Iris Liveness Detection Using Fragmental Energy of Haar Transformed Iris Images Using Ensemble of Machine Learning Classifiers
Smita Khade,Shilpa Gite,2,*,Sudeep D.Thepade,Biswajeet Pradhanand Abdullah Alamri
1Symbiosis International(Deemed University),Symbiosis Institute of Technology,Pune,412115,India
2Symbiosis Centre for Applied Artificial Intelligence,Symbiosis International(Deemed University),Pune,412115,India
3Computer Engineering,Pimpri Chinchwad College of Engineering,Pune,411044,India
4Centre for Advanced Modelling and Geospatial Information Systems(CAMGIS),School for Civil and Environmental Engineering,Faculty of Engineering and Information Technology,University of Technology Sydney,Sydney,New South Wales,2007,Australia
5Earth Observation Center,Institute of Climate Change,University Kebangsaan Malaysia,UKM,Bangi,Selangor,43600,Malaysia
6Department of Geology&Geophysics,College of Science,King Saud University,P.O.Box 2455,Riyadh,11451,Saudi Arabia
ABSTRACT Contactless verification is possible with iris biometric identification,which helps prevent infections like COVID-19 from spreading.Biometric systems have grown unsteady and dangerous as a result of spoofing assaults employing contact lenses,replayed the video,and print attacks.The work demonstrates an iris liveness detection approach by utilizing fragmental coefficients of Haar transformed Iris images as signatures to prevent spoofing attacks for the very first time in the identification of iris liveness. Seven assorted feature creation ways are studied in the presented solutions, and these created features are explored for the training of eight distinct machine learning classifiers and ensembles.The predicted iris liveness identification variants are evaluated using recall,F-measure,precision,accuracy,APCER,BPCER,and ACER.Three standard datasets were used in the investigation.The main contribution of our study is achieving a good accuracy of 99.18% with a smaller feature vector. The fragmental coefficients of Haar transformed iris image of size 8 * 8 utilizing random forest algorithm showed superior iris liveness detection with reduced featured vector size (64 features). Random forest gave 99.18% accuracy.Additionally,conduct an extensive experiment on cross datasets for detailed analysis.The results of our experiments show that the iris biometric template is decreased in size to make the proposed framework suitable for algorithmic verification in real-time environments and settings.
KEYWORDS Iris images; liveness identification; Haar transform; machine learning; biometric; feature formation; ensemble model
1 Introduction
Automatic human access to a system has become relatively simple in the digital era.Confirmation of the user’s identification is critical for automated system access. Biometric authentication systems employ biometric features to confirm the identification of a user [1]. Compared to conventional password-based traditional verification systems, the biometric system has a distinct advantage. It minimizes the need to memorize a passcode,pin,or keep a card in hand[2].Biometric authentication can be thought of as an additional layer of authentication for security-critical cyber applications and existing traditional authentication procedures. Today, there are indeed different businesses for biometric systems.The majority of the sectors seem to be rising quickly.According to www.statista.com(accessed on 24thJune 2022),the business for contactless biometric technologies is forecasted to increase by roughly 30.15 billion US dollars by 2027,while the overall biometric sciences industry is forecasted to touch 19.08 billion US dollars in 2021[3].Iris is widely employed in the verification and validation of people.In most applications,it uses,because of its complex textures[4]and distinctive features,such as the UIDAI project for citizen identification in India,the Amsterdam airport,and the Canada-US border onon-US[5].
In comparison to fingerprint and face authentication, iris authentication delivers an additional steadfast contactless user verification.The contactless method aids in the prevention of diseases like COVID-19 [6]. Despite the iris having a distinct textural structure, the imposter might falsify it [7].Table 1 shows the iris presentation attacks used that are found in the literature[8].

Table 1: Iris presentation attacks[8]
Individuals frequently assault the biometric system to get admittance to another person’s credentials or to conceal their accurate individuality.The iris identification system can be readily fooled by means of alternative contact lenses (which can be transparent, textured, colored) [10], replaying the video,or using a print attack[9].As a result,understanding the risk and susceptibility is critical for safeguarding the biometric system[14].The complicated risk of biometric spoofing is minimized by assessing the liveness of biometric features prior to authentication [15]. The main objective of this study is to identify iris liveness detection with reduced feature vectors.
The main objective of this study is to identify iris liveness detection with reduced feature vectors.Following are the novelty and the main contributions of this paper.
• Initiatory utilization of ‘fragmental coefficients of Haar transformed iris image data’as signatures in iris liveness detection;
• Determining the smallest size of fragmental coefficients that might be used for feature generation without impairing iris liveness detection performance;
• To identify which classifier is optimal in iris liveness detection, the performance of machine learning(ML)classifiers and their ensemble combinations are analyzed;
• Testing the feasibility of the developed iris liveness detection method against a variety of existing benchmark datasets.
The paper’s organization is presented herewith. Section 2 elaborates on an outline of existing methodologies. Section 3 portrays the proposed approach to iris liveness detection. The experimentation setup is put forth in Section 4. While Section 5 elaborates on the noted outcomes and the conclusions taken from the findings. Section 6 is where the discussion takes place. Finally, final thoughts,limitations,and future research suggestions are presented in Section 7.
2 Prevailing Iris Liveness Detection Techniques
Various strategies have been adopted to determine whether the acquired biometric traits are alive prior to the authentication.Several of the most well-known techniques are addressed in this section.
For liveness identification,Agarwal et al.[16]explored fingerprints with iris.To create a fingerprint vector function, the essential Haralick statistical characteristics use GLCM and NGTDM. The iris texture feature is utilized to improve the device’s performance. To evaluate if this model is more efficient than the current one, Agarwal used a standard dataset. GLCM has an extensive feature vector size in the current system.Iris spoofing attacks are detected using rotation-invariant features of Polar harmonic transformations and Zernike moments[5].Spoofing assaults on numerous sensors significantly impact the system’s overall competence. The system detects attacks like iris print and contact lenses.
Thavalengal et al. created a that uses smartphones to take RGB along with NIR images of the iris and eye [17]. Identification is made using pupil localization techniques and distance measures.4096-dimensional features are examined for feature vector generation,which is a considerable number.Although the author claims a high rate of liveness recognition, he does not work with standard datasets. Authors Fathy et al. have not examined the segmentation or normalization processes commonly utilized in Iris liveness discovery systems [13]. The original image is broken down into wavelets using Wavelet Packets(WPs).Although the author claims it is 100 percent accurate,it is not working with all genres of assaults and only covers a few spoof attacks.
Iris liveness detection will be made utilizing regional features by author Hu et al. [18]. The interaction of the properties of nearby regions is used to create regional traits. The author utilized one hundred forty-four relational measurements based on regional attributes during the experiment.
Using pupil dynamics,the author Czajka[19]created the liveness identification system.The pupil reaction is tested in this system using rapid changes in the intensity of light. In the case of the eye reacting to the variations in light intensity, it is alive; otherwise, presentation attack image. In [19],non-linear and linear SVM is employed to categorize natural reactions and impulsive oscillations.The system’s shortcoming is that it measures a variety of functions that take time.There are inaccuracies in the observation because the data utilized in this research does not include any details from elderly adults.
Author Fang et al. [20] apply many data augmentation methods to generate variability. The strategy-level and the score-level combination of fusion methods are used for Iris PAD.Bassi et al.[21]detected PAD using NIR, visible domain, cross-datasets and cross-spectrum datasets. Authors concluded that Cross-PA and cross-datasets are still challenging, as EER values above 20% in most of cases.
A technique to detect Accurate Ocular Regions was created by Naqvi et al. [22]. This solution uses deep neural network variants. The system’s evaluation considers publicly available databases.Kimura et al. [23] developed a CNN-based liveness detection System that improves model accuracy by modifying hyperparameters. “Attack Presentation Classification Error Rate [APCER]”and“Bonafede Presentation Classification Error Rate[BPCER]”metrics are taken to assess the system’s performance.The hyperparameters are all studied in this work.This method is solely effective against prints and contact lens attacks.Author[24]studied multiple transfer learning models to detect the iris liveness and concluded that EfficeintnetB7 gives highest classification accuracy.
Only a few studies were found to be robust against all sorts of spoofing assaults[3,25].Most of the studies used a higher size feature vector.Based on these findings,it can be believed that there is a necessity for a classifier or ensembles for the detection of every sort of spoofing assault.
3 Proposed Iris Liveness Detection Utilizing Fragmental Energy of Haar Transformed Iris Images
The iris recognition system is prone to a range of security threats. Because of these flaws, the system is less trustworthy for robust authentication applications. The study employs fragmental energy of Haar modified iris images to attempt iris liveness detection.These fragmental energies were employed as features to detect whether the iris was real or fake.Because of these characteristics,the suggested methodology does not require any pre-processing,such as segmentation,normalization,or localization,which are commonly employed by methods presented in the literature.These fragmental energies were employed as features to detect whether the iris was real or fake. Because of these characteristics,the suggested methodology does not require any pre-processing,such as segmentation,normalization,or localization,which are commonly employed by methods presented in the literature.These fragmental energies make the suggested technique faster and more accessible [26]. Resizing the iris image to 256*256 is the sole pre-processing performed in the proposed framework.The iris liveness detection process depicted in Fig.1 is a block diagram.There are three phases in the proposed system.Resizing[pre-processing]of iris images,feature formation,and classification with iris liveness identification.
