Dynamic Matching-Based Spectrum Detection in Cognitive Radio Networks
Yu Gu,Qingqi Pei,Hongning Li*
1 Shaanxi Key Laboratory of BlockChain and Security Computing,Xidian University
2 The State Key Laboratory of Integrated Services Networks,Xidian University,Xi'an 710071,China
Abstract: Cognitive Radio Network provides an opportunity to reduce the spectrum resource crisis by allowing secondary users to access the idle spectrum allocated to primary users.The precondition of spectrum sharing is to obtain the Spectrum Availability Information (SAI).Energy detection is a typical technology to get SAI.With the mobility of primary users,the energy received by secondary users varies greatly with the distance from the target primary users.Most of the existing energy detection algorithms that use fixed thresholds are not suitable.We propose a Dynamic Matching-Based Spectrum Detection (DMBSD) scheme which can detect sensing data,reduce the impact of malicious data and make final sensing results more accurate with dynamic threshold setting and data matching.Simulation results show that the proposed scheme can detect tempered data,and increase detection probability by decreasing false alarm probability and missed detection probability.
Keywords: cognitive radio;spectrum sensing;degradation domain;dynamic matching
I.INTRODUCTION
Cognitive radio (CR) is an efficient solution to improve the spectrum utilization for wireless communication systems.Secondary users should monitor spectrum bands to obtain and access available resources without disrupting the communication of spectrum owners (or primary user (PUs)) [1,2].Spectrum sensing allows secondary users to identify vacant spectrum bands without the need of PUs' communication intervention.Dynamic spectrum access allows secondary users to access the abundant spectrum holes in the licensed spectrum bands [3].Obtaining reliable SAI is the essential precondition.Efficient spectrum sensing solutions have been proposed to determine the presence of the PU transmission [4-12].Most of these solutions can be classified into three types,energy detection,feature detection [13] and matched filtering detection [9].Other spectrum sensing methods are also discussed in [9].Due to the simplicity and no requirements of prior information about PUs,energy detection is widely used in recent research.
Energy detection is widely used due to its low computational complexity,and generic implementation.It does not require transmitted signal properties,channel information,or even the type of modulation [14].Energy detection measures the received signal energy within the predefined bandwidth and time period,then compares it with a predefined energy threshold [15,16] to determine SAI.If the sensed energy level is above the threshold,then the state of the primary user is present,otherwise,the spectrum band is vacant.It is very practical since it requires little information about the signal to be detected.Lots of research on energy detection have been conducted in the past few years.For example,cooperative energy spectrum sensing algorithms among secondary users are proposed to improve sensing performance [17-21].With cooperation among secondary users,we can reduce the impact of hidden terminals and malicious users or attackers to obtain more reliable sensing data.Most of these algorithms are using fixed thresholds,which can be determined from the targeted false alarm or missed detection probabilities.
Although energy detection is the simplest scheme to obtain PUs' channel states,threshold selection is a challenge during spectrum decision.Both the noise level and the signal attenuation can affect received signal energy by secondary users during spectrum sensing.Unlike the conventional energy detections using a fixed value of λ,some recent works consider dynamic threshold control [22-24].The adaptive threshold which is relative to the time of spectrum sensing in [22] is obtained based on the number of samples in low SNR conditions.In [23],the threshold is dynamically adapted to noise levels based on the Constant False Alarm Rate (CFAR).Comparing with traditional methods,most of these schemes consider the detection threshold in low SNR conditions,and assume that PUs are fixed.However,most PUs are mobile devices in CRNs.The received signal energy in the same area of a target PU can be different with the mobility of the PU.Therefore,besides SNR,PUs' mobility is a significant factor to affect the final sensing data.From the content mentioned above,a dynamic detection threshold selection is necessary to make accurate spectrum sensing results.
In this paper,we propose a DMBSD scheme to dynamically select detection thresholds.
A) Division of degradation domains
In the proposed DMBSD scheme,we design degradation domains and confidence intervals to deal with sensing data with consideration of both the signal attenuation and different noise level together.With the fixed location of PUs,the received signal energy sensed by a secondary user is related to noise level and the distance between the secondary user and the target PU.
B) Dynamic thresholds with PUs’ mobility
The mobility of PUs can change the received signal energy sensed by secondary users.Traditional works always assume that PUs are fixed.However,similar to secondary users,most PUs are mobile users or devices.In DMBSD,the threshold for each PU in different areas are varying with the location of the PU,the signal power of the PU and the noise level in each area.
C) Dynamic matching
We adopt dynamic matching during sensing data processing.According to setting of degradation domains and confidence intervals,we can match secondary users' sensing data with the corresponding interval dynamically to detect sensed data and discard suspected tampered data to make sensing result more reliable.
In the proposed DMBSD,we divided all coverage area of PUs into different cells.Each cell belongs to one degradation domain of a target PU.All degradation domains and the detection thresholds are varying with PUs' mobility and noise level of each cell.Finally,we used dynamic matching to detect all sensing data to obtain reliable SAI.
The rest of this paper is organized as follows.Section II introduces spectrum sensing and problem description.Section III presents the proposed DMBSD scheme.Section IV discusses and analyzes the proposed scheme and Section V concludes this paper.
