Novel attribute-based framework for halftone watermarking
XIE Kun(谢琨), ZHENG Hai-hong(郑海红), ZENG Ping(曾平),2,,WANG Quan(王泉), GUO Tao(郭涛)
(1.School of Computer and Science, Xidian University, Xi’an 710071, China;2.College of Computer Science, Xi’an Shiyou University, Xi’an 710065, China)
Novel attribute-based framework for halftone watermarking
XIE Kun(谢琨)1, ZHENG Hai-hong(郑海红)1, ZENG Ping(曾平),WANG Quan(王泉)1, GUO Tao(郭涛)1
(1.School of Computer and Science, Xidian University, Xi’an 710071, China;2.College of Computer Science, Xi’an Shiyou University, Xi’an 710065, China)
A novel attribute-based framework is proposed to tackle the problem of halftone watermarking in combination of the spatial/transformation domain. The challenge is that the host image is continuous, while the watermarked halftone is bi-level. To search for a solution, an attribute image is defined as a good connection between the original grayscale image and its halftone image. When the attribute image is used as a watermark carrier, it helps to find the watermarked halftone efficiently by solving a constrained modified direct binary search problem. Experimental results demonstrate that the proposed scheme in comparison with other similar methods maintains high watermark capacity with good image quality, high robustness, processing efficiency and easy decoding. Especially it has a good performance in printing application.
digital halftoning; digital watermarking; attribute image; transformation domain
Digital halftoning[1]is the technique of rendering continuous tone images on binary display devices and printers which can reproduce image only in two levels, black and white. A halftone image is perceived as continuous tone image when viewed at a distance due to the low-pass effect in the human visual system (HVS). Halftoning is extensively used in computer printouts, books, newspapers and magazines. There are many halftone methods, such as ordered dither-ing[2], error diffusion[3], direct binary search (DBS)[4], etc.
Halftone watermarking methods are used to embed watermarks, e.g., secrete information, into halftone images for printing security documents such as ID card, passport, confidential documents as well as currency, and preventing from illegal duplication and forgery by further scanning these documents to digital forms. The common watermarking methods which were designed for continuous tone images could not be applied to halftone images directly. Therefore, halftone watermarking is becoming increasingly significant that need to be addressed. In recent years, many halftone watermarking methods have been proposed, and most of them embed watermark in spatial-domain (SD)[5-12]. Ref.[8] is a state-of-the-art method in spatial-domain, which embeds watermark by changing the parity of the pixel and employing noise-balanced error diffusion. But it has to quantize the watermarked image to a binary image before decoding the watermark and it is sensitive to pre-processes after print-and-scan. Currently, only a few studies take the advantage of watermarking in transformation-domain (TD) and SD meanwhile. Ref.[13] introduced a robust feature-based digital watermarking method by binding the watermark with the geometrically invariant features of the halftone image. But there is a false-alarm probability in detection (no watermark embedded but detected having one), so it has to use the original watermark as a reference during decoding. Another drawback is its low watermark capacity. Ref.[14] presented a framework to jointly halftone and watermark a grayscale image. It spread the watermark into the DCT domain of the grayscale image, and the watermarked halftone is achieved by searching in the halftone space and minimizing a joint cost function which is constructed by HVS-based error and correlation output. The approach is reported to be extremely resilient to printing, scanning, and post-processing. However, little work has been done on how to embed a meaningful watermark under this framework. Moreover, it suffers from complex solutions for acquiring initial halftone and further optimization. Furthermore, it needs an original watermark in decoding. Therefore, further studies are still necessary to make the framework simple, general and effective.
In this paper, we develop a novel halftone watermarking framework jointly working in SD and TD. With the objective quality evaluation, the performance of this method is outstanding in image quality, watermark rate, robustness, and watermark-rate flexibility.
The remainder of this paper is organized as follows: Section 1 briefly describes the framework of halftone watermarking. In Section 2, the four stages of the proposed method are discussed in details. In Section 3, its effectiveness is demonstrated by various experiments and section 4 concludes this paper.
