentication combined with the biometric factor). Practice has proved that three factor biometric-based user authentication is more secure than two-factor user authentication. Biometric identification has the following advantages in the field of user authentication, so it attracts much attention from experts and scholars [Qazi (2004)].
● Biometric identification will not be lost or forgotten;
● Biometric identification is not easy to be replicated;
● Biometric identification is not easy to be forged or distributed;
● Biometric identification is not easy to be guessed.
At present, security solutions to deal with hostile attack in WSNs mostly focus on key management, authentication and secure routing [Balakrishnan and Rino (2016); Amin and Biswas (2015)]. Two-factor authentication [Das, Sharma and Chatterjee (2012); Fan,Ping and Fu (2010); He, Gao and Chan (2010); Khurram and Khaled (2010); Lee, Li and Chen (2011)] combining password and smart card is a common solution for researchers,but two-factor authentication is still not reliable because smart cards are easy to lose and the password is also easily guessed by an attacker. He et al. [He, Kumar and Chilamkurti(2014)] devised a mutual authentication and key agreement scheme based on temporal credential, which can effectively deal with the simulated attacks on user or sensor node,offline password guessing attacks and user anonymous attacks. Their scheme can be put into practical applications in WSNs. However, this solution cannot satisfactorily certify after tracking attacks, insider attacks and identity guessing attacks. In order to solve the above problem, Jiang et al. [Jiang, Ma and Lu (2015)] proposed a linkless enhanced authentication strategy. They took full account of the sensor node's burden and reduced the energy consumption while defending against a series of security threats. Later, They designed a privacy-aware two-factor authentication scheme based on the research results of elliptic curve cryptography (ECC), which took into account the efficiency of WSNs and the safety features in a variety of environments [Jiang, Kumar and Ma (2016)]. Amin et al. [Amin and Biswas (2015)] improved the sensor network architecture and designed a low-energy user authentication and key agreement scheme to achieve two-way authentication, dynamic addition of nodes and password updates, which has improved the session key protection. Choi et al. [Choi, Lee and Kim (2014)] uses a heuristic analysis method and an ECC to improve a user authentication protocol that can reduce the energy consumption of WSNs and provide mutual authentication and key agreement between users and sensors. It can also resist session key attacks and sensor energy exhaustion attacks. In Sahingoz [Sahingoz (2013)], the author presented a key management framework for distributed WSNs that share the keys between sensor nodes and their neighbors. In addition, they used UAV as a management center of asymmetric key to achieve a multi-level dynamic key management. Three-factor user authentication based on biometric [Park and Park (2016)] in the WSNs shows the superior to traditional twofactor user authentication schemes. In this paper, we provide a new user authentication protocol for WSNs using smart card combining with biometric identification. The proposed authentication protocol should achieve these goals: (1) mutual authentication between the user and the sensor node; (2) anonymity: the attacker cannot get the user's identity; (3) session key generation: after the authentication procedure, a session key should be generate shared by the user and the sensor node; (4) GWN does not store the registered user's password and biometric template; (5) attack resistance: the protocol should be robust against a variety of attacks; (6) password update offline. The proposed protocol is lightweight and superior than the exiting protocols on the computational complexity. The security of the proposed protocol is proved by BAN-logic.
The remainder of the paper is organized as follows. In Section 2, we present the related work of user authentication. In Section 3, we review the Althobaiti's protocol and analyze the security vulnerability of Althobaiti’s protocol. In Section 4, we describe our proposed new user authentication protocol for WSNs. In Section 5, we perform the security analysis of our scheme by BAN-logic and compare the performance with the existing protocols. In Section 6, we conclude our research.
2 Preliminaries
2.1 Attacker threat model
In order to conduct security analysis of the Althobaiti’s protocol and our proposed protocol, we make use of the Dolev-Yao threat model [Ramanujam, Sundararajan and Suresh (2014)] and its improved model [Kim, Lee and Jeon (2014)]. In the unsecured open communications, the attacker has the following abilities:
● An attacker can gain all the messages transmitted over a public channel;
● An attacker can impersonate other communication entities to send messages to users;
● An attacker cannot get correct random number;
● An attacker cannot decrypt the message without the correct key;
● An attacker cannot crack the encryption algorithm;
● Once an attacker steals the user’s smart card, he can get all the information stored in the card;
● The ID and password of the user are usually low-entropy;
● An attacker cannot crack the encryption algorithm;
● The gateway node cannot be compromised.
2.2 Fuzzy extractor
Due to the fact that various of noises can lead to the failure of the biometric information acquisition, a fuzzy extractor method [Dodis and Reyzin (2004)] is proposed to extract the correct data with a given error tolerance. A fuzzy extractor method mainly contains two functions:Gen(·)and Rep(·)( )(R,P)BIO
Gen =
Rep( B IO')=RifBIO is similar to BIO'within a predefined threshold.
The function Genmaps the input biometric information to a secret string R∈{0,1}land auxiliary informationP. The functionRep can reproduce theRwith the auxiliary informationPandBIO'which is similar toBIOin some degree.
2.3 Notations
The notations used throughout this paper are described in Tab. 1.
