Trust assessment of business service workflow based on complex trust network*
Luo Yihang (骆怡航), Fan Yushun, Guo Xiaohui
(*Department of Automation, Tsinghua University, Beijing 100084, P.R.China)(**China Tobacco Guangxi Industrial Co., Ltd, Guangxi 530001, P.R.China)
Trust assessment of business service workflow based on complex trust network*
Luo Yihang (骆怡航)**, Fan Yushun*, Guo Xiaohui**
(*Department of Automation, Tsinghua University, Beijing 100084, P.R.China)(**China Tobacco Guangxi Industrial Co., Ltd, Guangxi 530001, P.R.China)
For business service workflow, QoS-based services selection can’t guarantee whether the composite service satisfies user’s requirement after delivery, because once any service interrupts or quality of service (QoS) maliciously reduces, the quality of workflow will be reduced. Trustworthy services can provide reliable QoS, so trustworthiness research could improve the efficiency of services selection. This paper investigates trust assessment in the perspective of workflow. Firstly, trust network of business service workflow (TN-BSW) is proposed to analyze trust attributes; then, the trust measurement system of TN-BSW is investigated to assess the trust value quantitatively; and then, a trust-aware service recommendation model (TaSRM) is proposed to enhance the efficiency of QoS-basedservices selection; finally, experiment shows the feasibility of TN-BSWand the performance of TaSRM.
business service workflow, trust attributes, trust assessment, quality of service (QoS), service selection
0 Introduction
The function of business service workflow is achieved by the composition of different abstract services, such as logistic service and payment service. Many concrete services can achieve the function of abstract service, such as EMS and UPS both of which can provide logistic service, but their qualities of service (QoS) are different.
How to select service is the key problem of service system. Some previous works[1-6]investigated services selection problems based on QoS. Ref.[1] proposed the QoS framework for services selection. Ref.[2] proposed the ranking of services by QoS assessment. Refs[3-5] focused on composite services by QoS composition calculation. Ref.[6] proposed context-aware QoS to deal with dynamic services selection. Based on QoS, service with high QoS value and service workflow with high aggregated QoS value can be selected.
However, these works ignored the problem: “Advertising QoS published before delivery might change after delivery”. The reason is: Business service has the characteristics of social, dynamic and subjective. In real case, once any service provider loses credibility, such as interrupting service and reducing QoS maliciously, the whole workflow will be affected. On one hand, the quality of workflow after delivery will deviate from advertising QoS; on the other hand, the whole workflow may be terminated with uncompleted response, so it can’t achieve user’s requirement. Obviously, QoS-based services selection can’t be aware of credit losses, while credit losses often happen in real business service scenario.
For this shortage of QoS-based services selection, some works[7-9]research credit rating to measure services’ credit from users or third-party monitoring. By comparing the credits, services with low credit can be filtered. However, service’s credit might be deliberately rated high by its own providers or rated low by competitors. Therefore, malicious behaviors detecting[10,11]is to make credit rating more believable. However, in general, these two methods only deal with one type abstract service while not service workflow. One service with credible QoS can’t represent that the whole workflow’s quality is credible.
In conclusion, credit rating and malicious behaviors detecting make QoS-based services selection more reliable, but it still can’t guarantee that the composite QoS satisfies user’s requirement after delivery.
Trust relationship is the key factor to solve this shortage. On one hand, trustworthy services can provide reliable QoS; on the other hand, in services interaction, a high credible service tends to cooperate with others having the same or higher credit. Thus, if service workflow can be provided by trustworthy services, meanwhile, these services have good cooperative relationship, the quality of workflow could be guaranteed more reliably.
By this motivation, two questions on the research of trust relationship should be solved.
(1) How to measure the trustworthiness of a service and the trust relationship of business service workflow?
(2) How to utilize this trust measurement in business services selection?
This paper devotes to solve these two questions and contains 5 sections. Section 1 proposes trust network of business service workflow (TN-BSW); Section 2 presents the measurement system of TN-BSW; Section 3 proposes a Trust-aware Service Recommendation Model (TaSRM) and its algorithms to solve services selection problem; Experiment in Section 4 is to verify TN-BSWandTaSRM; Section 5 presents the conclusions.
