Secure Transmission Scheme Based on Dual-Thresholds for Simultaneous Wireless Information and Power Transfer
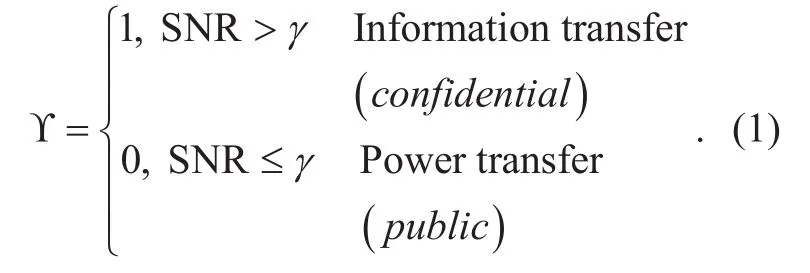
National Digital Switching System Engineering & Technological Research Center, Zhengzhou 450002, China
I. INTRODUCTION
Internet of Things (IoT) is a promising technology in 5G communications, whereas the devices in IoT are usually battery-powered and the working life of the entire network is severely restricted by the limited capacity of their batteries. Replacing batteries can extend the working life but may be rather difficult and costly for some of them (e.g., the electronic medical devices embedded into human bodies,the wireless sensors deployed inside building walls), thus how to provide continuous and stable power supply and reduce the cost of maintenance has become one of the burning issues that are urgent to be solved in IoT.
In recent years, simultaneous wireless information and power transfer (SWIPT) [1,2]has been deemed as a method of solving above problem. In SWIPT, wireless power transfer (WPT) and wireless information transfer(WIT) can be achieved in parallel owing to the opening and sharing feature of wireless transmission medium. Unfortunately, the openness may also expose the confidential information to non-target terminals, which brings security threats to the system [3,4]. To address this concern, innovative security technologies have been proposed for SWIPT systems.
As an important complement to the traditional cryptographic techniques, physical layer security (PLS) [5-7] exploits the “fingerprint”of wireless channels to protect communications from being eavesdropped with low computational complexity, which provides a novel approach to solving the issue of information leakage, especially in the cases where processing capacity is poorly guaranteed at communication terminals.
The paper proposes a lightweight secure transmission scheme based on dual-thresholds for physical-layer security enhancement,which consists of two protocols applied to the downlink (DL) and uplink (UL) transmission respectively.
1.1 Related works
In the past few years, great achievements have been devoted to securing SWIPT with PLS.The problem of PLS secure transmission,where the base station transmits confidential information to an information receiver (IR) in the present of multiple energy receivers (ERs),was studied in [8]. The authors regarded the ERs as potential eavesdroppers and designed the beam matrix to maximize the secrecy rate of the IR subject to the energy constraint of ERs. On this basis, the secrecy performance analysis and robust beam design were carried out respectively when the channel state information was imperfect at the transmitter in [9]and [10,11]. In addition, the authors in [12,13]considered the case where multiple ERs colluded with each other and eavesdropped on an IR user jointly, and the case where ERs and external eavesdroppers overhear the confidential information simultaneously was investigated in [14]. While in [15], the authors expanded the number of antennas at ERs, and the work in [16] dealt with a more complex SWIPT system, where both the IR and ER had multiple antennas. Furthermore, artificial noise (AN)was introduced to secure the transmission and the joint designs of AN-aided transmission beams were studied in [17,18], and that [19]utilized AN-aided transmission to secure the SWIPT in heterogeneous networks.