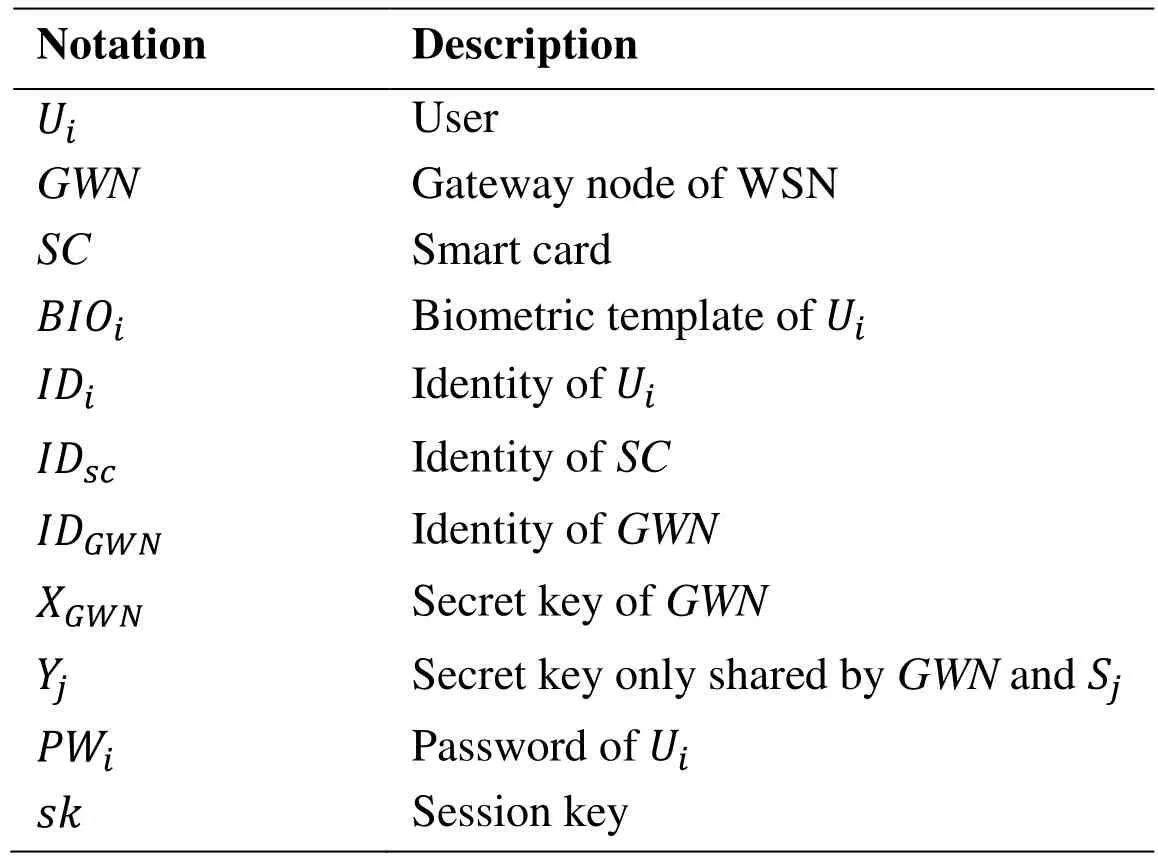
Table 1: Notations and parameters
3 Review of Althobaiti’s protocol
In this section, we review Althobaiti et al.’ user authentication protocol [Moreover and Section (2013)]. The notations used in the paper are listed in Tab. 1. Althobaiti’s protocol takes advantage of the biometric identification to enhance security and it includes three processes: registration phase, login phase and authentication phase.
3.1 Registration phase
When the new user Uiwants to access the perceptual data collected by the sensor node Sj, he needs to register to theGWN firstly. The Registration Phase of user Uiincludes the following procedures:
● TheGWN selects and saves a random key ekifor the new user Ui;
● The user Uiinputs his identity identification IDiand biometric information BIOi.Then computes BE = h( Bi) ⊕ekiand storesBE in the device of Ui;
● TheGWN calculates Fi=h(IDi⊕X), and send the message {I Di,Fi}to the Uivia secure channel;
● The Uistores the data {IDi,Fi,h(eki),BE}.
3.2 Login phase
The login phase of user Uiincludes the following procedures:
● The user Uiinputs IDiand BIOiand calculates N=h(Bi),eki'= BE⊕h(Bi);
●Uicalculates h (e ki')and verifies if h( e ki')= h(e ki). If yes,Uisends the login request message{I Di,request}toGWN. If no, it terminates the operation.
3.3 Authentication phase
The authentication phase realizes mutual authentication between user Uiand sensor node Sj. A detailed description of this phase is as follows:
● AfterGWN receives the message {I Di,request},GWNsends a authentication request{R}whereR selected randomly to Uias the login response. After Uireceives{R},Uiperforms the encryption {R ,T1}→ Eeki{R ,T1}based on the key eki, where T1represents the timestamp of Ui.Uisends the authentication request message Eeki{R ,T1}toGWN via public channel.
●GWN receives the message Eeki{R ,T1}at T2and decrypts the message to acquire the Deki{R,T1}according to eki. ThenGWN verifies if≤ ΔT. If no, it terminates the operation. If yes, sensor nodeSjresponses to Ui.
●GWN calculates
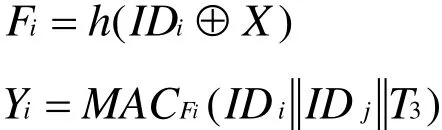
where,T3represents the current timestamp ofGWN.GWN sends the message{I Di,Yi,T3}via public channel.
●Sjreceives the message {I Di,Yi,T3}at T4.Sjverifies if≤ ΔT. If no, it terminates the operation. If yes, it calculates the following equations:
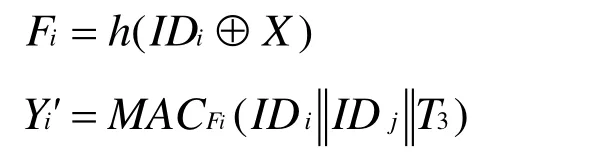
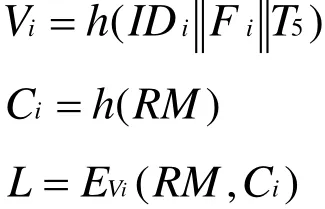
●Uireceives the message {L ,T5}at T6and verifies if≤ ΔT. If no,Uiterminates the operation. If yes,Uicomputes the following equations:
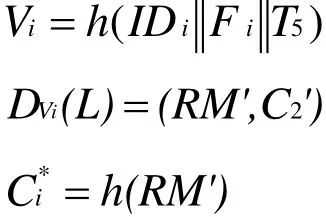
4 Security analysis of Althobaiti’s protocol
Althobaiti’s protocol is a typical light-weight user authentication protocol based on biometric identification. It reduces computational complexity effectively because it only applies hash function, XOR operation, concatenation operation and symmetric encryption without complex asymmetric encryption. It can resist attacks such as stolen smart card attack and stolen verifier attack. However, Althobaiti’s protocol is only based on biometric identification that has some Security Flaws. We utilize the Dolev-Yao attacker expansion model to analyze the security flaws existing in the Althobaiti’s protocol.
4.1 Node compromise attack
Assume that an attackerA first captures a sensor node Sj, then obtains secret keyX.The attackerA intercepts messages {IDi,Yi,T3}and {L,T5}thenAcalculates the following formulas:
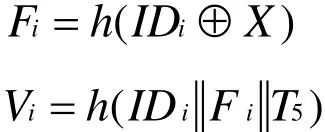
A can may get the correct value Viby constantly trying different T5, where Viis the session key shared byUiand Sj.Αcan steal the session key through the following steps:
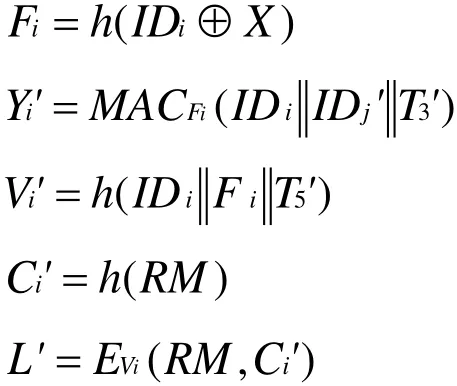
Step two:A intercepts messages {IDi,Yi' ,T3'}and {L',T5'}and obtains the parametersX,IDiand T5', then calculates Vi'=h(), soA acquires the session key between Uiand Sj. WhenAsuccessfully compromises a node, he can obtain session keys for all nodes. So this protocol cannot resist the node compromise attack.