1 TN-BSW
For business service, business correlations are formed gradually in the long-term interactions, such as partner and price alliance.It can be depicted by graph structure with nodes and links, as shown in Fig.1: node represents service, link represents business correlation, such asC(1, 2)representsthecorrelationbetweenservice1and2;theycanalsoformaloopcorrelation.
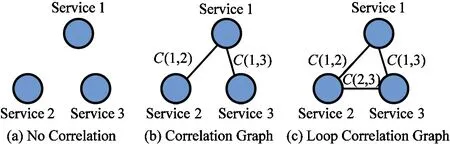
Fig.1 Business correlation graph
Service tends to cooperate with others having the same or higher credit, business correlations reflect trust relationships. We call it business correlation trust and classify it into Node-trust and Link-trust. For business service, reputation, business scope and transaction volume are main attributes and they affect trust relationships significantly. Further more, Node-trust can be measured by reputation level (RL), and Link-trust can be measured by business scope compatibility (BSC) and business compactness degree (BCD), which are corresponding to business scope and transaction volume.
(1) Node-trust: Real service systems provide various reputation mechanisms to assess reputation. For example, Amazon defines five stars[12]; Alibaba defines gold supplier and a series of authentications[13]. Thus, reputation mechanism can be utilized to assess Node-trust.
(2) Link-trust:On one hand, business scope reflects service function, such as payment service. BSC represents business scope compatibility between two services’ business scopes, for example, accessory manufacturer A only provides a special accessory to auto manufacturer B, another accessory manufacturer C can provide the same accessory and other accessories. To a certain extent, as the more compatiblescope, A can concentrate more on serving for B, and the intensity of trust between A and B is higher than C and B. On the other hand, BCD represents business compactness degree between two services, and it is reflected by transaction volume. The transaction might be product purchasing or service consumption. Stronger BCD reflects the deeper trust relationship.
By the combination of Node-trust and Link-trust, a trust network of business service workflow (TN-BSW) is established as Fig.2 to illustrate the trust relationship.

Fig.2 Trust network of business service workflow
As shown in Fig.2, circles marked with “S” and “E” respectively represent the start and end of workflow. This workflow is composed of 5 abstract services (AS).AS3andAS4formaparallelstructureandothersformasequentialstructure.EachAShasmanycandidateservices,e.g.,S1,1isthefirstserviceinAS1,S3,5isthefifthserviceinAS3.Cooperationbetweenservicesindifferentabstractservicesformsbusinesscorrelation.
Then,trustnetworkcanbeextractedwithNode-trustandLink-trust.Asanexample,oneworkflowinstancepathmarkedwithNode-trustandLink-trustisshowninFig.2(b).ByTN-BSW,trustrelationshipsofbusinessserviceworkflowcanbeshownintuitivelyandclearly.
2 Trustmeasurementsystem
TN-BSWconsidersservicetrust(Node-trust)andbusinesscorrelationtrust(Link-trust).ThissectionpresentsdetailedtrustmeasurementofTN-BSW.
2.1Reputationlevel
TakeSi,jrepresentsthejthserviceintheithabstractservice,herein,i=1,2,…,I.andj=1,2,…,Ji;IrepresentsthenumberofabstractserviceandJirepresentsthenumberofservicesintheithabstractservice.ReputationlevelofSi,jisdepictedasR(Si,j).