II.SPECTRUM SENSING AND PROBLEM DESCRIPTION
2.1 Cooperative spectrum sensing
Traditional centralized CRNs include a set of PUs,a set of secondary users (SUs),a set of routers and a fusion center (FC).Most literatures assume that all PUs are fixed,and different PUs can transmit with different power but the power of each PU remains unchanged when transmitting.All SUs are mobile and they can choose one or more PUs' signal to detect.A FC can collect sensing data from SUs by relays of routers.The system architecture is shown in Figure 1.Each SU can select a PU to sense if it is within the coverage of the PU.Single node spectrum sensing are not reliable since shadowing and time varying multipath fading exist,therefore,detecting channel states of PUs based on the observation of a single secondary user may not be enough.
To alleviate this problem,cooperative spectrum sensing is envisaged.Multiple SUs can sense PUs' signal cooperatively to improve spectrum sensing accuracy.Since the capabilities of SUs are different,parts of SUs can sense multiple channels synchronously.Each SU chooses channels to sense,then send the sensed data to the fusion center (FC).With the received sensing data,the FC will make final decisions to get the status of each channel.The state of channelican be decided according to the following:
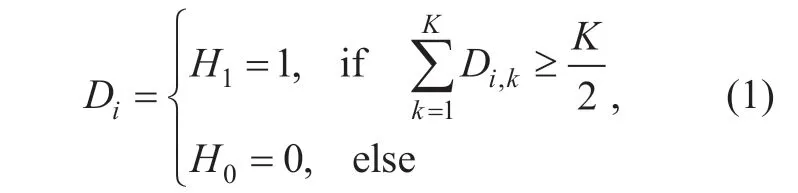
H1represents the channel is occupied by a PU andH0represents the channel is vacant.
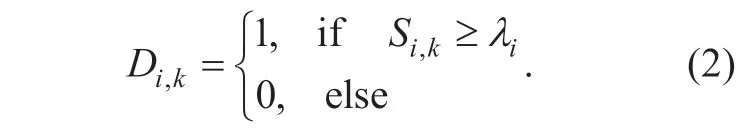
whereSi,kis the sensed data of PUiby a secondary user.λiis the threshold of the transmit power of PUi.IfSi,k≥λi,the state of PUidecided by the secondary user is“ON”,otherwise“OFF”.Kis the number of SUs that are sensing channeli.Dik,∈{0,1} is the individual decision of SUkon channeli.Majority rule is used in this paper for the decision making process.Other rules such as“AND”and“OR”are also used for decision making in literature.The“AND”rule decides that a signal is present if all SUs have detected a signal.The“OR”rule decides that a signal is present if any of the SUs detect a signal.“AND”and“OR”rule are special cases of majority decision.In cooperative spectrum sensing,majority decision is more reliable with the existing of multipath fading,shadowing,and the receiver uncertainty problems [25,26].
Due to the low complexity and no prior knowledge requirements for PUs' signals,energy detection is optimal for detecting any unknown signal.Besides,cooperative spectrum sensing is more reliable in a complicated wireless environment.Therefore,cooperative energy spectrum sensing is a efficient approach for cognitive radio networks.
2.2 Problem description
Although it is a efficient approach,energy detection has its own challenges.In this section,we describe a problem during spectrum sensing with cooperative energy detection.All SUs can sense the selected channels and make decisions with Eq.(1).The correct detection on the channel status of the primary users includes two cases.One is that when the sensing channel is busy,and the final detection result is busy.The other is that when the sensing channel is idle,and the final decision is idle.Therefore,for each channel denotedi,the correct detection probability should include two parts:Pi(H0|H0) when the target PU is absent andPi(H1|H1) when the target PU is present.As a result,we combine these two states,and the correct detection probabilityPDiis defined as:

Fig.1.System architecture.
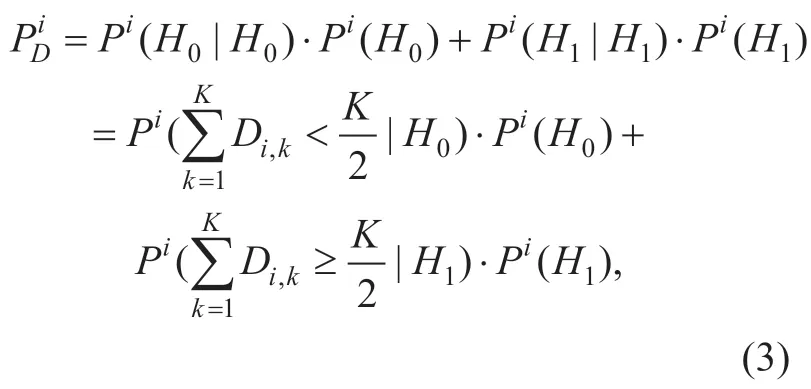
The detection probability of the whole networkPD:
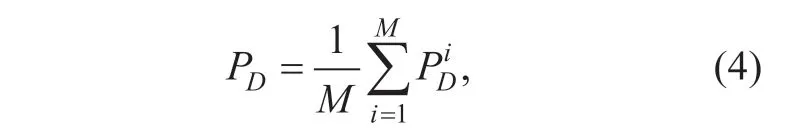
where,Mis the total number of channels (the total number of PUs that remained to be detected).In our scheme,one PU can also have multiple available channels,just like the OFDM-based networks.Energy detection is also can be applied in OFDM-based networks [27,28].To illustrate,we only talk about the scenario of one channel for one PU.P(Hi0) andPi(H1) are the probability of channeliin“OFF”state and“ON”state,respectively.The“ON/OFF”activity models of primary user have been researched in [29-31].To illustrate our proposed DMBSD scheme,we use the ON-OFF Bernoulli Model in [31] as the activity model of the primary user.P(H1|H0) andP(H0|H1) are false-alarm probabilityPfand miss detection probabilityPm,respectively.For each channeli,false-alarm probabilityPfiand miss detection probabilityPmiare:
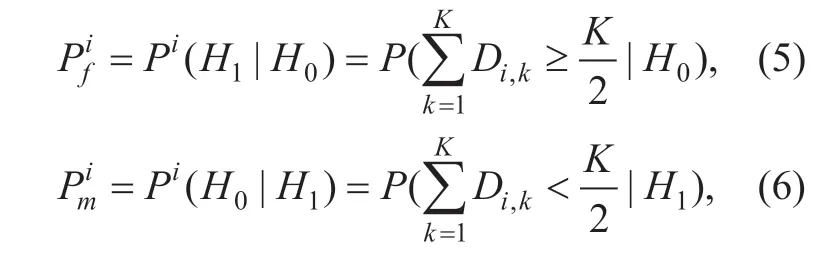
We consider the“ON”and“OFF”statuses of primary users' as the research object.For each channeli,according to the full probability formula,the total normalization probability formula is:
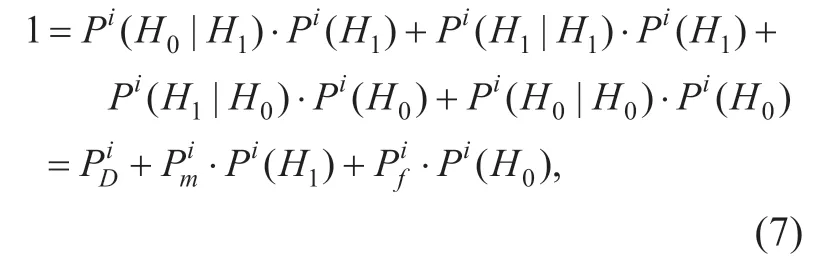
The total false-alarm probabilityPfand miss detection probabilityPmare:
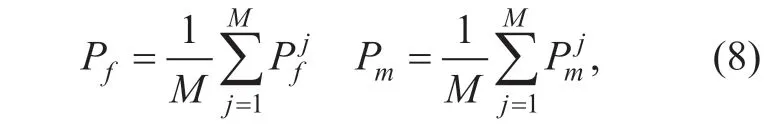
From the total probability formula Eq.(4),Eq.(7) and Eq.(8),we can obtain that:
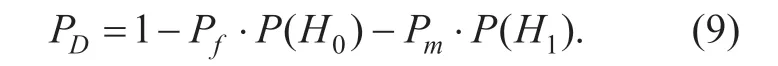
The decision of each channel relies on the sensing data and the threshold which has been predefined in Eq.(2).The value of the thresholdλifor each channel is a significant factor to the detection probability.Ifλiis too large,we will consider that a channel is vacant while it is busy in fact,andP(H0|H1) will increase.Ifλiis too small,we will miss opportunities to use a vacant channel,andP(H1|H0) will increase.Therefore,the detection probabilityPDis also related to the corresponding thresholdλi.Besides,for wireless channel fading and noise,even sensing the same signal,SUs in different location can get different sensing data.In consequence,setting the same thresholdλito make decision is not suitable during spectrum sensing in CRNs.The value ofλifor each channel should be dependent on the transmit power,the location of SU,actual physical environment around SU and the source signal (primary users in this paper),and so on.
As a typical kind of attack during spectrum sensing,spectrum sensing data falsification (SSDF) attack can affectPfiandPmi.With SSDF attack,malicious secondary users intentionally send falsified local sensing result to the FC to cause incorrect global decision [32,33].For instance,reporting high (low) sensing data when the signal of a PU is absent (present) actually,or sending out random sensing result to confuse final decision of the FC.Therefore,they can increase false-alarm probabilityPfand miss detection probabilityPm,finally decrease detection probabilityPD.From the features of attackers,we can classify the SSDF attack into two types:Counter Attack:Malicious secondary users always send opposite results to the FC during spectrum sensing.When the malicious secondary users obtain that the sensing channel is idle,they can send the sensing data greater than the decision threshold to FC,attempting to make FC decide that the channel is occupied by PU.Conversely,malicious secondary users can send sensing data less than the decision threshold to FC when the sensing channel is busy.Random Attack:Malicious secondary users send high and low sensing data randomly.Malicious secondary users randomly send data that is greater than or less than the decision threshold to the FC regardless of theirs sensing data.
Both Counter Attack and Random Attack can increase false-alarm probabilityPfand miss detection probabilityPm,thus decreasingPD.With low detection probabilityPD,secondary users can not make full use of available idle spectrum,and sometimes they may interfere the communication of primary user systems.How to guarantee the reliability of sensing data and the accuracy of the fi nal decision result in a hostile environment need to be solved.
III.DYNAMIC MATCHING CORRELATION-BASED SPECTRUM DETECTION
Before describing the dynamic matching correlation-based data detection scheme for spectrum decision,we state some of the assumptions that form the foundation of the scheme.The topology of the primary system is assumed to be variable,which means that all PUs are mobile,but they can be considered as stationary during a period of time.Each PU's transmitter output power remains unchanged,but any two of them can be different.All SUs are mobile and form an ad hoc network,and they can connect to nearby cognitive routers.Each SU is assumed to have GPS capability.Attackers are capable of changing their sensing data and transmission output power.
