A Weighted Threshold Secret Sharing Scheme for Remote Sensing Images Based on Chinese Remainder Theorem
Qi He, Shui Yu, Huifang Xu , Jia Liu, Dongmei Huang,Guohua Liu, Fangqin Xu and Yanling Du
Abstract: The recent advances in remote sensing and computer techniques give birth to the explosive growth of remote sensing images. The emergence of cloud storage has brought new opportunities for storage and management of massive remote sensing images with its large storage space, cost savings. However, the openness of cloud brings challenges for image data security. In this paper, we propose a weighted image sharing scheme to ensure the security of remote sensing in cloud environment, which takes the weights of participants (i.e., cloud service providers) into consideration. An extended Mignotte sequence is constructed according to the weights of participants, and we can generate image shadow shares based on the hash value which can be obtained from gray value of remote sensing images. Then we store the shadows in every cloud service provider, respectively. At last, we restore the remote sensing image based on the Chinese Remainder Theorem. Experimental results show the proposed scheme can effectively realize the secure storage of remote sensing images in the cloud. The experiment also shows that no matter weight values, each service providers only needs to save one share,which simplifies the management and usage, it also reduces the transmission of secret information, strengthens the security and practicality of this scheme.
Keywords: Remote sensing image, security, cloud, storage, weighted threshold.
1 Introduction
With the development of remote sensing (RS) techniques, more and more remotely sensed data are acquisition from different sensors of various platforms, and the amount of remote sensing images increases dramatically. Cloud storage is a service with large storage space, cost effective, which has brought new opportunities for massive remote sensing images. Due to the openness of cloud, the data stored in the cloud possess the risk of being malicious damaged or deleted by cloud providers. How to ensure the safety of remote sensing images stored in the cloud is a hot research topics.
Encryption is an effective mean of security. If we store encrypted data in clouds, it is easy to cause the ciphertext been tampered, and results in ciphertext not being restored. In order to avoid the situation that ciphertext cannot be restored, we need to create multiple backups for a secret. The secret sharing scheme based on Shamir can create backup for secret and prevent abuse of power, which is more suitable for data security in the cloud environment. Secret sharing scheme distribute a secret S to n participants such that a set of k or more participants can recover the secret S, and a set of k-1 or less shares cannot obtain any information about S which proposed by Thien and Lin in 2002. In the cloud environment, each service provider is a participant in a secret sharing scheme.
In the traditional secret sharing scheme, participants have the same status. While in the real life, different participants have different roles and importance, such as in the company, the position of general staff and managers are different. Therefore, it cannot satisfy the special needs of the real world when we teat participants equally. The weight threshold access structure allows different participants to have different weights, each participant is assigned a weight value, the bigger the weight value, the higher the participant position. The secret image can be reconstructed without distortion, if and only if the sum of the weights of the shadow images in the recovery process is equal or greater than the given weight threshold.
Most of the existing researches on weighted threshold secret sharing are mostly distributed to the participants with multiple secret shares, which caused low utilization of information, and large computation of data. Therefore, in this paper we proposed an improved weighted threshold secret sharing scheme based on the Chinese remainder theorem, introducing and extending Mignotte sequence to share the sensitive area image.By considering the differences of participants’ rights, which strengthens the security and practicality of the scheme.
2 Related work
At present, techniques for ensuring remote sensing images security in the cloud includes data encryption storage, security audit and access control of ciphertext. Homomorphic encryption is an important method to protect data security and privacy in the cloud storage environment, and is also one of the most effective methods. However, the data processing efficiency of homomorphic encryption technology is too low, and it needs complex exponential operations, which cannot support the rapid processing of large amounts of data. Therefore, homomorphic encryption storage technology is not an efficient way for secure storage of high volume data security storage. The distributed threshold secret sharing scheme is an effective method to protect cloud data, which can create backups for secret data and prevent the abuse of power, so it is widely used in image encryption [Feng, Qin and Yuan (2015)].
