Prototype of Multi-Identifier System Based on Voting Consensus
XING Kaixuan,LI Hui,YIN Feng,MA Huajun,HOU Hanxu,XU Huanle,Yunghsiang S.HAN,LIU Ji,and SUN Tao
(1.Shenzhen Graduate School,Peking University,Shenzhen,Guangdong 518055,China;2.School of Electrical Engineering and Intelligentization,Dongguan University of Technology,Dongguan,Guangdong 523808,China;3.The Network and Information Center of Shenzhen University Town,Shenzhen,Guangdong 518055,China)
Abstract:With the rapid development of the Internet,the expansion of identifiers and data brings a huge challenge to the network system.However,the network resources such as Domain Name System (DNS) are monopolized by a single agency which brings a potential threat to cyberspace.The existing network architecture cannot fundamentally solve the problems of resource monopoly and low performance.Based on the blockchain,this paper designs and implements a new Multi-Identifier System (MIS),providing the analysis and management for different identifiers in the multi-identifier network.Our preliminary emulation results prove the correctness and efficiency of the algorithm.Besides,the prototype system of MIS has been tested on the real operators’network,realizing the function of co-governing,security supervision and data protection.
Keywords:blockchain;multi-identifier;co-governing
1 Introduction
In nearly half a century,the Internet has experienced rapid development from simplicity to complexity.As the main carrier of cyberspace,the Internet plays a significant role in human life,social activity and even national security.However,serious problems such as resource exhaustion and poor business adaptability of the Internet network appear with the rapid development of big data and cloud computing.The semantic overload of IP address also reduces its scalability and mobility that further hinders security.In addition,under the existing system,the network resources such as Domain Name System (DNS) are monopolized by a single agency which brings a potential threat to cyberspace.Besides,malicious network users adopt a series of technical methods to hide individual IP address to escape the supervision and sanctions of the service provider.The content published by the malicious user is difficult to be discerned.These problems such as poor security and weak controllability under the traditional IP system need to be solved urgently.
To decentralize the management of the network architecture,blockchain [1] and other solutions [2]-[6] have recently been applied to build a future network realizing co-governing.Namecoin [7] and Blockstack [8] first applied blockchain to decentralize the management of the domain name system.However,in its underlying system based on public blockchain exists a bottleneck for its performance.To solve the problem,BENSHOOF et al.proposed an alternative solution of the DNS system based on blockchain and a distributed hash table named 3[9],which provides solutions to current DNS vulnerabilities such as Distributed Denial of Service (DDoS) attacks.However,it risks leaking users’IP information and increases the difficulty of large-scale deployment.To mitigate the problem,the HyperPubSub system [10] uses the passive publish/subscribe receiving mode to reduce the traffic load and the delay caused by blockchain.
The above methods improve the performance of network and level of decentralization,respectively,but are unable to meet requirements [11] simultaneously.Our preliminary work proposed a new architecture:Multi-Identifier Network (MIN)[12] that constructs a network layer with parallel coexistence of multi-identifiers,including identity,content,geographic information and IP address.To solve the two major defects of the traditional network,we decentralize the identifier management by using consortium blockchain.This paper proposes a voting consensual-based multi-identifier management system Multi-Identifier System (MIS).MIS is a decentralized system composed of software and servers providing unified identifiers registration generation,classification,storage and management for identity,content,IP and other identifier spaces through the consortium blockchain Proof of Vote (PoV) [13].Moreover,the MIS implements the digital signature to enhance security supervision and data protection.
The following chapter structures as follows.Section 2 introduces the MIN architecture.Section 3 describes the management system MIS and key technologies.Section 4 describes and analyzes the system flow of MIS,Section 5 shows the function realization and simulated verification of the prototype system,and Section 6 provides some concluding remarks and discusses ongoing and future research directions.
2 Architecture
2.1 Overview of Multi-Identifier Network
For the co-governing MIN,its decentralized management and large resolution capability enables a progressive transition from the existing network architecture to a new one.
MIN supports the coexistence of network identifiers including identity,content,geographic information and IP address.Identifiers in the network are identity-centric.All the resources are bound to the identity of their publishers.The architecture of MIN is shown in Fig.1.
Fig.2 shows the network hierarchy of MIN.It divides the whole network into hierarchical domains from top to bottom.The nodes in the top-level domain belong to the organizations of the major countries maintaining a consortium blockchain.The respective regional organizations govern the other domains.Among them,the registration and management mode of identifiers and the specific implementation details can vary.This low coupling guarantees the security of the network and enables the customization of each domain[13],[14].
The functions of a completed node in the network participate in the intra-domain management of users and the registration process of identifiers on the blockchain,as well as provide inter-translation and resolution services.In addition,there are supervisory nodes,individual users and enterprise users.Supervisory nodes are set up as the data access interfaces between the upper and lower domains.Each supervisory node has multiple identifiers.
The architecture of MIN includes a management plane and a data plane.The management plane supports traceable data signing and checking mechanism.The data plane provides the resolution for identity,content,geographic information and other identifiers.In addition,the data plane is responsible for packet forwarding and filtering.The reason for storing only the important data on-chain is to ensure efficiency,while all the information of the identifiers is stored off-chain.
2.2 Overview of Multi-Identifier System
The MIS we proposed in this paper is responsible for the generation and management of identifiers in the management plane.All user and publication resources are required to register their identifiers with the supervisory nodes.The supervisory nodes verify the identifier and reach a consensus through the consensus algorithm.It records the relevant attribution information and operation information on the blockchain to make the data in the whole network unified,tamper-resistant and traceable.All resources are required to register an identifier with a regulatory organization within the domain.Users can only access a resource in the network when its identifier has been approved by most organizations and successfully written on the blockchain.Meanwhile,the MIS uses a digital signature scheme that has the advantages of autonomy,uniqueness,security and traceability.
1)Autonomy.
The registration of identifiers is based on decentralized blockchain technology.The user independently defines the application for registration prefix on the premise of legal nonrepetition.Besides,the registration and management rules are open,and there is no centralized control organization.
2)Uniqueness.
Real identity information such as biological information and ID number is registered to generate prefix to ensure uniqueness.Meanwhile,each user can use a prefix to identify the published resources,so that the users can identify and obtain the resource accurately.
3)Security and traceability.