Above research works studied the PLS in SWIPT from different perspectives or in different scenarios, but they have some common problems. First, the authors mainly focused on the joint design of beam-forming and AN,which requires rich computational resources and does not match the idea of 5G green communications. In the optimization of beam matrix, the energy constraint of ERs as well as the leakage of both confidential message and AN need to be considered, which leads to high computational complexity when a large number of users are served simultaneously. Hence there lacks lightweight transmission scheme that coincides with the original intension of employing PLS. Then, the authors paid much attention to the downlink (DL) transmission,while the different case of uplink (UL) has been rarely concerned. In the UL, the transmission power is not fixed but related to the energy harvesting (EH) process during DL period, and the beam-forming cannot be carried out as the transmitter usually has single antenna, so the previous researches cannot be applied and how to secure the UL transmission remains to be studied. Furthermore, above works either discussed the eavesdroppers with fixed and known locations, or considered completely random location model (i.e. Poisson point process, PPP) for them, whereas there may exit some “goal-oriented” eavesdroppers that tend to hide nearly around certain targets,which cannot be accurately characterized by the previous two models but should be taken into account seriously.
1.2 Our approach and contributions
In this paper, we study the problem of enhancing PLS in SWIPT, where a resource center(RC) serves multiple energy-constraint users over quasi-static Rayleigh block-fading channels in the present of multiple external eavesdroppers and internal curious users. Focusing on the “goal-oriented” eavesdroppers that hide around RCs and legitimated users, we model the random network as Poisson clus-ter processes (PCPs) instead of independent homogenous PPPs. Meanwhile, having due regard to the constraint of energy, we establish communication model via time division multiple access (TDMA) to extend the EH duration of each user, which improves the quality of received signals as well.
On this basis, we propose a lightweight transmission scheme based on dual-thresholds to simultaneously secure the DL and UL transmission in SWIPT. To be specific, our main contributions can be summarized as follows:
● In the DL, we propose a dynamic information-power switching protocol based on signal-to-noise ratio (SNR) threshold. With this protocol, the RC dynamically switches between information transfer and power transfer by comparing instantaneous SNR to the pre-set threshold, which breaks through the fixed WPT-WIT period allocation and serves as an opportunistic approach.
● In the UL, we design a user-led on-off transmission protocol based on energy threshold. With this protocol, the single-antenna transmitter controls the UL transmission by comparing its harvested energy to the pre-set threshold, which exchanges short delay for the reliability and security of transmission.
● We evaluate various quality-of-service(QoS) measures by studying performance metrics in terms of transmission delay,security and reliability. The outage-based metrics that are suitable for quasi-static fading channels are adopted. We modify the metric of secrecy throughput according to the feature of SWIPT and utilize it to characterize the overall performance.
● Based on the analytical results, we propose efficient algorithms to optimize the two thresholds as well as the DL-UL partition coefficient. Simulation results show that with our proposed scheme, the secrecy performance can be significantly improved.
1.3 Organization and notations
The rest of this paper is organized as follows.Section II outlines the system model including location model, communication model and performance metrics. Section III designs the secure transmission scheme. Section IV provides the secrecy performance analysis of the proposed scheme. Section V optimizes the two thresholds and the DL-UL period coefficient.Section VI presents the simulation results and finally Section VII concludes this paper.
Notations: The Euclid second norm of vector v is denoted byThe factorial of a non-negative integer n is denoted bydenotes the circular symmetric complex Gaussian vector with mean vector Ο and covariance matrix Ω .denotes the Gamma-distributed random variable with shape θ and scale τ, and) denotes the exponential-distributed random variable with meandenotes the probability measure.denotes the statistical expectation. Besides the common notations mentioned above,others are outlined in Table 1.
II. SYSTEM MODEL
The SWIPT system is composed of several RCs with multiple antennas and a mass of energy-constraint users with single antenna. An RC serves multiple users by delivering power and transmitting information simultaneously.Meanwhile, it is assumed that there exist some malicious users, including external passive eavesdroppers and internal curious users,which aim to overhear the confidential information intended for specific targets.
We consider both large- and small-scale fading for the wireless channels. For the larger-scale fading, we adopt the standard path loss model l(r)=r−α, where r denotes the distance and α>2 is the fading exponent.For the small-scale fading, we assume independent quasi-static Rayleigh block fading.Furthermore, we assume the distributions of wiretapping channels are available, which has been widely adopted in the literature of secrecy performance analysis in PLS [20,21].

