An Algebraic Detection Approach for Control Systems under Multiple Stochastic Cyber-attacks
Yumei Li,Holger Voos,Mohamed Darouach,and Changchun Hua
An Algebraic Detection Approach for Control Systems under Multiple Stochastic Cyber-attacks
Yumei Li,Holger Voos,Mohamed Darouach,and Changchun Hua
—In order to compromise a target control system successfully,hackers possibly attempt to launch multiple cyberattacks aiming at multiple communication channels of the control system.However,the problem of detecting multiple cyber-attacks has been hardly investigated so far.Therefore,this paper deals with the detection of multiple stochastic cyber-attacks aiming at multiple communication channels of a control system.Our goal is to design a detector for the control system under multiple cyberattacks.Based on frequency-domain transformation technique and auxiliary detection tools,an algebraic detection approach is proposed.By applying the presented approach,residual information caused by different attacks is obtained respectively and anomalies in the control system are detected.Suf fi cient and necessary conditions guaranteeing the detectability of the multiple stochastic cyber-attacks are obtained.The presented detection approach is simple and straightforward.Finally,two simulation examples are provided,and the simulation results show that the detection approach is effective and feasible.
Index Terms—Cyber-attack detection,control system,multiple stochastic cyber-attacks.
I.INTRODUCTION
AS networks become ubiquitous and more and more industrial control systems are connected to open public networks,control systems are increased the risk of exposure to cyber-attacks.Control systems are vulnerable to cyber-threats,and successful attacks on them can cause serious consequences[1-3].Therefore,the security and safety issues in controlled systems have been recently realized and they are currently attracting considerable attention[4-20]. Some researchers focused on the cyber security of water systems[3,6-7].Further works considered cyber-attacks on smart grid systems[4,8-10,12].In order to detect as well as identify and isolate these cyber-attacks as early as possible, different detection approaches were presented.For example [13]investigated the problem of false data injection attacks against state estimation in electric power grids[14]proposed a model predictive approach for cyber-attack detection[15]. presented a stochastic cyber-attack detection scheme based on frequency-domain transformation technique[16].considered robustH∞cyber-attacks estimation for control systems[17].proposed a detection algorithm by investigating the frequency spectrum distribution of the network traf fi c.References [18-20]used consensus dynamics in networked multi-agent systems including malicious agents.As far as we know,no existing literatures deal with the problem of multiple cyberattacks.In practice,however,hackers might attempt to launch multiple attacks aiming at multiple communication channels of a control system in order to create attacks that are more stealthy and thus more likely to succeed.When a hacker launches two or more cyber-attacks against a control process, usually it is claimed that the control system suffers from multiple cyber-attacks.The fact that no research currently deals with the detection of multiple cyber-attacks on a control process motivates our research in detection of multiple cyberattacks.
This paper deals with the problem to detect multiple stochastic cyber-attacks aiming at multiple communication channels of a control system.We present an algebraic detection approach based on the frequency-domain transformation.The basic idea is to use appropriate observers to generate residual information related to cyber-attacks.An anomaly detector for the control system under multiple stochastic cyber-attacks and stochastic disturbances is derived.The main contributions in the paper are as follows.We fi rst propose a control system with multiple stochastic cyber-attacks that satisfy a Markovian stochastic process.In addition,we also introduce the stochastic attack models that are aiming at a speci fi c controller command input channel or sensor measurement output channel.Second, based on the frequency-domain transformation technique and auxiliary detection tools,the error dynamics of the control system is transformed into algebraic equations.We consider possible cyber-attacks as non-zero solutions of the algebraic equations and the residuals as their constant vectors.By analyzing the ranks of the stochastic system matrix and the auxiliary stochastic system matrices,the residual information caused by attacks from different communication channel is obtained,respectively.Furthermore,based on the obtained residual information,we are able to determine the detectability of these cyber-attacks.The suf fi cient and necessary conditions guaranteeing that these attacks are detectable or undetectable are obtained.Finally,we provide two simulation examples to illustrate the effectiveness of our results.In Example 1,we consider a control system with stochastic noises.We detect possible stochastic cyber-attacks,which are aiming at three different controller command input channels on the actuator. In Example 2,we use the quadruple-tank process(QTP)as described in[21].We also detect two possible cyber-attacks on the QTP.These simulation results show that the proposed attack detection approach is effective and feasible.
For convenience,we adopt the following notations:E{·}is the mathematical expectation operator;dim(·)denotes the di-mension of given vector;([0,∞);Rn)is the space of nonanticipative stochastic processes.
II.PROBLEM STATEMENT
Consider the following control system with multiple stochastic cyber-attacks aiming at speci fi c controller command input channels and sensor measurement output channels.
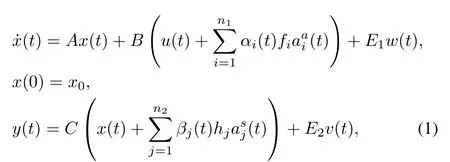
wherex(t)∈Rris the state vector,u(t)∈Rmis the control input,y(t)∈Rpis the measurement output,(t)∈R,i=1,...,n1and(t)∈R,j=1,...,n2denote the actuator cyber-attack aiming at thei-th controller command input channel and the sensor cyber-attack aiming at thej-th sensor measurement output channel,respectively.A,B,C,E1andE2are known constant matrices.w(t)andv(t)are stochastic noises(w(t),v(t)([0,∞);Rn)).fiandhjare the attacked coef fi cients.αi(t)andβi(t)are Markovian stochastic processes with the binary state(0 or 1),which satisfy the following probability
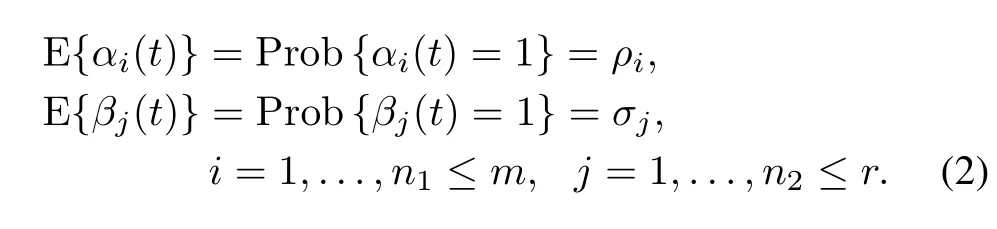
Herein,the eventαi(t)=1(orβj(t)=1)shows that thei-th controller command input channel on the actuator(or thej-th sensor measurement output channel on the sensor) is subject to an actuator cyber-attack(t)(or a sensor cyberattack(t));αi(t)=0(orβj(t)=0)means no attack on thei-th(or thej-th)channel.ρi∈[0,1](orσj∈[0,1])re fl ects the occurrence probability of the event that the actuator(or the sensor)of the system is subject to a cyber-attack(t)(or(t)).αi(t)andβj(t)are independent from each other,they are also independent from the stochastic noisesw(t),v(t)and the initial statex0.
The control input matrixBand the output state matrixCare expressed as the following column vector groups,respectively
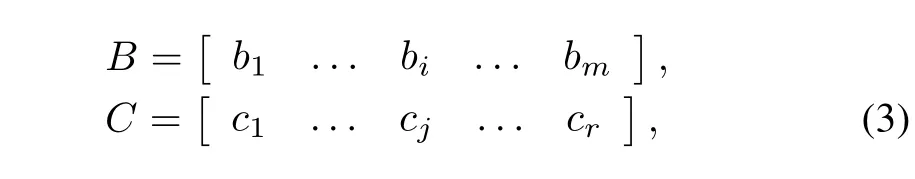
wherebiis thei-th column vector of matrixBandcjis thej-th column vector of matrixC.And the control inputu(t) and the system statex(t)are written as
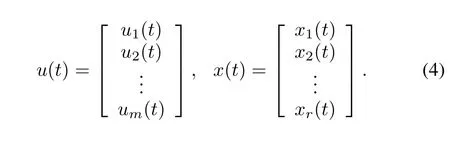
A.Modeling a Stochastic Cyber-attacks on a Speci fi ed Communication Channel
In order to increase the success chance of an attack and to intrude more stealthily,hackers may attempt to launch stochastic cyber-attacks aiming at one or several special communication channels of a control system.In a stochastic data denial-of-service(DoS)attack,the objective of hackers is to prevent the actuator from receiving control commands or the controller from receiving sensor measurements.Therefore,by compromising devices and preventing them from sending data, attacking the routing protocols,jamming the communication channels, fl ooding the communication network with random data and so on,hackers can launch a stochastic data DoS attack that satis fi es Markovian stochastic processes.In a stochastic data deception attack,hackers attempt to prevent the actuator or the sensor from receiving an integrity data by sending false information eu(t)(t)or ey(t)(t)from controllers or sensors.The false information includes:injection of a bias data that cannot be detected in the system,or an incorrect time of observing a measurement;a wrong sender identity, an incorrect control input or an incorrect sensor measurement. The hacker can launch these attacks by compromising some controllers or sensors or by obtaining the secret keys.