▲Figure 1.The architecture of Multi-Identifier Network.
The prefix name must be registered and generated with real ID information to ensure that the identity of the content publisher is authentic and reliable.In addition,registration is successful only when an identity has been approved by most institutions and successfully written into the blockchain.Users who have successfully registered must use prefixes to publish content identification,and resource-publishing operations need to add user signature information.After receiving the request for publishing resources,blockchain verifies the user through signature to ensure that the resources published in the network space are safe and reliability.At the same time,the prefix name of content realizes network supervision by tracing resources to publishers.
MIS manages users’behaviors of publishing and access permission.The blockchain undeniably records illegal actions as well.Therefore,MIS keeps the cyberspace in an orderly and secure state that will direct Internet traffic to the post-IP multi-identifier network.
3 Key Technologies for MIS
3.1 High-Performance Consensus Algorithm
The MIS system realizes the unified management of identifiers based on the improved PoV consortium blockchain consensus [13],a non-forking consensus algorithm for consortium blockchain.The core lies in the separation of voting rights and butler rights.The butler nodes work in a joint effort to conduct decentralized arbitration according to the votes of the commissioner nodes.
The PoV consensus divides the blockchain nodes into four characters:the commissioner,butler,butler candidate,and ordinary user.Each node has its own public-private key pair and digital certificate based on its identity and account number.
1)Commissioner.

