Cascading attack on trusted-relay quantum key distribution networks
Jian Wang and Xing-tong Liu
College of Electronic Science and Technology,National University of Defense Technology,Changsha,410073,China
Abstract Trusted relays are the main state-of-the-art way to realize quantum key distribution networks.However,it is hard to require that all nodes in the network are fully trusted.In a multipath keytransmission mechanism,the nodes can be weakly trusted because the secret key can be split into many parts and each part is transmitted to the receiver through a different path.However,if the capacity of a node’s quantum key pool is poorly designed,an attacker,Eve may eavesdrop on the communicating parties’secret message by initiating a redirection attack.In this paper,we show that Eve can trigger a cascading collapse effect by collapsing one of the edges in the network and forcing the communication parties to transmit the message through the nodes controlled by Eve.The influence of the traffic transfer ratio and the control parameters of the edge load on the breakdown probability of the edge are analyzed using a simulation.In order to effectively defend against the cascading attack,it is important for the designer to handle the relationship between the traffic and the capacity of the quantum key pool of each node in the network.
Keywords:Quantum key distribution,Quantum key distribution networks,Quantum communications
1.Introduction
Quantum key distribution(QKD),which provides a way for two legitimate parties to share a secret key[1],has been one of the most remarkable applications of quantum mechanics in quantum information science.Following key distribution,the parties can use a one-time pad to protect the secrecy of their transmitted messages.Point-to-point QKD systems focus on the communication between two endpoints,which is limited by the transmission distance.In order to provide an end-toend service for QKD users,QKD networks have been developed by many countries and regions.Typical QKD networks include optical switching QKD networks[2–5],entanglement swapping QKD networks[6],measurementdevice-independent(MDI)QKD networks[7,8]and trustedrelay QKD networks[9–11].QKD networks based on optical switching are easy to realize,but their transmission distance is limited by the losses caused by the optical nodes.QKD networks based on entanglement swapping cannot be practically used so far,because some significant technologies such as quantum memory and non-destructive measurement still need further breakthroughs.MDI-QKD networks are powerful candidates for future QKD networks,because they allow an untrusted third party to make measurements and the relay nodes in the network do not have to be trusted.However,there are currently some limitations in MDI-QKD networks,for example,all users are required to have near-identical distances to the untrusted relay,and the key rate degrades very quickly with an increased level of asymmetry between channels[8].Compared with entanglement swapping QKD networks and MDI-QKD networks,trusted-relay QKD networks are more practical and natural,given the current state of the art,and have been used as a standard for existing QKD networks.
In 2002,Elliott proposed the idea of using trusted nodes for QKD networks based on the point-to-point QKD system and the hop-by-hop encryption method[9].In 2008,by unifying the efforts of 41 research and industrial organizations,the Secure Communication based on Quantum Cryptography(SECOQC)network was established in Vienna with a focus on the trusted repeater paradigm[10].In 2010,Japan built a QKD network in Tokyo by integrating six different QKD systems into a mesh-type network[11].In 2017,the world’s first wide-area QKD network—the‘Beijing-Shanghai trunk line’opened,which also uses key-trusted repeaters to generate end-to-end keys.In the same year,China launched a low-Earth-orbit quantum satellite in order to establish a global-scale quantum network[12].In 2021,Chen et al demonstrated an integrated space-to-ground quantum communication network;the large-scale fiber network covers more than 2000 kilometres on the ground using a trustedrelay structure[13].Because software-defined networking(SDN)decouples the control plane from the data plane and then provides flexibility and programmability together with the centralized management of optical resources,QKD networks enabled by SDN have attracted more and more research attention.A QKD-enabled optical network architecture and some software-defined optical network keyassignment schemes have been proposed in recent years[14–16].
Trusted relays are a feasible method for building largescale QKD networks.However,trusted-relay QKD networks require each node to be fully trusted.If one of the relay nodes is compromised,the whole network is insecure.In trustedrelay QKD networks,each node constructs a quantum key pool(QKP)to allocate and manage its quantum keys.If the number of nodes in the network is relatively small,the nodes can be well protected and the security of the trusted-relay QKD network can be guaranteed.However,in the case of large-scale networks,it is difficult to ensure that every node is trusted.It is generally agreed that for large-scale QKD networks,each node can only be regarded as weakly trusted,and that a multipath key-transmission mechanism should be used to ensure the security of the network[17–21].Wen et al proposed a multiple stochastic path scheme to improve the security of partially-trusted relay QKD networks[17].Yang et al presented a dynamic routing scheme for trusted-relay QKD networks which can dynamically select a set of suitable paths to establish the routing table for key exchange[18].Ma et al proposed a multiple-path key distribution scheme with labels for QKD networks to avoid loops and public nodes in the routing[19].Xu et al designed a multipath key-transmission scheme based on link cost and a multipath selection algorithm to improve the security and efficiency of key transmission[21].