Based on the assumptions mentioned above,we propose a DMBSD scheme.The system architecture of DMBSD scheme based on literature [2] is shown in Figure 2.There are four kinds of entities in the system,PUs,SUs,cognitive routers and a fusion center (FC).The cognitive routers can be wifi routers,cellular base stations and other access points that can connect SUs to the FC.The proposed DMBSD scheme includes three parts: establishment of degradation domains,setting of confidence intervals and data matching.Each SU sends a packet including sensing data and its location information to the FC with the relay of cognitive router.During data matching,after receiving the packet,the FC matches the sensing data with the confi dence intervals of the corresponding degradation domain.Confidence intervals are tolerance intervals,which are set before data matching using data statistics of trusted users.Each confi dence interval can be considered as a threshold in the corresponding degradation domain.After data matching,the FC will make final decision on each sensed channel.
3.1 Establishment of degradation domains
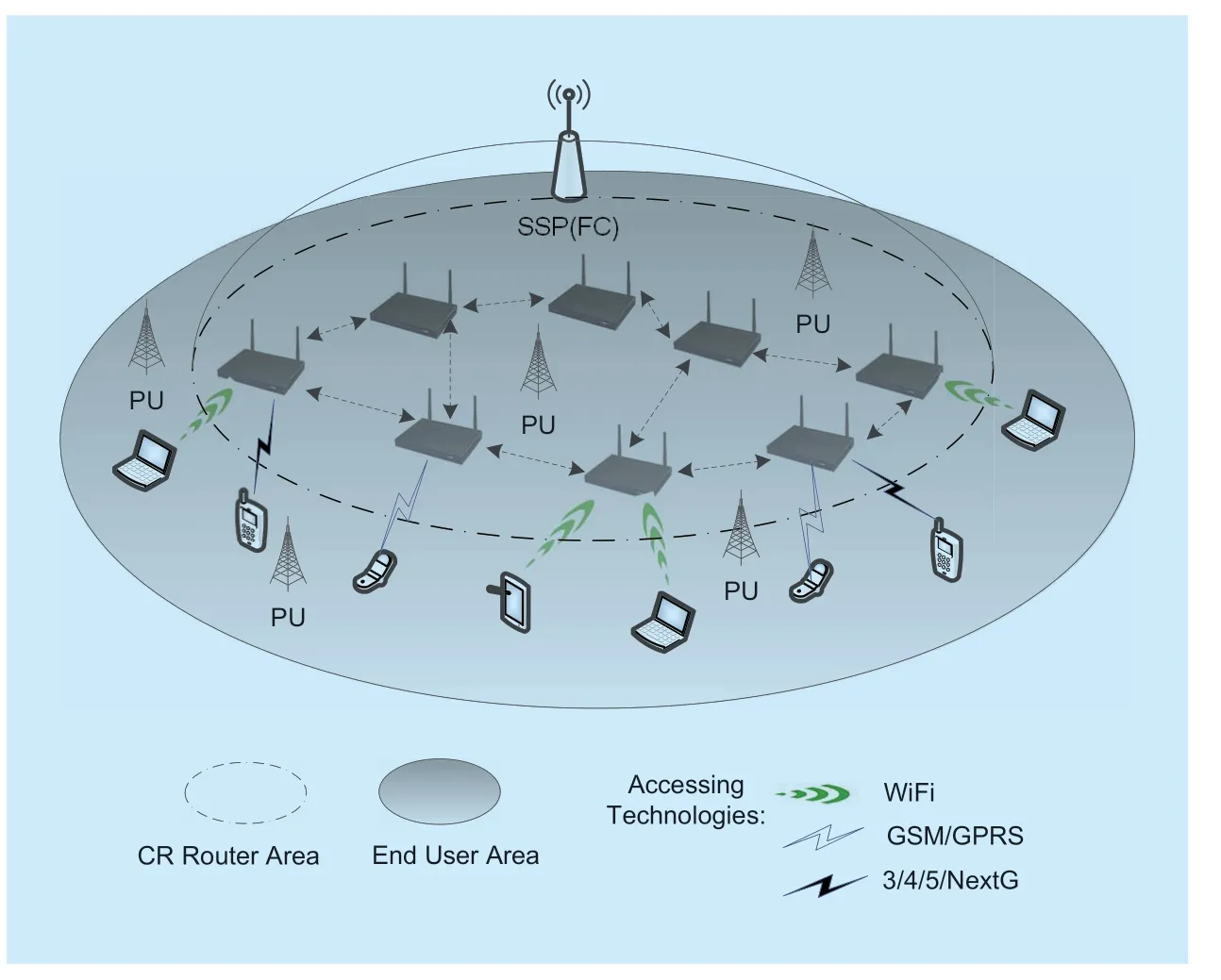
Fig.2.System model of DMBSD.
There are multiple PUs in the system,and different PUs may have different output powers.Firstly,we divide the whole area into several cells represented byVijin Figure 3(a) (to illustrate the scheme,we divide the whole network into average cells).For each PU in a certain time interval,we take the PU as a center and match all other cells into different degradation domains for this PU in Figure 3(b).As shown in Figure 3(b),degradation domain refers to the ring-shaped area with the same number between two rectangles centered on the PU.The degradation domains for each PU are varying with the mobility of the PU.