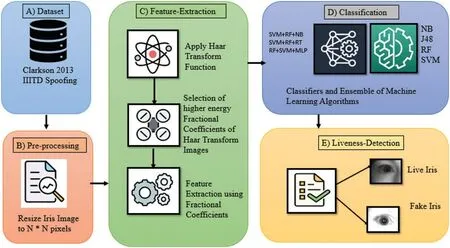
Figure 1:Block diagram of the projected iris liveness detection employing fragmental energy of Haar transformed iris images
3.1 Pre-Processing
The importance of iris pre-processing in iris liveness detection cannot be overstated.Two iris preprocessing techniques are used in the suggested algorithm.Because images are obtained using three standard datasets,each dataset stores images of different sizes.We normalized the original 256*256 images in pre-processing to ensure they remained intact throughout the experiment.At the same time,photographing various datasets with various sensors,some(LG,Content,Vista)acquired images in RGB format,while others[LG,Dalsa]acquired grayscale images.The images were then converted to grayscale to keep their originality.
3.2 Feature Formation with the Fragmental Energy of Transformed Iris
A scaled iris image is subjected to the Haar transform. The Haar transform allows content with high energy to congregate in the transform domain’s lower frequency section [27]. The Haar coefficients are described as below:
In case s=0,the function of Haar is presented as Eq.(1).

In case s >0,the function of Haar is presented by Eq.(2).

The nonzero part of the function’s amplitude and width are determined by p,whereas the nonzero part of the function’s placement is determined by q.
In the Haar transform iris image, the left highest corner has the higher energy and crucial information, as shown in Fig.2. This results in considerable energy compression in a limited count of high energy coefficients. As a result,these are the preferred feature vector elements. To construct feature vectors for proposed iris liveness detection,256*256,128*128,64*64,32*32,16*16,8*8,and 4*4.Pixels are used to capture the high-energy portion of Haar transformed iris image coefficients.

Figure 2:Proposed fragmental energy-based feature creation approach for liveness identification from cosine transformed iris images
These feature vectors support the reduction of the size of feature vectors.As a result,iris-liveness detection is speedier. The compacted high energy improves iris liveness detection accuracy in these low-frequency coefficients.These high-energy features are then employed for training the ML models working to detect iris liveness.
3.3 Iris Liveness Detection Using Meachine Learning Classifiers
The suggested method employs a combination of machine learning(ML)classifiers and ensembles.Naive Bayes(NB),Support Vector Machine(SVM),Random Forest(RF),and J48 are the ML classifiers[15]used here,along with SVM+NB+RF SVM+RT+RF,SVM+MLP+RF ensembles of classifiers.
Ensemble method—Using multiple models concurrently on a single set for categorization is always preferable to just one model.Ensemble learning is the name for this technique[23].Different classifiers are used to train a model,and the end output is an ensemble of the classifiers.The suggested method employs majority voting logic for an ensemble of ML classifiers.
These classifiers are trained using a tenfold cross-validation approach.The most effective method to train ML classifiers is tenfold cross-validation.Tenfold cross-validation allows all data in the dataset to be considered as either test or training data,giving a more unbiased classifier.The ensembles of ML classifiers are created using the majority voting mechanism.
Any deep learning architecture to perform well needs a considerable amount of data. Due to this, the time complexity increase. This disadvantage was overcome with the help of ML classifiers with handcrafted feature extraction. In the case of ensembles of classifiers, multiple classifiers help to classify correctly with majority vote logic. So, with the help of combined ML classifiers, the performance is superior compared to deep learning architectures/CNN.
4 Experimentation Setup
The investigative results of the proposed method are discussed in this section. The experiments were performed using an Intel (R) Core (TM) i3-6006U CPU @ 2.0 GHz, 12 GB RAM, and 6a 464-bit operating system with MATLAB R2015a as a programming platform.Clarkson LiveDet2013(Clarkson 2013),LiveDet2015(Clarkson 2015),and IITD Combined Spoofing datasets(IIITD CSD)were used to explore the suggested approach to iris liveness detection.
4.1 Description of Datasets
Three publicly available benchmark datasets are taken in this investigation.The dataset’s detailed description is as follows:
4.1.1 Clarkson LivDet2013
Around 1356 iris images are included in the Clarkson 2013 dataset [28]. There are two sets of data in this dataset:testing and training.The Dalsa sensor is utilized to acquire the iris.The images from training data(as given by the data creator)are used in this study for training purpose,and testing images(as given by the data creator)are used for testing purposes purpose.The dataset,sensors utilized in image acquisition, and the Count of images taken for training and testing a model during this exploration,with some examples,are all listed in Table 2.
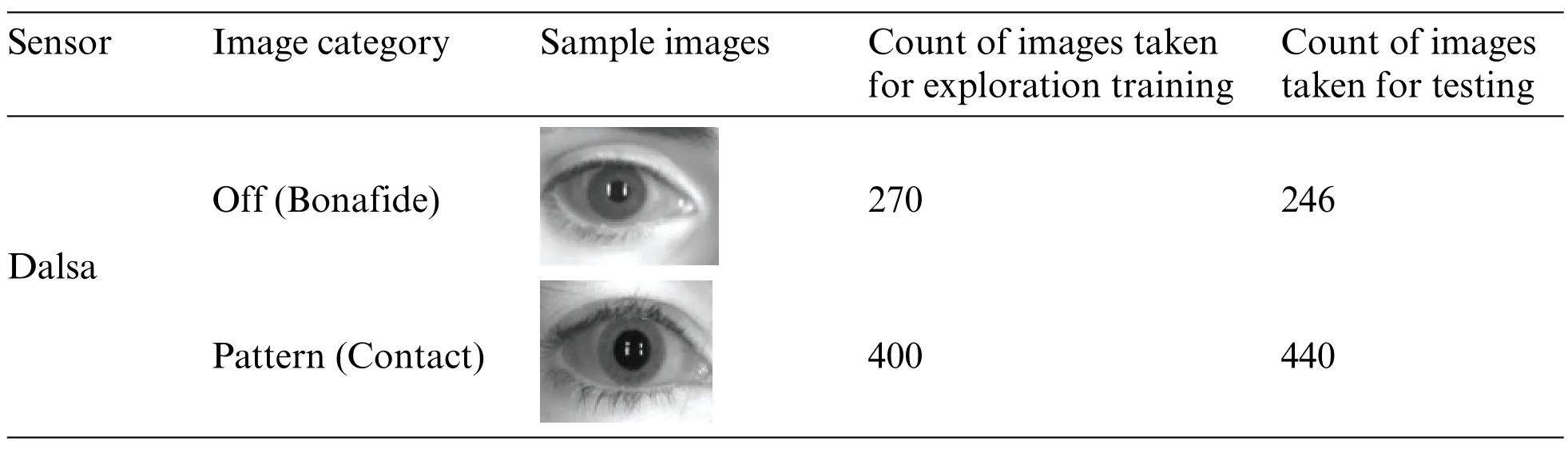
Table 2: Sample of images used for exploration from Clarkson 2013 dataset
4.1.2 Clarkson LivDet2015
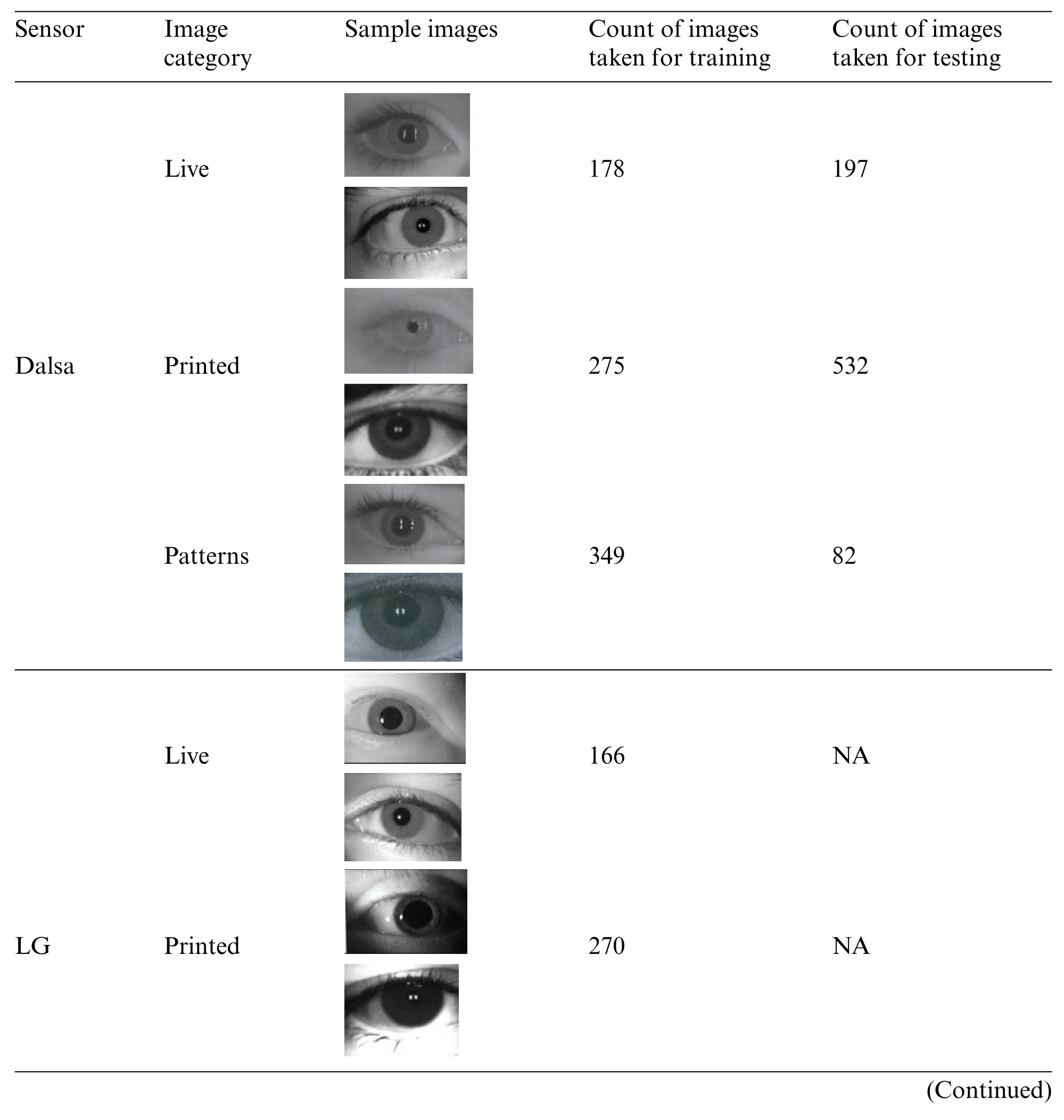
Table 3: Sample of images used for an experiment from Clarkson LiveDet2015 dataset

Table 3 (continued)Sensor Image category Sample images Count of images taken for training Count of images taken for testing Patterns images/BZ_324_920_694_1133_865.png303 NAimages/BZ_324_920_885_1142_1048.png
4.1.3 IIITD Combined Spoofing Database[IIITD CSD]
Two iris detectors,a Cogent sensor,and a Vista iris sensor,were utilized to create the images used in this collection[30,31].