4.2GWNimpersonation attack
We can prove that an attackerA can impersonate theGWNto authenticate sensor node.The detail steps are as follows.
Step one:Acaptures the sensor node, gets the secret keyX, and intercepts the message{}in the authentication phase.
Step two:Acalculates the follow formulas:
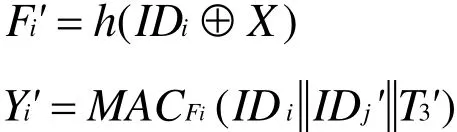
where,ID'jrepresents theID of sensor node Sj'queried by Ui,T3'represents the current timestamp ofA.Asends the message {}to Sj'via the public channel.Step three: AfterSj'receives the message {}, he verifies the freshness of T3'. If it fails to meet the requirement, the operation is terminated. ElseSj'calculates the following formulas:
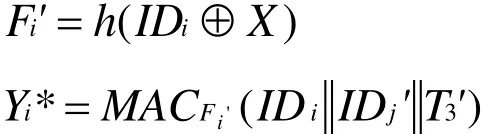
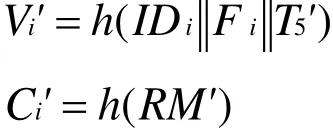
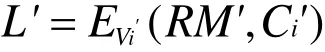
where,T5'represents the current timestamp of Sj' .Sj'sends the message {L',T5'}to Ui.Because the attacker can calculate the session key Vi'through X,IDiand T5', the protocol cannot resist theGWN impersonation attack.
4.3 Man-in-the-middle attack
An attacker can implement the Man-in-the-middle attack through the following processes:Step one:A captures node Sj, obtains the secret keyX , and intercepts the message{IDi,Yi,T3}.
Step two:A calculates the following equations:
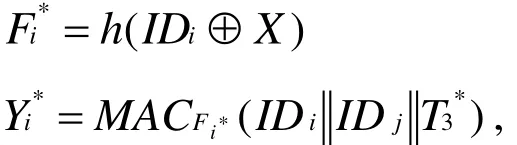
Step three: After Sjreceives message {}, it verifies the freshness of the,and computes the following equations:
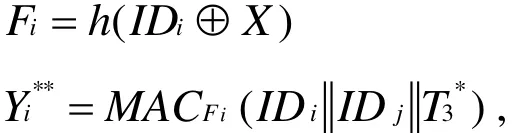
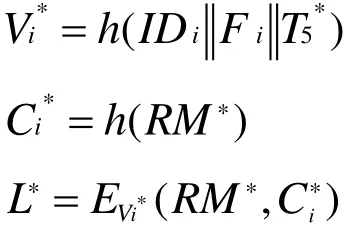
Step four:Aintercepts message { L*,}and computes Vi**=h().A decrypts L*to obtain RM*,C*. Besides,A can create response message RM**to replace RM*,and calculates:
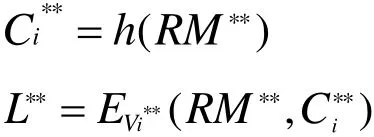
Finally,A sends the message {L**,T5*}to Ui.Uiwill authenticate { L**,T5*}successfully and regardRM**as the legal response, so the protocol cannot resist the Man-in-themiddle attack.
4.4 Privileged-insider attack
In the Registration PhaseGWN randomly generates ekifor Uiand storesin the database. Privileged-insider attack can obtain theekito decrypt message Eeki{R,T1}and forge a fakedUi. So the protocol cannot resist the Privileged-insider attack.
5 The proposed user authentication protocol
In order to improve the existing security flaws of Althobaiti's protocol, we propose a novel user authentication protocol based on biometric identification combined with smart card and password. The proposed protocol includes registration phase, login phase,authentication phase, and biometric identity update phase.
5.1 Registration phase
In this phase,Uiregister withGWN. Fig. 1 illustrates the registration phase and it is performed as follows.
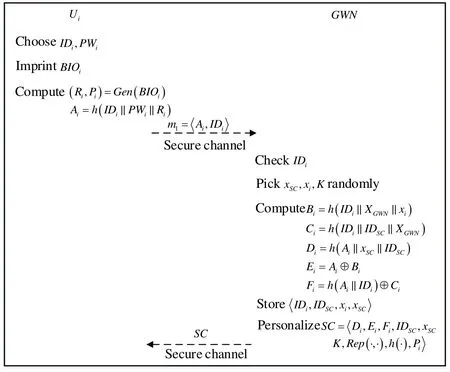
Figure 1: Registration phase
● Step 1:Uichooses IDi,PWi, and imprints biometric BIOi, and computes(Ri,Pi)=Gen(BIOi)and Ai=h(IDi,PWi,Ri). Then sendstoGWNvia a secure channel.
● Step 2:GWN checks if IDiexists in the database, if no,Uiis recommended to select a new identity; otherwise,GWNpicksxSC,xiand K randomly, and computes Bi=h(I Di, XGWN,xi)
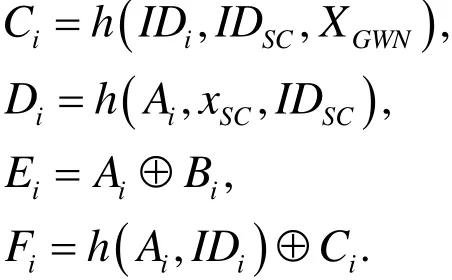
5.2 Login phase
When Uiwants to access the node Sj, the login request is launched at first by Uiwith SC . Fig. 2 illustrates the login phase and it is performed as follows.
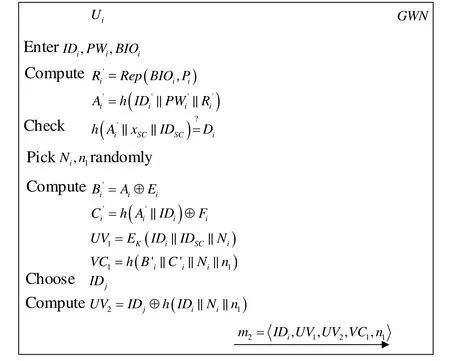
Figure 2: Login phase
● Step 1:UiinsertsSC and enters IDi,PWiand imprint BIOi.