▲Figure 2.Multi-Identifier Network management architecture and operation flow.
The commissioners come from different regions or institutions maintaining a consortium blockchain together.Commissioners have the right to recommend,vote and evaluate the butlers.They also have the obligation to verify and forward blocks and transactions.A block generated in the blockchain network will be sent to all commissioners for verification.When a block receives at least 51% of the votes,the block will be marked as valid and be added to the blockchain.The result of the voting can represent the will of all the commissioners.
2)Butler.
The butler is responsible for generating blocks in the current consensus round.The number of butlers is limited.A butler gathers transaction information from the network,packs them into a block,and signs the block.At the end of the term,the commissioner votes on the butler candidate to produce the next butler nodes.Besides,a node can be a commissioner and a butler at the same time.
3)Butler candidate.
As the number of butlers is limited,a butler comes from butler candidates by election and all commissioners vote candidates.If a candidate is lost in the election,he can stay online and wait for the next election
4)Ordinary user.
Ordinary users are responsible for processing block distribution and message forwarding if not being authorized.They can join or exit the network anytime without being authorized and their behaviors can be arbitrary.
There are two types of message voting in PoV for the transactions of identifiers and election:verification vote and confidence vote.
1)Vote for block generation.
The butler processes transactions to generate a block then sends it to all commissioners.A commissioner will encrypt the block header and return the signature to the butler if it agrees to produce the block.
2)Vote for confidence.
In the last duty cycle of the term,the commissioner sends signed voting transactions to the butler.After collecting and counting the ballot tickets,the butler generates a special block with election results and related records.Then the butler sends this block to all the commissioners for validation
3.2 Privacy Protection and Identity Management Solution
There are effective solutions to privacy protection in blockchain,but it is unable to achieve effective management of the participating nodes’identity and tracking of their behaviors.This is unacceptable in the MIS where there is a need to manage the behavior of participants.
The MIS provides privacy protection by applying identity management.