1 Halftone watermarking framework
Fig.1 illustrates the main motivation of our approach. The grayscale image (Fig.1a) and its DBS halftone image (Fig.1b) are quite different both in space and frequency domain, so it is difficult to obtain a good watermarked halftone image in SD when watermark is introduced in the frequency domain of the original grayscale image. To solve this problem, a common attribute is extracted from Fig.1a and Fig.1b and the corresponding attribute images are shown in Fig.1c and Fig.1d. The high similarity between the two attribute images makes it easy to find the required watermarked halftone image when the watermark is embedded in the frequency of attribute image.

Fig.1 Grayscale image, DBS halftone image and the corresponding attribute images
The framework of our method contains four main stages, and the flowchart is given in Fig.2. Letf(m,n)andg(m,n)denotethegrayscaleimageandthewatermarkedhalftoneimage,respectively.Inthefirststage,theattributeimageisdesignedbymeetingtwoconditions: ①commonpropertyofgrayscaleimageanditshalftoneimage;and②continuoustone.Supposetheattributeimageoff(m,n)isM,thewatermarkisembeddedinitstransformationdomainandtheresultisdenotedbyM′.Inthethirdstage,aninitialhalftoneimageisgeneratedforgettinganewhalftoneimagewhoseattributeimageisasclosetoM′aspossible,andthenewhalftoneimageisfurtheroptimizedbasedonthemodifiedDBSwithM′unchanged.Inthisway,thewatermarkedhalftoneisobtainedwithagoodvisualqualityaswellasahighwatermarkdecodingrate.Beforedecoding,thescannedembeddedhalftoneimageshouldbecorrectedonrotationandimagesizewithPhotoshop.Lastly,watermarkisretrievedwiththecorrespondingdecodingtechniques.
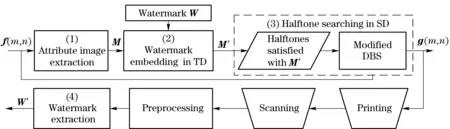
Fig.2 Block diagrams for halftone watermarking framework
2 Proposed method
Basedontheframeworkdevelopedabove,thismethodcanbeimplementedasbelow,asimilarattributeimagebetweenthegrayscaleimageandthehalftoneimageisdefinedatfirst,thenaspreadspectrumwatermarkingalgorithmwithacorrespondingwatermarkextractionmeasureisdesigned,nextasearchstrategyisemployedtofindthewatermarkedhalftoneimagewithhighquality.
2.1Attributeimageextraction
ThecharacteristicsoftheHVSshowthatwhenanobserverlooksatasmallareaofanimagefromacertaindistance,eyesonlyperceivetheaverageintensityofthislocalarea.Thatistosay,thoughthehalftoneimageisquitedifferentfromthegrayscaleimageineachpixel,theyaresimilarwitheachotherinalocalarea.Inaddition,itiscontinuousforbothgrayscaleandhalftone.Therefore,theaverageintensityofablockintheimageischosentoformtheattributeimage.
Toprovetheeffectiveness,theexperimentsareperformedasfollows.First,thegrayscaleimage,thecorrespondingFloyderrordiffusionhalftoneimageandthehalftoneimageafterprint-and-scan(wecallitPS-halftone)ofsize256×256aredividedinto8×8blocks.ThentheaverageofeachblockiscalculatedandsomedataareshowninFig.3.
InFig.3itcanbeobservedthat: ①theaverageintensityofthegrayscaleimageanditshalftoneimagearealmostidenticalwitheachother;and②theoneofPS-halftoneisalittledifferentfromthatoftheothertwoimagesduetotheimperfectionofprintandscanprocess.However,thevariationtrendissimilar,whichmeansthatthealternatingcurrent(AC)coefficientsinthefrequencyofattributeimagearestillkeptafterprint-and-scan,whereitissuitabletoembedwatermark.