Table I Important notations
2.1 Location model
According to the unplanned deployment of RCs and users, the statistic geometry is employed to model their random locations. We focus on the severe case where external eavesdroppers have certain targets and hide nearly around them to enhance the chance of successful wiretapping, while modeling the network with independent homogenous PPPs [22]indicates that the eavesdroppers are distributed randomly and wiretap aimlessly, which is not accordant to our assumption. Therefore, we adopt PCP [23,24] to fully reflect the extensive distribution of eavesdroppers around RCs and users, as shown in figure 1.
To be specific, there are two PCPs (i.e. Φrand Φu) in figure 1. Take Φras an example,which consists of a parent process Ωrand a daughter process Λr. The parent processΩris a PPP with intensity λrthat models the spatial locations of RCs, which forms the center of each cluster; the daughter process Λrcan be divided into infinite sub-processes that contain nrdaughter points (a sub-process corresponds to a cluster center) andis the one that models the locations of eavesdroppers around RCi. Similarly, the PCP ΦuincludingΩuand Λuis applied to model the locations of energy-constraint users and the dense eavesdroppers around them.

Fig. 1 Illustration of a SWIPT system where the locations of legitimated nodes (RCs and users) and dense eavesdroppers around them are modeled by PCPs
According to the distribution of daughter points, PCP can be further classified into Thomas Cluster Process (TCP) and Matern cluster Process (MCP). We consider the TCP in this paper, where each daughter point is scattered around the center based on an uncorrelated two-dimensional normal distribution with the variance τ2.
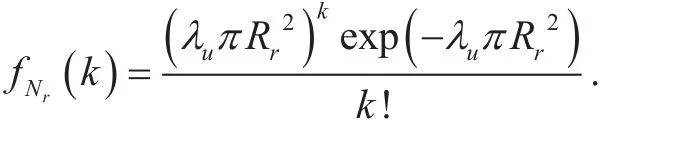
2.2 Commutation model
In general, the energy-constraint users are simply configured in the hardware with low processing capacity. Therefore, it is reasonable to assume that they adopt the “time switching”(TS) [25] receiver with lower complexity and work in the “harvesting-transmitting” (HT) [26] mode. It means that there is no independent power supply in each user, and all the transmission power must be acquired by EH.To promote the energy gain and guarantee the UL transmission, we establish the communication model of TDMA [27].
As shown in figure 2, a complete cycle is divided into DL βT and UL (1−β)T, and each of them is further separated into Ntslots that are dedicate for different users. In the DL, RCttransfers power or information to a specific user in one slot, which contributes to avoiding the complex interferences among users. In the meantime, non-target users harvest energy from the transmitted signal, which turns out to provide each user with Nt−1 more slots for EH besides its own assigned slot. In the UL, users take turns to send their confidential information to RCtwith the power stored during the DL.
However, since RCtcannot strictly control the behavior of users, it is likely that non-target users may also decode the information intended for specific user (DL) or RCt(UL),which leads to information leakage and brings secrecy threats. In this paper, we regard internal users as curious but honest users [28], who only decode others’ information due to curiosity and do not collude with external eavesdroppers.
For the sake of briefness, all the access users are numbered according to the relative distance to RCt(i.e. U1represents the nearest user to RCt) and RCtis assumed to communicate with Uiin the ithslot in either DL or UL period (i.e.

Fig. 2 Illustration of the slot allocation in TDMA
2.3 Evaluation Metrics
In the following, we detail the outage definitions for characterizing the transmission delay,the security performance and the reliability performance of the network. Specifically, we consider transmission probability (TP), connection outage probability (COP), secrecy outage probability (SOP) and secrecy throughput(STP) as metrics to characterize the performance of transmission in SWIPT.