Normal,Print-Capture attack,and Print-Scan attack are the three types of images available in the dataset[32].A 60:40 ratio is used for training testing split.The sensors utilized in image acquisition and the Count of images taken during this exploration with some sample images are all listed in Table 4.
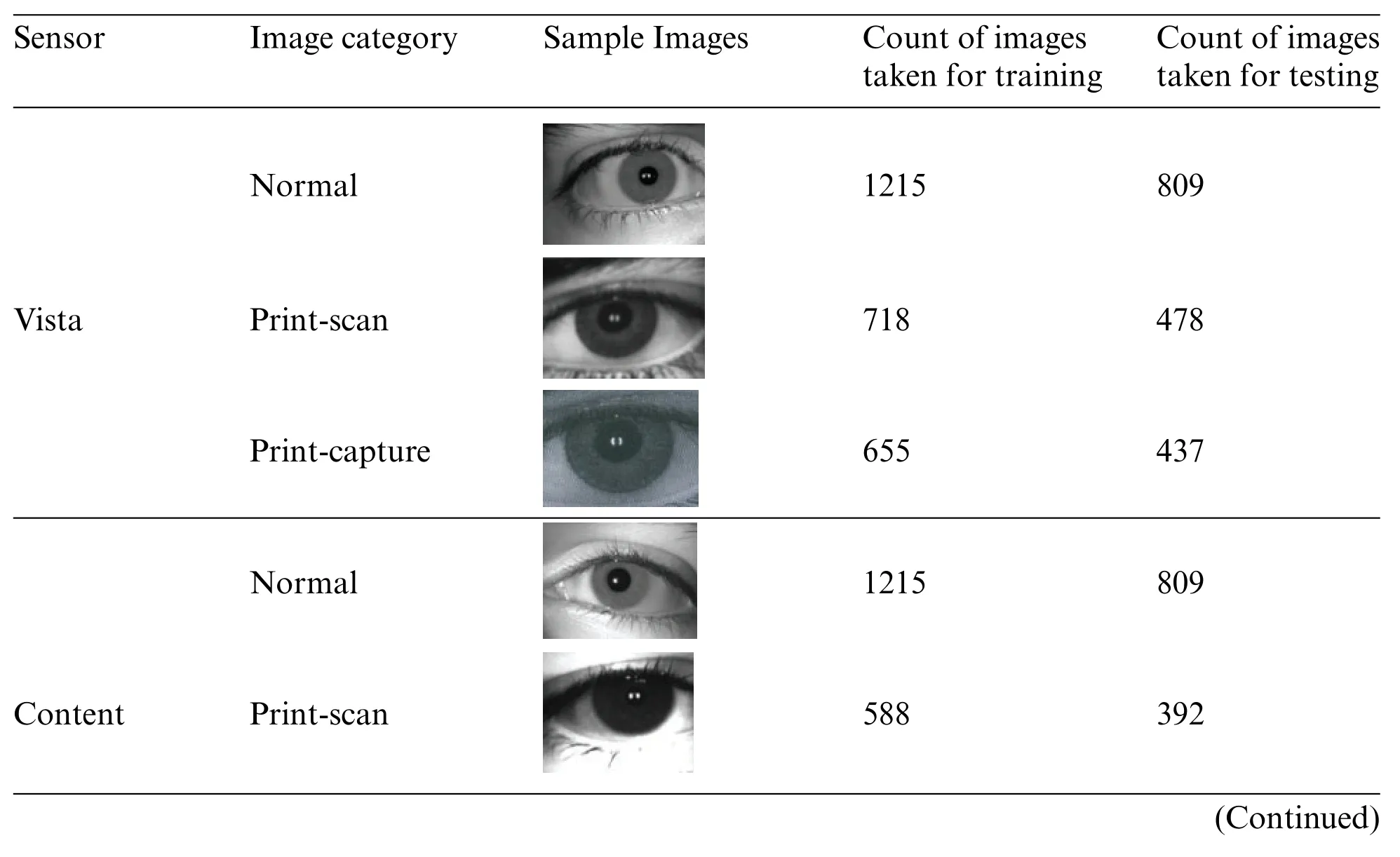
Table 4: Sample of images used for an experiment from IIITD combined spoofing dataset

Table 4 (continued)Sensor Image category Sample Images Count of images taken for training Count of images taken for testing Print-capture images/BZ_325_1057_694_1279_857.png668 445
4.2 Performance Measures
F-measure, accuracy, recall, precision, ACER (Average Classification Error Rate), APCER(Attack Presentation Classification Error Rate), and BPCER (Bonafide Presentation Classification Error Rate) are employed as performance metrics utilized here. Let the true positive, true negative,false positive,and false negative of the iris liveness detection be TP,TN,FP,and FN,respectively.The TP designates projected authentic data instances,which are truly what they are.The TN returns data examples that have been identified as spoofed and are also spoofed examples[2].FP denotes that the examples were detected as bonafide but were spoofed.The data examples were detected as presentation attacks imaged,but bonafide iris examples are shown in FN.The formulas for the performance metric utilized are given by Eqs.(3)to(9).

5 Experimentation Setup
The benchmark datasets for all feature size variants are taken to test the proposed iris liveness detection method.Performance measurements such as accuracy,F-measure,precision,and recall are considered for testing versions of the proposed iris liveness detection technique.
5.1 Clarkson LivDet2013 Results
Fig.3 compares the performance of the investigated fragmental coefficients for a particular ML classifier in the proposed technique of iris liveness detection, which was evaluated on the Clarkson 2013 dataset.In Fig.3,it can be seen that fragmental coefficients 8*8 outperformed other fragmental coefficient combinations for all classifiers. The highest noted iris liveness detection accuracy comes around 98.10%,with 8*8 fragmental coefficients using a RF classifier.

Figure 3:Performance assessment of considered fragmental coefficients for specific ML classifiers in iris liveness detection for Clarkson 2013 dataset
From Fig.4, it has been noted that the performance improves as the size of the feature vector is reduced from 256*256 to 8*8 and then begins to deteriorate with feature vector size 4*4.This demonstrates that the fragmental coefficients of Haar transformed iris images provide more outstanding iris liveness recognition capabilities while maintaining a small feature vector size,proving the importance of the suggested method. The highest average accuracy, 95.94% achieved by 16*16 fragmental coefficients.
Tsarevitch Ivan climbed the wall, entered the iron railing and found the three cages as the Gray Wolf had said. He took out the Fire Bird and wrapped it in his handkerchief, but he could not bear to leave behind him the beautiful golden cage.
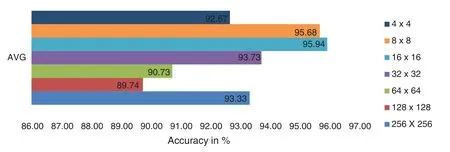
Figure 4: The performance assessment for the Clarkson 2013 dataset by averaging the specific fragmental coefficients in iris liveness detection
Table 5 appraises the performance of specific ML classifiers and ensembles of classifiers for iris liveness detection tested on the Clarkson 2013 dataset. From Table 5, it can be noted that NB classifiers give the highest average ACER, whereas the lowest average ACER, 2.63% achieved by SVM+MLP+RF ensembles of classifiers.