The traditional shamir secret sharing scheme has poor sharing efficiency, poor flexibility and poor practical use due to the same permissions. Therefore, the secret sharing with weight threshold becomes a hot in data security storage and encryption. In 1999, Morillo et al. [Morillo, Padró and Sáez (1999)] proposed a weighted secret sharing scheme, which is based on a decomposed structure that can only be applied to the case where the number of elements of each minimum authorized subset is 2. Zhang et al. [Zhang and Zhang(2013)] proposed a weighted threshold secret sharing scheme which requires solving the congruent polynomial equations, the computational complexity is large. Then, the weighted threshold secret sharing scheme was first proposed based on the Mignotte sequence [Shao (2014)]. The scheme first constructs the weighted Mignotte sequence and completes the secret sharing and recovery process based on the Chinese remainder theorem. The scheme reduced secret share size of the privileged participants, but the system parameters are harsh and the system is too complicated. Iftene based on Asmuth and Bloom scheme achieve a more secure weighted threshold secret sharing scheme,which need to construct the weighted Asmuth-Bloom sequence [Harn and Miao (2014);Harn and Hsu (2015)].
Wang et al. [Wang, Zhou and Li (2015)] proposed a weighted secret sharing scheme based on the Chinese remainder theorem, it can effectively solve the problem of sharing pictures with different weights. Many verifiable secret sharing schemes are proposed to solve the deception attack in secret sharing. The verifiable secret sharing scheme [Harn and Miao (2014); Li, Ma and Guo (2015)] increased the secret sharing process and improved the security of secret sharing. In order to increase the security and practicability of the scheme,many dynamic weighted secret sharing schemes are proposed [Wu and Tseng (2011); Harn and Lin (2010)]. When the reconstruction fails, the cheating behavior of the participants can be found by verifying the identity of the participants [Hsu and Harn (2014)]. However, the scheme cannot prevent the cheater from obtaining the secret, and the attacking from semi honest participants. Meanwhile, the scheme can only share a secret at the same time, and the algorithm needs to be performed again when updating the secret.
The existing researches on the image encryption mainly solve the security problem in the centralized storage environment. In the open cloud storage environment, the security problem of remote sensing image is rarely involved. So, this paper proposes an encryption scheme for remote sensing images in a cloud environment combined with the large quantities, large scale and high sensitivity characteristics of remote sensing images,Fig. 1 shows the flow chart of the scheme proposed in this paper. In Fig. 1 we know that the scheme consists of four steps: the construction of weighted Mignotte sequences, the calculation of the hash value based on the gray value of the remote sensing image, the secret image sharing process and the secret image recovery process. While the secret image core process is divided into three stages: preparation, sharing and recovering. In this scheme, each participant only needs to keep a secret share, it can reduce the transmission of secret information, and improve the security of secret.
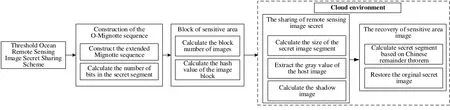
Figure 1: Process of weighted threshold secret sharing scheme based on extended Mignotte
3 A weighted secret sharing scheme based on extended mignotte sequence
In this paper, we first block the remote sensing image and use the hash algorithm to calculate the average gray value of each image block based on the gray value of the remote sensing image, in the last we obtain the secret share by the quantization operation.The secret image can be reconstructed without distortion when the weight of the participants is equal to or greater than the weight threshold. In this paper, this section describes and defines the research problems, and gives the extended Mignotte sequence based on the weighted threshold of the sensitive area remote sensing image secret sharing.
3.1 Description and definition of the problem
This paper constructs a secret image sequence of the remote sensing image based on the Mignotte sequence, the secret image is decomposed into different secret sharing, and recorded as the shadow image. In the secret reconstruction stage, the secret share is recovered based on the Chinese remainder theorem. Then, the secret shares are filled into the corresponding position in the image according to the number and the secret image is obtained. Now we describe and define the related concepts of the remote sensing image secret sharing scheme based on extended Mignotte sequences.
DEFINITION 1: Weighted Threshold Remote sensing Image Secret Sharing Scheme.The weighted threshold secret sharing scheme is expressed as,is the weight held by the participant, w is threshold valueis a participant set, for any subsetof. It can restore the secret image when
Definition 2: Remote sensing image data set. The remote sensing image dataset is a four tuple, id is the number of the image, r is the resolution of remote sensing image, L is latitude and longitude of the remote sensing image, bnthe number of bands for remote sensing images.