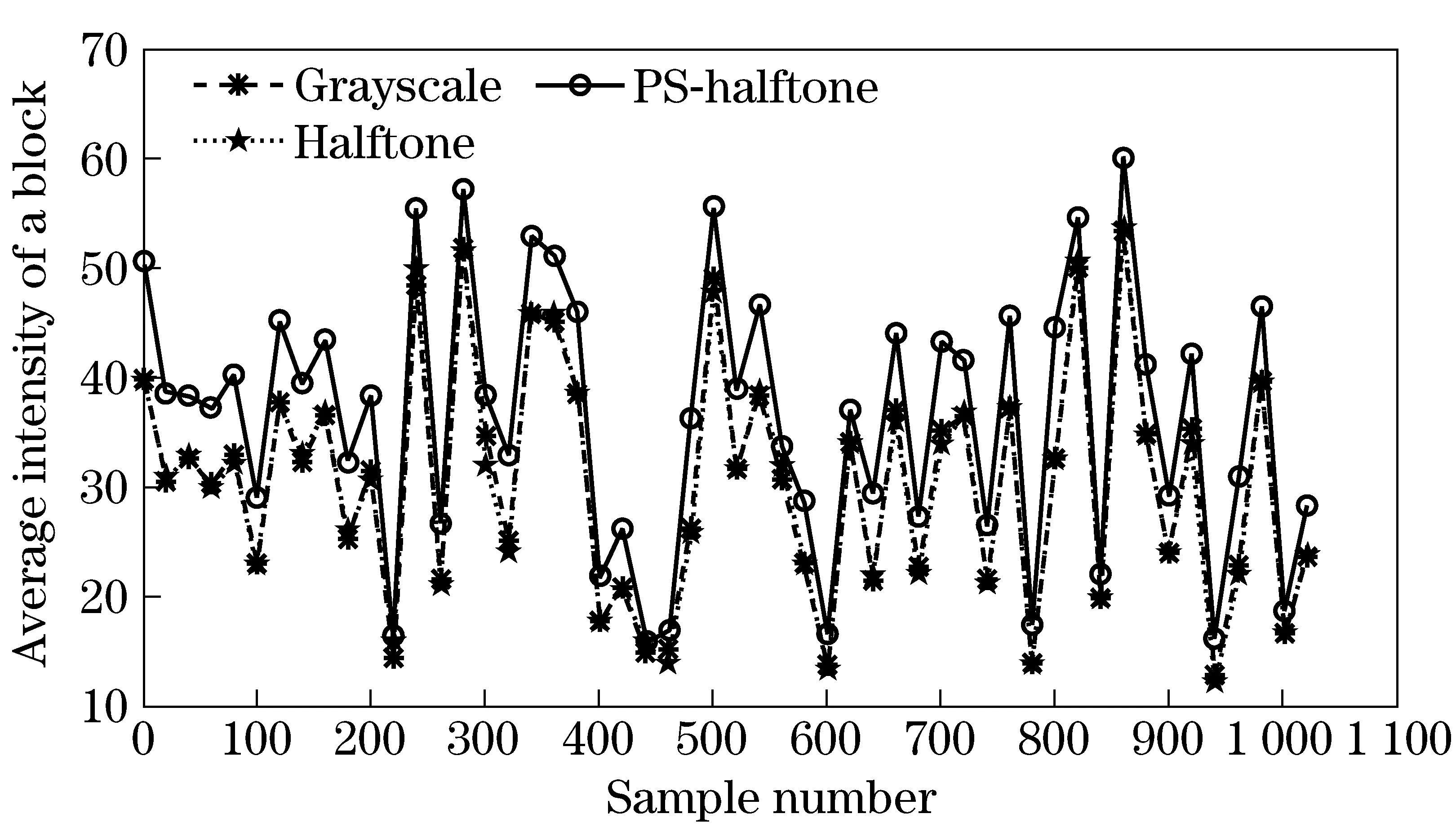
Fig.3 Relationship among the attribute of grayscale image, halftone image and PS-halftone image
2.2WatermarkembeddinginTD
SupposetheattributeimageisdenotedasM,watermarkembeddingprocessisdescribedasfollows.First,MisdividedintoblocksofsizeP×QandDCTisperformedoneachblock.Then,itistransformedintoavectoraccordingtotheZig-ZagsequencetogetF(l),wherel=1,2,…,PQ.IfascrambledwatermarkisdenotedbyW(i),thenwechangethevalueofF(l)inaninverseZig-Zagsequence,andLbitscanbeembeddedwith
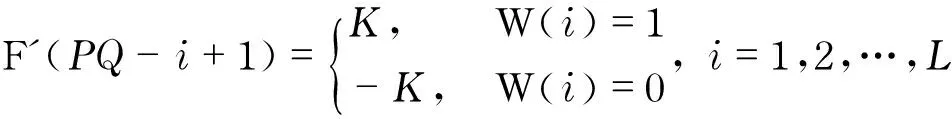
(1)
whereKis the watermark embedding strength.Lequals to the number of watermark bits divided by the number of blocks. After Re-arrangingF′(l)intoP×QblockandtakingIDCT,thewatermarkedattributeimageM′isobtained.