Table 5: ML classifier’s performance evaluation in the proposed iris liveness detection approach for Clarkson 2013 dataset using an average of%accuracy,%APCER,%BPCER,and%ACER values
5.2 IIITD Combined Spoofing Database Results
Fig.5 reflects the performance comparison of considered Fragmental coefficients for particular ML classifiers in the proposed iris liveness detection,tested on IIITD CSD.Here,it is noted that,for all classifiers,4*4 fragmental coefficients outperformed other fragmental coefficient combinations for IIITD CSD.The highest accuracy,97.94%achieved by using an RF classifier.Because of its significant energy compaction,Haar can produce the best results with 4*4 fragmental coefficients.
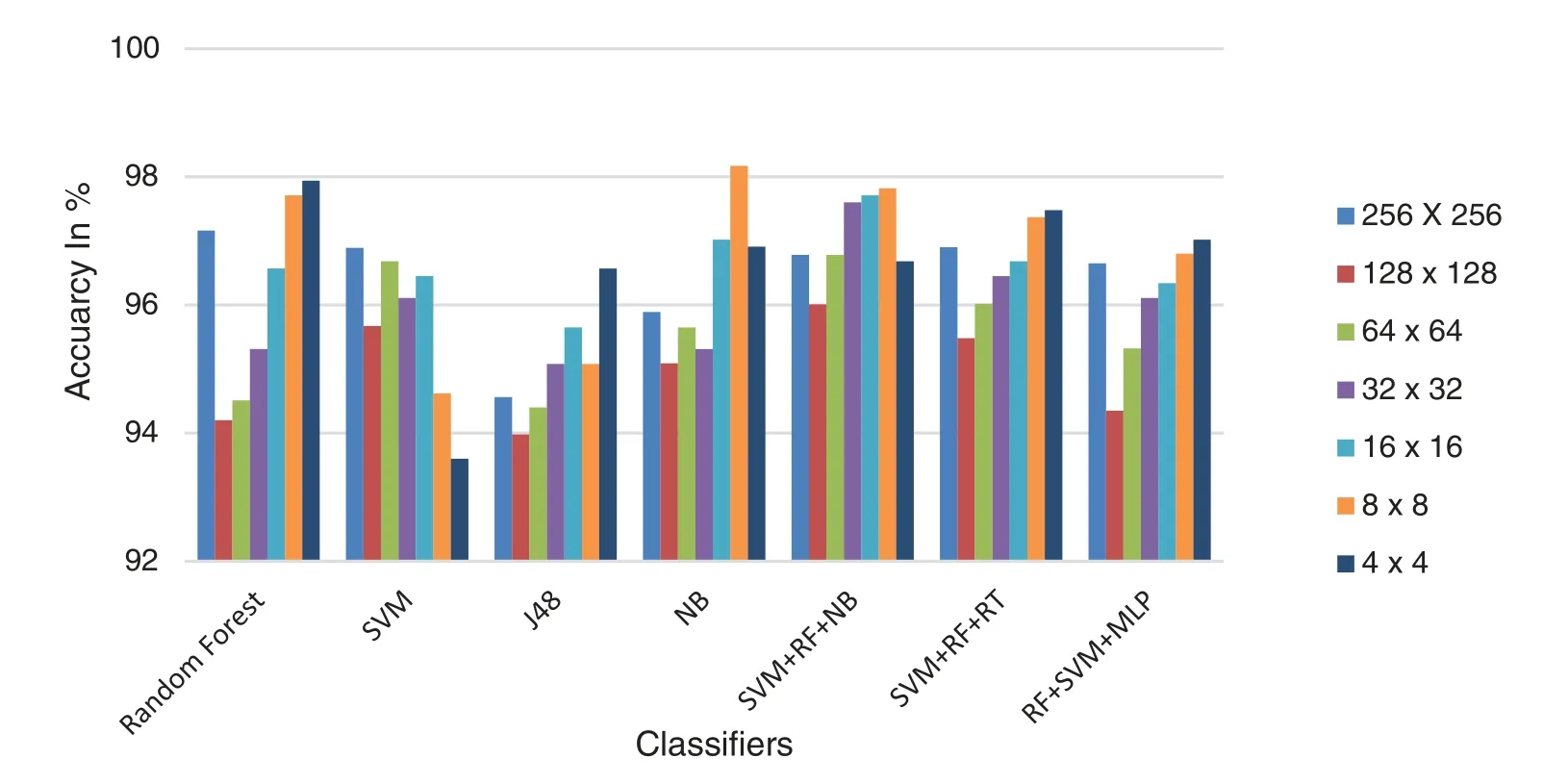
Figure 5:Performance assessment of considered fragmental coefficients for specific ML classifiers in iris liveness detection for IIITD CSD dataset
From Fig.6,it can be seen that the performance improves as the feature vector size is compacted from 256*256 to 8*8 and then begins to deteriorate with feature vector size 4*4.This demonstrates that the fragmental coefficients of Haar transformed iris images provide more excellent iris liveness recognition capabilities while maintaining a small feature vector size. The highest average accuracy,96.80%achieved by 8*8 fragmental coefficients.
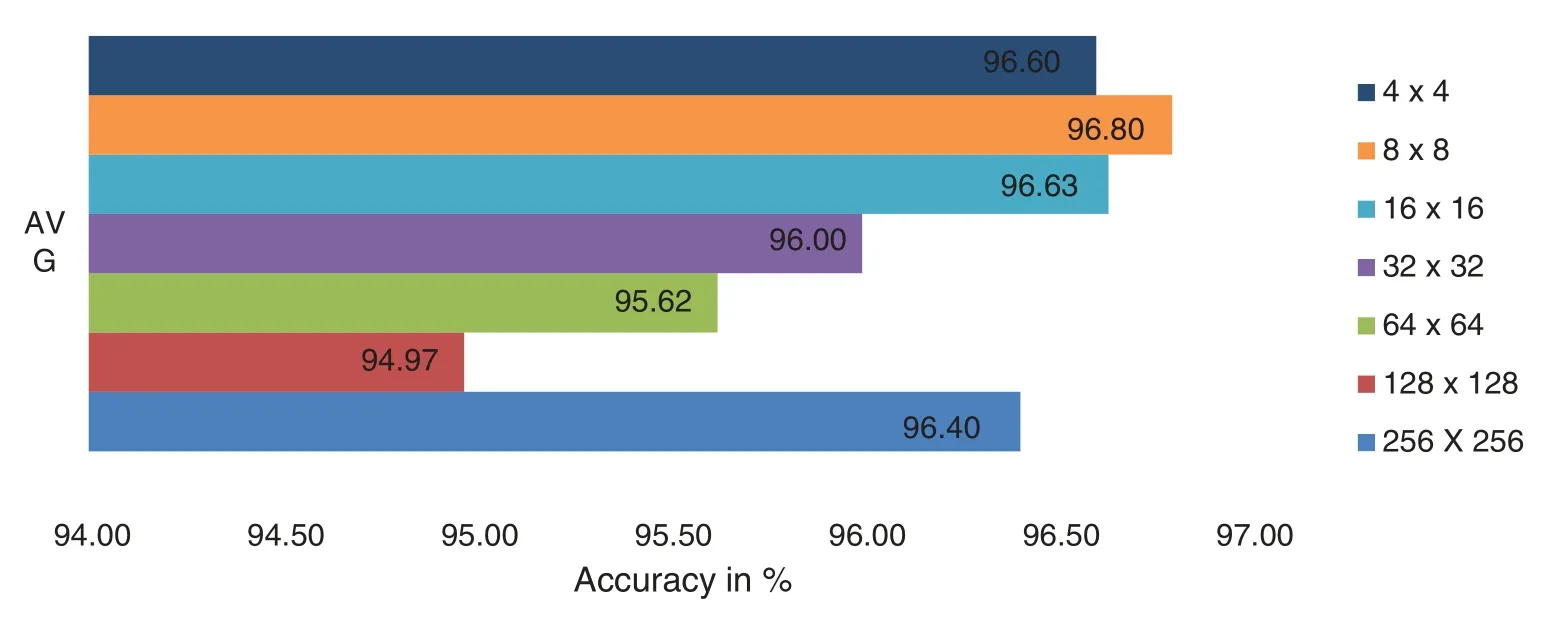
Figure 6: Performance assessment by averaging the specific fragmental coefficients in iris liveness detection for IIITD CSD
Table 6 provides the performance assessment of specific ML classifiers and ensembles of classifiers in the projected iris liveness detection explored on the IIITD CSD dataset.It is noted from the table that Decision Tree(J48)classifiers give the highest average ACER,whereas the lowest average ACER,2.29%,is achieved by SVM+NB+RF ensembles of classifiers.The majority voting technique generates ensembles of classifiers,so they provide the best classification accuracy.