In this work,we model stochastic data DoS attacks and stochastic data deception attacks,which hackers possibly launch on a control system aiming at a speci fi c controller command input channel or sensor measurement output channel.
1)A stochastic DoS attack preventing the actuators from receiving control command of thei-th control channel can be modelled as
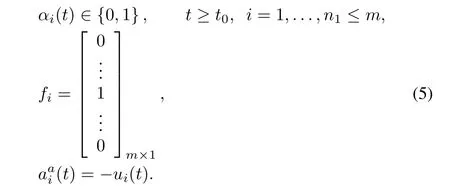
2)A stochastic DoS attack preventing the sensors from receiving sensor measure of thej-th output channel can be modelled as
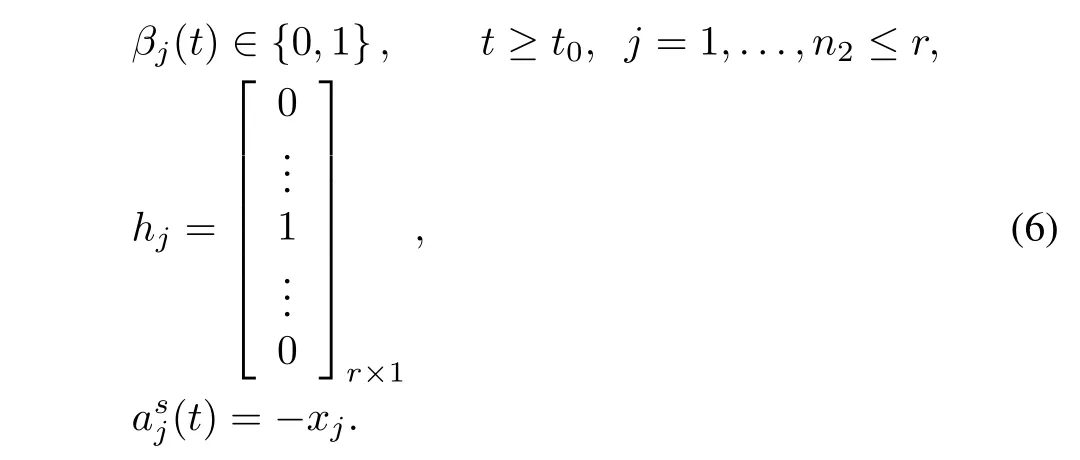
Moreover,if the following conditions are satis fi ed:
these stochastic attacks mentioned above completely deny the services on the actuator and on the sensors,respectively.
3)A stochastic data deception attack preventing the actuator from a correct control input of thei-th control channel can be modelled as
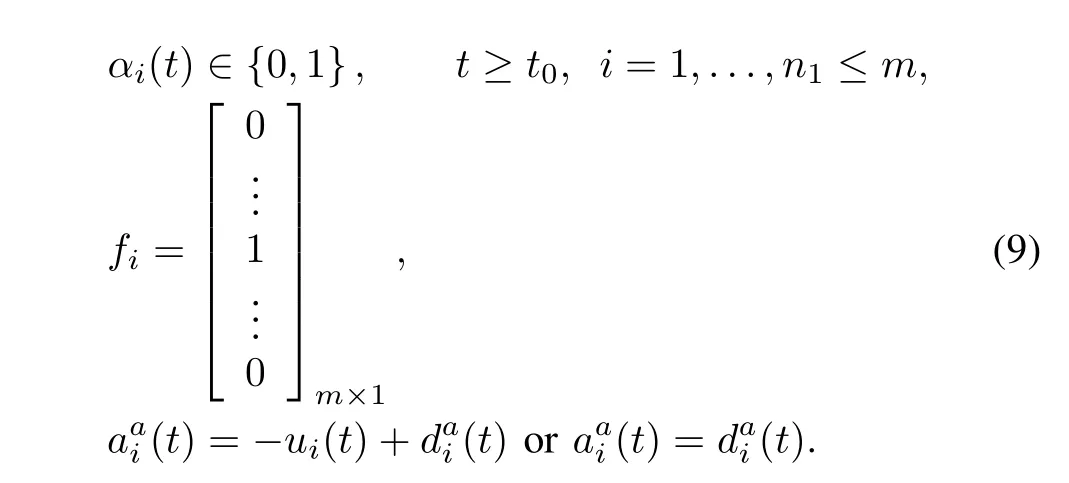
4)A stochastic data deception attack preventing the sensor from a correct sensor measurement of thej-th output channel can be modelled as
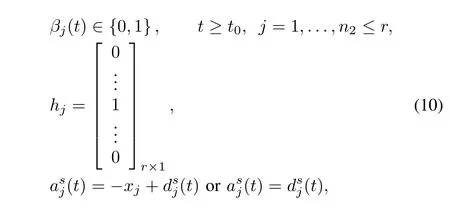
where(t)and(t)are deceptive data that hackers attempt to launch on the actuator and the sensor,respectively.
Now,let(s)=C(sI-A)-1biwhich is the transfer function from the attack(t)to output measurey(t).When hackers launch a data deception attack(t)=(t)on the actuator to make(s)=0,a zero dynamic attack occurs on the actuator.Obviously,a zero dynamic attack is undetectable. In addition,it is not possible for a hacker to launch a zero dynamic attack on the sensor,since the transfer function from the attack(t)to outputy(t)is(s)=cj0.
Remark 1.In the stochastic attack models(5)-(10),the attacked coef fi cientsfiandhjare column vectors.Herein only the element in thei-th row is 1 and the rest elements are 0 infi,which implies that only thei-th control channel of a control system is attacked.Similarly,only the element in thej-th row is 1 and the rest elements are 0 inhj,which implies that only thej-th output channel of a control system is attacked.
Remark 2.To attack a target,hackers may launch multiple attacks aiming at multiple communication channels so that the aggression opportunities are increased and the attack target is compromised,more stealthily and successfully.For example, in order to effectively disturb the formation control of multivehicle systems,a hacker could launch multiple stochastic cyber-attacks,which are respectively aiming at different communication links among these vehicles or aiming at multiple controller command input channels of a single vehicle.Obviously,the detection and isolation of multiple cyber-attacks are very important in the formation control of multi-vehicle systems.Therefore,the research on multiple cyber-attacks is signi fi cant,and requires further research.
III.MAIN RESULTS
In this section,we present the approach to the anomaly detection.We assume that the following conditions are satis fi ed: 1)the pair(A,B)is controllable;2)(A,C)is observable. For simpli fi cation of the discussion,we ignore the in fl uence of control inputs in the remainder of this paper because they do not affect the residual when there are no modeling errors in the system transfer matrix.Therefore,system(1)can be rewritten as follows:
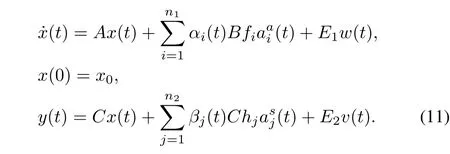
We set up the following anomaly detector:
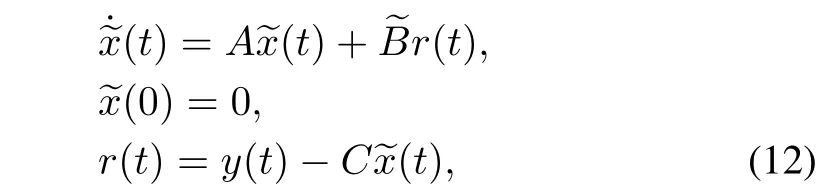
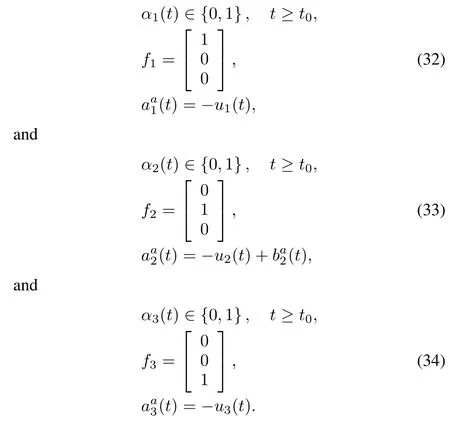
whereeBis the detector gain matrix andr(t)represents the output residual.