In this paper,we show that although the QKD network model can be changed from the trusted-relay model to the weakly trusted-relay model by using the multipath keytransmission mechanism,Eve’s attack may cause a cascading effect if the QKP size of each node in the network is not well designed,which makes many links in the local area of the network unusable.The communication parties may choose another link to transmit their secret message and a node in this link may be controlled by Eve.Eve may access the secret message of the communication parties.In this paper,we use classical complex network theory to describe the construction of a cascading attack model that can be employed against a QKD network.The relationships between the parameters such as the breakdown probability,the traffic transfer ratio and the load limitation are analyzed and a strategy for defending against the cascading attack is proposed.
2.Vulnerability of trusted-relay QKD networks
The basic idea of trusted-relay QKD networks is to divide the whole long-distance quantum communication link into several segments.Each segment is connected by trusted-relay nodes,and each node shares a secret key with its neighboring node;the communication parties,Alice and Bob,can share a common key through the trusted-relay nodes.As illustrated in figure 1,Alice shares k1 with a trusted-relay node R1.R1 shares k2 with R2 and sendsk1⊕k2to R2.R2 obtains k1 by calculatingk2⊕k1⊕k2and sendsk1⊕k3to Bob.Bob shares k3 with R2 and obtains k1 usingk3⊕k1⊕k3.Thus,Alice shares k1 with Bob through the trusted-relay nodes R1 and R2.It is obvious that R1 and R2 should be fully trusted.If any relay node is captured by Eve,the shared key is not secure.
In the weakly trusted multipath key-transmission scheme,we suppose that a node is not fully trusted and can only be trusted by Alice and Bob with a probability of 1-t.Thus,Eve can controlnodes if there are N nodes in the network.We now suppose that there are l paths between Alice and Bob and that each pair of paths has no intersection.The sender,Alice splits the secret message m into l shares,and sends them to Bob through l paths,respectively.After Bob receives all l parts,he can recover the secret message m.As long asl>,Eve cannot obtain the secret message shared by Alice and Bob.It can be seen that as the number of available paths increases,the probability of Alice and Bob exchanging a security key also increases.Rass et al showed that Eve may indirectly eavesdrop on the key by initiating a redirection attack[22].In the redirection attack,Eve continues to consume Alice’s key by pretending to be a legitimate node and continuing to communicate with Alice.When there is no key available in Alice’s QKP,her packets are forwarded through other nodes,and if the node is controlled by Eve,Eve can acquire Alice’s packets through a redirection attack,even though she cannot get Alice’s key directly.
We further show that Eve’s attack may cause a cascading effect if the size of the QKP is not well designed.As illustrated in figure 2,suppose that node 4 is controlled by Eve,and Alice is most likely to communicate with Bob through nodes 1 or 2,according to the principle of shortest path priority.In order to eavesdrop on Alice’s secret message,Eve pretends to communicate with Alice through node 1 and consumes the key pair of Alice and node 1.In this way,if Alice wants to communicate with Bob and there are no key pairs belonging to Alice and node 1 left in her QKP,Alice may send her message through node 4 and Eve has the opportunity to acquire Alice’s secret because node 4 has been captured by Eve.This is an intuitive example of a redirection attack.In the cascading attack,Eve communicates with Alice through node 1 and consumes Alice and node 1's key pairs.If there are no key pairs belonging to Alice and node 1 left,node 1 will contact Alice through node 2 and the key pairs of Alice and node 2 are also consumed.Finally,if there are not enough key pairs belonging to Alice and node 2,Alice can only communicate with Bob through node 4,and Eve then obtains the shared key of Alice and Bob.
In classical networks,cascading collapse often occurs,especially for complex networks,which may cause paralysis of the local network,greatly affecting the efficiency of the network.For QKD networks,the greatest damage caused by a cascading attack is a decrease in network security,because it directly reduces the available paths in the network and the security of the multipath key-transmission mechanism is closely related to the number of paths.
3.A model for a cascading attack on a trusted-relay QKD network
A QKD network is a combination of a quantum network and a classical network.It uses a one-time pad to encrypt data and the length of the ciphertext is the same as that of the plaintext,so the data traffic characteristics of a QKD network are similar to those of classical networks.The theory of classical complex networks can be used to analyze cascading collapse in a QKD network.The Barabái-Albert(BA)model is an algorithm which generates a scale-free network by incorporating growth and preferential attachment.We use the BA model to describe the topology of the QKD network[23].
For any two adjacent nodes,i and j,in the network,kiand kjrepresent the degrees of nodes i and j,respectively,where degree means the number of connections a node has.Let eijdenote the edge of nodes i and j.According to the BA model,the greater the degree of a node,the more nodes are connected to it,and the more important it is to the whole network.It is assumed that the initial load of eijisLij=(k i kj)α,whereα>0 is a tunable parameter that controls the size of the edge load[24].The edge load is related to the degrees of the two nodes connected to it.The greater the degrees of the nodes,the greater the load at the edge,indicating that the flow through the edge is larger.If the edge eijcollapses,its initial load is transferred to the adjacent edges and the additional load received by an adjacent edge is proportional to its initial load.We useΔLimto denote the increased load of edge eimafter edge eijcrashes,