Definition 3: O-Mignotte sequence. O-Mignotteas a sequence of remote sensing images.Firstly, constructing a Integer prime Sequence .According to the participant weight vector,and extending
3.2 Weighted threshold remote sensing image secret sharing
In this paper, the Chinese remainder theorem can be used to reconstruct remote sensing image by its set of remainder numbers, this set of remainder numbers is obtained by taking a set of two mutually integers.
Theorem 1: As known O-Mignotte sequence isrecorded as,and remote sensing image secret segments are.Then, the Congruence Equations are:

There is a unique solution in the sense of modular m congruence:
Proof. By definition 4, we knowis a primitive sequence. When, there is. As. As, there is onewhich it satisfied. In addition, when,byand,we get.According to the above formula we have:
1) O-Mignotte threshold secret sharing scheme
O-Mignotte threshold secret sharing scheme, we construct O-Mignotte sequence on the basis of Mignotte sequence, and complete the secret sharing and recovery process based on Chinese remainder theorem. Assuming n is the number of participants, P is a collection of all the subsets of the participants,is the weight sequence of each participant,is the weight threshold of access structure, and it satisfied. We call thesequence a weighted sequence under this condition.
The traditional threshold secret sharing scheme based onsequence does not implement the weighting of the participants. So the secret distributor builds an extended O-Mignotte sequence according to the weight assignment. So that the extended OMignotte sequence has equivalent effects to the traditional Mignotte sequence. The construction of O-Mignotte sequence is a key part of the weighted threshold secret sharing scheme. Specific steps are as follows:
Step1: Let w is the weight threshold of the access structure, which it satisfied
Step2: Constructing a prime sequence
Step3: According to the weight of participant, extending
Step4: Public O-Mignotte sequence;
Step5: When the sequence is constructed, then calculating, which it satisfied, among them. By lettingwe regard the remote sensing image as a series of b-bit segments.
2) Remote-sensing image secret sharing
The secret sharing of remote sensing image uses the constructed weighted sequence to decompose the secret image into many secret shares with different weights, each secret share is recorded as shadow images, and is distributed to different participants. While the secret image sharing process is divided into three stages: preparation, sharing and recovering. In the preparation phase the remote sensing image is divided into blocks, and we calculated the hash value of each image. We use the gray value of the remote sensing image as the image feature to generate the hash value. Fig. 2 shows a diagram of the secret image sharing process, according to Fig. 2 we know that this process is also divided into three phases. Firstly, we block the remote sensing images, and calculate the gray value for each image block to obtain a gray mean value sequence as the middle hash of images. Then, we calculate the average of the gray mean value sequence, note as.Finally, we compare the middle hash withone by one, greater than, which we code as 1, less than, which we code as 0. Based on the above, we obtain the value of the image by connecting the coding value, see algorithm 1.
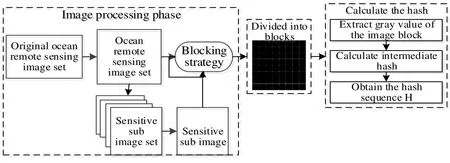
Figure 2: Process of remote sensing image hash based on gray value
The specific algorithm 1 is as follows:
Input: Remote sensing image
Output: The hash sequence of remote sensing image
Step1: Block remote sensing image N into, i is equal to the length of the hash sequence;
Step2: Extarct the gray value matrix of, calculate the mean value of each matrix, noted as; Merge, we will get a sequence with i length, and take the sequence as Middle hash. Then, we calculate the average of the gray mean value sequence, note as.Among them
Step3: Compare the middle hash withone by one, and take the comparing result as a binary sequence. Then, we can obtain the hash.
The sharing is the key stage for generating shadow image. Firstly, calculating the size of the remote sensing image according to the number of secret segments, and distributing them to different participants, see algorithm 2. Fig. 3 shows the basic flow of the secret image sharing process.