2.3WatermarkedhalftonesearchinginSD
AccordingtothewatermarkedattributeimageM′,ahighqualitywatermarkedhalftoneimageshouldbefoundwhoseattributeimageisasclosetoM′aspossible.Thefollowingtwostepsareusedtoaddressthisproblem.
2.3.1Initialwatermarkedhalftone
Anykindofhalftonemethodcanbeselectedtoobtainaninitialhalftoneimage.Inthispaper,Floyderrordiffusionischosenandthecorrespondinghalftoneimageisdenotedbyg0(x,y).Asitisknown,itsattributeimageisnotalwaysthesameasM′,sotoggleoperationisemployedtofulfillit.
TheblocksizeusedforattributeimageisR×S.Ifawhite/backpixelistoggled,theaverageintensityofthisblockdecreases/increases255/(R×S).Underthisrelationship, |N(i,j)|pixelsofthe(i,j)thblocking0(x,y)shouldbetoggled,andN(i,j)iscalculatedasfollows:
N(i,j)=Round[(M0(i,j)-
M′(i,j))/(255/(R×S))]
(2)
whereM0(i,j)istheaverageofthe(i,j)thblocking0(x,y).IfN(i,j)>0, |N(i,j)|whitepixelsarerandomlychosentobetoggled,otherwise|N(i,j)|blackpixelsarerandomlychosentobetoggled.Thustheinitialwatermarkedhalftoneisobtainedandmarkedasg1(x,y).
2.3.2Block-basedmodifiedDBS
2.4 Watermark extraction

(3)
3 Experimental results
To evaluate the performance of the proposed approach quantitatively, correct decoding rate (CDR) and HVS-based peak signal-to-noise ratio (HPSNR)[15]are used. CDR is defined as
(4)
wherewi,jandw′i,jstand for the original watermark and the decoded watermark respectively, and the notation ΘstandsfortheNotexclusiveORoperation(XNOR).AhigherCDRvalueindicateshighercertaintyofthedecodedwatermark.HPSNRisusedtoestimateimagequaityanditisdefineas
HPSNR=
(5)
Therexi,jandbi,jdenote the pixel values of an original grayscale image and its corresponding halftone image, respectively. The variableFm,ndenotes a 2-D Gaussian filter with size 7×7 and σ=1.3.
Intheexperiments,eightimages(Macaw,Lena,Mandrill,Airplane,Tank,Pepper,LakeandBoat)ofsize2 048×2 048showninFig.4areusedastestimages,andawatermarkofsize64×64isembedded.Thesizeoftheblockissetto8×8whichisusedtogettheattributeimageandtakeDCT.Fig.5showstheembeddedhalftoneimagequalitiesandcorrectdecodingratesundertendifferentlevelsofwatermarkstrengthK(1,2,3,4,5,10,15,20,25,30)withoutanyattack,inwhichtheaveragevalueoftheeighttestimagesmentionedbeforeisshown.Amongthemostcommonhalftonemethodsincurrentuse,DBSoffersthebestimagequality.TheaverageHPSNRofDBShalftoneoftheeighttestimagesis38.22dB,andthelowestHPSNRofourwatermarkedimageis35.86dB.Itindicatesourmethodcanmaintainagoodimagequality.InFig.5a,itdemonstratesthattheimagequalitydecreasesasKincreases,butCDRrisessignificantly.Itisworthmentioningthatthewatermarkstrengthlevelof20isagoodexperimentalvalue.Atthissetting,itcanachievebothagoodimagequalityandahighcorrectdecodingratesimultaneously.Moreover,HPSNRandCDRdidn’tdecreaseobviouslyeventhewatermarkedimagesufferedfromprint-and-scan.