All degradation domains of a PU can be decided by the distance between the PU and the corresponding cells.Take Figure 3(b) for an example.There are 4 degradation domains of the PU.From Figure 3(b),assuming that the length of eachVijisaand the center PU's domain isD0,we can conclude the distribution of each degradation domain as follows:
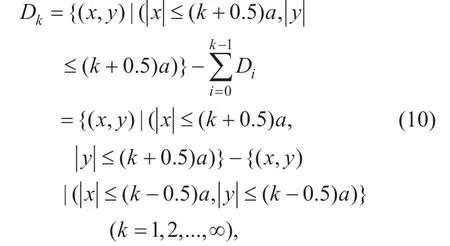
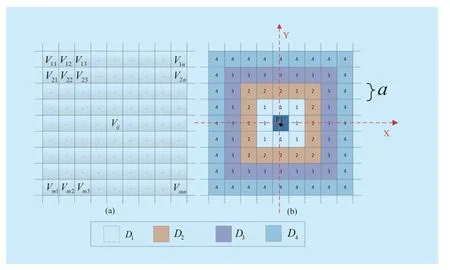
Fig.3.Establishment of degradation domains.
From the division of cells,we can see that the cellsVijare fi xed,but a cell may belong to different degradation domains in different time with mobility of PUs and a same cell may belong to different degradation domains of multiple PUs synchronously.Similarly,even at the same time,if two PUs namely PUBand PUChave different coordinates,a secondary user SUAwill belong to different degradation domains of PUBand PUC,respectively.Besides,if a PU remains fixed,SUs can sense the PU in different degradation domains with their mobility,but the degradation domains remain unchanged of the PU.However,if the PU moves,all its degradation domains can be changed.
3.2 Setting of confi dence intervals
According to location of each PU,we can match all cells into different degradation domains of each PU with Step 3.1.Each degradation domain of received signal includes two parts: the target PU's signal and the noise.In initialization process,after the establishment of degradation domains for different PUs,we will deploy a number of trusted nodes to sense the wireless environments to obtain the noise level of each cell (the noise level of each degradation domain remains unchanged before we update it next time ).The trusted nodes can be authenticated internal nodes,and the nodes are not affected by the hidden terminal.In practice,the trusted nodes can be secondary nodes in the wireless network.Then we compute all maximum and minimum energy value for the degradation domains of the whole network.The energy value can be statistically calculated.Afterwards,we can obtain all energy intervalsand the thresholdλNof each degradation domain.Since the nature characteristics of wireless signal,even in the same location,SUs cannot get the same sensing data for uncertain factors such as breakdown,malicious behavior,etc..We set a toleranceδfor each energy interval.We call the energy interval with toleranceδas the confidence interval.Therefore,dynamic confidence interval of each degradation domain can be represented as:
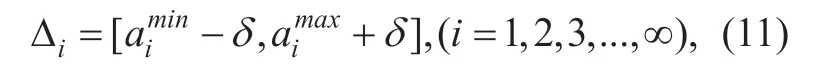
The tolerance for each conf idence interval is 2δ,which is relative to the accuracy of spectrum sensing data.
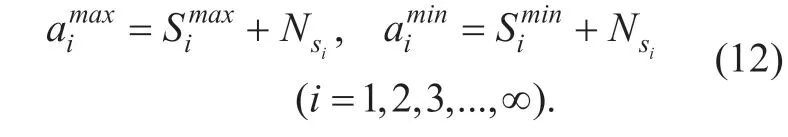
Simaxis the maximum received power of the target PU (when the PU is“ON”) sensed in the degradation domainDiof the PU andSiminis the minimum received power of the target PU (when the PU is“ON”) in the degradation domainDi.Nsiis the average noise of the corresponding degradation domainDi.Allai,(i= 1,2,...,∞) are obtained during“ON”state of each PU.Confidence intervals for all degradation domains can be calculated after a period of sensing by trusted nodes.These data will be stored in the FC to be used to match data in the stage of data matching.The relation among confidence intervals is shown in Fig.4.Most sensing algorithms make decision of channel states according to the comparison between received signal andλwhich is a common threshold of the target PU.However,for the uneven distribution,thresholds in different areas are not the same.The Received Signal Strength (RSS) can vary from the emission signal strength toa∞,the limit of which is 0.And it is also related to the location of the target PU.With PUs' mobility,the thresholds in different areas should be different.Therefore,to set dynamic thresholds for a channel in different areas is much more suitable during spectrum sensing.
All data collected by the trust nodes will be stored in a database and shared with the FC.The data includes RSS of each PU and the noise interval in different degradation domains.Information about all PUs' location should be shared with the FC.