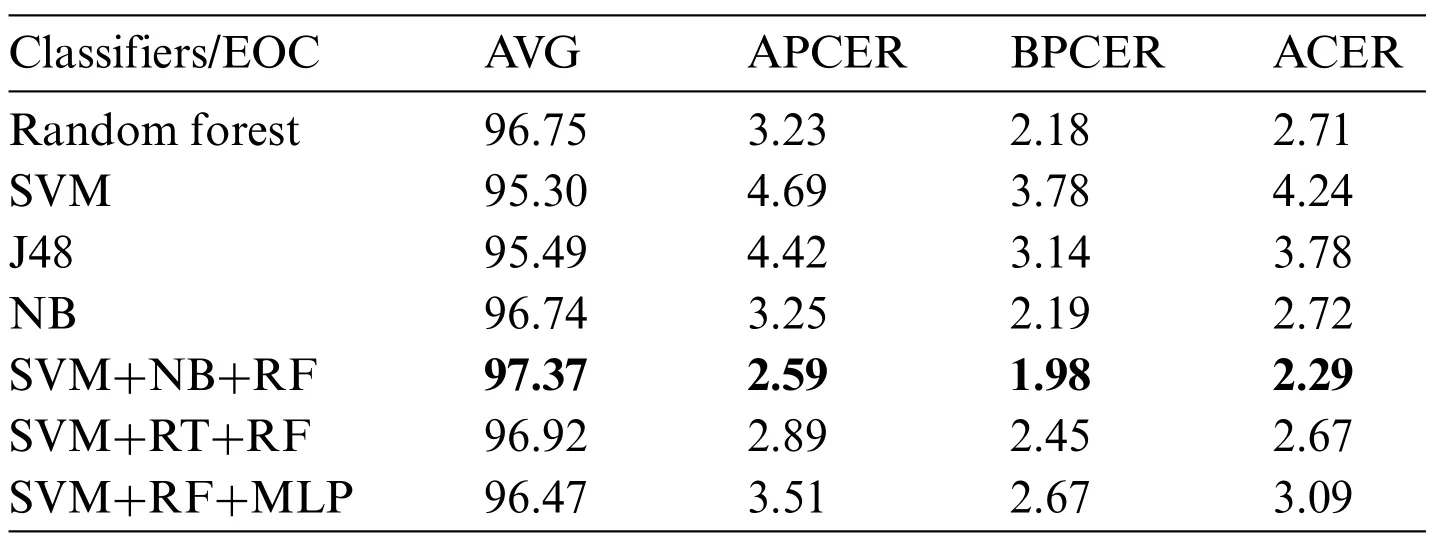
Table 6: Performance evaluation of ML classifiers in the proposed iris liveness detection for IIITD CSD dataset with an average of%accuracy,%APCER,%BPCER,and%ACER values
5.3 Clarkson 2015
Fig.7 reflects the performance comparison of considered Fragmental coefficients for particular ML classifiers in proposed iris liveness detection,tested on the Clarkson 2015 dataset.Here,it is noted that for all classifiers,16*16 fragmental coefficients outperformed other fragmental coefficient combinations for Clarkson 2015 dataset.The highest accuracy,99.90%achieved by using an SVM+RF+RT ensemble classifier. Because of its significant energy compaction, Haar can produce the best results with 8*8 fragmental coefficients.
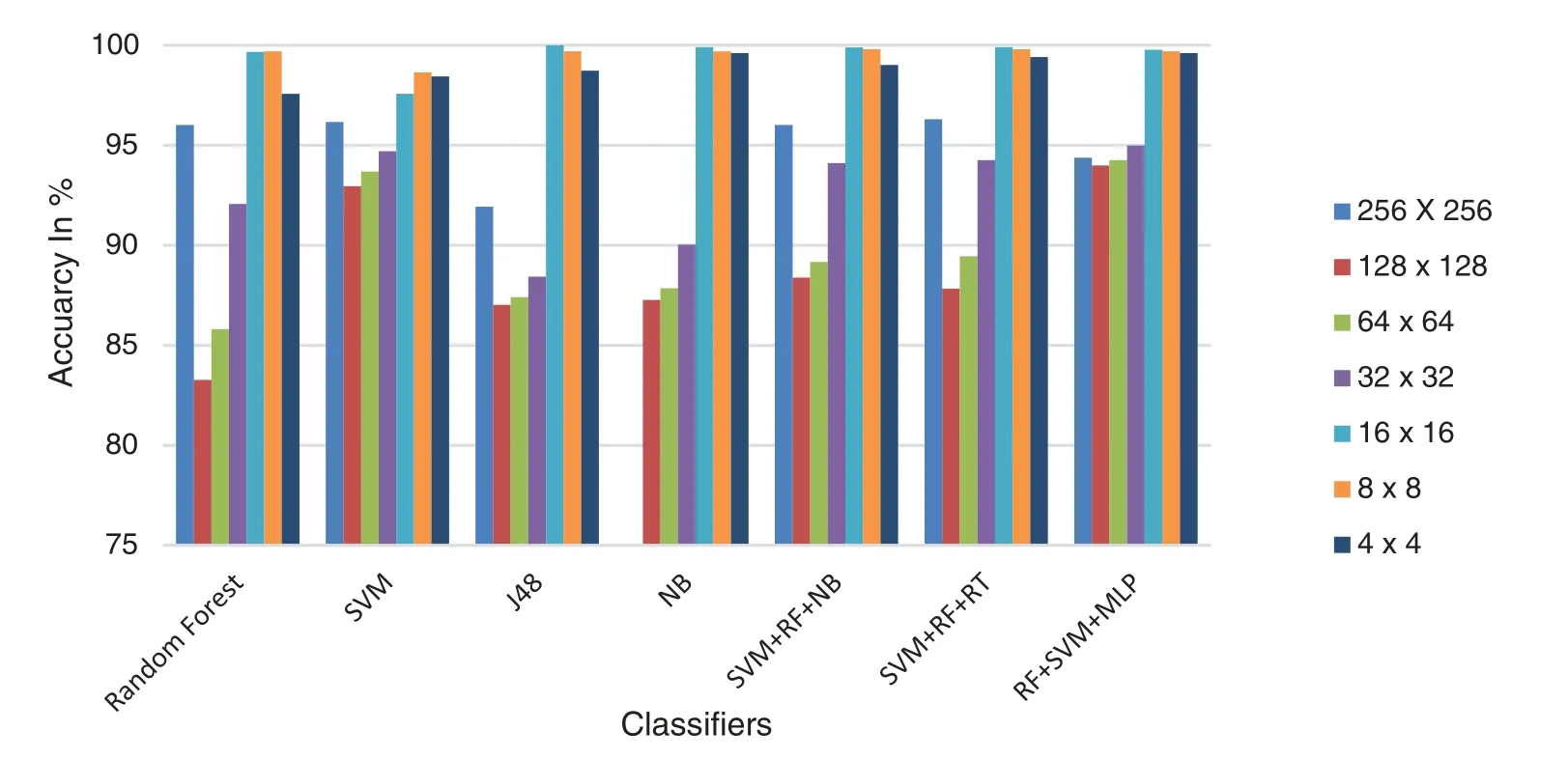
Figure 7:Performance assessment of considered fragmental coefficients for specific ML classifiers in iris liveness detection for Clarkson 2015 dataset
From Fig.8, it has been noted that the performance improves as the feature vector size is compacted from 256*256 to 8*8 and then begins to deteriorate with feature vector size 4*4.This demonstrates that the fragmental coefficients of Haar transformed iris images provide more excellent iris liveness recognition capabilities while maintaining a small feature vector size.The highest average accuracy,99.58%achieved by 8*8 fragmental coefficients.
Table 7 gives the performance assessment of specific ML classifiers and ensembles of classifiers in the projected iris liveness detection explored on the Clarkson 2015 dataset. It is noted from the table that Decision Tree (J48) classifiers give the highest average ACER, whereas the lowest average ACER,3.2%,is achieved by SVM+RF+MLP ensembles of classifiers.The majority voting technique generates ensembles of classifiers,so they provide the best classification accuracy.