● Step 2:SC computes Ri'=Rep(BIOi,Pi),Ai'=h(I Di,PWi,Ri')and checks whetherequals to Di. If yes,SC picks two random number Niand ni, and computes
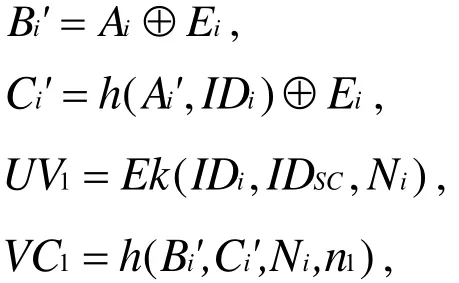
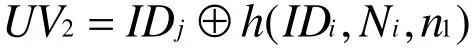
5.3 Authentication phase
Fig. 3 illustrates the authentication phase and it is performed as follows.
● Step 1:GWN checks the validity of IDiand the freshness of n1. If yes, it computes(IDi,IDSC,Ni)=Dk(UV1),Ci=h(IDi,IDSC,XGWN), and Bi=h(IDi,XGWN,xi), and checks whetherh(Bi,Ci,Ni,n1)equals to VC1. If yes,GWN computes IDj=UV2⊕h(IDi,Ni,n1),
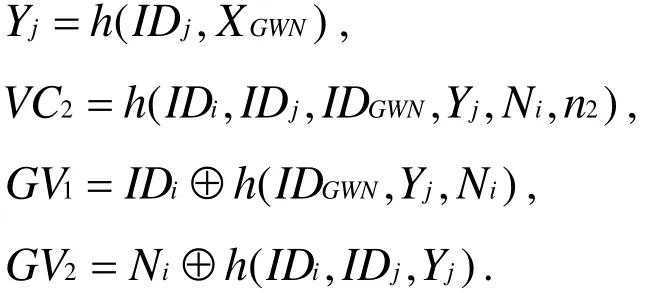
● Step 2:Sjchecks the freshness of n2. If n2meets freshness requirement,Sjcomputes
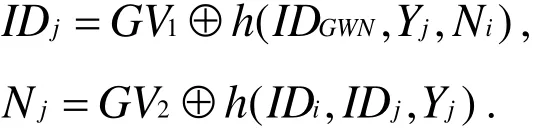
Then, it checks whetherh(IDi,IDj,IDGWN,Yj,Ni,n2)equals to VC2. Next,Sjpicks Njand n3randomly and computes
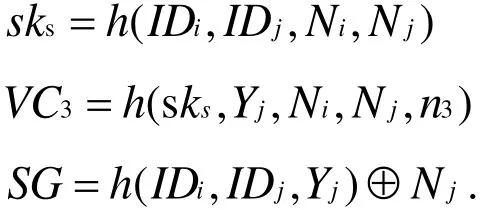
After that,SjsendstoGWN , where n3is a random number.
● Step 3:GWN checks the freshness of n3. If n3meets the freshness requirement,GWN computes:
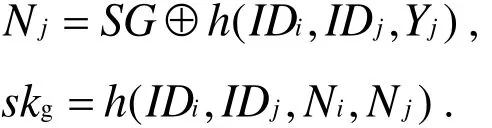
ThenGWNchecks whether h(skg,Yj,Ni,Nj,n3)equals to VC3. If yes,GWN computes:
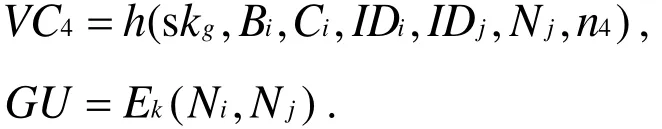
● Step 4:Uichecks the freshness of n4. If n4meets freshness requirement,Uicomputes:
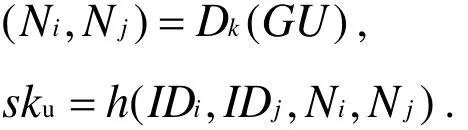