Fig.4 Thumbnail of eight test images
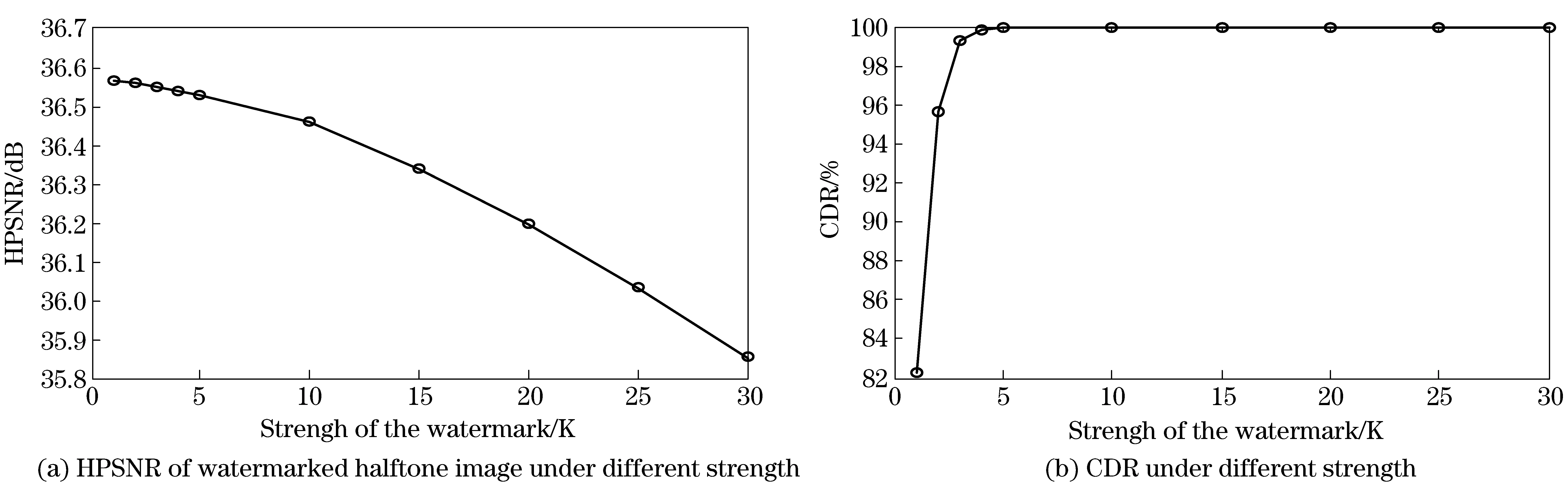
Fig.5 HPSNR and CDR under different strength
Fig.6demonstrateswatermark-rateflexibility.Fig.6a-Fig.6bshowtheoriginalwatermarkofsize64×64and1 024×1 024.Fig.6c-Fig.6dshowthewatermarkedhalftoneimagesofHPSNRat36.29dBand35.56dB,withthewatermarksshowninFig.6a-Fig.6b.Theresultsshowthatevenifwatermarkrateincreases,agoodimagequalitystillcanbeachieved.Fig.6e-Fig.6fshowtheextractedwatermarksfromFig.6c-Fig.6dwithCDRat100%and77.89%,respectively.Toembedwatermarkofsize1 024×1 024,wesettheblocksizeat2×2togettheattributeimage.Thesizeofblockcanbeconsideredasasecretkeytoprovideahighersecurity.Withthedecreaseofblocksize,thedifferencebetweenthetwoattributeimagescomesfromgrayscaleimageandhalftoneimageislarger,soCDRdecreasesinFig.6f.