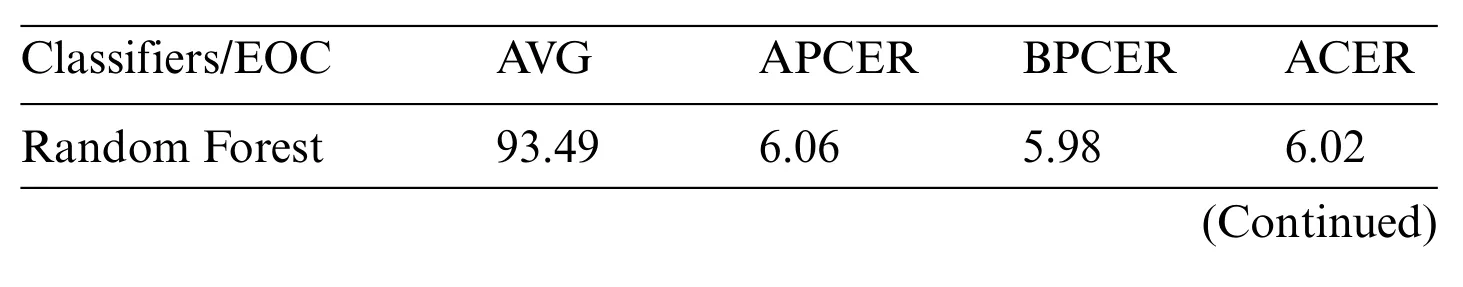
Table 7: Performance evaluation of ML classifiers in the proposed iris liveness detection for Clarksonclarkson 2015 dataset with an average of%accuracy,%APCER,%BPCER,and%ACER values
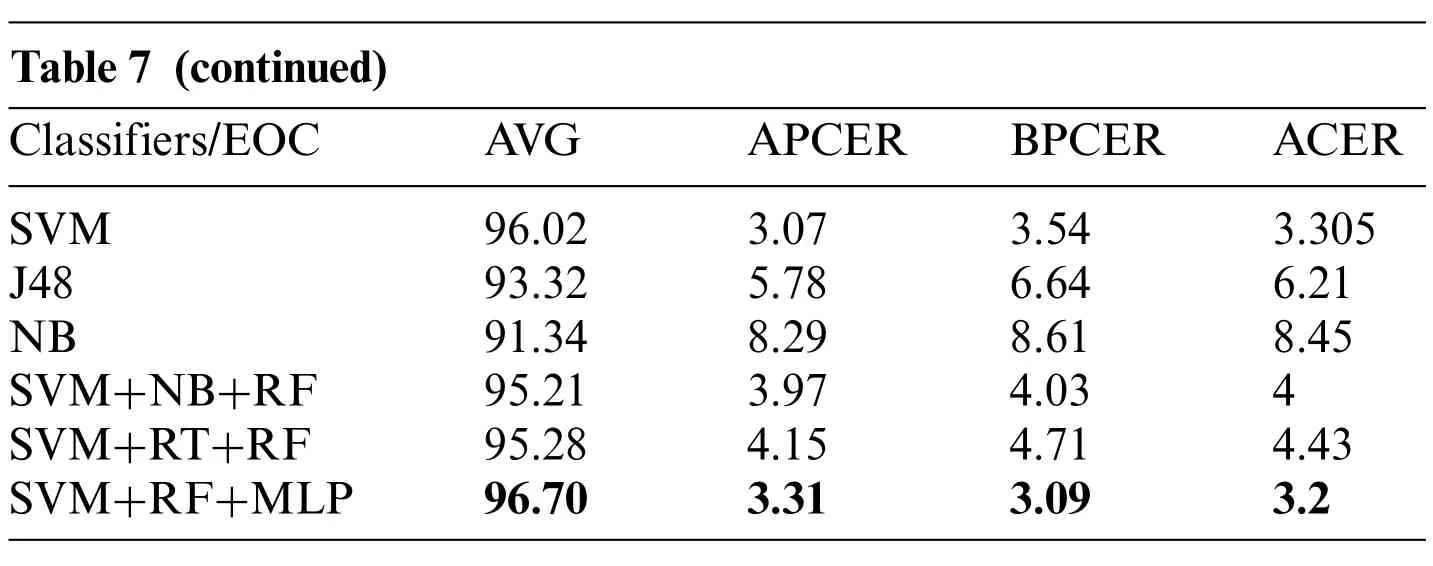
Table 7 (continued)Classifiers/EOC AVG APCER BPCER ACER SVM 96.02 3.07 3.54 3.305 J48 93.32 5.78 6.64 6.21 NB 91.34 8.29 8.61 8.45 SVM+NB+RF 95.21 3.97 4.03 4 SVM+RT+RF 95.28 4.15 4.71 4.43 SVM+RF+MLP 96.70 3.31 3.09 3.2
5.4 Cross Datasets Evaluation Results
In this section, the results of cross datasets performances are explained in detail [33]. The first scenario,where model train on Clarkson 2015 datasets was evaluated on the Clarkson 2013 and IIITD test datasets. The evaluation results are presented in Table 8, where bold digits indicate the highest accuracy.From Table 8,we observed that Clarkson’s 2015 datasets give a lower ACER of nearly zero percent. However, Clarkson’s 2013 datasets do not perform well and give a high ACER of around 74%.

Table 8: Cross datasets evaluation
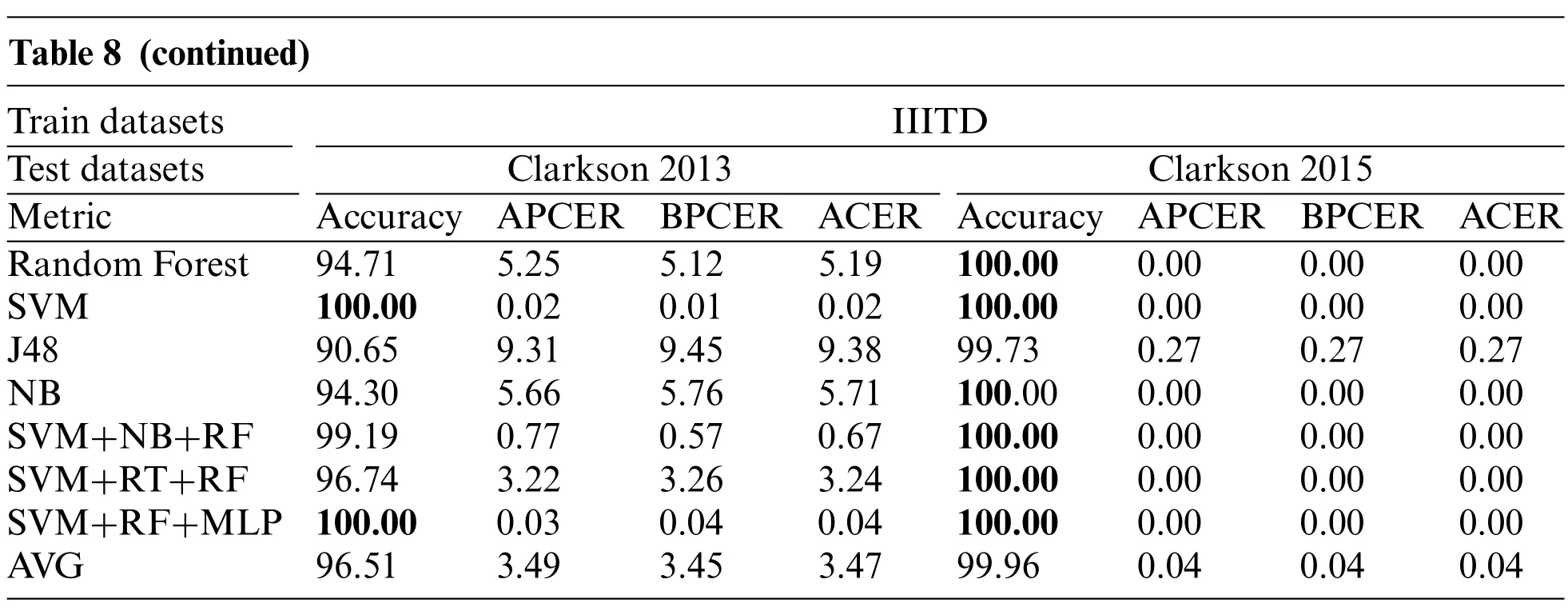
Note:The highest performance is represented in bold.
In this section,the results of cross datasets performances are explained.The first scenario,where model train on Clarkson 2015 datasets was evaluated on the Clarkson 2013 and IIITD test datasets.The evaluation results are presented in Table 8,where bold digits indicate the highest accuracy.From Table 8, we observed that Clarkson 2015 gives a lower ACER of nearly zero percentage. However,Clarkson 2013 datasets do not perform well and give a high ACER of around 74%.
Fig.9 shows performance evaluation on cross datasets.It can be seen that our model outperforms in IIITD and Clarkson 2015 datasets,however,shows low performances for Clarkson 2013 dataset.One possible reason for this is Clarkson 2013 dataset has a smaller number of images compared to the other two datasets.
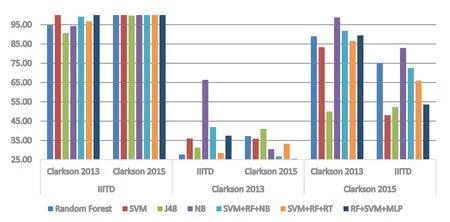
Figure 9:Performance assessment on cross datasets evaluation
Table 9 represents the performance comparison of fragmental coefficients across all datasets used for implementation with an average of percent accuracy,percent precision,percent recall,and percent F-ratio values.The highest performance is represented in bold and underlined.From Table 8,it can be seen that reducing the number of higher energy coefficients from 128*128 to 8*8 improves performance since the common part is reduced and discriminative is emphasized more.