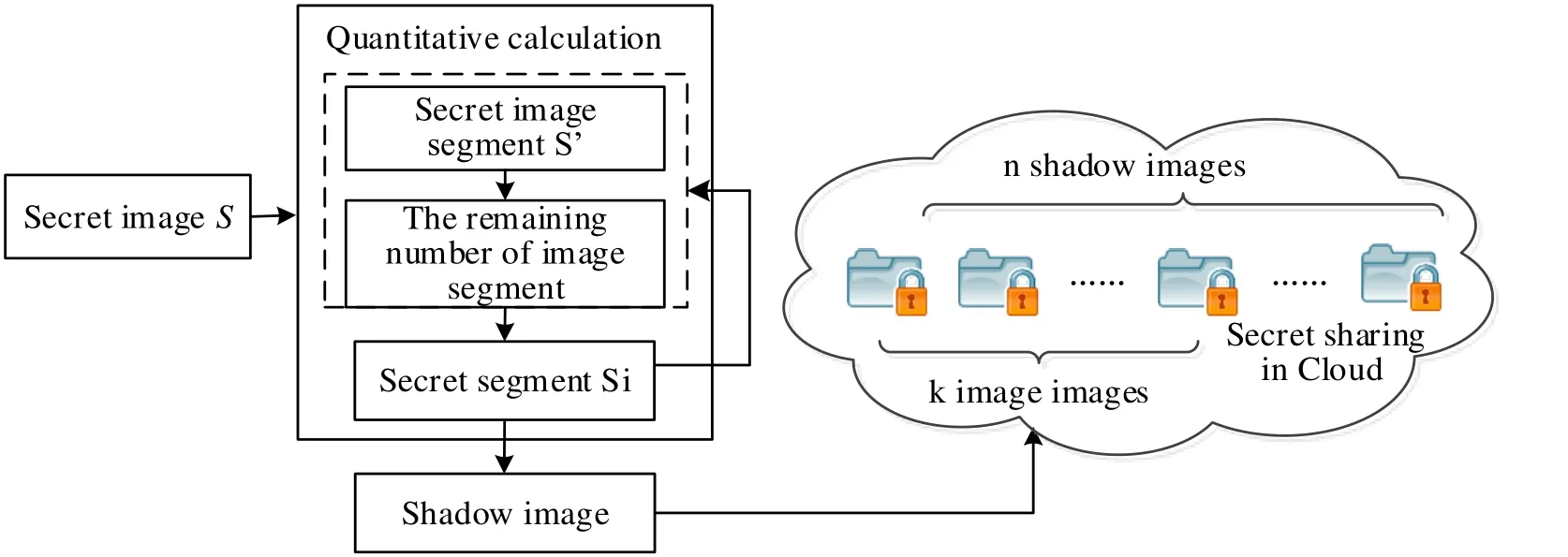
Figure 3: The procedure of secret image sharing
The specific algorithm 2 is as follows:
Input: Remote sensing image
Step 1: Calculating the number of secret images:

Step 2: Using the formula to adjust the secret image segment:
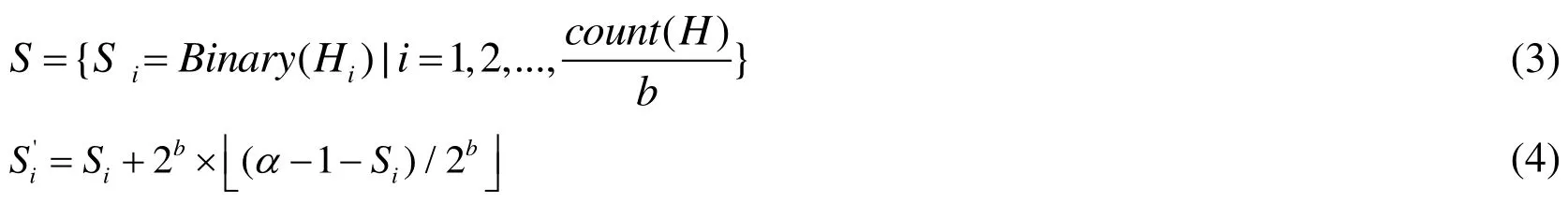
Step 5: Repeat Step 3, until all the secret segmentsare process.