3.3 Data matching
After spectrum sensing,all SUs send sensing data to the FC with the relay of routers.The data transmitted includes three parts,(Se,Vij,t),which presents spectrum sensing data,location and the time of transmission,respectively.Receiving sensing data from all SUs,the FC will match all data received with corresponding confidence intervals stored before.If the value ofSelies within the confidence interval range defined ofDi,the FC will use the sensing data to make final decision,otherwise,the FC will give up the dataSe.For example,a SU sends sensing datato the FC.The FC firstly computes which degradation domain of PUAthe SU belongs to,and then matchesSeAwith the confidence intervalThe matching resultSigniA jcan be represented as:

Then,we can obtain the sensing result of all SUs who sent sensing data to the FC in domainDifor PUA:
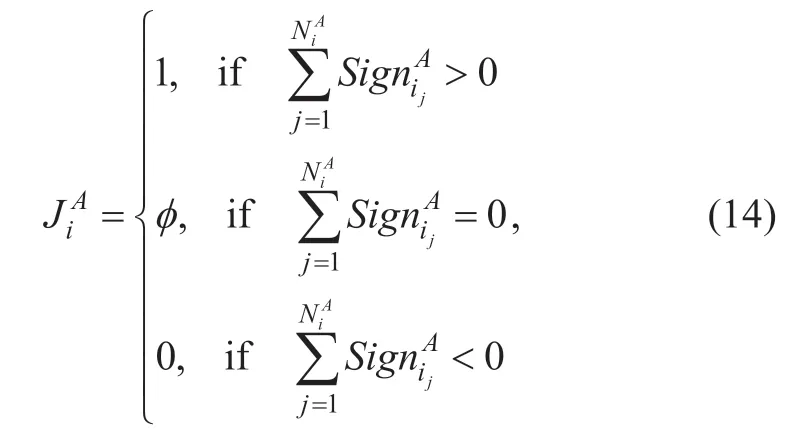

Fig.4.Relation presentation among confidence intervals.
JiAis the sensing decision in the degradation domainDiAfor the channel state of PUA.NiAis the number of SUs whose sensing reports fall inside the corresponding intervalin degradation domainDiA.NsiAis the average noise in degradation domainDiA.Δsiis the fluctuation range ofNsiA.If a SU is an attacker or an honest user but affected by the hidden terminal,the sensing dataSemay not fall within the confidence interval of degradation domainDiA.From Eq.(13),its sign functionSigniA jwill be set to 0.This means that the data of attackers or hidden terminal users is culled and does not affect the FC final decision result.
The final decision of the channel state of PUAis:
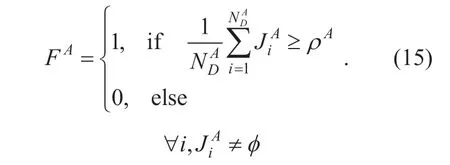
NDAis the number of degradation domains of the signal of PUA.ρAis a decision threshold to judge the existing of the signal of PUA.It is not like the traditional threshold in Eq.(2).The value ofJiAis 0 or 1.We first sum the value ofJiA,then average it,and finally compare with thresholdρAto get the final decision.For example,we assume that the final decision is 1.If the value ofρAis 0.5,it means that there are at least half of the 1 in theJiA.If the value ofρAis set too large,it needs more value of 1 in theJiAand the missed detection probabilityPumwill increase,and vice versa,it needs more value of 0 in theJiAand the false alarm probabilityPufwill increase.Therefore,in Eq.(15) the decision accuracy is partly related to the setting ofρA.In addition,ifJiA=φ,the data will be invalid.
Following the steps mentioned above,the FC can calculate all channels' states,and make final spectrum availability information of the whole network.With establishment of degradation domains,setting of confidence intervals and data matching,the proposed matching correlation-based data detection scheme can increase the accuracy of spectrum sensing data efficiently.
IV.ANALYSIS OF DMBSD SCHEME
In this section,to demonstrate the reliability of the sensing result with our proposed DMBSD scheme,we consider the case of a single PU,and the PU can be mobile.But it is assumed that the PU's position is unchanged during a spectrum sensing period.The SU can be fixed or mobile.Based on the these assumptions,the detection probabilityPudis,
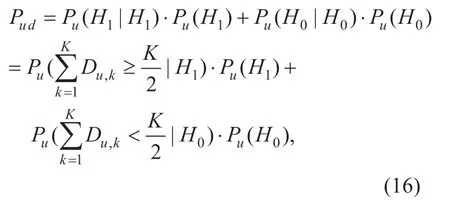
the false alarm probabilityPuf,
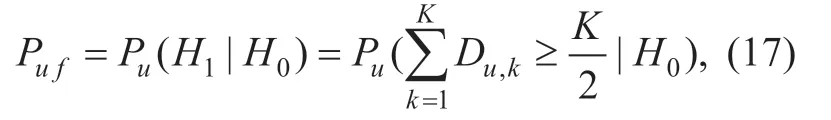
the missed detection probabilityPum,
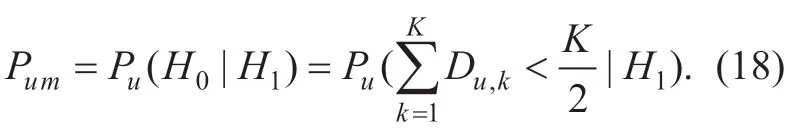
and the attacker detection probabilityPad,Pad=ai/aN,which is the ratio of the number of detected attackersaiand the total number of attackersaN.