2.2Businessscopecompatibility
(1)
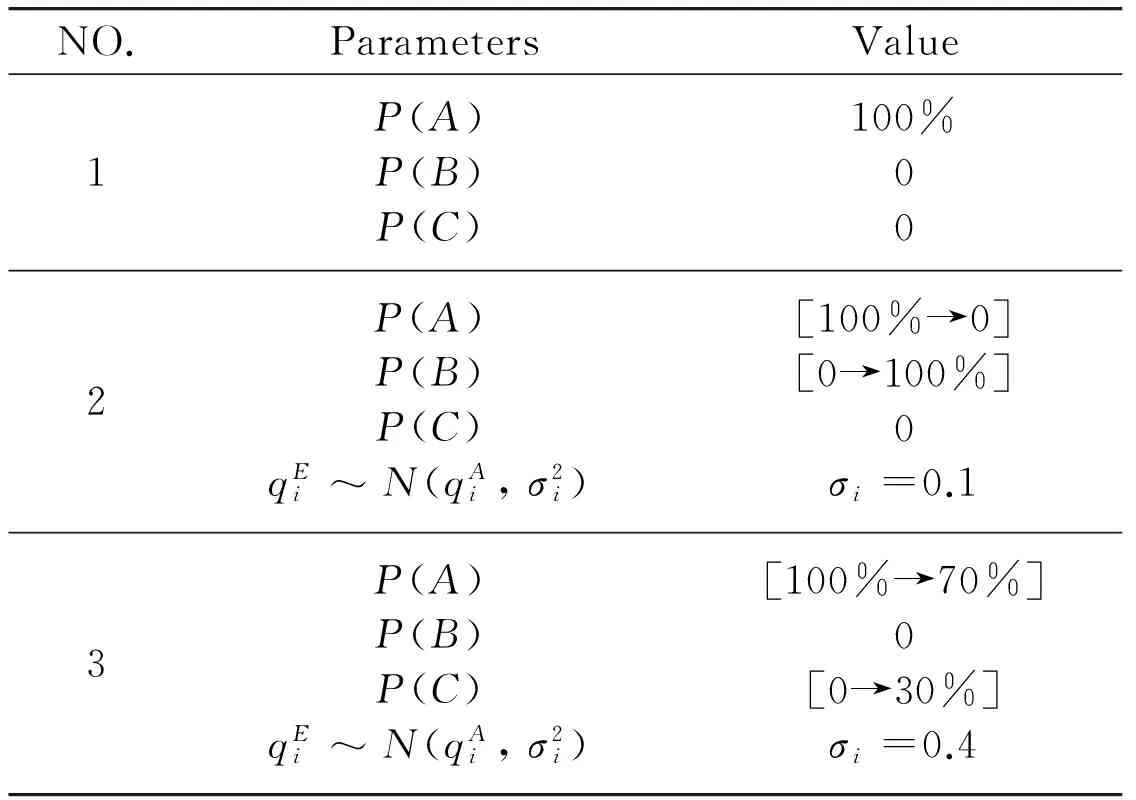
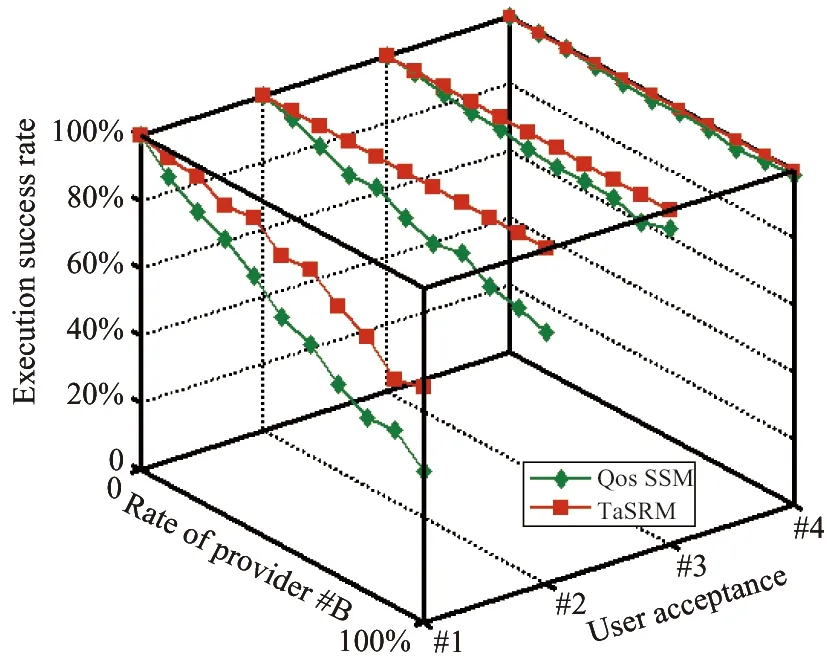
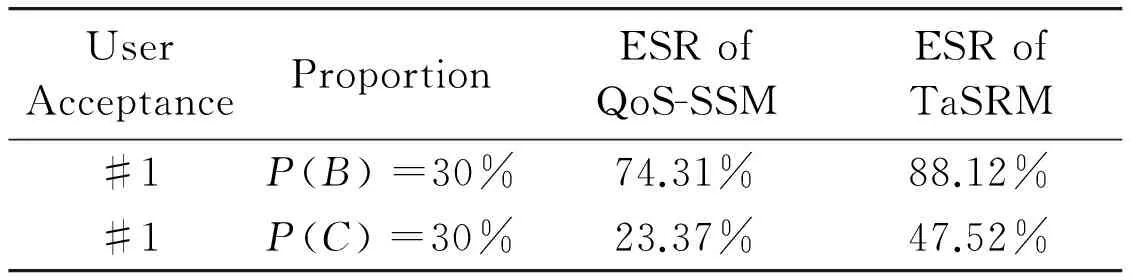
whereS(Si,j)andS(Sk,l)representthebusinessscopeofserviceSi,jandSk,l.Theycanbeobtainedbyservicetags,whicharemoreconcretethanservicecategories.Forexample,inthewebsite(www.programmableweb.com),theAPI“GoogleMaps”iscategorizedasmappingandannotatedwiththetagsofmapping,places,vieweranddisplay.Thesetagsreflectitsbusinessscope.ThebusinessscopecompatibilitybetweenSi,jandSk,liscalculatedbysimilaritymeasurementofbusinessscope[14].S(Si,j)∩S(Sk,l)getsthenumberofmatchedscopes;S(Si,j)∪S(Sk,l)getsthetotalnumberoftheirscopes.Thus,thevaluedomainofBSC(Si,j,Sk,l)is[0, 1].BSC(Si,j,Sk,l)=0representstheirbusinessscopesareirrelative;BSC(Si,j,Sk,l)=1representstheirbusinessscopesarematchedabsolutely; 0 2.3Businesscompactnessdegree (2) whereV(Si,j)andV(Sk,l)representthetotaltransactionvolumeofserviceSi,jandSk,l.Theycanbeobtainedbytransactionhistoryandformattedastransactiontimes.ThebusinesscompactnessdegreebetweenSi,jandSk,liscalculatedbysimilaritymeasurementoftransactionvolume[14].V(Si,j)∩V(Sk,l)getsthetransactiontimesbetweenthem;V(Si,j)∪V(Sk,l)getsthemaxtransactiontimes.Thus,thevaluedomainofBCD(Si,j,Sk,l)is[0, 1].BCD(Si,j,Sk,l)=0representsnotransactionbetweenthem;BCD(Si,j,Sk,l)=1representstheirtransactionsareabsolutelyfromeachother; 0 Then,foraserviceworkflowinstancepathp,asinFig.2(b),theutilityvalueofRL,BCDandBSCcanberespectivelycalculatedasEq.(3).WRrepresentsthereputationweightvectorofservice,WBSCrepresentstheBSCweightvectorofbusinesscorrelation,WBCDrepresentstheBCDweightvectorofbusinesscorrelation,UR(p)representstheweightedaveragereputationofp,UBSC(p)representstheaggregatedBSCvalueofp,andUBCD(p)representstheaggregatedBCDvalueofp. (3) Theconcretemeasurementcanbeexpressedas: (4) Finally,thetrustutilityvalueofpathpintegratedwithNode-trustandLink-trustisexpressedas U(p)=δ1UR(p)+δ2UBSC(p)+δ3UBCD(p) (5) 3.1 TaSRM Based on the trust measurement system, Trust-aware service recommendation model (TaSRM) is established as Fig.3 to measure the trust of business service workflow instance paths (BSW-IP) and get the trustworthy BSW-IP. Fig.3 Trust-aware service recommendation model TaSRM sets two judgments and three layers. Judgment I:“Is there QoS requirement?” It represents that if a user has QoS requirement? This judgment can distinguish different users.User without QoS requirement is like a new user who isn’t familiar with QoS index or does not know their concrete requirement. Judgment II:“Is there local QoS?” It represents that if QoS requirement contains local QoS requirement? Local QoS requirement can be applied to some specific scenarios, for example, user specifies the accommodation fee or transportation cost in travel service. Layer I: User requirement acquirement User requirement contains requirements of function and QoS. Through service functionscomposition, abstract business service workflow can be obtained. Layer II: QoS-based services selection This layer gets the feasible BSW-IP. If the user has local QoS requirement, firstly local selection is triggered to select services by local QoS; then, use QoS-based services selection to optimize composite QoS by global QoS requirement to get the feasible BSW-IP. Layer III: Trust-based service recommendation This layer gets the trustworthy BSW-IP by trust measurement system. When there is no QoS requirement, directly adopt this layer to get service recommendation. 