3) Remote sensing image secret restoration
After the sharing of the remote sensing image is completed, any participant whose weight is equal to or greater than the weight threshold can use their shadow images to generate the secret segments based on Chinese Remainder Theorem, and theoriginal secret image can be recovered without distortion according to the secret segment . Fig. 4 shows the recovery process of the secret image. See algorithm 3.
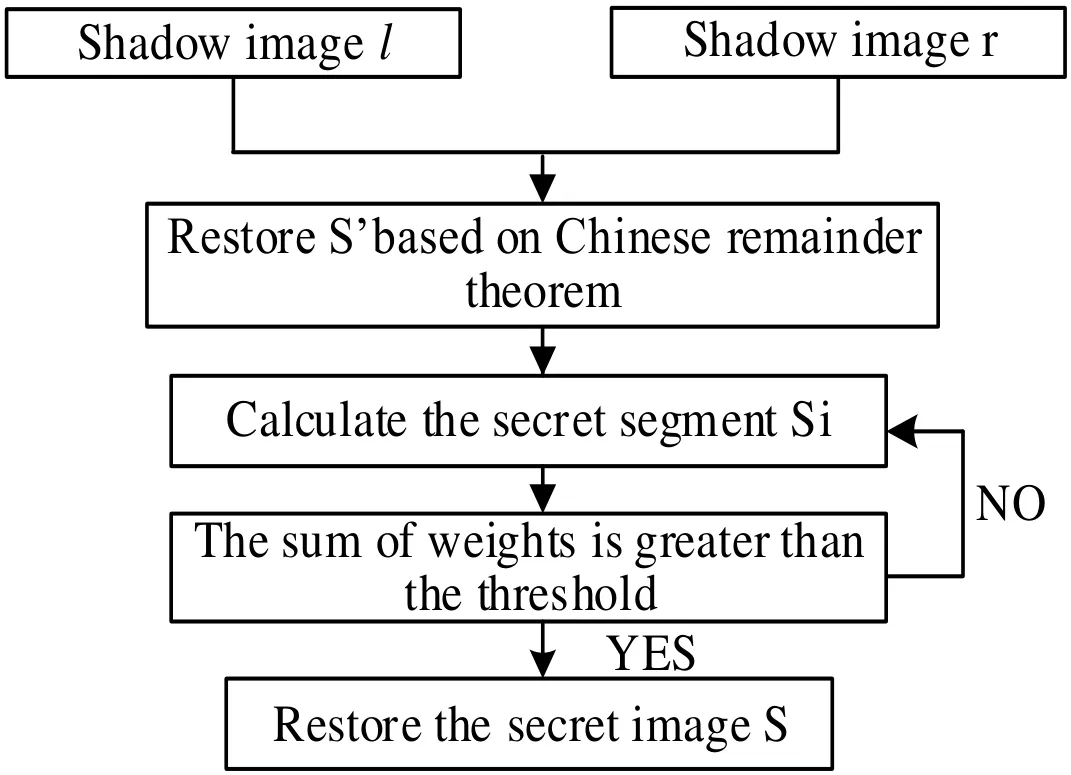
Figure 4: The procedure of secret image recovery
The specific algorithm 3 is as follows:
Input: r shadow images
Output: Original secret image
Step1: The weight vector of each participant is
Step2: Use A=(u1, u2,…,uk) to restore the image of the secret segment;

Step 4: Calculating the secret segments
Step 5: Repeating the above steps until allare extracted;
Step 6: When the sum of the weights of the participants is equal to or greater than the threshold. Takingas the ith b-bit segment, and then placinginto the corresponding position, and recovering the original secret image;
4 Experimental results and analysis
The experiment uses Matlab2010 to obtain the remote sensing image of Hangzhou area TM image acquired in April 16, 2015.The format of image is TIFF, the size is 1024×1024, the resolution is 30m.From the third section, we split the selected images to obtain sensitive area remote sensing images, as shown in Fig. 5, and extracting the single band gray image, as shown in Fig. 6.

