Security in Edge Blockchains:Attacks and Countermeasures
CAO Yinfeng,CAO Jiannong,WANG Yuqin,WANG Kaile,LIU Xun
(Department of Computing,The Hong Kong Polytechnic University,Hong Kong SAR 852,China)
Abstract: Edge blockchains,the blockchains running on edge computing infrastructures,have attracted a lot of attention in recent years.Thanks to data privacy,scalable computing resources,and distributed topology nature of edge computing,edge blockchains are considered promising solutions to facilitating future blockchain applications.However,edge blockchains face unique security issues caused by the deployment of vulnerable edge devices and networks,including supply chain attacks and insecure consensus offloading,which are mostly not well studied in previous literature.This paper is the first survey that discusses the attacks and countermeasures of edge blockchains.We first summarize the three-layer architecture of edge blockchains: blockchain management,blockchain consensus,and blockchain lightweight client.We then describe seven specific attacks on edge blockchain components and discuss the countermeasures.At last,we provide future research directions on securing edge blockchains.This survey will act as a guideline for researchers and developers to design and implement secure edge blockchains.
Keywords: blockchain;edge computing;security;survey
1 Introduction
Edge computing has developed rapidly in recent years and raised wide interest from both industry and academia[1].As a new computing model,edge computing extends cloud computing to the network edge and utilizes rich computation,storage,and networking resources on large-scale distributed devices.In edge computing,the optimization techniques on resource allocation and scheduling are extensively studied,enabling computation tasks to be divided and offloaded to the optimal edge devices according to different constraints.As a result,edge computing plays an important role in maintaining low latency,supporting heterogeneity,and improving applications’ quality of service (QoS),such as virtual reality,distributed machine learning,wireless sensing,and robotics.
At the same time,the concept of edge blockchains has also been proposed.It refers to the blockchains deployed on edge computing infrastructures.Edge blockchains inherit favorable features from edge computing,like data privacy,scalable computing resources,and distributed topology.Thereby,edge blockchains are more suitable for large-scale applications than traditional blockchains hosted on the cloud or onpremise machines.For example,applications like blockchainbased federated learning,blockchain-based security middleware in the Internet of things (IoT),and metaverse essentially rely on edge blockchains[2–4].
However,the security in edge blockchains is not well understood in existing works.Specifically,in the works alleged“blockchain-based edge computing”[2,5–6],the edge blockchains are typically assumed to be secure and trusted.On the contrary,in real implementation,it is challenging to protect and keep the edge blockchain networks functioning in edge environments for many practical reasons,like vulnerable lowend edge devices,unstable networks,and centralized provider corruption.Thus,it is desired to analyze the critical security issues facing edge blockchains.
To fill this gap,we investigate and evaluate the security in edge blockchains systematically.Our survey essentially differs from previous blockchain security surveys and provides more practical details[7–9].As shown in Fig.1,we start by describing the motivation and summarizing the system architecture and applications of edge blockchains to provide readers with a brief overview in Section 2.Then in Section 3,we discuss the core components of an edge blockchain,e.g.,blockchain management,blockchain consensus,and blockchain lightweight clients,in terms of potential attacks and countermeasures.Finally,we point out the challenging issues and future directions for securing edge blockchains in Section 4.

▲Figure 1.Structure of this survey
2 Overview of Edge Blockchains
2.1 Motivations
In recent years,the blockchain technology and its applications have received extensive attention from the research community and industry[10].Blockchain is a decentralized ledgerbased Byzantine fault tolerant (BFT) consensus system.Under a bounded number of adversary environments,blockchain nodes can reach chain-linked agreements on incoming transactions with traceability,immutability,and transparency.Besides,the consensus procedure does not rely on a trusted third party (TTP),making blockchain systems trustless and hard to tamper with.
Nowadays,the blockchain technology is still facing several bottlenecks,thus seriously restricting its application scenarios and making it inaccessible in the real world.Among them,blockchain’s decentralization,scalability,and security are considered the most significant and recognized as a trilemma[11].Generally speaking,existing works cannot well satisfy all three properties together.