3.2 Algorithms of TaSRM 3.2.1 QoS-based services selection algorithm Table 1 QoS-based services selection algorithm 3.2.2 Trust-based service recommendation algorithm In this stage, inputFWP_ListandTN-BSW;firstly,setweightvectors(WR,WBSC,WBCD),andsetparametersδ1,δ2andδ3;thencomputetrustutilityvalueofeachFWPby Eqs (4) and (5) to getU(pi);finally,sortU(pi)togetthelistoftrustworthyBSW-IP.ThisstageisshownasTable2. Table 2 Trust-based services recommendation algorithm In conclusion, TN-BSW and its measurement system are applied into TaSRM. TaSRM is to get the trustworthy BSW-IP on the premise of meeting QoS requirement. Experiments should investigate two issues. (1) Whether TaSRM can detect malicious behaviors and provide the trustworthy BSW-IP? (2) How about the execution efficiency of TaSRM? 4.1 Paremeters setting 4.1.1 Common parameter definitions Common parameter definitions are shown as Table 3. Table 3 Common parameter definitions 4.1.2 Evaluation indicators definition There are two types of QoS: 1) Cost QoS, and users expect it lower, such as price and execution time; 2) Benefit QoS, users expect it higher, such as reputation and usability. Besides, three indexes are defined: QoS deviation degree represents the degree thatQoSEdeviatesfromQoSR.Itisformulizedas (6) User acceptance degree represents the degree that deviates from. It is formulized as (7) Recommendation Success Function represents if the selection result satisfies user’s requirement. For cost and benefit QoS,ρD≤ρAindicatesthatusersacceptthedeviation,sotherecommendationissuccessful;andρD>ρAindicatesthatthedeviationexceedsuser’sacceptance,sotherecommendationisfailed.Itisformulizedas (8) Inaddition,behaviorsofserviceprovidersreflectthetrustworthydegreeoftheirservices.Classifyprovidersintothreetypes(#A, #B, #C)andP(A),P(B)andP(C)respectivelyrepresenttheproportionoftheirnumbers. Provider A represents providers with high credible, who advertise QoS truth fully. They would makeQoSEconsistentwithQoSAevenifataprofitloss. Provider B represents providers with medium credit, who try to guarantee user’s benefit, althoughQoSEvariesfromQoSAasuncertaincommercialfactors. Provider C represents fraudulent providers, who maliciously overstate advertising QoS for more benefit, resulting thatQoSEdeviatesmuchfromQoSA. 4.2 Simulation experiments The algorithms are programmed by Matlab 2009a and then run the experiments on DELL Optiplex 380 (Intel Core2 E7500 2.93GHz CPU, 1.96GB RAM). 