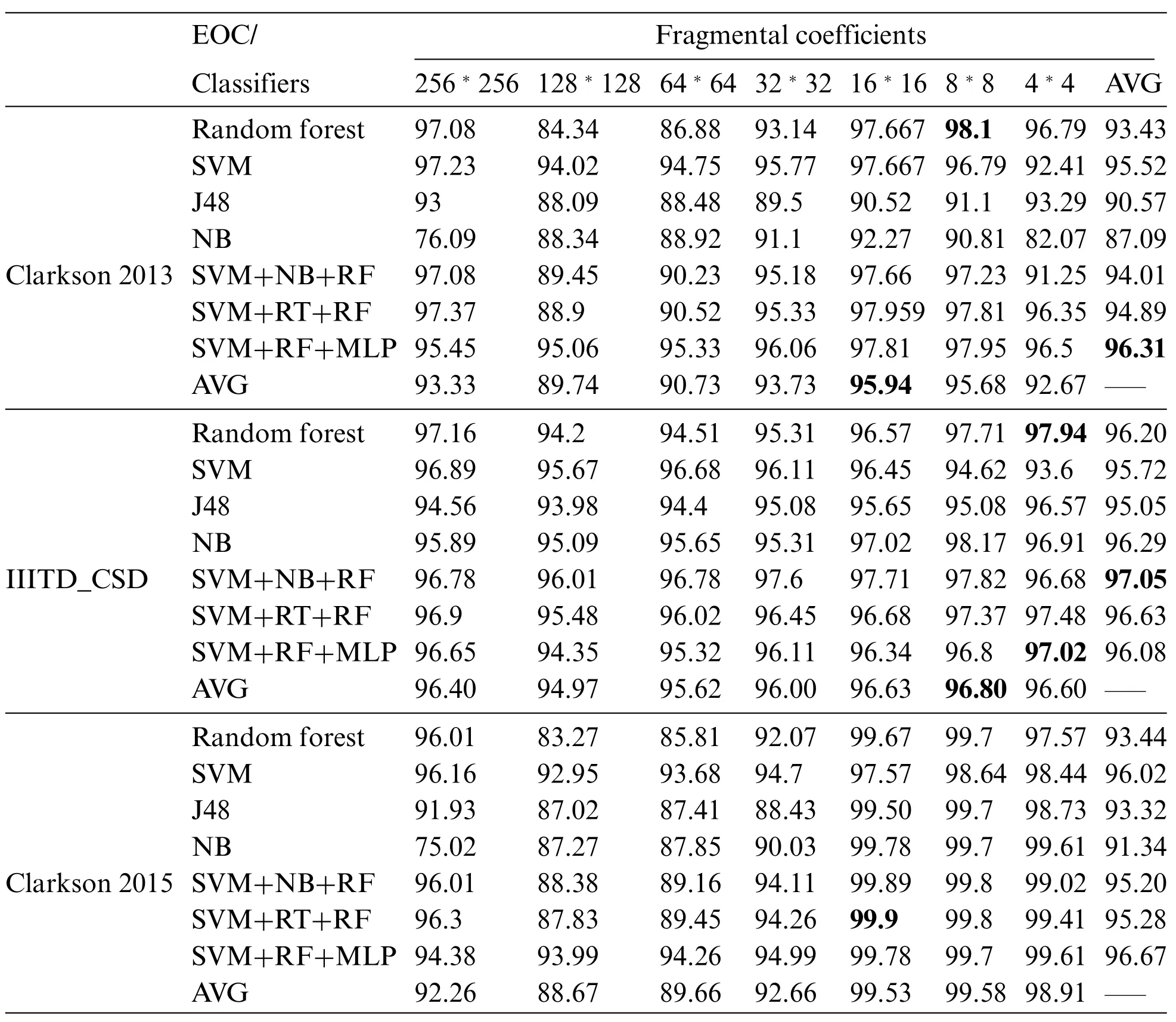
Table 9: Performance comparison of fragmental coefficients with an average of percent accuracy,percent precision,percent recall,and percent F-ratio values
6 Discussion
The proposed experiment was performed using the Haar transform. The fundamental goal of experimenting with the transform domain is to learn more about how the image is split into low and high-energy parts,reducing the feature vector size and speeding up retrieval.The Haar statistic is used to transform data[27].
By applying Haar transform on Iris images, high energy coefficients of transformed iris images sized 256*256, 128*128, 64*64, 32*32, 16*16, 8*8, and 4*4 do generate feature vectors for the projected iris-liveness detection. The procedures outlined in Section 3.2 are used to create the feature vector.Seven distinct ML and ensembles of classifiers are trained using these features.These classifiers are trained using the tenfold cross-validation method to detect presentation attacks.Three benchmark datasets are taken for testing: Clarkson 2013, Clarkson 2015, and the IIITD combined spoofing database.These three datasets explain in Section 4.1.Accuracy,Precision,Recall,and F-ratio and ISO standard metrics APCER,BPCER,and ACER are utilized to compare the performance of all the variants of the suggested approach.Section 4.2 describes several performance measures.
As stated in Sections 5.1 and 5.2, feature extraction using Haar has shown outstanding average classification accuracy. For the Clarkson 2013 dataset, the highest noted iris liveness detection accuracy comes around 98.10%, with 8*8 fragmental coefficients obtained using the classifier RF.The highest average accuracy, 95.94% was achieved by 16*16 fragmental coefficients, whereas the maximum average accuracy was 96.31%, and the average ACER was around 2.63%, achieved by SVM+MLP+RF ensembles of classifiers. For Clarkson 2015, the highest accuracy achieved was 99.90%by using an SVM+RF+RT ensemble classifier.For IIITD CSD,the uppermost accuracy of 97.94%was obtained by using the RF classifier.The uppermost average accuracy was 96.80%achieved by 8*8 fragmental coefficients,whereas the utmost average accuracy was 97.05%,and average ACER was around 2.29%,achieved by SVM+NB+RF ensembles of classifiers.The findings show that our suggested approach distinguishes between the bonafide and presentation attack images artifacts using the Haar transform approach.Table 10 shows a comparison of the suggested strategy to recent studies in this area.
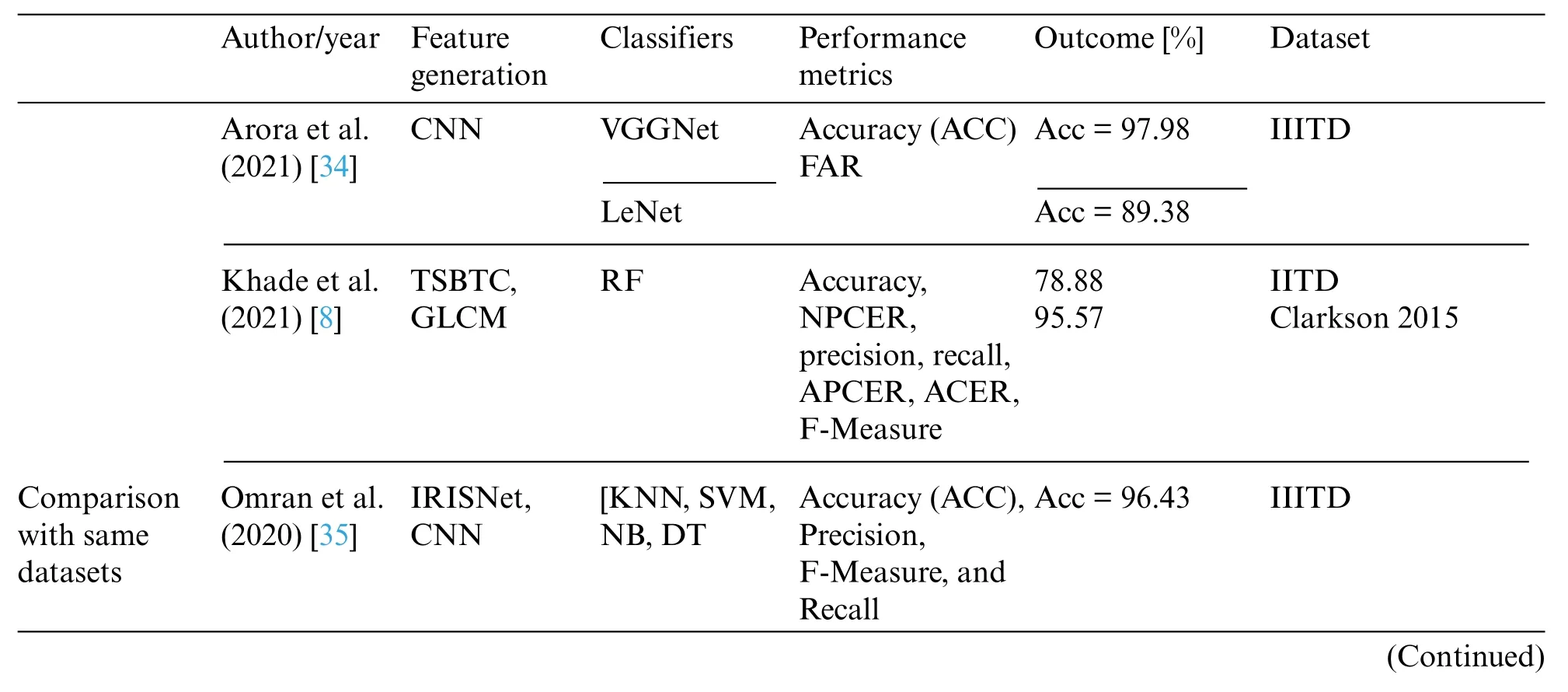
Table 10: The comparison of the prevailed methods with the proposed approach
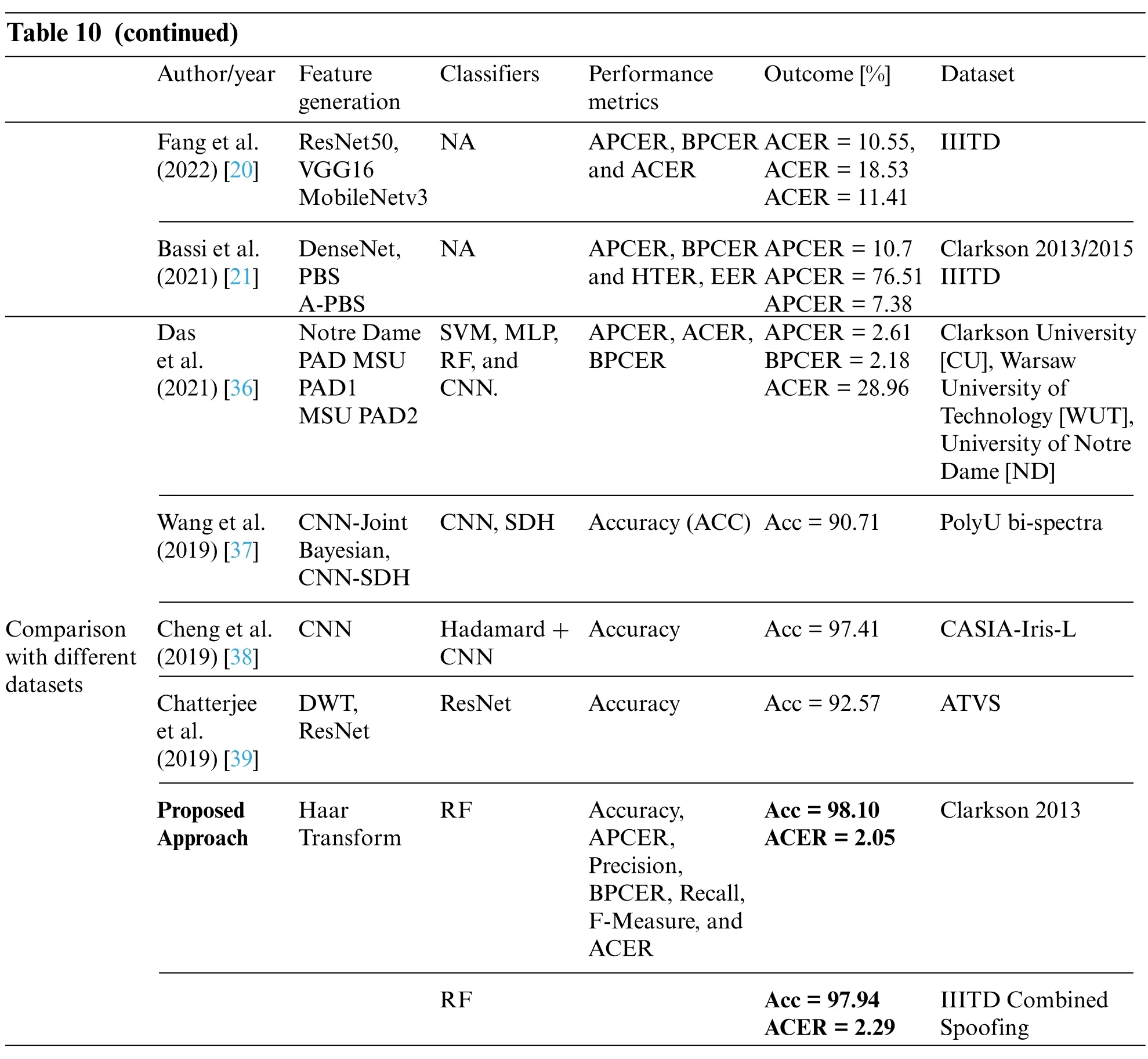
Table 10 (continued)Author/year Feature generation Classifiers Performance metrics Outcome[%] Dataset Fang et al.(2022)[20]ResNet50,VGG16 MobileNetv3 NA APCER,BPCER and ACER ACER=10.55,ACER=18.53 ACER=11.41 IIITD Bassi et al.(2021)[21]DenseNet,PBS A-PBS NA APCER,BPCER and HTER,EER APCER=10.7 APCER=76.51 APCER=7.38 Clarkson 2013/2015 IIITD Das et al.(2021)[36]Notre Dame PAD MSU PAD1 MSU PAD2 SVM,MLP,RF,and CNN.APCER,ACER,BPCER APCER=2.61 BPCER=2.18 ACER=28.96 Clarkson University[CU],Warsaw University of Technology[WUT],University of Notre Dame[ND]Wang et al.(2019)[37]CNN-Joint Bayesian,CNN-SDH CNN,SDH Accuracy(ACC) Acc=90.71 PolyU bi-spectra Comparison with different datasets Cheng et al.(2019)[38]CNN Hadamard+CNN Accuracy Acc=97.41 CASIA-Iris-L Chatterjee et al.(2019)[39]DWT,ResNet ResNet Accuracy Acc=92.57 ATVS Proposed Approach Haar Transform RF Accuracy,APCER,Precision,BPCER,Recall,F-Measure,and ACER Acc=98.10 ACER=2.05 Clarkson 2013 RF Acc=97.94 ACER=2.29 IIITD Combined Spoofing
Compared to similar current techniques based on fragmented energy, the Haar transformation better discerns between real and artificial artifacts.The results reveal that the proposed method reduces classification error and gets better accuracy when compared to earlier ways of detecting presentation attacks using an iris liveness detection.Table 10 summarizes this information.The proposed strategy outperforms some recent existing studies. As many recent studies used the different train and test datasets,so we partition Table 10 into two parts,comparing with same datasets and different datasets.Even though some studies outperform,our approach achieved this performance with reduced feature vector size(only with 64 features).