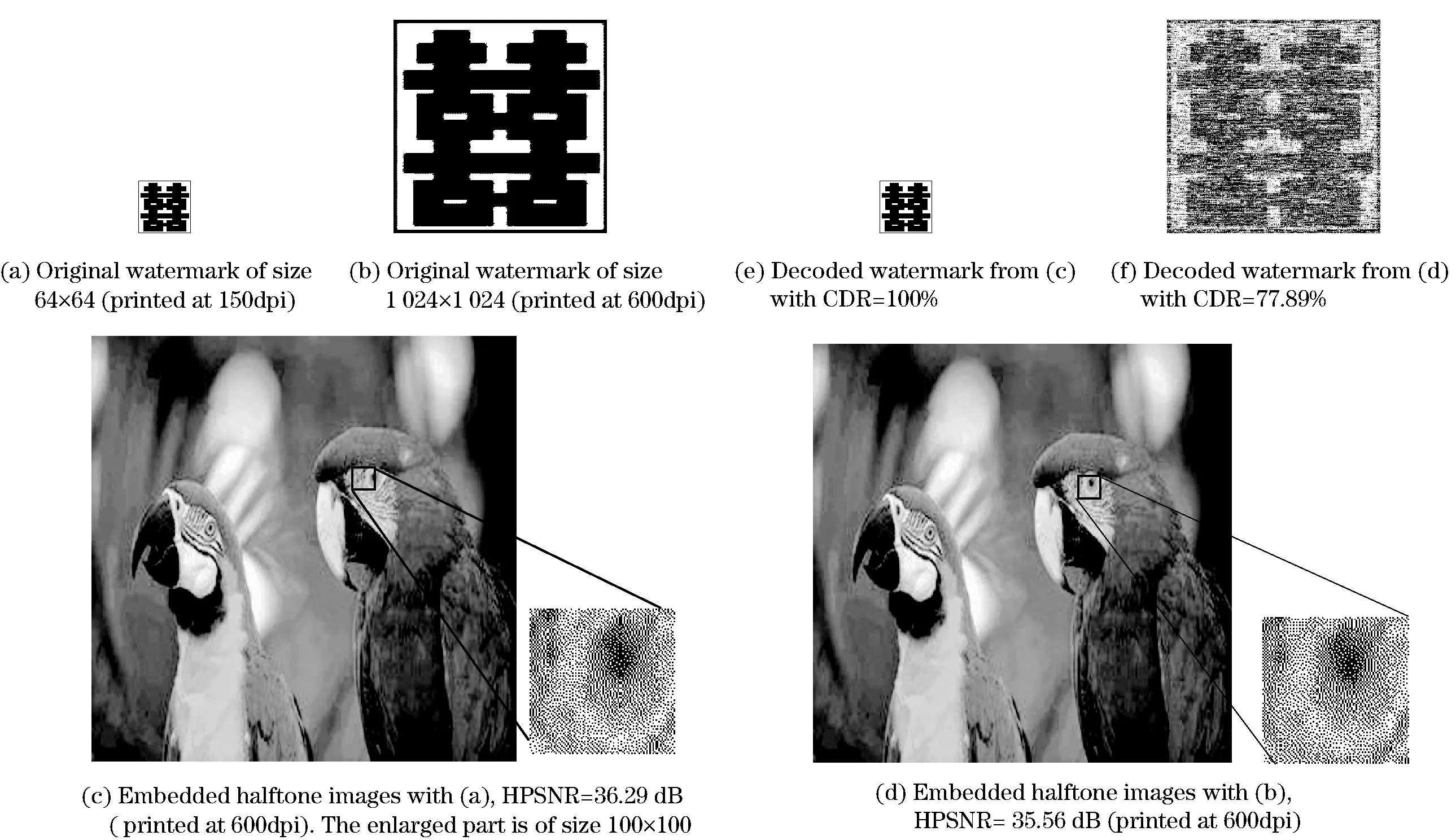
Fig.6 Experiments under different watermark-rates

Fig.7 Samples under various attacks
Inordertotesttherobustnessoftheproposedmethod,differentattacksincludingcropping,noising,JPEGcompression,darkening,scaling,rotating,tamperingandprint-and-scanarecarriedoutinFig.6c.Fig.7a-Fig.7ishowthewatermarkedimageundervariousattacksandthecorrespondingextractedwatermarks.Intheexperimentsagainstprint-and-scanattack,thewatermarkedhalftoneimageisprintedfirstlybyHPColorLaserJetCP2025at300dpi,andthentheprintedimageisscannedbyEPSONPerfection1 200Uat300dpi.Beforethedecodingprocess,thewatermarkedPS-halftoneimageneedstobecroppedbyAdobePhotoshop7.0.Afterthat,itneedstobetransformedintosizeof2 048×2 048byusinganinterpolationoperation,becausethesizeofprint-and-scanimageisgenerallylarge.InFig.7,itcanbeseenthattheproposedmethodcanachievehighrobustnessagainstvariousattacks.
Atlast,ancomprehensiveperformancecomparisonsbetweenourmethodandRef.[8]aresummarized.AgrayscaleMacawofsize2 048×2 048andawatermarkofsize64×64areusedintheexperiment,andthewatermarkstrengthissetto20.TheHPSNRofourwatermarkedimageis36.29dB,anditishigherthanthatinRef.[8]whichequalsto34.82dB.Themaximumwatermarkcapacityofthetwomethodsisidentical.Tab.1showsthedifferentrobustnessbetweenourmethodandthatinRef.[8],andabetterperformancecanbeobtainedbytheproposedmethodagainstthedifferentattacksmentionedabove.