·Decentralization.Making blockchain run without trust depends on a small group of centralized actors with specialized rights.
·Scalability.Processing numerous transactions in the network simultaneously with low latency.
·Security.Resisting a certain percentage of Byzantine nodes that can conduct arbitrary adversary behaviors.
Although blockchain theoretical advancement keeps appearing,some researchers have begun to focus on infrastructure-level solutions to improving blockchain performance.Edge computing shares a similar system architecture with blockchain and can provide the needed computing resources for blockchain systems,which can be a promising option[12–13].By employing edge computing as blockchain infrastructures to realize edge blockchains,blockchain trilemma can be further resolved simultaneously in terms of the above-mentioned properties.In particular,1) for keeping decentralization,edge computing physically guarantees the hierarchical and decentralized architecture of blockchain.Edge computing has a layered architecture with a largescale distributed edge device network to keep the on-device blockchain nodes from centralization.2) For improving scalability,edge computing has rich computation,storage,and networking resources accomplished with automatic optimization of resource allocation and scheduling.These resources can be utilized by blockchain to realize a large-scale blockchain network.3) For enhancing security,edge computing provides permission environments with data privacy guarantees,reducing Byzantine nodes’ risks and thus relaxing the blockchain security assumption for better performance.In conclusion,edge blockchains can offer better decentralization,scalability,and security with lower latency for applications than normal blockchains deployed on public cloud environments or distributed individual devices.
2.2 Architecture
To comprehensively analyze and understand edge blockchains,we first present their architecture,components,and functionalities.Based on the existing literature and platforms,we find that the edge blockchain system architecture typically follows a three-layer pattern including a cloud server layer,an edge server layer,and a mobile device layer,with different blockchain components and functionalities,as shown in Fig.2.To be specific,we conclude each layer’s components and functionalities as follows:
·Cloud server layer: blockchain network management.The cloud server in edge computing has knowledge of network specifications and attached edge devices connectivity.Therefore,the cloud servers are typically set to configure,deploy,and monitor the edge blockchain networks to reduce management costs.
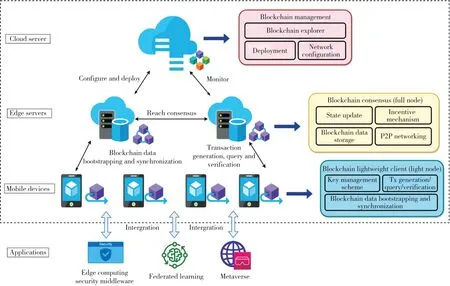
▲Figure 2.System architecture of a typical edge blockchain which follows a three-layer pattern with different blockchain components and functionalities
·Edge server layer: blockchain consensus for incoming transactions.Edge servers are close to the data source and provide more computing resources than mobile devices.Thus,it is reasonable to deploy blockchain full nodes at this layer to have sufficient resource support for updating ledger states and incentive nodes,storing blockchain data,and communicating with other nodes.
·Mobiledevice layer: blockchain lightweight client (light node) for transaction operations (generation,query,and verification).Edge applications interact with blockchain through numerous transactions from large-scale mobile devices.Deploying the interfaces for transaction operations and maintaining partial blockchain data (blockchain data bootstrapping and synchronization) at this layer can significantly reduce the latency and improve QoS.Besides,the key management schemes for protecting signing keys are also integrated to support transaction operations.
2.3 Applications
Edge blockchains feature high QoS and security guarantees in edge environments.In the current stage,edge blockchain solutions are application-specific,which means that they are typically embedded with applications to improve their performance.Here we summarize the three representative types as follows.
·Security middleware for edge computing[2,14–15].Edge blockchains can be utilized as security middleware to tackle security issues in the edge computing infrastructure.For instance,detecting unstable or low-performance edge devices and designing strategies to avoid using these devices are challenging research issues in the edge resources optimization area.To address these issues,reputation systems with incentive mechanisms can be built upon edge blockchains.They record the status of edge devices and provide trusted reference information for strategy design and decision making in edge optimization algorithms.Besides,other efforts like secure data sharing methods,authentication schemes,and control systems based on edge blockchains are also proposed to enhance edge computing security.