4.2.1 Common parameters assignment Common parameters assignment is shown as Table 4. Table 4 Common parameter assignment 4.2.2 Experiment parameters assignment Three group experiments are designed to show the performance of TaSRM as to different service providers. Table 5 sets the parameters of three group experiments. Table 5 Experiment parameters assignment 4.2.3Modelperformanceexperiment ComparativeexperimentisdesignedtoverifyTaSRM.QoS-SSM(QoS-basedservicesselectionmodel)referstoanotherofourpapers[16],whichsupportsQoScorrelationinQoS-basedservicesselection,whiledoesnotconsiderthetrustimpact.ThefollowingshowsthethreegroupexperimentsrespectivelyforProviderA,BandC. (1)ForProviderA a)Observation Fig.4 ESR distribution by interacting with Provider A b) Description Table 6 Coordinates of Fig.4 Table 6 shows the coordinates of Fig.4. For one type user acceptance, one experiment repeats 30 execution times with random QoS to calculate execution success rate (ESR) as Eq.(9).S(p)referstoEq.(8),whichrepresentstheexecutiontimes. (9) c)Analysis AllservicesareprovidedbyProviderA.Whenuseracceptancerangesfrom#4to#1,userdemandbecomesstricterandESRbecomeslower.At#4,bothmodelscanrecommendservicessatisfyingQoSRateachtime,i.e.ESR=100%,butwithacceptancedegreedecreasing,bothmodelshavefailedrecommendation,i.e.ESR<100%. Thereasonis:allservicesarecredibleandQoSEisequaltoQoSA.BothmodelscangettheoptimalBSW-IPbyQoSA.Butforstrongeruserdemand,QoSEofoptimalBSW-IPmightdissatisfyQoSR. (2)ForProviderB a)Observation Fig.5 ESR distribution by interacting with Provider B b) Description Table 7 Coordinates of Fig.5 Table 7 shows the coordinates of Fig.5. Coordinate Y represents the proportion of Provider B; the other is Provider A.For one type user acceptance and a certain rate of Provider B, one experiment repeats 30 execution times by random QoS to calculate ESR. c) Analysis On one hand, comparing with Fig.4, ESR of both models is decreasing; on the other hand, for one specific user acceptance type, with the increasing of Provider B rate,TaSRM achieves a higher ESR than QoS-SSM. (3) For Provider C a) Observation Fig.6 ESR distribution by interacting with Provider C b) Description Table 8 shows the coordinates of Fig.6. Coordinate Y represents the proportion of Provider C; the other is Provider A.For one type user acceptance and a certain rate of Provider C, one experiment repeats 30 execution times by random QoS to calculate ESR. Table 8 Coordinates of Fig.6 c) Analysis Fig.6 and Fig.5 have different coordinate Y scales, one is[0%,30%] and the other is[0%,100%]. It indicates that ESR falls severely when Provider C increases and an example is shown in Table 9. Table 9 ESR Comparison (Provider B and Provider C) Obviously, ifP(C) continues increasing, ESR will fall more severely, and even no successful recommendation. In conclusion, Provider B and C can’t guaranteeQoSE=QoSAafterdelivery.QoS-SSMjustdependsonQoSA,soitisunawareofQoSchange,andESRwilldecreasemorecertainly.ForTaSRM,beforedelivery,TaSRMevaluatesandsortsthetrustvalueoffeasibleBSW-IP,thenselectsthemosttrustworthyone.AccordingtoQoSA,BSW-IPbyTaSRMmightnothavetheoptimalcompositeQoS,butit’sthemosttrustworthyonetomakeQoSEconsistentwithQoSA.Thus,TaSRMcanidentifymaliciousservicesandresisttheirselection. Inconclusion,fromFig.5andFig.6,ESRofTaSRMisobviouslyhigherthanQoS-SSM,especiallywhenthenumberofmaliciousservicesisincreasing.D.Executionefficiencyexperiment Anappropriateexecutiontimecanmakerecommendationeffective.Herein,changethenumberofabstractserviceandservicetosimulatedifferentserviceworkflows. 