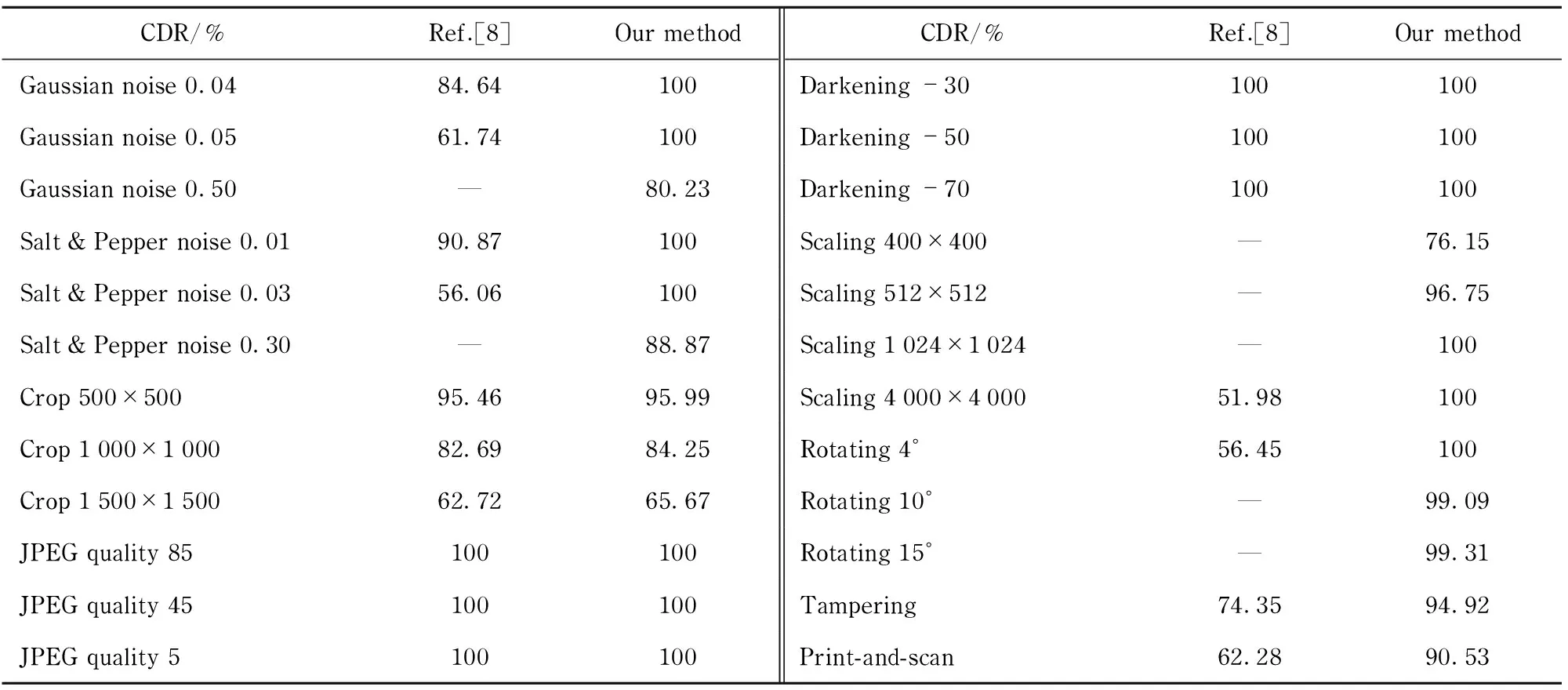
Tab.1 Robustness comparisons with Ref.[8]
—denotes that extracted watermark can not be distinguished
4 Conclusions
In this paper, a novel attribute-based halftone watermarking method was proposed. The main objective of this technique is to embed meaningful watermarks into halftone images by exploiting the good properties of watermarking techniques in transformation domain. The attribute image is the connection between the grayscale and its halftone. It makes it easy to embed watermarks in the transformation domain and get the watermarked halftone in spatial domain. The proposed framework has three advantages listed in the following:
①Effectiveness, the watermarking method based on transformation domain is generally better than that on spatial domain in robustness and invisibility.