·Edge-based federated learning[3,16–17].Edge-based federated learning is a distributed machine learning scheme that collects closed-source data to train global models in a privacy-preserving and personalized manner.However,due to the self-voluntary ways to contribute to model updates,malicious behaviors may occur and affect the quality of global models,e.g.,poison attacks.To this end,blockchain is proposed to provide failure tolerance ability,malicious behavior detection,and incentive mechanisms for securing and boosting federated learning.
·Metaverse[4,18–19].Metaverse is a trendy edge application aiming to build a virtual world with immersive experience.Edge-based VR and blockchain-based economic systems are two critical techniques for the metaverse.Edge blockchains provide lower latency,better decentralization,and better personal data privacy than blockchains in the cloud,thus making the metaverse scalable and trusted.
2.4 Challenges
Deploying blockchains at the edge will bring extra challenges,especially from security aspects.On the one hand,vulnerable edge devices,unstable network conditions,and physical accessibility expose many attack interfaces on edge blockchains to adversaries.On the other hand,designing sufficient and efficient security solutions on resourceconstrained edge devices is challenging.
For example,efficient and secure key management is challenging in edge blockchains.Traditional methods like using custodial wallet software require considerable computing resources on edge devices,which are also insecure since external attackers can access the devices.Ideal solutions should be lightweight but also can prevent such kinds of attacks.Another example can be the task-offloading feature of edge computing.Offloading tasks to arbitrary nodes in blockchain networks is risky since the blockchain nodes do not trust each other.Malicious nodes could collect the offloaded tasks to gain illegal benefits and launch attacks by forging identities.
3 Attacks and Countermeasures
In this section,we describe the critical security issues and attacks of edge blockchains in each layer.We also present and analyze the state-of-the-art countermeasures for reference in each subsection.We summarize these contents with brief descriptions in Table 1.
3.1 Blockchain Management
Blockchain management aims to configure,deploy,and monitor edge blockchain networks.In edge blockchains,such procedures are typically implemented by centralized service providers,e.g.,Blockchain-as-a-Service (BaaS) platforms,due to costeffective concerns[20–23].These platforms provide the tools or software development kits (SDKs) to define the blockchain network in client software,access control,deployment methods,etc.For example,AWS Blockchain Template is a tool for configuring cloud-based Ethereum[24]or hyperledger fabric networks[25].
3.1.1 Identity Credential Provider Compromise
In edge blockchains or other consortium blockchains,identity credentials are required to authenticate the participation legality of users or organizations.Identity credentials can be certificate authority/public key infrastructure (CA/PKI) certificates and public/private key pairs,which are generated and assigned to blockchain nodes.These credentials specify the vote right,communication channels,and data access.For popular frameworks in edge blockchains,like Hyperledger Fabric,X.509 CA-based Membership Service Provider (MSP)is responsible for participation identity management;in IBM blockchain,blockchain identities are associated with Azure Active Directory,a unified access control mechanism in Azure Cloud[26].In edge blockchain literature,similar mechanisms are also applied to authenticate edge devices that run blockchain nodes[27–29].However,due to the centralized nature of this procedure,blockchain management procedures in edge blockchains are vulnerable to many attacks,even to traditional cyber attacks.
Although nodes themselves keep the credentials,the issue,update,and revoke operations are typically performed by centralized providers (e.g.,blockchains using CA/PKI),which is risky to adversaries.Existing works show that if such providers are compromised,many other level attacks may be conducted and further damage the blockchain networks[30–31].Malicious providers can manipulate and subvert identity management by making legal credentials invalid,refusing to issue,and even issuing illegal credentials to launch a Sybil attack.Eventually,malicious providers will control the full blockchain networks and could launch arbitrary attacks.
State-of-the-Art countermeasures focus on making blockchain identity management decentralized and transparent.In Geth (Proof of Authority consensus mode) and Tendermint,new validators are elected to have vote rights by original validators,which are initially from the hard-coded genesis block[32–33].This way increases the difficulty for adversaries to compromise since it is equivalent to tamper the entire blockchain.The substantial verification,update,and revocation operations are also on-chain.Some works extend similar ideas and construct new identity blockchains,which are specifically designed for managing identities on other blockchains[34–36].