5typeworkflowsareconstructedinTable10. a)Observation b)Description CoordinateXrepresentsdifferentworkflowtypes,andcoordinateYrepresentsexecutiontime.ExecutiontimeofQoS-SSMcontainsonestep[16]andTaSRMcontainstwosteps:QoS-basedservicesselection(Step1)andTrust-basedservicesrecommendation(Step2). Table 10 Scale of services workflows Fig.7 Statistics of execution time c) Analysis The statistics of Fig.7 is presented in Table 11. Table 11 Statistics of execution time With workflow’s scale increasing, the execution times of two models are increased. The execution time of TaSRM’s Step 1 is close to QoS-SSM; TaSRM’s Step 2 adds an execution time with the range of [2.2s, 3.1s]. Through analysis, QoS-SSM is to optimize the nonlinear combination of multi dimensional QoS[16], thus QoS-SSM depends on the numbers of abstract service and service; while trust measurement in TaSRM (Step 2) depends on the limited number of feasible BSW-IP from Step 1. Thus, Step 2 in TaSRM is lesscomplex than Step 1 and consumes less time. Therefore, although TaSRM adds a certain time comparing with QoS-SSM, it can get the trustworthy BSW-IP within the effective execution time. Further, TaSRM can recommend more reliable BSW-IP to users, as considering both QoS and trust for selection. E. Empirical study and insight For the real service system, an online marine logistic service platform (OMLSP)[17]is selected for investigation. It is a typical business services system with 5 main abstract services, including forwarder, ship owner, ship agency, insurance agency and online payment service. OMLSP just provides QoS query with single abstract service, e.g. querying ship agency by freight charge or reputation will return a list of ranked ship agencies. But it may be hard for users to select other services and composite a whole BSW-IP. Therefore, if assess trust value and apply TaSRM, the trustworthy BSW-IP can be obtained. For example, BSW-IP recommendation might be {forwarder 1, ship owner 4, ship agency 5, insurance agent 2, payment 2}, while not a single {ship agency 3}. In this perspective, trust assessment mechanism and TaSRM is feasible and effective to enhance the recommendation accuracy and user experience. Services selection is a significant problem in business service management. This paper devotes to a trustworthy service recommendation to enhance the accuracy and reliability of QoS-based services selection. First, TN-BSW is established to combine service reputation (Node-trust) and business correlation trust (Link-trust); then the corresponding trust measurement system is proposed to calculate the trust utility value; based on it, the trust-aware service recommendation model can filter unreliable service and recommend trustworthy BSW-IP; finally, an experiment verifies the feasibility of TN-BSW and the performance of TaSRM. Reference [1] Herssens C, Faulkner S, Fouss F, et al. A framework for QoS driven selection of services. In: Proceedings of the 5th International Conference on Service Computing (SCC 08), Honolulu, USA, 2008. 