Lete(t)=x(t)-ex(t),then we obtain the following error dynamics:
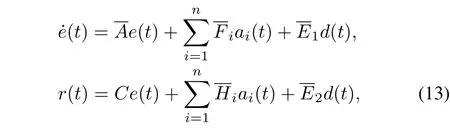
with the matrices
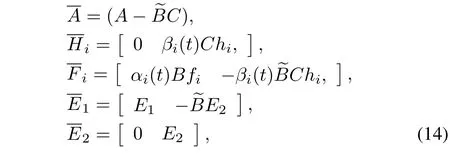
and the vectors
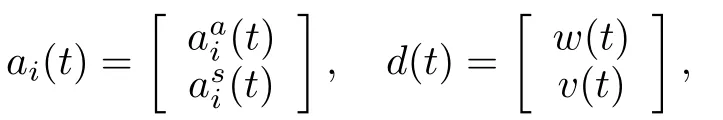
where cyber-attacks(t),(t),i=1,...,nand the vectors describing the attacked coef fi cientsfi,hi,i=1,...,nsatisfy the following conditions
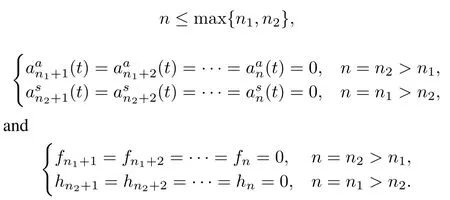
Before presenting the main results,we give the following de fi nition and lemma.
De fi nition 1.For anomaly detector error dynamics,if a cyber-attack on a control system leads to zero output residual, then the cyber-attack is undetectable.
IfTdr(s)=denotes the transfer function from stochastic disturbanced(t)to output residualr(t),the robust stability condition of error dynamic(13)is given in term of the following lemma.
Lemma 1[16].When all stochastic eventsαi(t)=βi(t)=0 (i=1,...,n),there are the following conclusions:
1)The error dynamics(13)without disturbances is asymptotically stable,if there exists a symmetric positive de fi nite matrixP>0 and a matrixXsuch that the following linear matrix inequality(LMI)holds
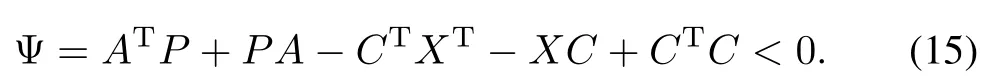
2)The error dynamics(13)with disturbancesd(t)(0(t)([0,∞);Rn))is robustly stable,if‖Tdr(s)‖∞<1 and if there exists a symmetric positive de fi nite matrixP>0 and a matrixXsuch that the following LMI holds
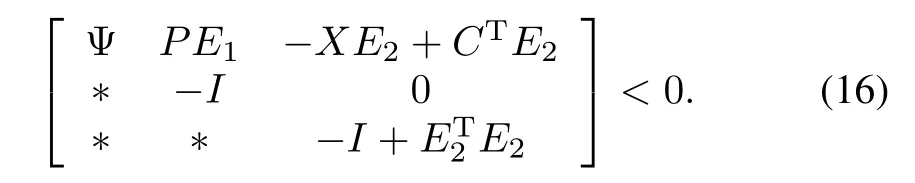
When the LMIs above are solvable,the detector gain matrix is given by=P-1X.
A.Algebraic Detection Scheme for Multiple Stochastic Cyberattacks Aiming at Multiple Communication Channels
In this section,using the frequency-domain description of the system,we transform the error dynamics(13)into the following equation:
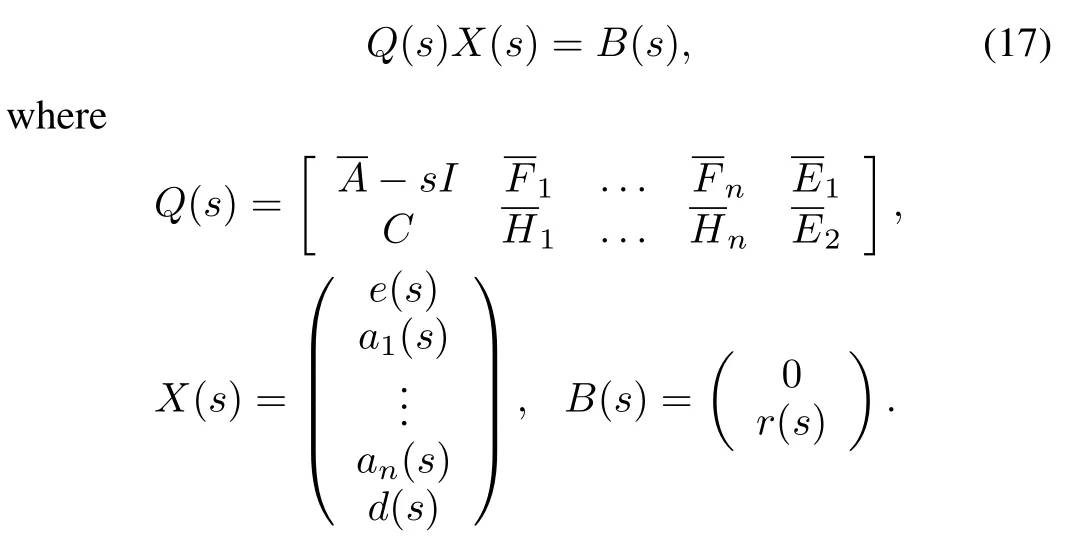
Further,in order to obtain effective results,we introduce the mathematical expectation of the stochastic matrixQ(s)as follows:
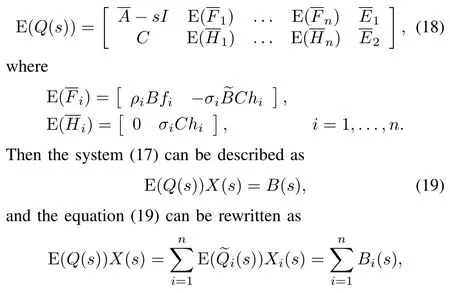
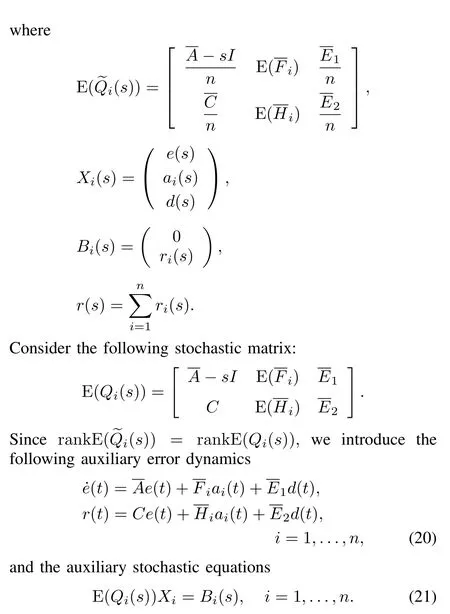
Remark 3.Here,since the matricesinclude the stochastic parametersαi(t)andβi(t),the system matrixQ(s)correspondingly includes these stochastic parameters, and E(Q(s))and E(Qi(s))include stochastic probabilitiesρiandσias well,which take values in[0,1].Therefore,they are stochastic matrices.
Remark 4.In this work,we introduce the auxiliary mathematical“tools”(20)and(21).The auxiliary error dynamics (20)represents the fact that the control system is only subjected to a stochastic cyber-attackai(t)on thei-th communication channel.Applying the auxiliary equation(21),we can obtain the information of residualri(t)that is caused by the cyber-attackai(t).In addition,the detector gain matrixeBcan be determined according to Lemma 1.
Now,applying the rank of the stochastic matrix,we obtain the following theorem.
Theorem 1.For system(11),we assume that all of these stochastic matrices E(Q(s))and E(Qi(s))(i=1,...,n) have full column normal rank.All of these cyber-attacksai(s)(i=1,...,n,(0(s))whens=z0are undetectable,if and only if there existsz0∈,such that
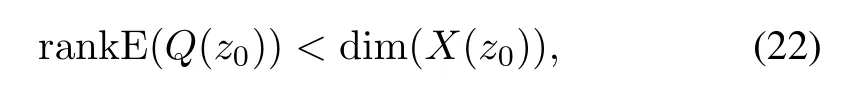
and
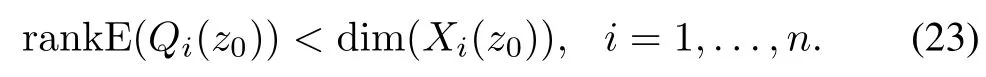
Hereinis a set of undetectable cyber-attacks.