Then he checks whether h(sku,Bi,Ci,IDi,IDj,Nj,n4)equals to VC4. If yes,Uiaccepts GWNand Sj, and agree the session key sku= sks=sk.
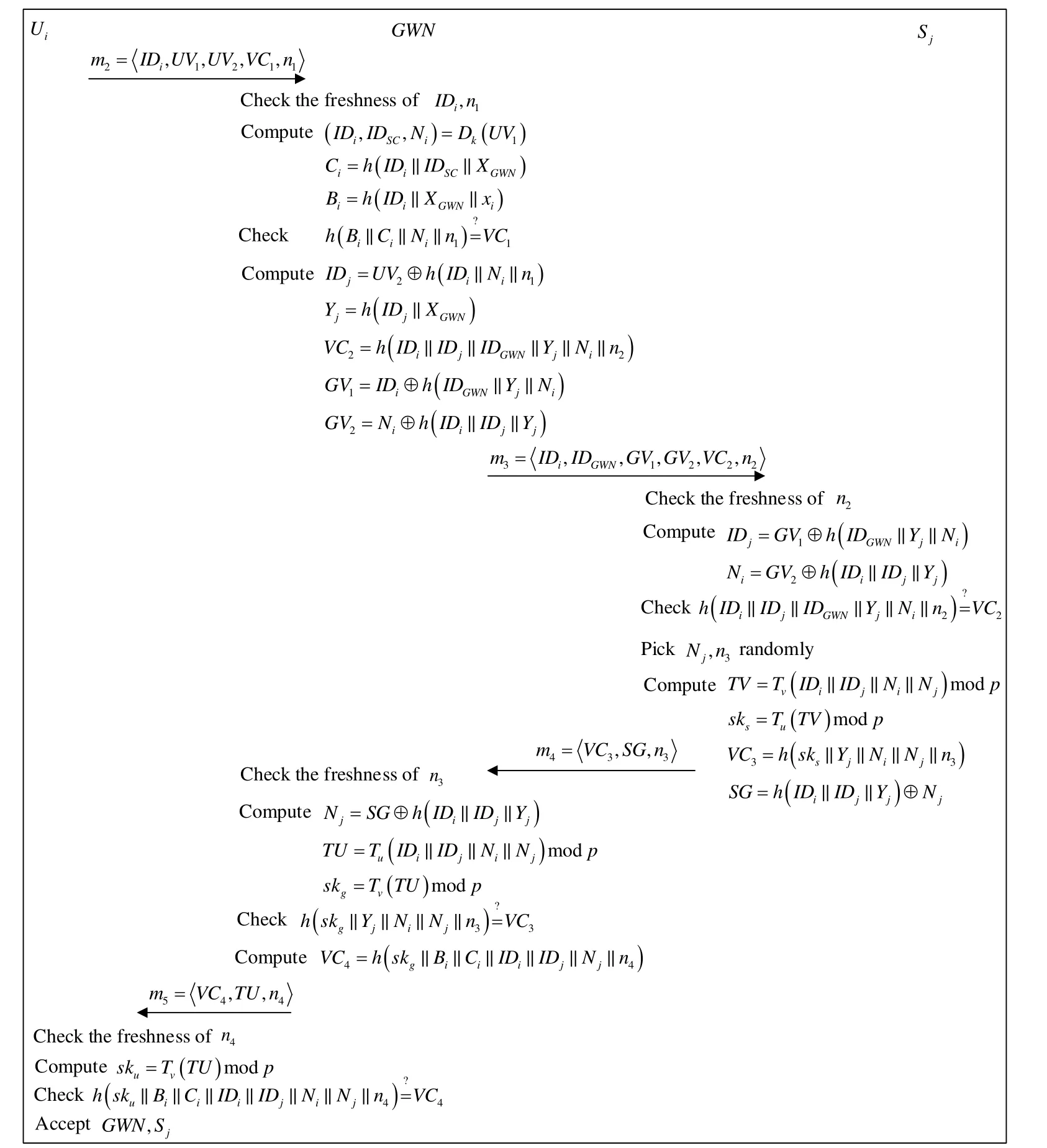
Figure 3: Authentication phase
5.4 Update phase
A legal user can update the old password PWiand the biometric BIOias follows:
● Step 1:Uiinserts the smart cardSC into a card reader, then Uiinputs the IDi, old passwordPWiand imprints old biometric BIOi.
● Step 2:SC computes Ri=Rep(BIOi,Pi),Ai=h(IDi,PWi,Ri), and checks whether h(Ai,xSC,IDSC)equals to SC . If yes,Dicomputes:
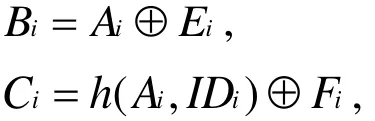
● Step 3:SC computes:
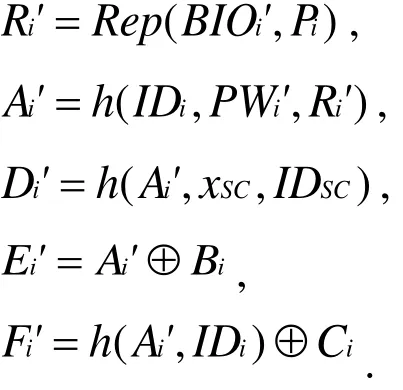
● Step 4: The smart card updates the parameter towithout GWN.
6 Security analysis and performance comparison
6.1 Proof of authentication and key agreement based on BAN Logic
6.1.1 The BAN logic postulates
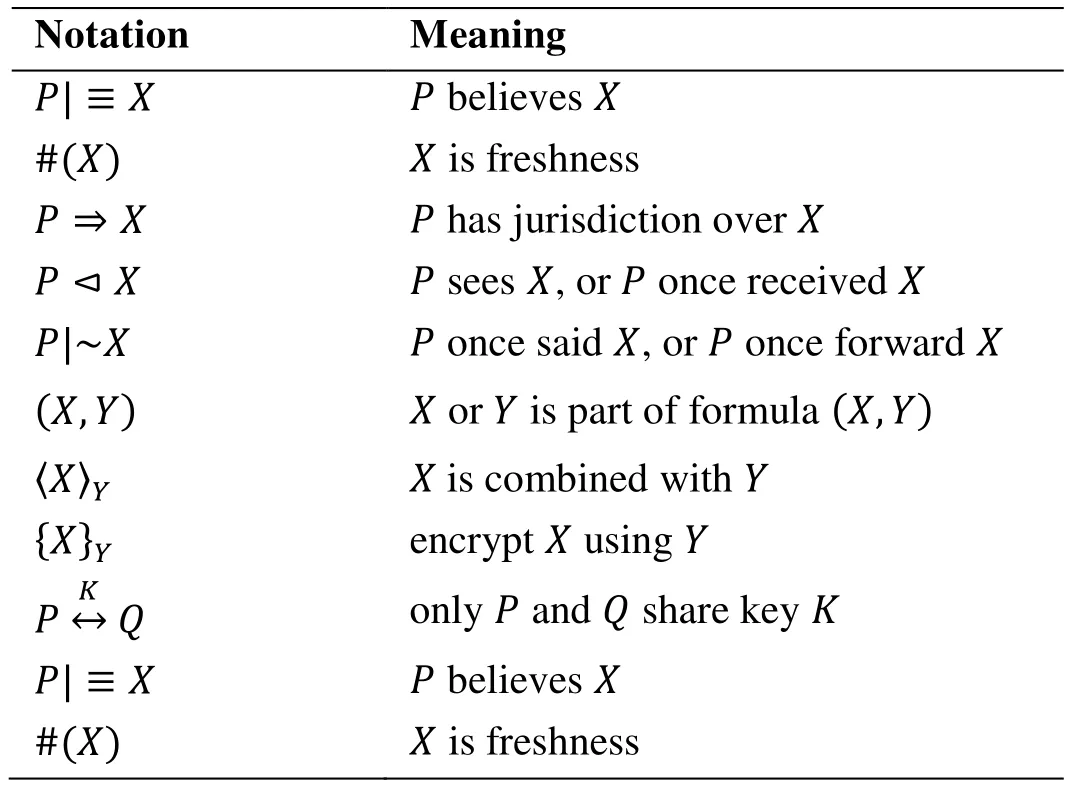
Table 2: Notations and parameters of ban logic
(1) Message meaning rule of shared key
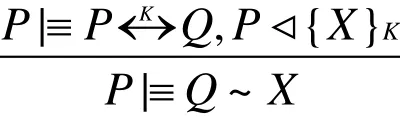
(2) Nonce verification rule
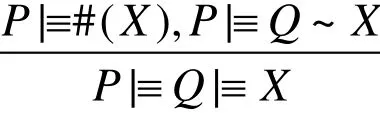
(3) Jurisdiction rule
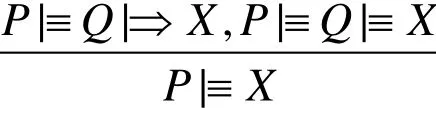
(4) Freshness-conjunction rule
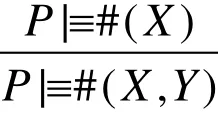
6.1.2 Security goal
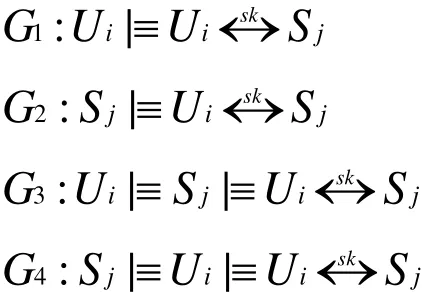
6.1.3 Idealized form

6.1.4 Assumptions
We make the assumptions about the initial state of the scheme to analyze the proposed scheme as follows.