▼Table 1.Attacks and countermeasures on edge blockchain components
3.1.2 Supply Chain Attack
In practice,blockchain nodes are implemented by blockchain client software like Geth[32]and Bitcoin Core[37].These blockchain clients are developed or orchestrated from multiple libraries,packages,and dependencies,providing consensus,blockchain data storage,APIs,wallet functionalities,etc.Due to the nature of decentralization and trust concerns,their blockchain components are usually supplied by open-source projects.For example,Geth involves Web3.js library to provide APIs for blockchain,and smart contract interactions[38].
A supply chain attack (e.g.,a third-party attack,a valuechain attack,or a backdoor breach) aims to inject malware or malicious hardware by hiding in upstream supplied system components to damage software.Historic attacks were mainly launched by suppliers in traditional information and communications (ICT) technology areas.However,recent accidents show that it can also affect blockchain since blockchain projects are mostly built by open-source dependencies to increase transparency.As shown in Fig.3,attackers may upload predesigned malicious libraries and packages to open-source repositories by compromising blockchain managers,and then deliver them to blockchain software developers.Users will be compromised when they run crafted blockchain software like wallets[39].Likewise,there is so-called mining malware that pretends to be normal browser plugins,executable programs,and miner tools,stealing the computation power of devices to obtain benefits[40].In edge blockchains,such attacks are noteworthy since the blockchain clients running on edge devices are provided and maintained in a similar way.Even worse,edge blockchain networks are dynamic,and edge devices frequently join and leave the networks by installing the blockchain client software from different sources.These processes expose additional attack interfaces for supply chain attacks.
The preventive solutions try to eliminate the risks from both the upstream components supplier side and the device side[41–43].On the one hand,researchers and developer communities use various security mechanisms to assert the projects hosted in open-source repositories.Many scoring and threat detection and analysis systems like OpenSSF Metrics and OpenSSF Scorecard are built to provide an overview of the security status for developer reference[44–45].They calculate the scores according to the code maintenance status,vulnerability existence,and programming specification as metrics.On the other hand,the automated code analysis project,and services for detecting blockchain software and smart contracts are emerging[46–48].They can check sensitive codes and functions like money transfer,deploying contracts,and making signatures by semantics formalization.This way is more active than the former but may bring huge additional development costs.

▲Figure 3.Supply chain attacks in blockchain: attackers can inject malicious scripts into libraries and packages to damage blockchain networks
3.2 Blockchain Consensus
Consensus is a core component of blockchain systems that refers to the continuous agreement protocol on blocks/transactions among multiple blockchain nodes.Blockchain consensus can reach an agreement and update node states under the existence of Byzantine nodes.Byzantine nodes can behave arbitrarily to achieve malicious targets except by breaking cryptography primitives,and they can also cooperate.For example,Byzantine nodes can keep silent to pretend to crash or corporately send fake messages to foolish honest nodes.Currently,there are mainly two types of blockchain consensus: the Nakamoto style and the traditional BFT style.Nakamoto style consensus includes Proof of Work (PoW),Proof of Stake (PoS),Proof of Authority(PoA)[37,49,32],etc,which rely on external validity rules like mining power,stocks,and authority to reach agreements.BFT style consensus purely concerns the votes on broadcasted values,like practical Byzantine fault tolerance(PBFT),HotStuff,and Honey badger[50–52].Besides,blockchain consensus is also highly related to hardware,blockchain data structure,networking algorithms,and blockchain lightweight client design[53–54].
Consensus is a vulnerable component due to the complexity and non-deterministic procedures.Existing attacks focus on breaking two consensus features as follows:
·Consistency (safety): If any two honest nodes in the blockchain network maintain two blockchains,they should be on the same chain.
·Liveness: If the honest nodes receive a transaction,the transaction should be included in all blockchains maintained by honest nodes after the consensus procedure.