Proof.(If)Assume that there existsz0∈C such that conditions(22)and(23)hold for allai(z0)it becomes obvious thatz0is an invariant zero[22]of the detector error system(13)and the auxiliary system(20).Then all of the equations in(19) and(20)are homogeneous,i.e.,B(z0)=0 andBi(z0)=0.Therefore,the output residualri(z0)=0,i=1,...,n,andr(z0)==0 as well.By De fi nition 1,all of these cyber-attacksai(s),i...,nwhens=z0are undetectable.
(Only if)Assume that all of these cyber-attacksai(s),i=1,...,nwhens=z0are undetectable,then there must exist az0∈C such that the residualri(z0)=0 andr(z0) =P=0.Therefore,all of the equations in(19) and(21)are homogeneous.If we assume that all of matrices E(Q(z0))and E(Qi(z0))have full column rank,then all of these homogeneous equations have and only have one zero solution.However,this contradicts with the conditions that
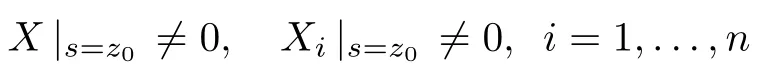
are solutions to(19)and(21),respectively.Therefore the assumptions are false,only conditions(22)and(23)are true.□
Theorem 2.For system(11),we assume that all of stochastic matrices E(Q(s))and E(Qi(s))(i=1,...,n)have full column normal rank.All of these cyber-attacksai(s)(i=1,...,n,(0(s)∈G))are detectable,if and only if the following conditions always hold for anyz0∈C:
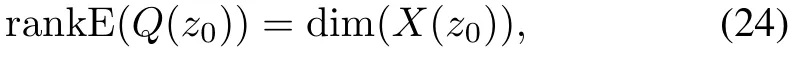
and
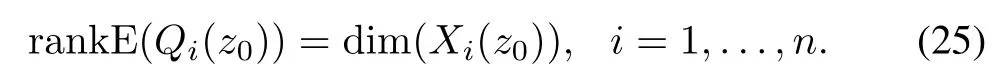
HereinGis a set of detectable cyber-attacks.
Proof.(If)Assuming that conditions(24)and(25)always hold for anyz0∈C,it is obvious that the stochastic matrices E(Q(z0))and E(Qi(z0))(i=1,...,n)have full column rank.Then the equation
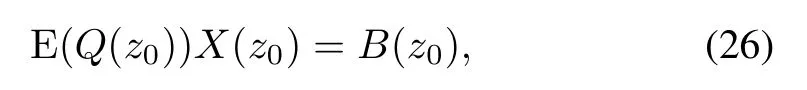
and the auxiliary stochastic equations
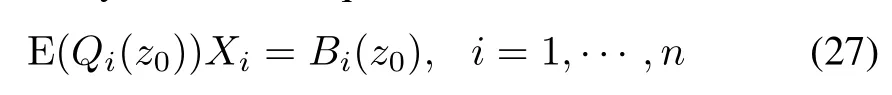
have one and only one solution.In the following,we proof by contradiction.Assume that residualr(z0)=0 andri(z0)=0,i=1,...,n,then equations(26)and(27)has one and only one zero solution,i.e.,
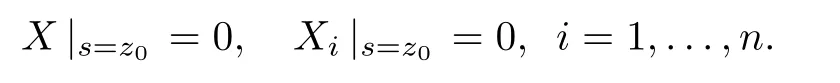
However,this violates the given condition 0(z0)∈G, i.e.,

Thereforer(z0)/=0 andri(z0)/=0,i=1,...,n,these cyber-attacksai(s)(0(s)∈G),i=1,...,n,for anys=z0are detectable.
(Only if)Assume that there exists az0∈C which satis fi es conditions(22)and(23).Since all of the stochastic matrices E(Q(s))and E(Qi(s))(i=1,...,n)have full column ranks, according to Theorem 1,these cyber-attacksai(s),i=1,..., nare undetectable ass=z0.However,this is in contradiction with the given condition that all of these cyber-attacksai(s), i=1,...,nare detectable for anys=z0.Therefore the assumption is false,only
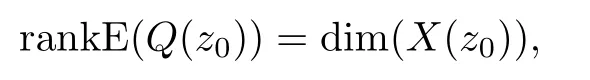
and
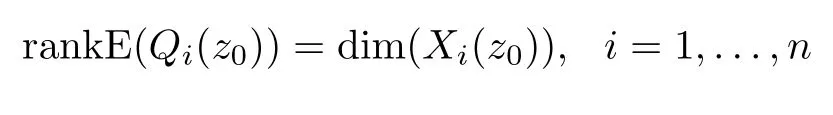
are true.
Furthermore,we can obtain the following corollary according to Theorem 1 and Theorem 2.
Corollary 1.For system(11),assume that all of stochastic matrices E(Q(s))and E(Qi(s))(i=1,...,n)have full column normal rank.If there existsz0∈C,such that
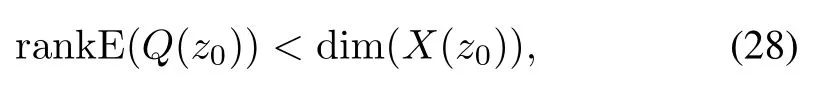
then there are the following conclusions.
1)The cyber-attackai(z0)(0(s)∈G)is detectable, if and only if
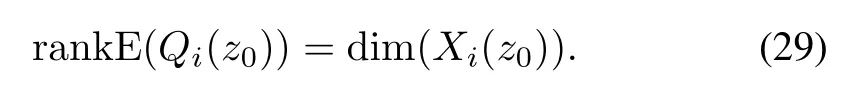
2)The cyber-attackaj(z0)(0(s)∈G)is undetectable, if and only if
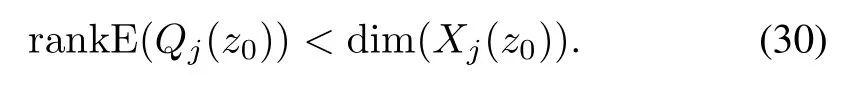
IV.SIMULATION RESULTS
In this section,we provide two simulation examples to illustrate the effectiveness of our results.In Example 1,we consider a control system under three stochastic cyber-attacks and a stochastic noise.We detect two possible stochastic data DoS attacks and a possible stochastic data deception attack, which are aiming at three controller command input channels on the actuator.In Example 2,we use the laboratory process as presented in[21],which consists of four interconnected water tanks.We will also detect possible cyber-attacks on QTP controlled through a wireless communication network.