Nodes in the domain can be divided into three characters:the ordinary node,butler node and commissioner node according to their different missions.One node can concurrently act as more than one characters (Fig.3).The ordinary nodes in green color have the right-to-know and the right-to-propose but cannot participate in the consensus process.The butler nodes own the rights to the generate blocks.The commissioner nodes have the right to verify the block; they can recommend,verify and evaluate the butler node and participate in consensus on the upper level.The commissioner nodes of the lower domain also act as a character in the upper domain.
A hierarchical group/ring signature mechanism is used in the MIS due to the different node division.The node signatures in the network form a tree structure,and each parent node regards a group of subordinate nodes as its leaf nodes.The superior signature is generated by the combination of the subordinate signatures.The superior signature contains all the subordinate signature information.The verification of the superior signature also includes the verification of the tree with the signature as the root.Similar to normal group/ring signature requirements,no third party can trace the identity of the signer who has produced the signature with obtained signature and verified the public key.In addition,the security of the hierarchical group signature scheme requires that the group administrator can only trace the signer’s leaf nodes’identity,while he/she cannot open the signatures generated by other groups’members.The group administrator of the parent node can quickly locate the problem group and identify the corresponding malicious users by establishing a group relationship between nodes of different levels and characters.
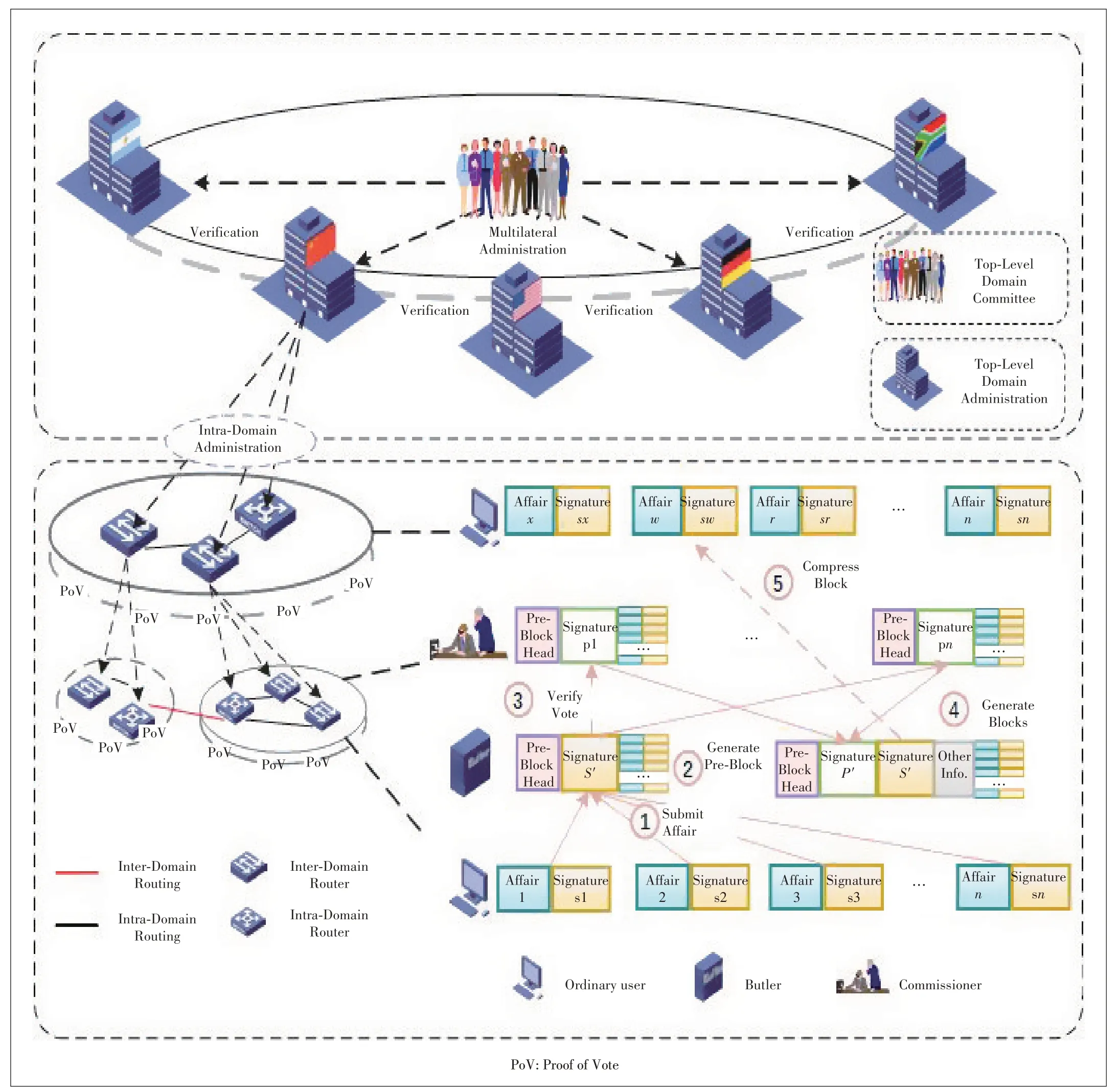
The following specific signature process is shown in Fig.4.
1) An ordinary node in the underlying domain produces a transaction and a signatureS.It also receives intra-domain transactions,verifies the correctness of the transaction content and signature,and forwards the transaction to other nodes in the domain if correct.The butler nodes listen on intra-domain transactions and place valid transactions into the transaction pool.
2) The butler nodes periodically take some transactions out of the transaction pool and then encapsulates them into preblocks.The pre-blocks group with the ordinary nodes it belonged to generate a new parent group signatureS'.S'and the pre-block are sent to all the commissioner nodes and other butler nodes in the domain.Once receiving the new parent group signatureS'and the pre-block,the other butler nodes save them.
3) After the commissioner node receives the pre-block,they verify the transaction and butler signature in the pre-block.If it agrees to the generation of this block,it sends back its relat-able ring signaturePand timestamp to the butler node.