whereΓiandΓjrepresent the sets of neighboring nodes of node i and node j,respectively,and ρ denotes the proportion of traffic transferred.We assume that the capacity Cijof edge eijis proportional to its initial load forCij=βLij,where β is a tolerance parameter,β≥1.
According to the protection mechanism of the SECOQC network against a denial-of-service attack,when the remaining key of the shared QKP is lower than a certain threshold C,the two sides no longer adopt the one-time pad encryption method,but use a hybrid encryption method to slow down the rate of consumption of QKP keys.Finally,when all the keys in the QKP are consumed,the communication between the two parties stops.Based on this mechanism,we set a control parameterγ≤1 and letC=γCij.When the actual load of edge eijis lower than the threshold C,the edge can communicate normally and does not crash.When the actual load of edge eijis higher than the threshold C,the QKD network adopts the hybrid encryption method and the key consumption rate decelerates,but the key may be exhausted at any time.In this case,in order to ensure that more traffic can be encrypted using the one-time pad encryption method,part of the load of edge eijis transferred to other adjacent edges.The breakdown probabilityP(eij)of edge eijcan be written as

This means that if the load of edge eij,Lijis lower thanγCij,eijdoes not crash.If Lijis greater than C,eijtransfers trafficρ*Lijto its adjacent edges.If the remaining traffic passing through eijis greater than Cij,eijcrashes with a probability of 1.
In order to observe the effects of the cascading attack,we built a simulation of a BA network where the number of nodes n=3000 and the initial number of edges M0=2.In the simulation,we setα=1.1,and chose 50 random nodes to attack each time.We calculated the average breakdown probability,E(P(eij))of triggering a cascading effect after the attack by setting different values of γ,ρ and β.Figures 3 and 4 show the relationship betweenE(P(eij))and β for different values of γ and ρ,respectively.According to the simulation results,it is obvious that the smaller the value of β,the easier Eve can trigger the cascading collapse effect.Otherwise,the higher the value of β,the more difficult it is to trigger the cascading collapse effect.In particular,when β reaches a certain level,Eve can hardly trigger the cascading collapse effect.It can be seen that the greater the value of γ,the bigger the probability of breakdown of the edge.The simulation breakdown probability of the adjacent edge eimis lower than p,that is
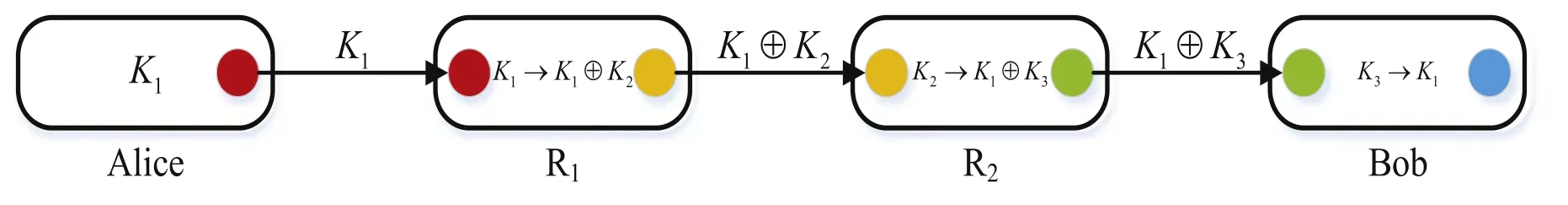
Figure 1.The structure of a trusted-relay QKD network.