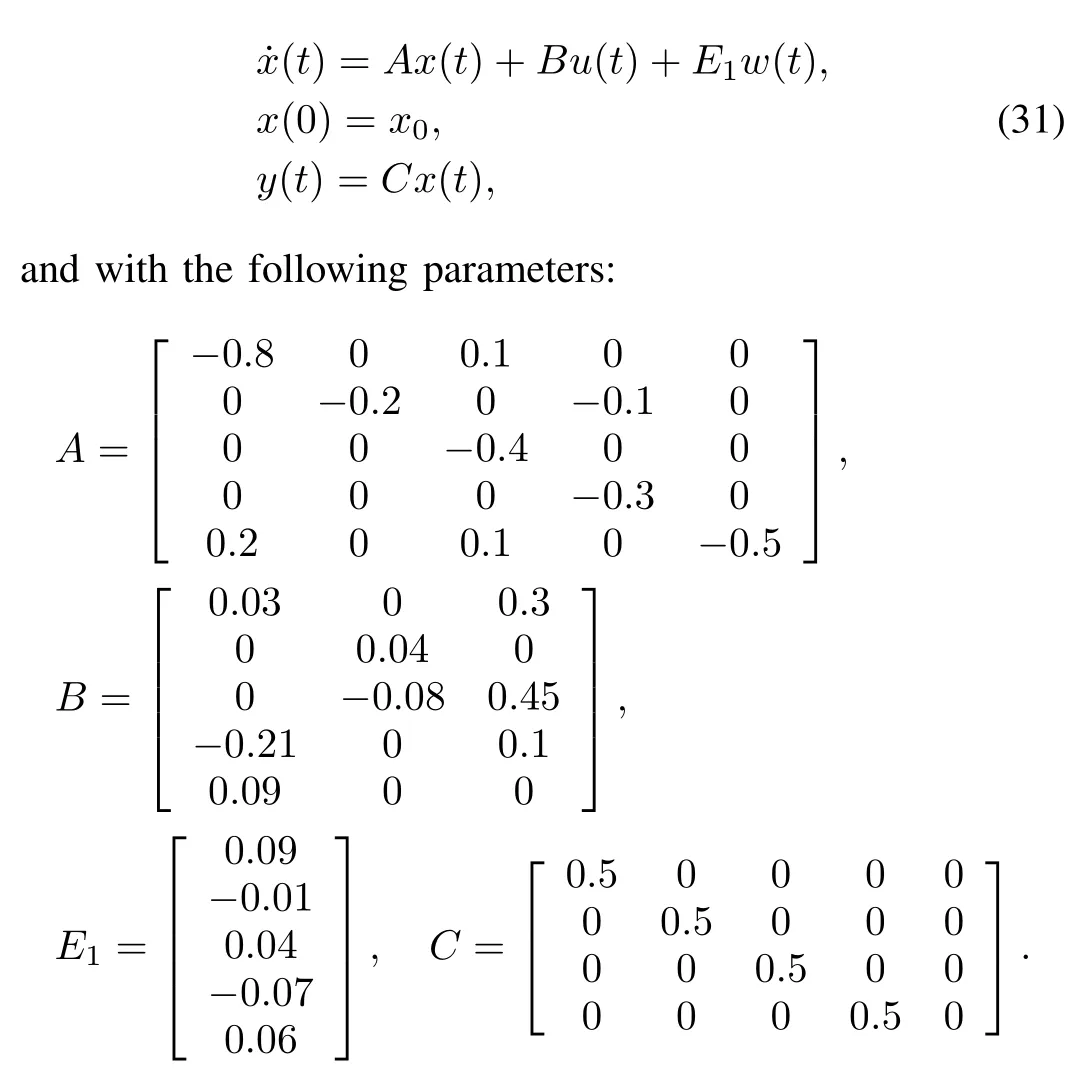
Example 1.Consider the following system with a stochastic noisew(t)
Assume that it is subjected to two stochastic data DoS attacks and a stochastic data deception attack on the actuator aiming at three controller command input channels,i.e.,
As mentioned before,we ignore the control input,since it does not affect the residual.
By applying Lemma 1,the robust detector gain matrix can be obtained as follows:

Set the initial conditions as=[0,0,0,0,0]Tandx(0) =[-0.2,0.4,0.8,-1,0.1]T.When the stochastic eventsα1(t) =α2(t)=α3(t)=0 occur,the system is not under any cyber-attacks.Fig.1 displays the time responses of the residual and the system state under stochastic noisew(t)only, which shows that the system is robustly stable.When the stochastic eventsα1(t)=α2(t)=α3(t)=1 occur,the system is under multiple cyber-attacks.We take the attack probabilitiesρ1=ρ2=0.8 andρ3=0.5,the stochastic matrix rank(E(Q(s)))=9,and rank(E(Q(z0)))=9,rank(E(Qi(z0)))=7(i=1,2,3),which shows that rank(E(Q(z0))),rank(E(Qi(z0)))(i=1,2,3)have always full column rank for anyz0.According to Theorem 2,the three attacks are detectable.Fig.2 displays the noise signal and the attack signals,while Fig.3 shows the time responses of the residual and the system state under three attacks and noise.Fig.4,Fig.5 and Fig.6 give the time responses of the residual under the attackaa1(t),aa2(t)andaa3(t),respectively. Simultaneously,they show the corresponding attack signals. The simulation results underline that these cyber-attacks can be effectively detected if the conditions in Theorem 2 are satis fi ed.
Example 2.Consider the model of the QTP in[21].
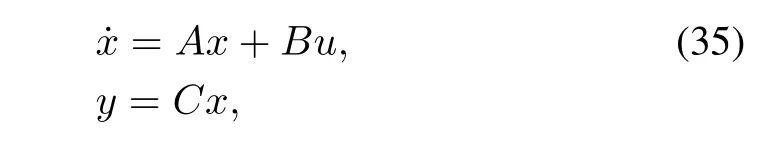
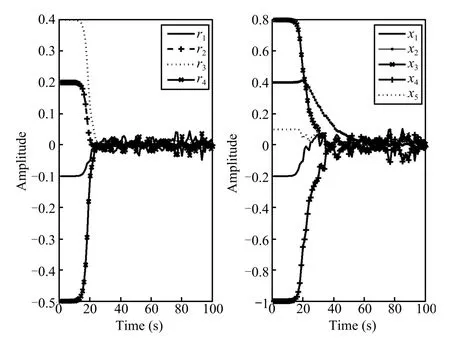
Fig.1.The time responses of the residual and the system state under the noise.
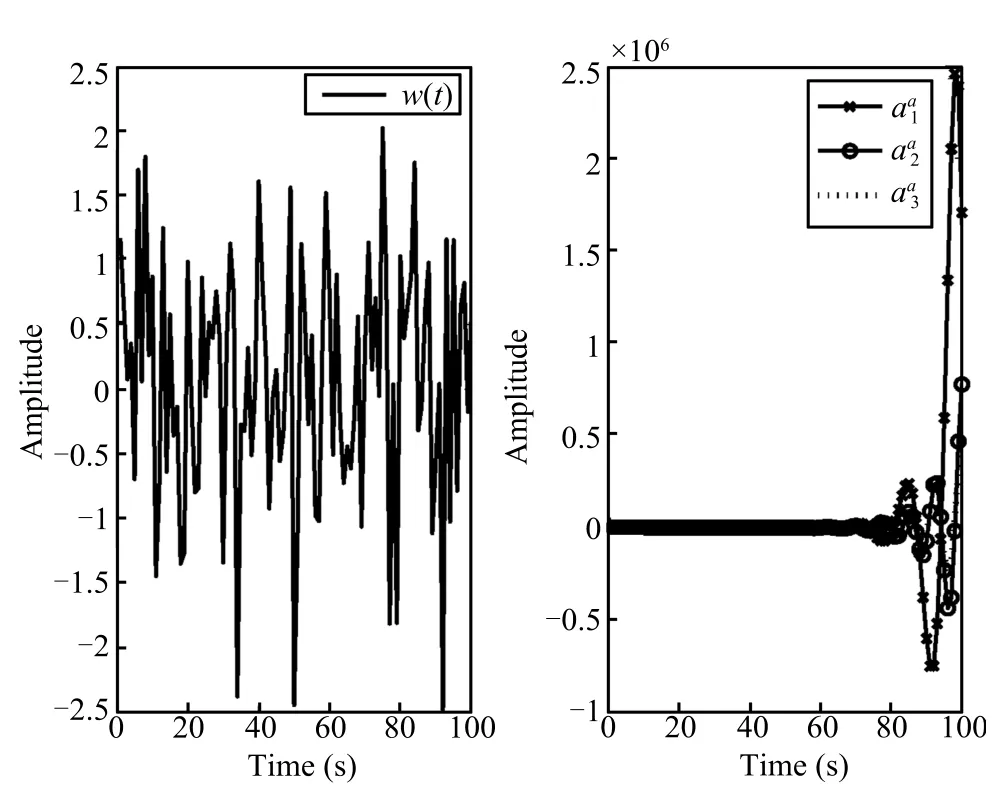
Fig.2.The noise signal and the attack signals.