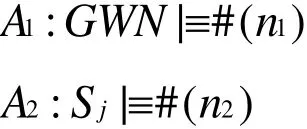
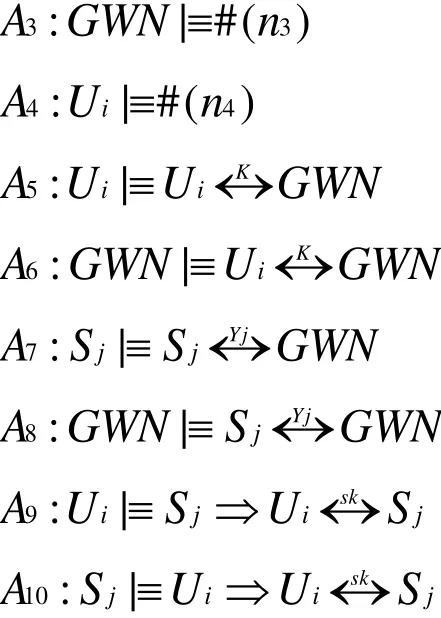
6.1.5 Security analysis of the idealized form of the proposed scheme
According to m2, we can easily obtain
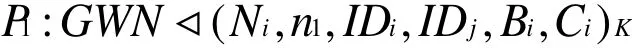
According to A6and the message-meaning rule, we have
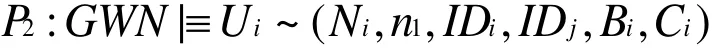
According to A1and the freshness-conjunction rule, we have
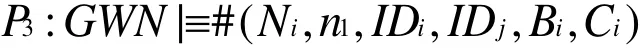
According to P2,P3and the non-verification rule, we have
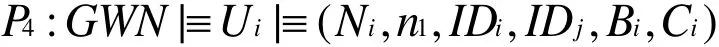
According to m3, we have
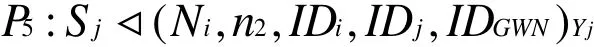
According to A7and the message-meaning rule, we have
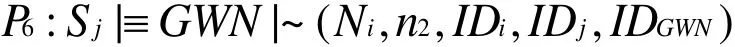
According to A2and the freshness-conjunction rule, we have
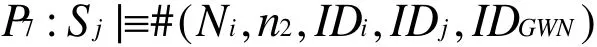
Then from P6,P7and the non-verification rule, we have
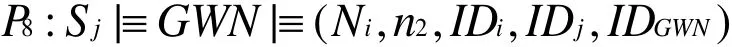
According to m4, we have
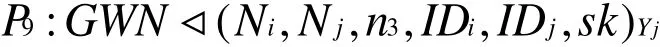
According to A8and the message-meaning rule, we have
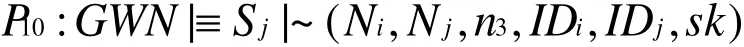
According to A3and freshness-conjunction rule, we have
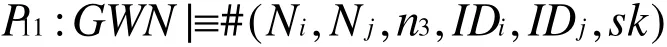
Then according to P10,P11and the non-verification rule, we have
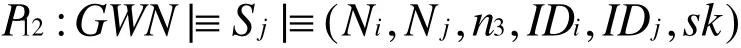
According to m5, we have
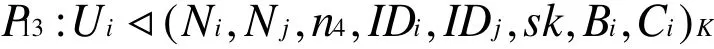
According to A4and the message-meaning rule, we have
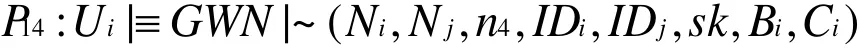
According to A5and freshness-conjunction rule, we have
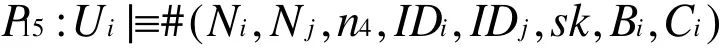
Then, from P14,P15and the non-verification rule, we have
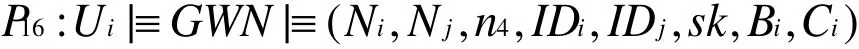
Because sk=h(IDi,IDj,Ni,Nj)according to P16and P12, we have
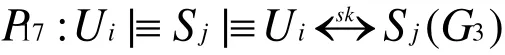
Likewise, according to P4and P8, we have
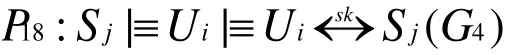
According to P9,P17and jurisdiction rule, we have
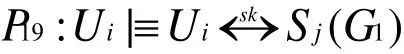
Likewise, according to P10,P18and jurisdiction rule, we have
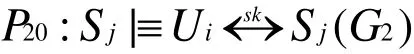
According to G1,G2,G3and G4, we conclude that both Uiand Sjbelieve they share the session key users identity, password,SC and biometrics. It can be concluded that our proposed scheme not only provides mutual authentication between user, sensor node and GWN, but also generates a shared session key for subsequent communication.
6.2 Security aalysis against vrious atacks
● Node capture attack:Assume that an adversaryA physically captures a sensor node Sj, he can access real-time perception data collected by Sj. What is more,Acan obtain the secret information including node key and session keysk . Due to the fact that sk is generated by the Niand Njcorresponding to Uiand Sj, so the session key is different from each other because both the User and Sensor Node are different. One compromising node cannot reveal the information of other nodes and users. Legal users can still communicate with other nodes securely. The proposed protocol can resist Node capture attack.
● Off-line password guessing attack:Assume that an adversaryA may attempt to guess the password PWi. He can obtain AiAisuccessfully, if he steal the data from the smart card. He can obtain PWisuccessfully only if he knows Riwhich is very relevant to the biometric identification BIOi.BIOicannot be forged because of its uniqueness. It is impracticable to guess the password PWicorrectly in our protocol.