537-538 [2] Yau S S, Yin Y. QoS-based service ranking and selection for service-based systems.In: Proceedings of the 8th International Conference on Service Computing (SCC 11), Washington DC, USA, 2011. 56-63 [3] Jaeger M C, Muhl G, Golze S. QoS-aware composition of web services: a look at selection algorithms.In: Proceedings of the 12th International Conference on Web Service (ICWS 05), Orlando, Florida, USA, 2005. 807-810 [4] Haddad J E, Manouvrier M, Ramirez G, et al. QoS-driven selection of web services for transactional composition.In: Proceedings of the 6th International Conference on Web Service (ICWS 08), Beijing, China, 2008. 653-660 [5] Zheng H Y, Yang J, Zhao W L. QoS analysis and services selection for composite services. In: Proceedings of the 7th International Conference on Service Computing (SCC 10), Miami, USA, 2010. 122-129 [6] Lin D H, Shi C Q, Ishida T. Dynamic services selectionbased on context-aware QoS. In: Proceedings of the 9th International Conference on Service Computing (SCC 12), Honolulu, USA, 2012. 641-648 [7] Xiong L, Liu L. A reputation-based trust model for peer-to-peer e-commerce communities. In: Proceedings of the 2003 International Conference on E-Commerce, Newport Beach, USA, 2003. 275-284 [8] Daisaku S, Yoshiaki Y, Kuniaki U. Estimating credibility of reputaion on the web using contributor’s stance. SIG-KBS, 2006, 73:85-90 [9] Zhu F Y, Yang G M, Tan Z H. A commodity’s reputation-based trust model of P2P e-commerce systems. In: Proceedings of the 4th International Conference on Genetic and Evolutionary Computing,Shenzhen, China, 2010. 430-433 [10] Xu P, Gao J, Guo H. Rating reputaion: anecessary consideration in reputation mechanism. In: Proceedings of the 2005 International Conference on Machine Learning and Cybernetics, Guangzhou, China, 2005. 182-187 [11] Maheswari S, Karpagam G R. Empirical evaluation of reputation based trust in semantic web.InternationalJournalofEngineeringScienceandTechnology, 2010, 2(10):5672-5678 [12] Amazon Web Site. http://www.amazon.com. [13] Alibaba Web Site. http://www.alibaba.com. [14] Zhang Y, Liu Y D, Ji Z. Vector similarity measurement method.TechnicalAcoustics, 2009, 28(4): 532-538 [15] Qin L. AHP-based teaching evaluation index system of weights. In: Proceedings of the 2012 Conference on Informatics and Management Science, Kunming, China, 2012. 449-457 [16] Luo Y H, Fan Y S, Wang H Y. Business correlation-aware modelling and services selection in business service ecosystem.InternationalJournalofComputerIntegratedManufacturing, 2013, 26(8): 772-785 [17] E-business for freight. http://en.shippingchina.com Luo Yihang, born in 1986. He is a Ph.D candidate of Automation Department at Tsinghua University. His research focuses on service quality control. 10.3772/j.issn.1006-6748.2015.01.004 *Supported by the Research Fund for the Doctoral Program of Higher Education of China (No. 20120002110034) and Initiative Scientific Research Program of Tsinghua University (No. 20111080998). *To whom correspondence should be addressed. E-mail: yihangluo@hotmail.comReceived on Oct. 8, 2013

3 TaSRMandalgorithms




4 Experiments and analysis











5 Conclusions
 High Technology Letters2015年1期
High Technology Letters2015年1期