While implementing this study, we faced a few challenges-one of them was getting access to datasets with permissions for use in experimentation. The second challenge we faced was the explorations of the proposed method with the number of test runs was time-consuming task.
The limitations of the study are:(i)it was applied only two pre-processing techniques like resizing and converting an image into grayscale; (ii) this experiment is limited to image size 256 by 256 and only grayscale images were used during this study.
7 Conclusion
The paper proposed a new method for determining iris liveness. Until now, several approaches have relied on pre-processing, such as iris segmentation, localization, and normalization; however,this method of iris liveness detection is computationally intensive. The suggested method employs Haar transforms on iris images to address this issue, obtaining fragmental coefficients as feature vectors. The Haar transformed iris image fragmental coefficients are used to train various ML and ensemble algorithms. Seven criteria are considered to compare the performance of variants of the suggested approach.Various metrics such as accuracy,precision,recall,f-measure,APCER,BPCER,and ACER are used to check the performance of the models.Presentation attack images are detected with 98.10%accuracy in the Clarkson 2013 dataset.The best accuracy for IIITD-CSD was 97.94%.The experimental results prove the effectiveness of the projected method for detecting iris spoofing attacks. The study’s main contribution is achieving a good accuracy of 98.10% with lesser feature vector size by using the fragmental coefficients of the Haar transformed iris image of size 8*8 utilizing a RF algorithm with reduced featured vector size.The reduction in considered feature vector size of iris images with improved accuracy of liveness detection is achieved by exploiting the energy compaction property of Haar transform in the proposed method. The method is tested on three available benchmark datasets for validation of results in a generic form.The cross-dataset validations are performed to prove the worth of the proposed method.The main limitations of this study are as follows:only two pre-processing techniques were applied,such as resizing and converting an image into grayscale.Moreover,this experiment is limited to image size 256 by 256 and only grayscale images are used.In future work,this framework may be extended with the best performance features.Currently,the presented work is limited to the exploration of explored Haar transform features only.However,the hybridization of transform using Haar,DCT and Kekare transforms would be an exciting exploration in the future. Moreover, the proposed framework may be applied for the liveness detection of other biometric traits,like face,fingerprints,etc.The best performance features a level fusion of fragmental coefficients of Haar may be added to this framework in future work.
Author Contributions:Data curation:Smita Khade;Writing original draft:Smita Khade;Supervision:Shilpa Gite,Biswajeet Pradhan;Project administration:Shilpa Gite,Biswajeet Pradhan;Conceptualization:Sudeep Thepade;Methodology:Sudeep Thepade,Shilpa Gite;Validation:Biswajeet Pradhan;Visualization:Sudeep Thepade,Smita Khade,Shilpa Gite,Biswajeet Pradhan;Resources:Biswajeet Pradhan,Abdullah Alamri;Review&Editing:Sudeep Thepade,Biswajeet Pradhan;Funding acquisition:Biswajeet Pradhan,Abdullah Alamri.
Funding Statement:The Centre for Advanced Modelling and Geospatial Information Systems(CAMGIS), Faculty of Engineering and Information Technology, the University of Technology Sydney,Australia,has funded the research.This research is also partially supported by the Researchers Supporting Project No.RSP-2021/14,King Saud University,Riyadh,Saudi Arabia.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computer Modeling In Engineering&Sciences2023年7期
Computer Modeling In Engineering&Sciences2023年7期
- Computer Modeling In Engineering&Sciences的其它文章
- Edge Intelligence with Distributed Processing of DNNs:A Survey
- Turbulent Kinetic Energy of Flow during Inhale and Exhale to Characterize the Severity of Obstructive Sleep Apnea Patient
- The Effects of the Particle Size Ratio on the Behaviors of Binary Granular Materials
- A Novel Light Weight CNN Framework Integrated with Marine Predator Optimization for the Assessment of Tear Film-Lipid Layer Patterns
- Implementation of Rapid Code Transformation Process Using Deep Learning Approaches
- A New Hybrid Hierarchical Parallel Algorithm to Enhance the Performance of Large-Scale Structural Analysis Based on Heterogeneous Multicore Clusters