with the following parameters:

Assume that it is subjected to two stochastic data deception attacks on the actuator,i.e.,
and
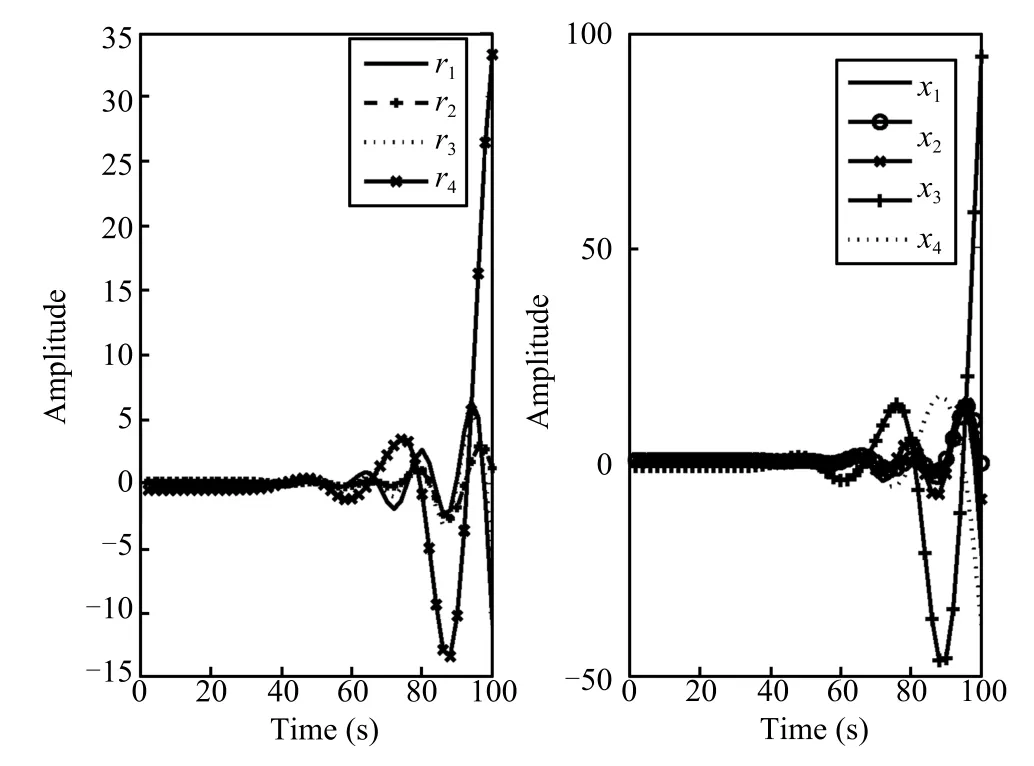
Fig.3.The time responses of the residual and the system state under three attacks and noise.
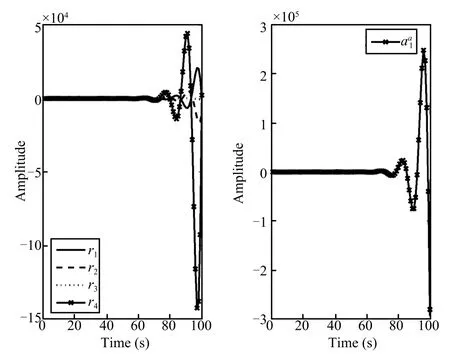
Fig.4.The time responses of the residual under attackand the attack signal
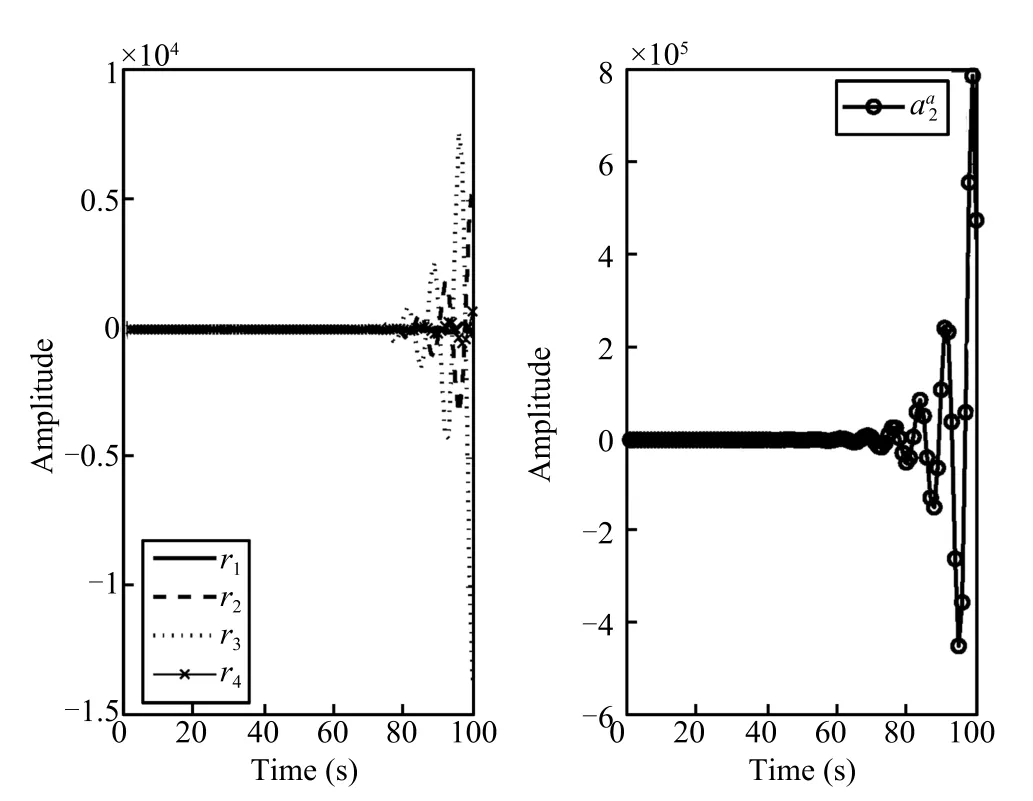
Fig.5.The time responses of the residual under attackand the attack signal
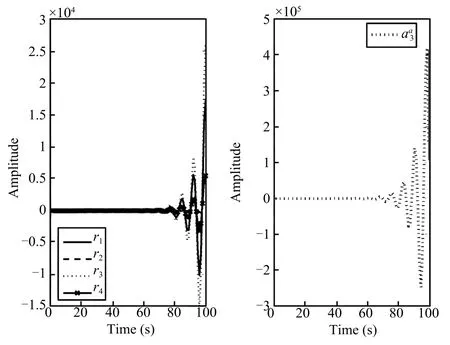
Fig.6.The time responses of the residual under attackand the attack signal
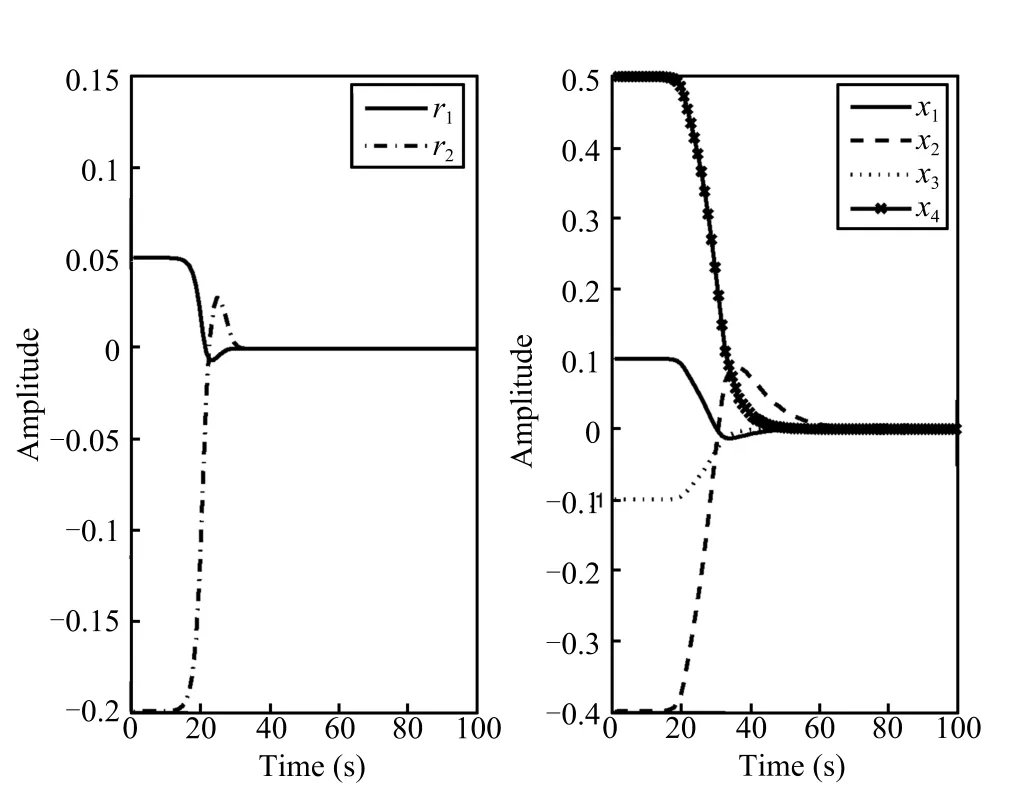
Fig.7.The time responses of the residual and the system state without attacks.