All SUs should send sensing report to the FC with content of the sensing data and degradation domains they belong to.Each degradation domain is computed with the process described in Step 3.1 of Section III.In cognitive radio networks,there are multiple PUs and SUs.To illustrate our scheme proposed in this paper,we consider a simple structure first.In the structure,there is only one primary user representedPU1.Tp1is the transmit power ofPU1.PU1can be mobile,but its location (which cell is belongs to) should be shared with the FC.Then the FC can divide degradation domains for the primary userPU1.A mobile primary user can be dealt with a fixed one during a time interval.The degradation domains ofPU1areD11,D12,D31andD14in this time interval.The number of collaborative SUs is assumed to be 20,all of which are randomly distributed in the coverage area ofPU1.A few SUs are malicious and they will launch SSDF attack with reporting inauthentic sensing data during spectrum sensing.The corresponding confidence intervals areandrespectively.We setδ=Δsi=2,and setPu(H0)=Pu(H1)=0.5 that is consistent with the ON-OFF Bernoulli Model in [31] in our simulation.We use multiple USRPs to worked asPU1and SUs.The USRPs are used to transmit and receive FM signal,and divide degradation domains.Then,we use USRPs to measure the maximum received energy valueSimax,minimum received energy valueSiminand noise levelNsiof each degradation domain to obtain the confidence interval for simulation.In the actual network,SimaxandSimincan be obtained by mobile SUs(trusted nodes mentioned earlier) or Okumura Model,which is determined by the specific network environment.On the basis of obtaining the degradation domains and the confi dence intervals,the USRPs are also used to simulate the different distribution of SUs in different degradation regions (including the attackers),and multiple measurements are performed to obtain the actual sensing energy value.During time intervalt1,the FC collected sensing data from all SUs.We fi rst simulated the sensing decision result without attackers in Figure 5.In traditional energy detection,the detection probability is varying with different thresholds.In this simulation scenario,the optimal threshold of traditional energy detectionλis -85.From the comparison,the detection probabilityPudof the proposed DMBSD in this paper is much greater than traditional energy detection,and less volatile,which is more stable for different user distributions.The reason for this result is that the traditional energy detection cannot deal with faulty node,shadow effect,hidden terminal problem,etc..However,with DMBSD,we can detect and eliminate the effects caused by the problems mentioned above.In the following step,we selected the optimal thresholdλ=-85 to illustrate simulation.
Besides the detection algorithm,network environment such as malicious behavior is also a major factor that can affect detection probabilityPud.We consider the typical kinds of SSDF attack named“Counter Attack”and“Random Attack”.“Counter Attack”refers to that an attacker always sends the opposite result to the FC,for instance,reports high energy whenPU1is idle or reports low energy whenPU1is busy.