Literally speaking,if the attack breaks consistency,there will be unexpected blockchain forks or double spending events.If the attack breaks liveness,the consensus will halt and no agreement has been reached for incoming transactions.
3.2.1 Sharding-Based Consensus Attack
In edge blockchain networks,the numerous edge devices require the blockchain consensus to be scalable to maintain high Transaction per Second (TPS).However,the theoretical limitations make the communication complexity hard to be subquadratic (BFT style consensus).Sharding is a celebrated and preferred technique to deal with scalability issues in edge computing[55–57].Generally speaking,sharding splits the blockchain networks into several pieces,where each piece individually deals with transaction consensus and data storage.This way can reduce the communication to nearly linear as well as the storage cost[58–59].
However,in practice,the transaction may be related to multiple shards,which brings extra security issues.For example,in the unspent transaction output (UTXO) model,the outputs of a transaction must be equal to (or smaller than) its input.If the inputs come from different shards,nodes in one shard cannot verify the validity of this transaction for they have no knowledge of other shards.In the account/balance model,the transaction is still probably from different shards when the shard number increases.Thus,a cross-shard consensus protocol as the coordinator is needed to deal with this situation.The typical solution is using the atomic commit (AC) protocol to implement this coordinator.However,existing works show that existing coordinators are vulnerable to various attacks,including transaction forging attacks,message withholding attacks,publish-revert attacks,and replay attacks,which can break the liveness and safety of sharding-based consensus[60–61].Generally speaking,these attacks leverage the knowledge difference and message delay during the AC process,further cheating or isolating the honest shard chains.
Another fundamental security issue of sharding-based consensus is committee selection for shard formation.Traditional blockchain consensus assumes that the number of Byzantine nodes is under a certain percentage (security boundary),e.g.,50% for PoW and 33% for PBFT.When the blockchain network is splitted into reveal shards,the number of Byzantine nodes may exceed security boundaries in particular single shards.This issue is also called a signal shard takeover attack.For example,a blockchain network runs PBFT with seven nodes,where five nodes are honest and two nodes are Byzantine.If the network manager randomly selects committees in shards as shown in Fig.4,the second shard will be compromised since there are more than 33% Byzantine nodes.This situation comes from the uncertainty of Byzantine nodes,making managers hard to decide which node is honest.

▲Figure 4.Signal shard takeover attack: shard may contain exceeded numbers of Byzantine nodes after committee selection
For the first security issue,researchers try to design new AC protocols that have extra features like termination.It requires all involved shards on a cross-shard transaction to eventually decide on it.Besides,in real implementation,a “garbage collection” is used for dealing with uncompleted crossshard transactions[62–63].However,such works are specific to their blockchain systems,and cannot be directly applied to other blockchains.Traditional non-blocking atomic commit(NC-AC) is also needed to be significantly modified to be compatible with the blockchain system[64].For the second security issue,the public verifiable randomness sources and countermeasures for active adversaries are introduced.The randomness sources provide the reference for shard formation.Being unpredictable and uniform can minimize the probability of selecting excessive Byzantine nodes in shards[59].For active adversaries,which corrupt nodes after shard formation,there are also mechanisms to limit their abilities of malicious voting[65].
3.2.2 DDoS on Memory Pool
A memory pool in a blockchain system is a caching area for receiving,verifying,and ranking incoming transactions before consensus.The memory pool is the first step for processing transactions.Thus its performance will be the bottleneck of TPS.For example,in Bitcoin,the miner first checks the validity of transactions in terms of signatures,UTXOs,formats,etc.Then the transactions will be put in a memory pool waiting to be mined into blocks[37].The ranking of transactions depends on the mining fee attached to the transactions.High mining fees stimulate miners to mine transactions in a high rank,making them early confirmed.Besides,the relay fees are also required for miners relaying the transactions to each other.Other blockchain systems are designed with similar philosophies.The differences lay in the requirement for fees.In edge blockchains,the fees are omitted and the ranking is decided by the arriving time or other parameters[66–68].