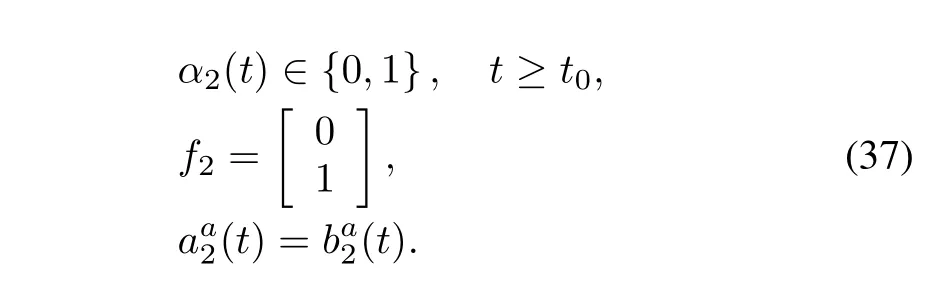
The detector gain matrix can be obtained as follows:

We set the initial conditions as ex(0)=[0,0,0,0]Tandx(0) =[0.1,-0.4,-0.1,0.5]T.When the stochastic eventsα1(t) =α2(t)=0 occur,Fig.7 visualizes that the system(35) is asymptotically stable.When the stochastic eventsα1(t)=α2(t)=1 occur and the attack probabilities areρ1=0.8,ρ2= 0.5,we have stochastic matrix rank(E(Q(s)))=6,however, there exists az0=0.0127 such that rank(E(Q(z0)))=5 and rank(E(Qi(z0)))=5(i=1,2).Aiming at two different con-trol channels,it is possible for the hacker to launch two stochastic data deception attacks as follows:

such that the transfer function from attacks to residual is zero. Therefore,it is dif fi cult to detect these stealthy attacks.Fig.8 displays the time responses of the residual and the system state under the two attacks(t)and(t),which shows that these attacks whens=z0=0.0127 could not be detected by original model.However,applying the auxiliary tools(20), (21)and according to Corollary 1,these attacks can also be detected.Fig.9 displays the attack signal(t)and the responses of the residual under this attack.Fig.10 shows the attack signal(t)and the responses of residual under this attack.Obviously,applying Corollary 1,the two stochastic data deception attacks can be detected effectively.
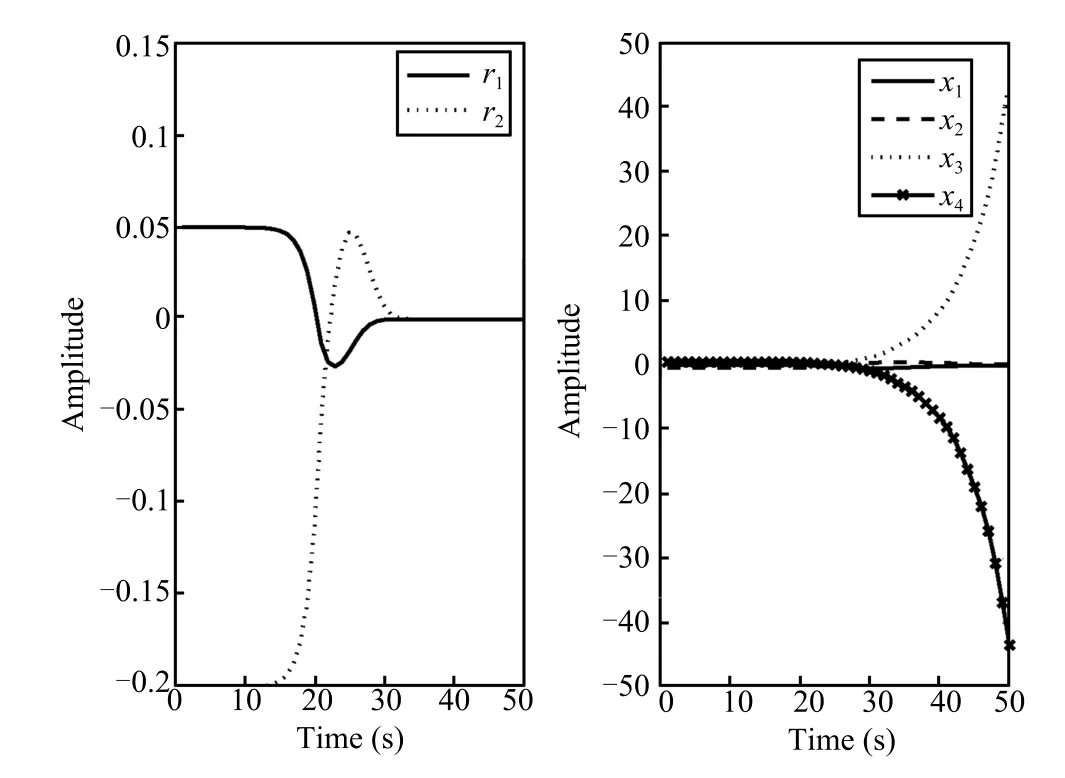
Fig.8.The time responses of the residual and the system state under attacks(t)and(t).
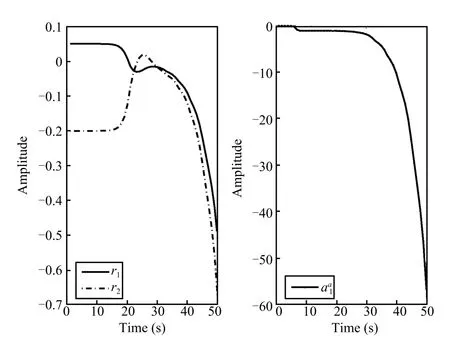
Fig.9.The time responses of residual under the attack(t)and the attack signal(t).
V.CONCLUSION
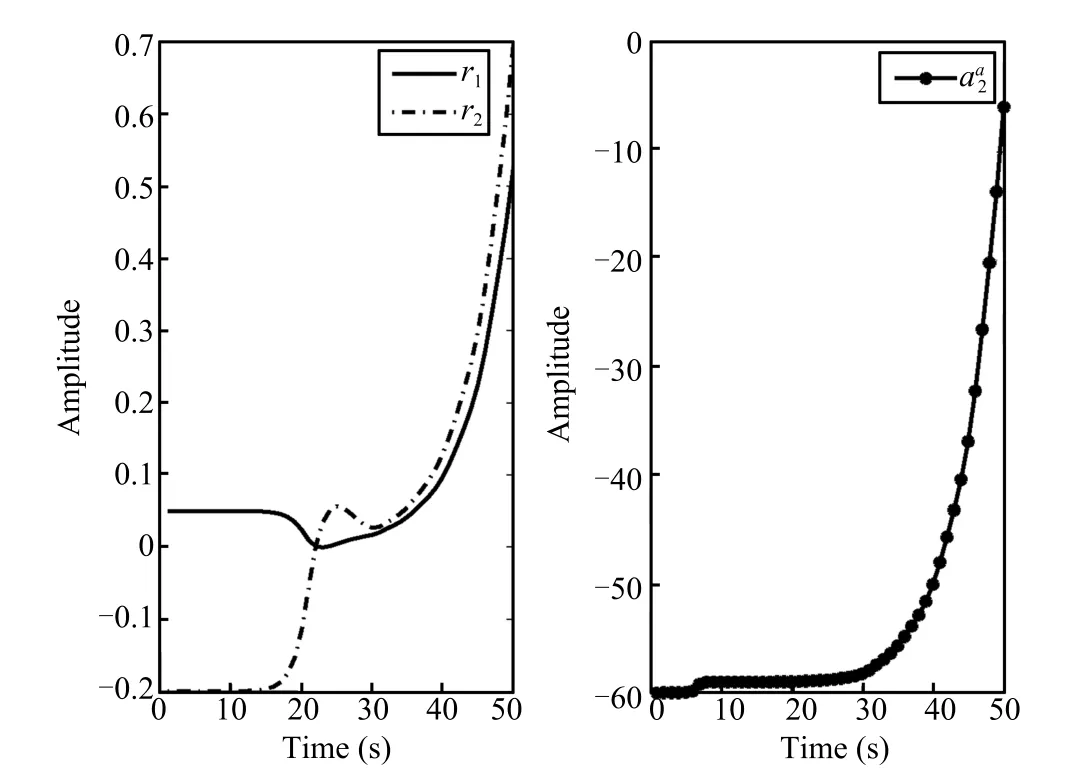
Fig.10.The time responses of residual under the attack(t)and the attack signal(t).
This paper presents a cyber-attack detection approach for control systems under multiple stochastic cyber-attacks and disturbances.The proposed problem is signi fi cant in practice, because hackers might launch multiple attacks aiming at one target so that the aggression opportunities are increased and the attack target can be compromised,more stealthily and successfully.For example,the hacker is able to simultaneously launch DoS attacks,deception attacks and replay attacks that are respectively aiming at different communication channels of a control system.The main work here is focused on novel cyber-attack detection schemes that allow the detection of multiple stochastic attacks in order to protect control systems against a wide range of possible attack models.We give two simulation examples the results of which demonstrate that the detection approaches proposed in this paper are feasible and effective.
