基于关联分析与FCE的网络安全风险评估
孙雪岩 吴俊华 刘效武 张淑雯

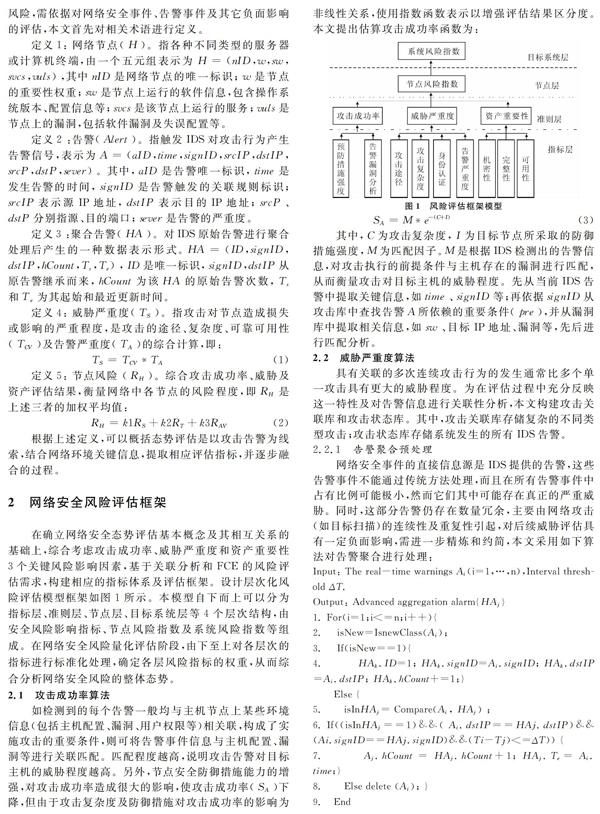

摘要:传统的网络安全风险评估方法中,存在评估结果单一性和过分主观依赖性等问题。为使评估结果更切合实际及解决不确定性因素难以定量评估的问题,设计一个用来衡量安全防御措施能力与节点脆弱性对攻击结果影响的成功率算法;采用攻击威胁严重度算法,通过安全漏洞评分对脆弱性进行评估。最后,提出基于熵权理论的模糊综合评判分析方法计算系统整体的风险态势值,从而更好地辅助网络分析人员及时掌握系统实时风险态势。针对该方法进行仿真实验分析,结果表明该方法可以准确并客观地评估网络风险,进而避免传统方法存在的主观性和片面性,证明了该方法的合理性。
关键词:网络安全风险评估; 模糊综合评判(FCE) ; 熵权理论
DOIDOI:10.11907/rjdk.161039
中图分类号:TP309文献标识码:A文章编号:1672-7800(2016)006-0192-04
参考文献:
[1]ELSHOUSH H T,SWMAN I M.Alert correlation in collaborative intelligent intrusion detection systems-a suvey[J].Applied Soft Computing,2011,11(7):4349-4365.
[2]CHEN X Z,ZHENG Q H,GUAN X H,et al.Quantitative hierarchical threat evaluation model for network security[J].Journal of Software,2006,17(4):885-897.
[3]CHEN FENG,LIU DEHUI,ZHANG YI,et al.A hierarchical evaluation approach for network security based on threat spread model[J].Journal of Computer Research and Development,2011,48(6):945-954.
[4]DU S,LI X,DU J,et al.An attack-and-defense game for security assessment in vehicular ad hoc networks[J].Peer-to-Peer Networking and Applications,2014,7(3): 215-228.
[5]葛海慧,肖达,陈天平,杨义先.基于动态关联分析的网络安全风险评估方法[J].电子与信息学,2013,35(11):2630-2636.
[6]LYU H,PENG W,WANG R,et al. A real-time network threat recognition and assessment method based on association analysis of time and apace[J].Journal of Computer Research and Development,2014,51(5):1039-1049.
[7]梁吉业,钱宇华.信息系统中的信息粒与熵理论[J].中国科学E辑:信息科学,2008,38(12):2048-2065.
[8]FU S,LIU Z,ZHOU H,et al.A security risk analysis method for information system based on information entroy[J].Open Cybernetics& Systemics Journal,2015,9(1):23-27.
[9]M SOLEIMANI DAMANEH,M ZAREPISHEH.Shannon's entropy for combining the efficiency results of different DEAmodels:Method and application[J].Expert Systems with Applications,2009,36:5146-5150.
[10]WANG TONG.The research of electronic banking risk evaluation based on comprehensive assessment AHP-entropy[J]. International Journal of U-& E-Service,Science & Technology,2014,7(6):413-422.
[11]TSAI H Y,HUANG Y L.An analytic hierarchy process-based risk assessment method for wireless netorks[J]. Reliabity, IEEE Transactions on,2011,60(4):801-816.