● Smart card loss attack:Assume that the smart card of a legal user is stolen by an adversaryA , and he wants to carry out Smart card loss attack.A can get the informationstored in the smart card. AlthoughA can obtainand Ai=h(IDi,PWi,Ri), he cannot obtain PWidue to the one-way function andRiwithout biometric identification BIOi. The proposed protocol can resist Offline password guessing attack.
●GWN impersonation attack:Assume that an attackerAphysically captures a sensor nodeSjand impersonatesGWN to attack sensor node SNj'. In order to be authenticated by the sensor nodeSNj' ,A needs to forge message m3. ThoughAcan obtainyjbecause he captures Sj, he cannot calculate yj'response to SNj'.yj'is the key factors for generatingGV1,GV2and VC2, soA cannot forge message legal m3. The proposed protocol can resist GWN impersonation attack.
● Man-in-the-middle attack and replay attack:Assume that an adversaryA can intercept legitimate login request message. Due to the feature of one-way hash function,Acannot obtain the keyK , the random number Ni,passwordPWiand biometric identification value Rirelated Ui, soAcannot forge message m2. What's more, the login request message m2is related to n1varying with time, so the intercepted m2will be invalid over time. Therefore, our protocol can withstands Man-in-the-middle attack and Replay attack.
● Denial of Service Attack:In the proposed protocol,Ui,SjandGWNverify the freshness of fresh factors n1,n2,n3and n4during the authentication process,respectively. Each message for verification such as m2,m3,m4and m5contains a fresh factor. In addition, each of Ui,SjandGWNverifies if the received value is equal to the recalculated value. The proposed protocol can resist denial of service attack.
● Mutual Authentication:The proposed protocol achieve the mutual authentication of each entities Ui,SjandGWN.GWN authenticates Uiby verifying the validity of m2generated by Ui. Then SjandGWNconduct two-way authentication by checking the validity ofm3generated byGWNand m4generated by Sj. The authentication between Uiand Sjis proved by m5generated byGWN. All the legal messages are only produced by legalUi,SjandGWN. Therefore, our protocol provides proper mutual authentication.
Tab. 3 shows the security features supported by our protocol and existing protocols [Kim(2014); Chang, Lee, Lin et al. (2015); Yoon and Yoo (2014)]. It is clear to see that our protocol has superiority on the extra important security features compared with existing protocols. We note that the protocol of Kim et al. [Kim (2014); Chang, Lee, Lin et al.(2015); Yoon and Yoo (2014)] is susceptible to several attacks, such as man-in-themiddle attack and impersonation attack. The protocol of Chang et al. [Chang, Lee, Lin et al. (2015)] is prone to man-in-the-middle attack and unauthorized access attack. The protocol of Yoon et al. [Yoon and Yoo (2014)] cannot provide user anonymity which may lead to the privacy information disclosure. Our protocol provides the formal BAN-logic to prove security. Due to biometrics application, our protocol can offer nonrepudiation which is regarded as a practical application.
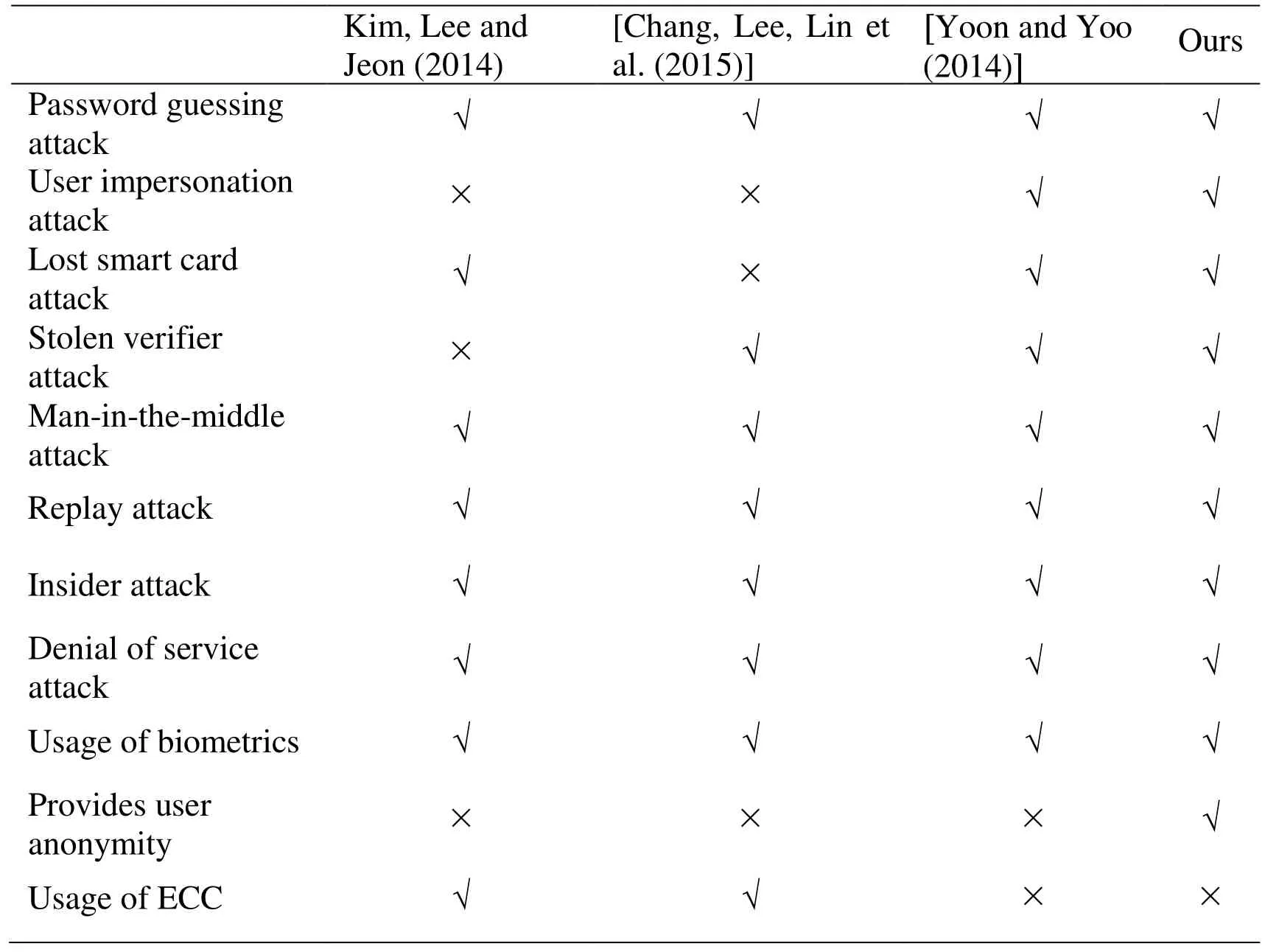
Table 3: Anti-attack performance
6.3 Performance comparisons
Tab. 4 shows the computational load imposed by the authentication protocol in the registration, login, and authentication phases. We denote Th,Tx,TFand TEas one-way hashing operation, XOR operation, fuzzy extractor operation(Gen( ·)or Rep(·)) and symmetric-key encryption or symmetric-key decryption operation ,respectively. In order to reduce computational load, we only use one-way hashing operation and XOR operation to authenticate sensor node. So our protocol is ideal for resource-constrained WSNs.