REFERENCES
[1]Bier V,Oliveros S,Samuelson L.Choosing what to protect:strategic defensive allocation against an unknown attacker.Journal of Public Economic Theory,2007,9(4):563-587
[2]Amin S,Schwartz G A,Sastry S S.Security of interdependent and identical networked control systems.Automatica,2013,49(1):186-192
[3]Slay J,Miller M.Lessons learned from the Maroochy water breach.Critical Infrastructure Protection,2007,253:73-82
[4]Andersson G,Esfahani P M,Vrakopoulou M,Margellos K,Lygeros J,Teixeira A,Dan G,Sanderg H,Johansson K H.Cyber-security of SCADA systems.Session:Cyber-Physical System Security in a Smart Grid Environment,2011.
[5]Mo Y L,Sinopoli B.False data injection attacks in control systems.In: Proceedings of the 1st Workshop on Secure Control Systems.Stockholm, Sweden,2010.
[6]Amin S,Litrico X,Sastry S,Bayen A M.Cyber security of water SCADA systems:(I)analysis and experimentation of stealthy deception attacks.IEEE Transactions on Control Systems Technology,2013,21(5):1963-1970
[7]Eliades D G,Polycarpou M M.A fault diagnosis and security framework for water systems.IEEE Transactions on Control Systems Technology, 2010,18(6):1254-1265
[8]Metke A R,Ekl R L.Security technology for smart grid networks.IEEE Transactions on Smart Grid,2010,1(1):99-107
[9]Sridhar S,Hahn A,Govindarasu M.Cyber-physical system security for the electric power grid.Proceedings of the IEEE,2012,100(1):210-224
[10]Mohsenian-Rad A H,Leon-Garcia A.Distributed internet-based load altering attacks against smart power grids.IEEE Transactions on Smart Grid,2011,2(4):667-674
[11]Sardana A,Joshi R C.Dual-level attack detection and characterization for networks under DDoS.In:Proceedings of the 2010 International Conference on Availability,Reliability and Security.Krakow:IEEE,2010. 9-16
[12]Weimer J,Kar S,Johansson K H.Distributed detection and isolation of topology attacks in power networks.In:Proceedings of the 2012 HiCoNS′12.Beijing,China,2012.17-18
[13]Liu Y,Reiter M K,Ning P.False data injection attacks against state estimation in electric power grids.In:Proceedings of the 2009 ACM Conference on Computer and Communications Security.Chicago,IL, USA:ACM,2009.21-32
[14]Rosich A,Voos H,Li Y M,Darouach M.A model predictive approach for cyber-attack detection and mitigation in control systems.In:Proceedings of the 52nd Annual Conference on Decision and Control.Firenze: IEEE,2013.6621-6626
[15]Li Y M,Voos H,Rosich A,Darouach M.A stochastic cyber-attack detection scheme for stochastic control systems based on frequencydomain transformation technique.In:Proceedings of the 8th International Conference on Network and System Security.Xi′an,China:Springer, 2014.209-222
[16]Li Y M,Voos H,Darouach M.RobustH∞fault estimation for control systems under stochastic cyber-attacks.In:Proceedings of the 33rd Chinese Control Conference.Nanjing,China:ORBilu,2014.3124-3129
[17]Hashim F,Kibria M R,Jamalipour A.Detection of DoS and DDoS attacks in NGMN using frequency domain analysis.In:Proceedings of the 14th Asia-Paci fi c Conference on Communications.Tokyo:IEEE,2008.1-5
[18]Sundaram S,Hadjicostis C N.Distributed function calculation via linear iterative strategies in the presence of malicious agents.IEEE Transactions on Automatic Control,2011,56(7):1495-1508
[19]Teixeira A,Sandberg H,Johansson K H.Networked control systems under cyber attacks with applications to power networks.In:Proceedings of the 2010 American Control Conference.Baltimore,MD:IEEE,2010. 3690-3696
[20]Pasqualetti F,Bichi A,Bullo F.Consensus computation in unreliable networks:a system theoretic approach.IEEE Transactions on Automatic Control,2012,57(1):90-104
[21]Johansson K H.The quadruple-tank process:a multivariable laboratory process with an adjustable zero.IEEE Transactions on Control Systems Technology,2000,8(3):456-465
[22]Zhou K M,Doyle J C,Glover K.Robust and Optimal Control.Upper Saddle River,NJ,USA:Prentice-Hall,Inc.,1996.


Holger Voos studied electrical engineering at Saarland University,Germany,and received his Ph.D. degree in automatic control from the Technical University of Kaiserslautern,Germany,in 2002. He is currently a professor at the University of Luxembourg in the Faculty of Science,Technology and Communication,Research Unit of Engineering Sciences.He is the head of the Automatic Control Research Group and of the Automation and Robotics Research Group at the Interdisciplinary Centre of Security,Reliability and Trust(SnT)at the University of Luxembourg.His research interests include distributed and networked control,model predictive control,and safe and secure automation systems with applications in mobile and space robotics,energy systems and biomedicine.

Mohamed Darouach graduated from Ecole Mohammadia d’Ingnieurs,Rabat,Morocco,in 1978, and received the Docteur Ingnieur and Doctor of Sciences degrees from Nancy University,France,in 1983 and 1986,respectively.From 1978 to 1986 he was associate professor and professor of automatic control at Ecole Hassania des Travaux Publics, Casablanca,Morocco.Since 1987 he is a professor at University de Lorraine.He has been a vice director of the Research Center in Automatic Control of Nancy(CRAN UMR 7039,Nancy-University, CNRS)from 2005 to 2013.He obtained a degree Honoris Causa from the Technical University of IASI and Since in 2010.He is a member of the Scienti fi c Council of Luxembourg University.Since 2013 he is a vice director of the University Institute of Technology of Longwy(University de Lorraine). He held invited positions at University of Alberta,Edmonton.His research interests include span theoretical control,observers design,and control of large-scale uncertain systems with applications.

Changchun Hua received his Ph.D.degree from Yanshan University,China,in 2005.He was a research fellow in National University of Singapore Carleton University,Canada and University of Duisburg-Essen,Germany.Now he is a professor at Yanshan University,China.His research interests include nonlinear control systems,control systems design over network,teleoperation systems,and intelligent control.
received her Ph.D.degree in control theory and control engineering from Yanshan University,China,in 2009.She is currently a research associate at the Interdisciplinary Centre of Security, Reliability and Trust(SnT)at the University of Luxembourg.Her research interests include intelligent control and stochastic systems,secure and resilient automation control systems,distributed control,and cooperative control of multiagent system.Corresponding author of this paper.
Manuscript received September 30,2014;accepted January 24,2015.This work was supported by the Fonds National de la Recherche,Luxembourg (CO11/IS/1206050(SeSaNet))and National Natural Science Foundation of China(61273222).Recommended by Associate Editor Xinping Guan.
:Yumei Li,Holger Voos,Mohamed Darouach,Changchun Hua. An algebraic detection approach for control systems under multiple stochastic cyber-attacks.IEEE/CAA Journal of Automatica Sinica,2015,2(3):258-266
Yumei Li and Holger Voos are with the Interdisciplinary Centre for Security Reliability and Trust(SnT),University of Luxembourg,Luxembourg L-2721, Luxembourg(e-mail:yumei.li@uni.lu;holger.voos@uni.lu).
Mohamed Darouach is with the Centre de la Recherche en Automatique de Nancy(CRAN),Universite de Lorraine,Longwy 54400,France(e-mail: modar@pt.lu).
Changchun Hua is with the Institute of Electrical Engineering,Yanshan University,Qinhuangdao 066004,China(e-mail:cch@ysu.edu.cn).
 IEEE/CAA Journal of Automatica Sinica2015年3期
IEEE/CAA Journal of Automatica Sinica2015年3期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- Dynamic Coverage with Wireless Sensor and Actor Networks in Underwater Environment
- Cyber-physical-social System in Intelligent Transportation
- Decentralized Event-Triggered Average Consensus for Multi-Agent Systems in CPSs with Communication Constraints
- Cyber-physical Modeling and Control of Crowd of Pedestrians:A Review and New Framework
- An Approach of Distributed Joint Optimization for Cluster-based Wireless Sensor Networks
- Robust Dataset Classi fi cation Approach Based on Neighbor Searching and Kernel Fuzzy C-Means