Figure 2.Attack on a trusted-relay QKD network.

Figure 3.Influence of γ on E(P(eij))in the simulation of a cascading attack on a QKD network.

Figure 4.Influence of ρ onE(P(eij))in the simulation of a cascading attack on a QKD network.

By substituting Lim,ΔLim,Ciminto the above formula,we obtain

results are consistent with the actual situation.If the value of γ is relatively small,the threshold C is small and once the load exceeds the threshold,the traffic is transferred to other edges,meaning that the value ofE(P(eij))is large.As shown in figure 4,the greater the value of ρ,the smaller the value ofE(P(eij)).It is obvious that if the traffic transfer ratio is relatively large,the remaining load on eijis small and the breakdown probability of eijis also small.
4.Defense strategy against cascading attacks on trusted-relay QKD networks
In a cascading attack,Eve aims to trigger the successive collapse of other edges by using the traffic transfer that is triggered when one edge crashes.In order to prevent cascading attacks on trusted-relay QKD networks,it is necessary to arrange the a suitable payload limitation for each edge in the network.When edge eijcollapses,we expect that the which can be written as



As described above,if we want to reduce the breakdown probability,the value of β should be increased.Supposing the breakdown probability of eim,p=0,then we have

According to this formula,we can reduce the requirement for β by increasing the value of γ.At the same time,we can increase the value of ρ and transfer more payload to other paths.We can then obtain a suitable value for β by adjusting the parameters ρ and γ in order to defend against the cascading attack on the QKD network.
5.Conclusion
In this paper,we analyzed the security of the trusted-relay QKD network.It was shown that although the nodes in the network were not necessarily fully trusted in the case of the multipath key-transmission mechanism,the QKD network was vulnerable to a redirection attack.We further showed that Eve’s attack was able to cause a cascade effect and that it was possible for Eve to obtain the communicating parties’secret message by forcing the communication parties to transmit their messages through a node controlled by Eve.We built a model of the cascade attack and used a simulation to analyze the influence of the transfer ratio ρ and the control parameter γ on the breakdown probability.We showed that it was necessary to set the value of β appropriately by increasing the values of γ and ρ,and that if the QKP capacity of each node is well designed,the cascading attack can be defeated satisfactorily.Our findings will help to improve the security of trusted-relay QKD networks.
ORCID iDs
 Communications in Theoretical Physics2021年6期
Communications in Theoretical Physics2021年6期
- Communications in Theoretical Physics的其它文章
- Intermediate symmetric construction oftransformation between anyon and Gentile statistics
- Proton radioactivity within the generalized liquid drop model with various versions of proximity potentials
- Joule–Thomson expansion of higher dimensional nonlinearly AdS black hole with power Maxwell invariant source
- Notch fatigue of Cu50Zr50 metallic glasses under cyclic loading:molecular dynamics simulations
- Eigen microstates and their evolutions in complex systems
- Non-similar mixed convection analysis for magnetic flow of second-grade nanofluid over a vertically stretching sheet