▲Figure 3.Relationship among characters.
▲Figure 4.The specific signature processes.
4) Before the deadline of generating a block,if the number of the commissioners’signatures and time stamps that the butler has received is more than the default value,the butler will generate a new superior ring signature and add it to the head of the pre-block to generate a block.This block will be broadcasted to all domains with block body and signatureS'.Otherwise,if the number is no more than the default value or timeout,there will be no block generated in this consensus cycle.The default value can be set in different scenarios.
5) After receiving the block,the commissioner node verifies its signatureS'andP',and then removes the transaction contained in the valid block from the transaction pool.If the commissioner nodes are not in the top-level domain,extract the block as a transaction,generate a new superior group signatureS″ according to the attached butler signatureS',and submit the transaction as an ordinary node of the previous domain.The other superior nodes continue to verify the signature.Only if the block is in the top-level domain and the number of commissioner nodes is greater than the default value,it will enter the legal state and have the final confirmation.
According to the characteristics of the hierarchical signature scheme,the MIS uses different data structures for block and pre-block(Tables 1 and 2).
The multi-identifier management and privacy protection mechanism based on digital signature is the key technology to ensure the security and reliability of the transaction of the consortium chain.
4 Implementation of MIS
1)User registration.
Every blockchain node in the MIS runs a service thread that is used to process requests sent by clients and provide corresponding services.Fig.5 describes the full process of user registration including request reception,verification and user registration information saving on the blockchain.User registration involves the communication between clients and blockchain nodes by embedding the user registration into the consensus of blockchain.The commission nodes verify and reach consensus so as to achieve the co-governing function.
The main function of the user client is to generate a pair of public and private keys for the user according to his/her identity.The two keys will be bound and then uploaded to the blockchain.At the same time,the user who publishes the resource will apply for a content name prefix when registering,thus realizing the binding of content identifier and public key.The users who have successfully registered can publish resources using the content name prefix produced through registration.The resource publishing needs to add the user private key information.
When a new user registers for using the network,MIS will require the user to submit the information such as prefix and real identity shown in Table 3.According to different security requirements,MIS can dynamically adjust the biometric information recognition strategy.For now,the prototype achieves the function for collecting fingerprint,facial and human iris information.
In particular,the prefix information follows the naming rules for hierarchical network domains.In addition,the system creates a table as shown in Table 4 to store the successfully registered user information on the blockchain.
MIS generates a certificate for users once it receives and saves such an application.Then user identity and prefix binding process are completed.All the resources published by,for example,Jason will be located in/Jason.The certificate con-tains the user information and will be located under/Jason/cer.Other users who request for/Jason resources will first verify the certification under the/Jason/cer to check whether legal or not.Besides,the user information determines the access permission so as to achieve specific management functions underlying different scenarios.
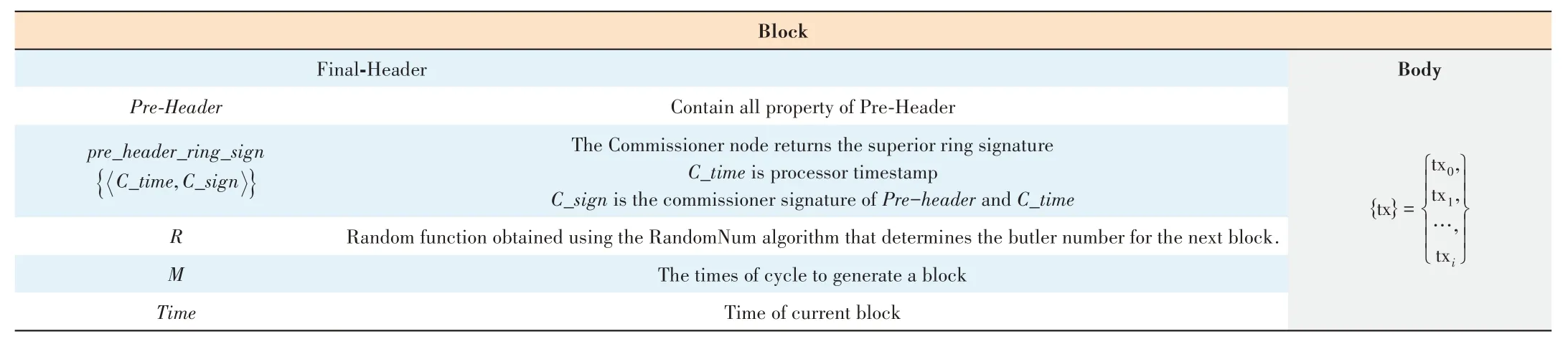
▼Table 1.Data structure for block