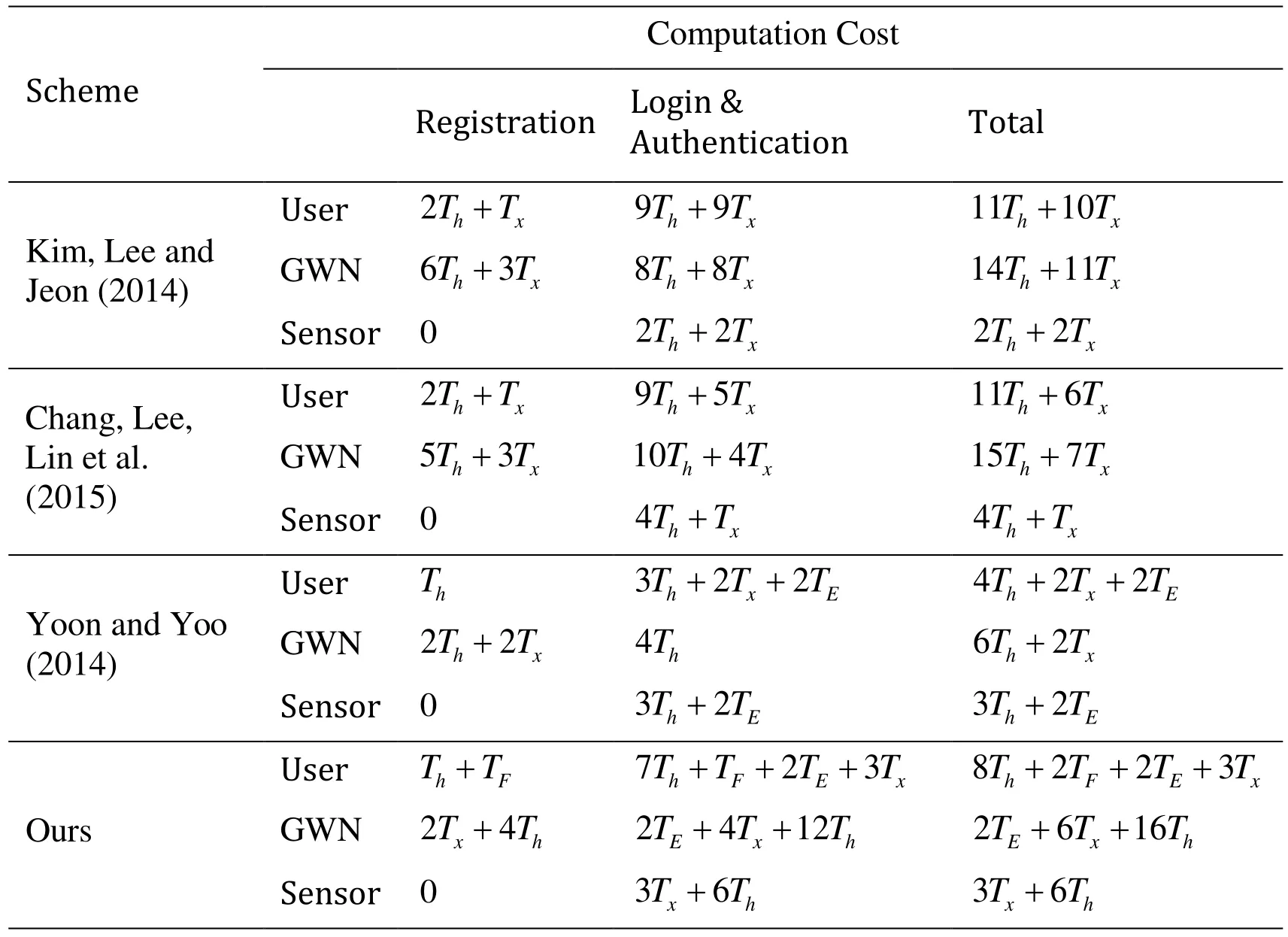
Table 4: Computational Load Comparison
7 Conclusion
Before introducing our protocol, we review the Althobaiti et al. protocol and analyze its security vulnerabilities. Then we propose a novel three-factor user authentication protocol for the information perception of IoT. The proposed protocol can achieve fast authentication process without biometric templates. It not only effectively solves the possible security threats of information perception of IoT, but also realizes easily without changing any hardware conditions. In addition, our protocol can not only be applied to IoT authentication, but also be applied to any scene that needs to protect privacy data and sensitive data. In order to improve algorithm security, the future work may improve the algorithm by applying the lightweight encryption algorithm.
Acknowledgement:This work is supported by the National Science Foundation of China(Grant No. 61501132, Grant Nos. 61771154, 61301095, 61370084), the China Postdoctoral Science Foundation No. 2016M591515, the Heilongjiang Postdoctoral Sustentation Fund with No. LBH-Z14055, Harbin Application Technology Research and Development Project(Grant Nos. 2016RAQXJ063, 2016RAXXJ013).
 Computers Materials&Continua2019年2期
Computers Materials&Continua2019年2期
- Computers Materials&Continua的其它文章
- Optimization Algorithm for Reduction the Size of Dixon Resultant Matrix: A Case Study on Mechanical Application
- Online Magnetic Flux Leakage Detection System for Sucker Rod Defects Based on LabVIEW Programming
- Design of Feedback Shift Register of Against Power Analysis Attack
- Social-Aware Based Secure Relay Selection in Relay-Assisted D2D Communications
- Detecting Iris Liveness with Batch Normalized Convolutional Neural Network
- Forecasting Model Based on Information-Granulated GA-SVR and ARIMA for Producer Price Index