Figure 5: Remote sensing image

Figure 6: Single band image

Figure 7: Block image
4.1 Experimental results
According to the previous condition, we can figure outand.
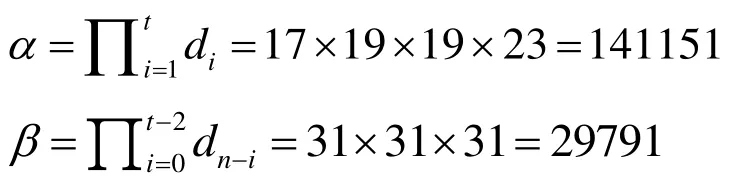
In the secret image sharing stage, the secret image is regarded as a series of b-bit and we calculate, that is, every 16 bits in the original secret image is treated as a secret segment. In order to obtain image share as a series of b-bit, in this paper, the image is divided into blocks using a formulaby adopting a hash algorithm based on gray value of remote sensing image, we can get. The result of the block is shown in Fig. 7. After that, we calculate the image block hash value based on remote sensing image gray value method, see Tab. 1. According to algorithm 2, the values of the five secret segments are calculated as follows S1=30430, S2=23124, S3=42682,S4=26325, S5=14439, the specific construction process is shown in Fig. 8. According to algorithm 2, we can calculateand then calculate the remaining number of five secret segments,respectively x1=1, x2=301, x3=10, x4=92, x5=6593. Then we distributed shadow image of the first segment to each participant. Each person can only save a sub image share,regardless of the size of the participants.
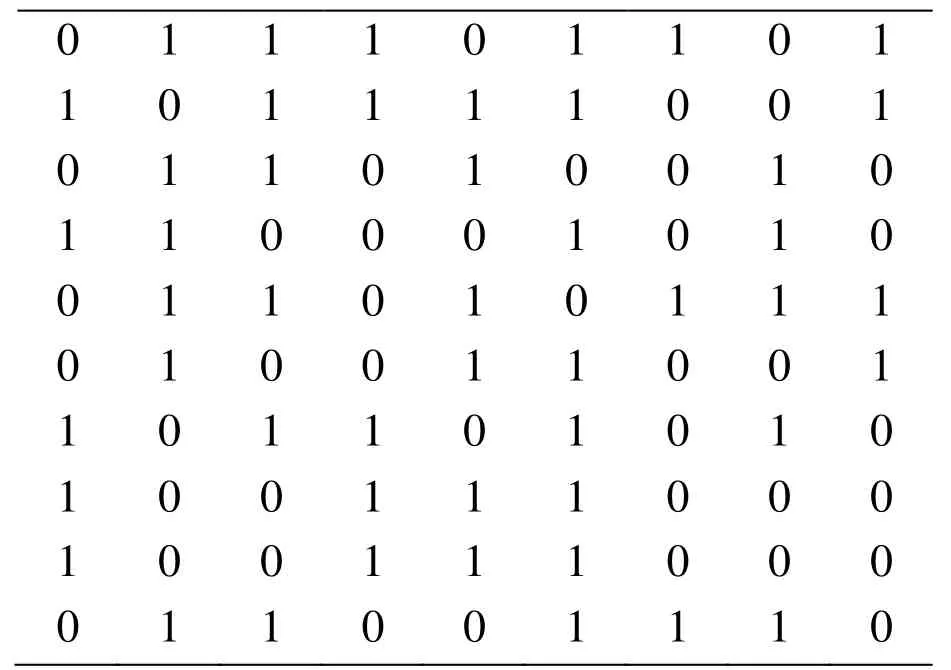
Table 1: Hash sequence of remote sensing image
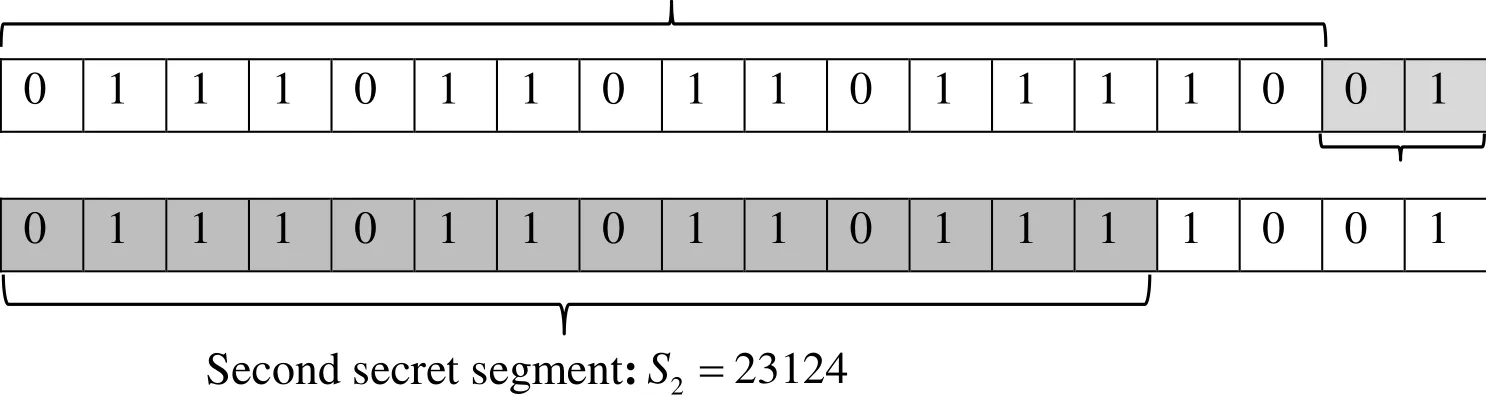
Figure 8: The construction of 16-bit secret segments
4.2 Discussion
In order to verify the validity of the remote sensing image based on the extended Mignotte sequence. In this paper we verify the validity from security and correctness two aspects.
1) Security analysis
In order to verify the security of the scheme, we select participant 1 (weight is 1) and participant 4 (weight is 2) to restore the secret image. We know that x4=92. According to the Chinese remainder theorem:

We can figure outand S1=10184. The results show that the first secret segment value is unequal to the original image. So we cannot restore the original secret image when the shadow images do not meet the weight threshold. It verified the security of this scheme.
2) Correctness analysis