▼Table 2.Data structure for pre-block

▲Figure 5.User registration flow.
2)User inquiry.
The user inquiry process consists of receiving the client’s query user request,querying the user information from the user information table and returning it to the client.MIS system supports two types of queries:querying the corresponding user information through the user public key and querying all user information.
3)Resource publishing.
The content in the network also follows the rules of prefix names.Fig.6 shows the full process of resource publishing.When a user applies to publish content on the network,the published resource will be signed and submitted to the blockchain node for the consensus process.Specifically,the blockchain node that receives the request encapsulates the request in an ordinary transaction,and then several nodes verify and vote on this transaction.If the consensus is agreed,the inter-translated information will be stored in the table shown in Table 5.
4)Resource inquiry.
The resource inquiry function receives the client’s identifier query request.The request inquires about the real addresscorresponding to the inter-translation information table.Similar to the user inquiry,MIS supports two types of queries:querying data by content identity and querying data by the resource publisher’s public key.

▼Table 3.An example of the user application table

▼Table 4.User information table

▼Table 5.Content in inter-translation table

▲Figure 6.Resource publication flow.
5 Evaluation
We develop a prototype system for MIS and deploy it on a real carrier-level operators’network consisting of the Chinese mainland and China’s Hong Kong and Macao special administrative regions,as shown in Fig.7.The system has realized the binding mechanism of user content and private key signature,as well as the blockchain function module and application function module.The system contains the user client and administrator client.
The main function of the user client is to generate a pair of public and private keys for the user and upload the user ID and public key to the blockchain so that the user ID is bound to the public key.Details are shown in Fig.8.At the same time,the users who publish resources will apply for a content name prefix when registering,achieving the binding of content identifier and public key.The users who have successfully registered can publish content using the content name prefix applied during registration.The resource publishing operation needs to add the user’s private key signature information.After the blockchain receives the request to publish the resource,it verifies the user rights through the signature.The signature also binds the user identity to the published content identifier,so as used for the inter-translation of the identity when routing.
The main function of the administrator client of blockchain includes the real-time display of the running state of nodes,querying of blockchain data and configuration of blockchain nodes.Blockchain nodes store the identifier data,the user information stored in the form of transactions in each block.Each registration and publication generate a consensus for the whole network.The consensus is reflected in the number of transactions in the administrator interface that is shown in Fig.9.
We deployed PoV and Practical Byzantine Fault Tolerance(PBFT) in a distributed environment and measured their throughput Transaction Per Second (TPS) separately.The experimental environment included five servers connected to the same router,each with 128 Gigabytes of memory and an Intel Xeon Silver 4116 processor.The PoV butler node was set to generate six PoV blocks,including five common blocks and one special block,within one service cycle.The theoretical calculation and experimental test results are shown in Table 6.

▲Figure 7.The proposed prototype system for multi-identifier System.

▲Figure 8.Interfaces of user registration and resource publishing.
The results show that the performance trends of the two algorithms are consistent with the theoretical values.When the number of nodes is more than 100,the TPS of PoV declines slowly,and the rate of decline is slower than PBFT.Compared with the traditional PBFT algorithm,PoV has better scalability.This is because the PoV consensus two-phase commit communication complexity is onlyO(n),which is only affected by the number of commission nodes.In terms of performance,the PoV consensus only needs one block to achieve tamper-proof transaction confirmation,with better performance and lower energy consumption than the public chain.

▲Figure 9.Status information of blockchain.
6 Conclusions
A future network should be decentralized,secure and compatible with the existing IP-based network.In this paper,we propose a multi-identifier system that constructs a network layer with a parallel coexistence of multiple identifiers,including identity,content,geographic information,and IP address.MIS provides the generation,management,and resolution ser-vices of identifiers and uses consortium blockchain to enable decentralized management.MIS also implements data privacy protection.The test results based on the prototype system show that the network has excellent performance and can support real-world applications after further development.

▼Table 6.Comparison between PBFT and PoV
- ZTE Communications的其它文章
- Advanced EPC Network Architecture Based on Hardware Information Service
- Integrated Architecture for Networking and Industrial Internet Identity
- Identifier Management of Industrial Internet Based on Multi-Identifier Network Architecture
- Risk Analysis of Industrial Internet Identity System
- Security Risk Analysis Model for Identification and Resolution System of Industrial Internet
- Construction and Application of Identifier Resolution in Automotive Industrial Internet