②Simplicity, the attribute image assists in finding the initial watermarked halftone easily without iterations, and parameters are free in optimization.
③Generality, different attributes can be selected in the first stage and any grayscale watermarking schemes in transformation domain can be applied in the second stage. That is to say, appropriate choices can be made for each stage with regard to different applications. Besides, not only a pseudo-random sequence, but also a meaningful image can be embedded.
[1] Ulichney R A.Digital halftoning[M]. Cambridge, MA: MIT Press, 1987.
[2] Ulichney R A. The void-and-cluster method for dither array generation[J].Proc SPIE, Human Vision Visual Processing and Digital Displays IV, 1993, 1913:332-343.
[3] Zhen H. Hierarchical error diffusion[J]. IEEE Transactions on Image Processing,2009, 18(7):1524-1535.
[4] Analoui M, Allebach J P. Model based halftoning using direct binary search[J]. Proc SPIE, Human Vision, Visual Processing, and Digital Display III,1992, 1666:96-108.
[5] Fu M S, Au O C. Data hiding watermarking for halftone images[J]. IEEE Transactions on Image Processing, 2002,11(4):477-484.
[6] Jiang W, Ho A T S, Treharne H.A novel least distortion linear gain model for halftone image watermarking incorporating perceptual quality metrics[J]. Transactions on Data Hiding and Multimedia Security IV, LNCS, 2009,5510:65-83.
[7] Bulan O, Sharma G, Monga V. Orientation modulation for data hiding in clustered-dot halftone prints[J]. IEEE Transaction on Image Process, 2010,19(8):2070-2084.
[8] Guo J M, Pei S C, Lee H. Watermarking in halftone images with parity-matched error diffusion[J]. Signal Processing, 2011,91(1):126-135.
[9] Fu M S, Au O C. A multi-bit robust watermark for halftone images[C]∥International Conference on Multimedia and Expo, Baltimore,USA, 2003, 2: 213-216.
[10] Sherry P, Savakis A. Improved techniques for watermarking halftone images[C]∥International Conference on Acoustics, Speech, and Signal Processing Proceedings,Quebec,Canada, 2004,5:V-1005-1008.
[11] Guo J M, Su C C, Liu Y F. Oriented modulation for watermarking in direct binary search halftone images[J]. IEEE Transactions on Image Processing, 2012,21(9):4117-4127.
[12] Guo J M, Tsai J J. Data-hiding in halftone images using adaptive noise-balanced error diffusion[J]. IEEE Multi-Media, 2011,18(2):48-59.
[13] Wang X Y, Xu Z H, Niu P P. A feature-based digital watermarking scheme for halftone image[J]. International Journal of Electronics and Communications, 2010,64(10):924-933.
[14] Kacker D, Allebach J P. Joint halftoning and watermarking[J].IEEE Transactions on Image Processing,2003,51(4):1054-1068.
[15] Guo J M, Su C C, Liu Y F. Texture orientation modulation for halftoning watermarking[J]. IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP),Japan, 2012:1813-1816.
(Edited by Wang Yuxia)
10.15918/j.jbit1004- 0579.201524.0217
TN 911.7 Document code: A Article ID: 1004- 0579(2015)02- 0246- 08
Received 2014- 06- 12
Supported by the National Natural Science Foundation of China (61100156); the National 12th Five-Year Plan Item of China(513160702); the Fundamental Research Funds for the Central Universities (JB150317, JB140311, K5051303014)
E-mail: zengp@xsyu.edu.cn
 Journal of Beijing Institute of Technology2015年2期
Journal of Beijing Institute of Technology2015年2期
- Journal of Beijing Institute of Technology的其它文章
- Numerical simulation of effects of operating conditions on the molecular weight of polypropylene using a response surface method
- Efficient and fair resource allocation in downlink OFDMA systems
- Effect of cutting speed on residual stress of special coating during remanufacturing
- Un-powered gliding aircraft’s ballistic missile optimal design
- Quantification of CP4-EPSPS in genetically modifiedNicotianatabacum leaves by LC-MS/MS with 18O-labeling
- Investigation on experimental method of low-impedance materials using modified Hopkinson pressure bar