Recent studies show that the DDoS attack can significantly affect the memory pool,prohibiting normal transactions from being confirmed[69–72].Attackers first allocate multiple Sybil accounts with enough balances for paying transaction fees and relay fees.Then they initiate a large number of unconfirmed transactions that transfer money to each other to several blockchain nodes in a short time period.When the transaction arrival rate is larger than the confirmation rate of blockchain consensus,there will be a transaction backlog,and the blockchain nodes have to increase the size of memory pools eventually.Although the consensus processes as normal,the actual TPS for normal transactions will be decreased.Attackers try to maximize the number of these transactions in the memory pool but do not want them to be confirmed since it will cost more fees.Therefore,these transactions typically only have relay fees to reduce the attack costs.In edge blockchains,conducting such attacks is more possible than doing this in cryptocurrency.The reasons include that the transactions in edge blockchains are application-specific and may not need to pay money,and the corrupted edge devices can easily generate a large number of transactions.
Existing solutions focus on increasing the costs of launching such attacks to further prevent them from happening.Researchers set additional constraints to filter the transactions that are likely to be malicious.The constraints consider whether the parents transactions are confirmed previously and therefore pay mining fees[69–72],or set the relay fees dynamically increasing when the memory pool size is too large[70].These solutions only care about cryptocurrency systems,but such mechanisms may not be feasible in edge blockchain networks.
3.2.3 Insecure Computation Offloading
Computation offloading is a unique technique in edge computing.It transfers resource-intensive computational tasks to other nearby devices by dividing and optimizing tasks.In this way,resource-constrained devices reduce the burden and are capable of dealing with complex tasks.Computation offloading is extensively studied and applied in edge computing,and many edge applications essentially rely on it,such as distributed machine learning,video surveillance,and VR/AR[73–75].In edge blockchains,offloading is also utilized for reducing the blockchain consensus costs on mobile devices[76–77,13].Researchers model the consensus tasks and edge compute services pricing as Stackelberg games to improve the system throughput and optimize the accessibility of the blockchain network.
However,such offloading methods cannot well meet the security requirements of blockchain.Even though the consensus tolerates a certain percentage of Byzantine nodes,malicious edge computing service providers (e.g.,corrupted edge servers) are still possible to break the threshold.Specifically,malicious providers can execute other nodes’ consensus tasks and act like them simultaneously.This behavior is equivalent to corrupting honest nodes in the blockchain since malicious providers obtain free computation power paid by honest nodes,which is definitely out of the BFT model definition.Consequently,the percentage of Byzantine nodes in blockchain networks will increase and finally become overwhelming.
Secure multiparty computation (SMPC) and outsourced computing can be promising solutions to addressing these issues.SMPC is a cryptographic technique that enables multiple parties to jointly compute tasks without revealing their own private inputs and outputs[78].With the development advancing,its efficiency is becoming acceptable for edge and IoT devices.Combining the SMPC with blockchain and offloading can prevent malicious computing service providers from manipulating outsourced blockchain tasks[79].
3.3 Blockchain Lightweight Client
Blockchain lightweight client is another critical building block of a blockchain system,especially for developing edge blockchains.It contains transaction generation,query,and verification schemes with blockchain data bootstrapping and synchronization procedures.In practice,a blockchain lightweight client typically does not directly participate in consensus like blockchain full nodes do to save computation,storage,and networking resources.Therefore,a blockchain lightweight client is suitable to be integrated into mobile applications and run on resource-constrained devices in edge networks[80,12,81].Specifically,a lightweight client contains the following functionalities[82]:
·Bootstrapping and synchronization: Given a blockchain genesis block or file,the client should synchronize all the state metadata from full nodes (e.g.,all block headers) with bootstrapping proofs.When the full nodes update their states(e.g.,new blocks),the client should also synchronize it and update state metadata with synchronization proofs.
·Transaction generation,query,and verification: Clients should generate valid transactions for full node updating its states.After that,a client can query the existence of submitted transactions confirmed in blockchain states and verify the result proofs.
Bitcoin simplified payment verification (SPV) is believed to be the first implementation of a lightweight client[37].As shown in Fig.5,it only stores the block headers of the longest chain locally,which is initially downloaded and periodically synchronized from nearby full nodes.Upon receiving transaction verification requests,lightweight clients retrieve the blocks that contain the transactions with corresponding Merkle branches for verifying their existence.