After generating the shadow image, we began to recover the secret image. In the process of image recovery, when the weight of the participants is equal to or greater than the weight threshold, we can recover the original secret image without distortion by using their shadow image and . It is known that the weight of each participant is. In this paper, we firstly select participant 1,participant 3 and participant 5 to restore the secret image,,which satisfied.The shadow images of Participant 1 Participant 3 and Participant 5 are respectively x1=1, x3=10, x5=6593. According to the Chinese remainder theorem:

5 Summary and future work
In this paper, we propose an extended weighted threshold remote sensing image sharing scheme based on the Chinese remainder theorem. Combining with the large volume and large scale characteristics, we construct an extended remote sensing image sequence according to the weight of cloud service providers based on the Mignotte sequence. The secret image is divided into several secret shares, we record the secret shares as the shadow image.
Experimental results show the scheme we provide can effectively realize the secure storage of remote sensing images in the cloud. In addition, we take the weights of cloud service providers into consideration, the experiment shows that no matter what the weight value size, each service providers only needs to save one share, which simplifies the management and usage, it strengthens the security and practicality of this scheme.
Acknowledgement:This research was partly supported by (National Natural Science Foundation of China under 41671431, 61572421, and Shanghai Science and Technology Commission Project 15590501900.
 Computers Materials&Continua2019年2期
Computers Materials&Continua2019年2期
- Computers Materials&Continua的其它文章
- Design of Feedback Shift Register of Against Power Analysis Attack
- An Improved Unsupervised Image Segmentation Method Based on Multi-Objective Particle Swarm Optimization Clustering Algorithm
- Forecasting Model Based on Information-Granulated GA-SVR and ARIMA for Producer Price Index
- Detecting Iris Liveness with Batch Normalized Convolutional Neural Network
- Social-Aware Based Secure Relay Selection in Relay-Assisted D2D Communications
- A Lightweight Three-Factor User Authentication Protocol for the Information Perception of IoT