“Random Attack”refers to that an attacker randomly sends high and low energy regardless of the activities ofPU1.We considered 5 out of 20 are attackers in our simulation.The variation curves of detection probabilityPudare shown in Figure 6.The detection probabilityPudcan reach 0.95 with DMBSD when“Counter Attack”or“Random Attack'' exists.However,the detection probabilityPudwith traditional energy decision is less than 0.8 and has more fl uctuations .The detection probabilityPuddecreases when attackers appear.False alarm probabilityPufand missed detection probabilityPumare two important indicators of spectrum sensing.Whenk=5,the comparison ofPufandPumbetween DMBSD and the traditional energy detection is shown in Figure 7.From the figure,Pufof DMBSD is smaller than traditional decision.It is because that the unifi ed threshold of traditional decisionλis not suitable for all different cells.The smaller theλ,the larger thePuf.The larger theλ,the larger thePum.Just as in Eq.(9),ifPfandPmincrease,PDwill decrease,and vice versa.
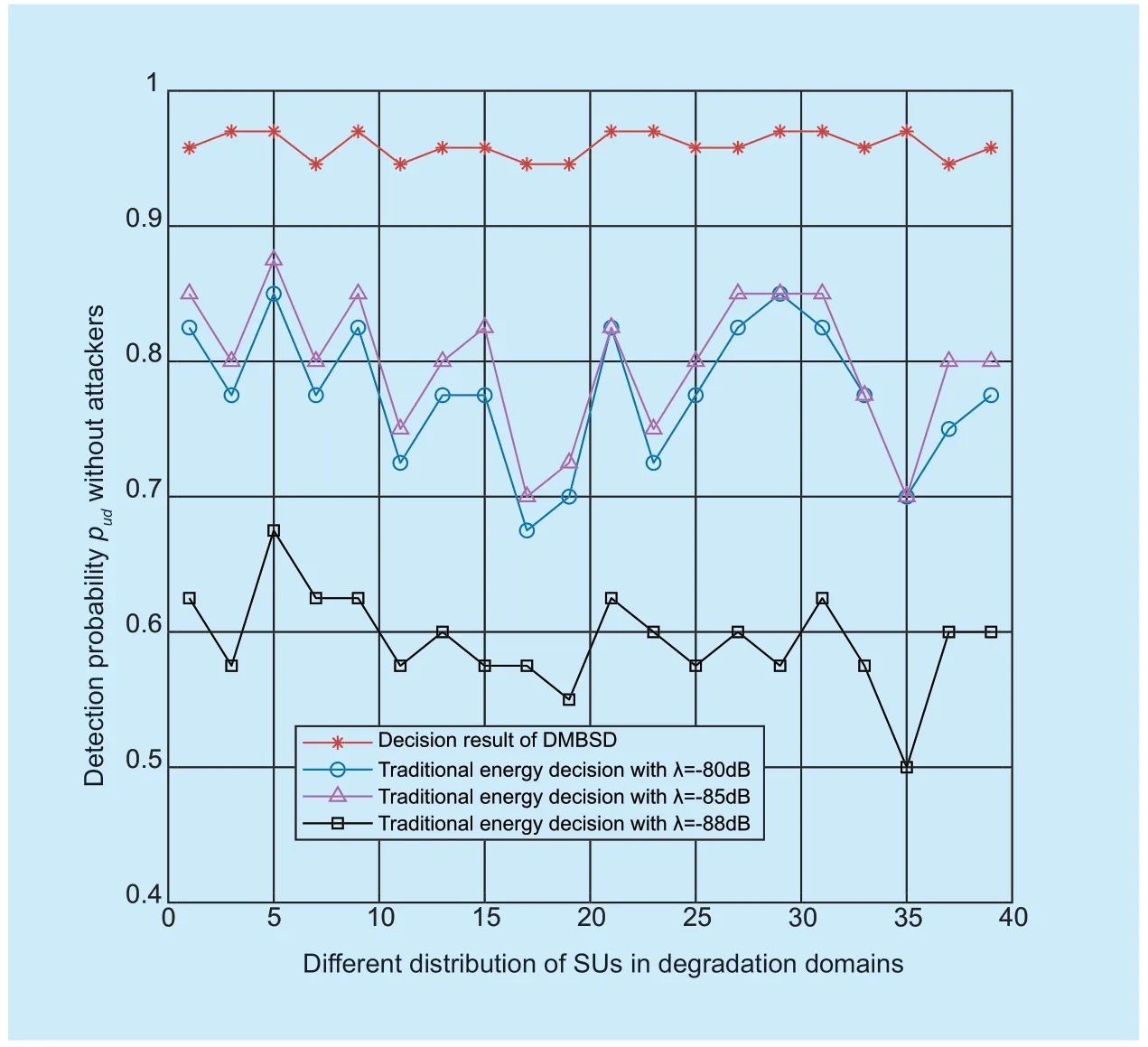
Fig.5. Comparison of detection probability Pud without attackers.
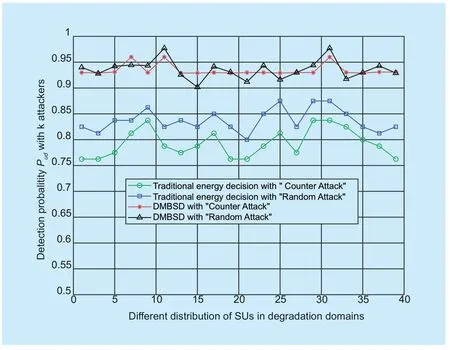
Fig.6.Detection probability Pud when k=5.
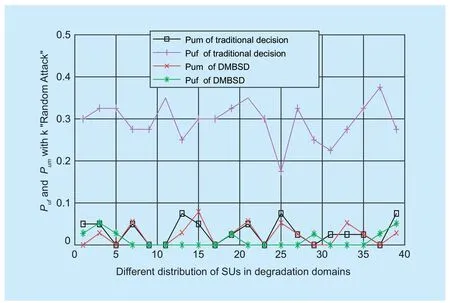
Fig.7.Puf and Pum with“Random Attack”(k=5).
Besides,to analyze the effi ciency of attacker detection,we gave the attacker detection probabilityPaddefi ned in the beginning of this section in Figure 8.We can obtain that the proposed DMBSD can detect attackers with large probability.The more attackers detected,the more accurate of the fi nal spectrum decision.
To make spectrum sensing decision more reliable,the proposed DMBSD can reject malicious data according to dynamic thresholds setting.With degradation domains establishment,confidence intervals setting and data matching,DMBSD is much more effective for spectrum sensing when PUs are mobile in complex wireless environment.
V.CONCLUSION
Cognitive radio technology provides opportunities for unauthorized users (or secondary users) to access spectrum bands without interfering primary systems.It utilizes vacant spectrum to increase spectrum utility and alleviates spectrum resources crisis.To guarantee the reliability of spectrum available information is vital to prevent primary systems from interfering during spectrum sensing.
In this work,we first gave the description of the problems existed in energy detection.A signifi cant factor is the threshold during spectrum sensing,especially when PUs are mobile.We proposed a DMBSD scheme to dynamically matching sensing data and the corresponding confi dence intervals.The obtained results verifi ed that the proposed scheme is a robust method against SSDF attacks and it is more effective in mobile environment.
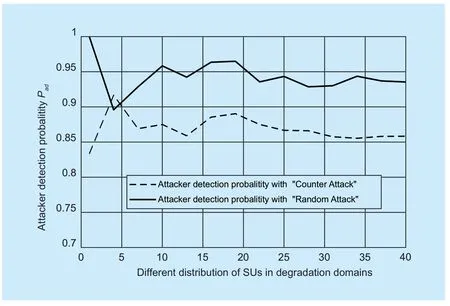
Fig.8.Attacker detection probability Pad when k=5.
ACKNOWLEDGMENT
This work is supported by the National Natural Science Foundation of China (No.61602358),the Key Program of NSFC-Tongyong Union Foundation under Grant U1636209,and the Fundamental Research Funds for the Central Universities (No.XJS17078).
- China Communications的其它文章
- A Bandwidth-Link Resources Cooperative Allocation Strategy of Data Communication in Intelligent Transportation Systems
- UP-TreeRec: Building Dynamic User Profiles Tree for News Recommendation
- A Fuzzy Decision Based WSN Localization Algorithm for Wise Healthcare
- Bistable Stochastic Resonance Enhanced 4-ary PAM Signal Detection under Low SNR
- Tensor Completion for Recovering Multichannel Audio Signal with Missing Data
- A PCA-Based Internet Delay Space Dividing Algorithm