3.3.1 Key Compromise
Key management refers to the schemes of generating,updating,using,and deleting cryptographic keys.In the blockchain context,the keys are employed for identifying edge nodes,signing transactions,and encrypting data.Due to the decentralized nature,such keys are usually kept by the user sides,and no managers are responsible for them.In well-established blockchain wallets like MetaMask[83],the key files are stored locally with mnemonic phrase encoding and password/biometric authentication protection.Users need to input the correct password or biometric information to unlock the key inside the wallet to sign transactions.

▲Figure 5.Bitcoin simplified payment verification (SPV): a lightweight blockchain client for Bitcoin,which only stores the block headers to reduce costs
Although many elaborately crafted key management schemes are designed and implemented for high security and usability,the keys are still extremely vulnerable to software bugs,hardware failure,and even simple human errors[84–85].Key compromise is still a significant security issue that remains unsolved.To add insult to injury,these issues are more likely to happen in edge blockchains since edge devices (like IoT devices) are mostly low-end in hardware and software with few sufficient security mechanism.Besides,the devices are also physically accessible and controllable.Attackers can attack the devices through various interfaces existing on edge devices and applications.As a result,the keys managed in edge devices are highly risky of being theft,lost,and broken.
Existing efforts to enhance the security and usability of blockchain key management are twofold.First,from the blockchain side,many schemes are proposed to replace or supplement the transaction verification in blockchains to realize key compromise protection[86–89].The general idea is to allow new operations to claim new keys or recall transactions for users who are theft or lose their keys accidentally.This way serves as remedial measures for unlucky users but creates additional difficulties and lowers the blockchain TPS for normal users.From the device side,advanced cryptography primitives are applied to minimize the risk of key compromise.Group signature,threshold signature,and hierarchical key derivation are used to construct robust key management schemes[90–92].These schemes can provide additional rescue solutions,present informative network typology,and set flexible access control in edge blockchain key management.
3.3.2 Malicious Full Node Attack
The purpose of a malicious full node is to influence light nodes that interact with the blockchain network via a light protocol and inject adversarial blocks.Light clients have poor bandwidth and limited storage capacity.To improve the efficiency of light clients,firstly,they do not store complete ledger information;secondly,they generally verify the validity of the chain within a limited scope.For example,in SPV,light clients validate the chain only through block headers and request Merkle from full nodes on demand to verify that a specific transaction is valid.Incomplete validation makes it possible for malicious full nodes to inject adversary chains into light clients.
Malicious full nodes can create forks in the blockchain.A fork consists of blocks with block headers that satisfy block header validation and adversarial status.Honest full nodes will immediately reject these adversary blocks because they fail in state validation.However,since light clients can only perform header validation,but not state validation,the fork is also a normal chain from the perspective of light clients.If the adversary chain contains more work than the honest chain,according to the longest chain rule,a light client will accept the adversary chain.In addition,a patient adversary willing to wait (days or months) can obtain a high probability of successfully injecting a forged state into a light client.Considering a node,such as an IoT node with a limited battery,is operating in a duty cycle mode and periodically active,the longer the interval between two active states,the higher the adversary probability of successful state injection.Moreover,the adversary also has the probability of having a successful adversarial chain at any random point in time,so it may also successfully convince a light node[93].
Existing solutions focus on building reputation systems and using game-theoretic approaches to secure the light client from malicious full nodes.In reputation systems,miners are ranked by their consensus contribution[94].Light clients cache the recent blocks from miners with good reputations to securely download blockchain data.Game-theoretic approaches use smart contracts as a trusted arbiter to deal with the client and a set of full nodes[95].Participants need to deposit some funds on the arbiter contract as collateral.Malicious behaviors like sending fake blocks will be plenty by costing the deposited funds,thus encouraging the full node to provide block data honestly.
4 Future Research Directions
In this section,we point out some specific future research directions that are related to the security of edge blockchains.We envision these directions being significant in future edge blockchains.
4.1 Modular Blockchain Framework
Existing frameworks in edge blockchains only support one or multiple fixed components such as consensus algorithms,databases,and communication protocols.This fact significantly decreases the resistance to supply chain attacks and amplifies the attack revenue.Imagine if some widely used consensus algorithms or other components are suddenly found vulnerable,all the blockchain systems with those components will be risky and hard to be fixed in a short time.This is because the interfaces,data structures,and algorithms among these components are highly coherent.Developers do not have much flexibility to adjust them when security issues occur.Besides,the valuable on-chain assets and data make blockchain systems hard to be readily updated as normal software.
In our previous work,PolyChain proposes a modular blockchain framework,where the main components are fully pluggable and changeable[96].We divide the blockchain into four components: application component,consensus component,storage component,and network component.This provides much flexibility when facing attacks.In PolyChain,developers can replace vulnerable components with low costs to avoid potential damage.Other works with similar philosophy also emerged recently,and better solutions to blockchain modularization remain to be explored[97–98].
4.2 Ordered Blockchain Consensus
Some transactions have inherent relationships and dependencies in certain applications.For example,in Decentralized Finance (DeFi) and Central Bank Digital Currencies (CBDC)[99–100],manipulating transaction confirmation orders can launch financial attacks on smart contracts[101].This is because when users need to submit a batch of transactions to these applications,their exact confirmation order is not guaranteed in most existing consensus algorithms.Miners usually include transactions in blocks according to the attached fees.Many blockchain financial infrastructures are also deployed in edge environments,such as Bitcoin ATMs and cryptocurrency wallets.Therefore,we need to guarantee the security of transaction confirmation orders in edge blockchains.
One easy and safe way is submitting transactions to consensus one by one and waiting for confirmation,but this is inefficient when there are a large number of pending transactions.New efforts on consensus need to provide security guarantees on transaction orders while keeping high efficiency.This is challenging since it basically requires designing extra consensus rounds expressly agreeing on transaction orders.
4.3 Blockchain Secure Live Migration
In edge blockchains,multiple small-size blockchain networks may exist for specific user groups and applications.However,accessing these size-constrained blockchains can be difficult for they are only deployed in a limited number of edge devices with poor network connectivity.Simply scaling the blockchain network by setting up new nodes is a naive solution,but this will occupy other device computing resources and interrupt blockchain consensus,causing further security concerns for the blockchain network,like congestion.
Live migration is a technique that transfers services or processes across computing infrastructures without disrupting normal operations.It has been extensively studied in cloud computing for load balancing,resource management,server consolidation,predictive maintenance,and QoS improvement[102].Such a technique is also beneficial to edge blockchains.It can reduce the latency of accessing the abovementioned size-constrained blockchain with low costs and high QoS.Existing migration techniques only focus on container or process architecture,which may not perform well on blockchain since they do not consider the specific architecture of blockchain systems.More effective and secure solutions can be adopted by separately migrating different components of the blockchain system,such as blockchain data and memory pool transactions while keeping consensus running for security[103].
5 Conclusions
Integrating blockchain with edge computing is a valuable landscape in future wireless communication.Many efforts have been made to make blockchain securely run in adversarial environment.However,the features of edge computing bring new security issues,which have not been extensively studied and addressed in previous literature.Many attacks on edge blockchains components are not well understood and prevented.Through this study,we comprehensively review the security of edge blockchains in terms of attacks,countermeasures,and future directions.We envision this survey acting as a security guideline for designing and developing edge blockchains.
- ZTE Communications的其它文章
- Editorial: Special Topic on Wireless Communication and Its Security:Challenges and Solutions
- Utility-Improved Key-Value Data Collection with Local Differential Privacy for Mobile Devices
- Key Intrinsic Security Technologies in 6G Networks
- Air-Ground Integrated Low-Energy Federated Learning for Secure 6G Communications
- Autonomous Network TechnologyInnovation in Digital and Intelligent Era
- Distributed Multi-Cell Multi-User MISO Downlink Beamforming via DeepReinforcement Learning