With our proposed scheme, the UL transmission may not happen all the time and there is a probability of transmission referred to as TP, which is adopted as a measure of the performance of transmission delay [29]. As for the DL, there are two kinds of signals transmistted, our proposed scheme replaces the fixed allocation of them with an opportunnstic approach, so we further have information transfer probability (ITP) and power transfer probability (PTP). All these three probabilities can be expressed aswhere 1conditionrepresents a symbolic function, and 1condition=1 indicates the condition of transmission holds.
When the information transfer (DL) or transmission (UL) turns on, there are two kinds of outage events [29]: connection outage event and secrecy outage event.
The connection outage event happens when the message cannot be decoded without error at the intended receiver, and the probability of connection outage referred to as COP is given by
The secrecy outage event happens when the perfect secrecy of the message cannot be guaranteed, and the probability of secrecy outage referred to as SOP can be expressed aswhere Cmrepresents the ergodic rate of malicious users.
We adopt the COP as the measure of transmission reliability and SOP as the measure of transmission security.
Moreover in [29], STP is defined as, which can characterize the overall performance of the system by taking the transmission delay, security and reliability into account simultaneously. ξoquantizes the average rate at which the messages are securely and reliably transmitted. Whereas in SWIPT, WIP and WPT share an entire DL period, DL and UL period share an entire cycle. The period allocation of them is also critical to measure the overall performance. Hence we modify STP asξ=ξo⋅T*,where T*represents the duration of transmission. STP in this paper measures the average amount of confidential information that is reliably and securely transmitted to the intended user within the given time.
III. SECURE TRANSMISSION SCHEME
For the considered SWIPT system in section II, we design a secure transmission scheme based on dual-thresholds, which consists of two protocols that can secure the DL and UL transmission respectively. Following to the H-T working manner, we start the design from the DL transmission.
3.1 Dynamic Information-Power Switching Protocol
In the DL, both information transmission and power transfer need to be accomplished. In the traditional protocol for TS receivers, a complete DL period Tdlis divided into µTdland(1−µ)Tdl, which is occupied by power and information transfer respectively (as shown in figure 3). However, due to the randomness of wireless channels, this inflexible switching mode cannot guarantee the quality of transmission. Therefore, we design a protocol named dynamic information-power switching(DIPS) transmission that breaks through this fixed allocation.
In our proposed DIPS protocol, there is no pre-set µ but a pre-set SNR threshold γ for switching-control. RCtdynamically switches the transmission between information and power during a slot according to the instantaneous channel state acquired by channel esti-mation. To be specific, when the instantaneous SNR is larger than the switching threshold,the quality of transmission can be guaranteed,hence this time is considered to be suitable for information transfer and RCttransmits confidential information; otherwise when the channel is poor in quality, both the connection outage event and secrecy outage event are likely to occur, for secrecy reasons, RCttransmits public information for power transfer.
An indicator function is introduced here to illustrate the content of transmission information, which can be expressed as
This opportunistic approach accomplishes the information (power) transfer in several small slices of the DL period instead of a whole range, and the average duration of information and power transfer in a DL slot(later referred to as ADIT and ADPT) can be quantized byand
3.2 User-led on-off transmission protocol
In the UL transmission, the transmitters are single-antenna users, and all their power used for transmitting UL information is acquired by EH in the DL.
If the harvested energy is not “sufficient”,the transmission power may be rather low.

Fig. 3 Comparison between traditional and DIPS protocol

Fig. 4 Flow chart of the proposed scheme
This will lead to low SNR and then poor reliability and security of transmission. For the sake of secrecy, it is prudent to turn off the transmission at this time rather than transmit information insecurely. Therefore, we design a user-led on-off transmission protocol, where the user can control the transmission according to its harvested energy.
With this protocol, the user only transmits the UL information when it harvested more energy than the pre-set energy threshold v.An indicator function is introduced to illustrate the transmission is “on” or “off”, which is given by

It is noteworthy that we exchange the transmission delay for the security and reliability with this on-off protocol, but too much delay is also unacceptable in the transmission, which implies the trade-off between delay and security/reliability should be carefully considered.
3.3 Transmission procedure
A complete communication cycle under the proposed secure transmission scheme is shown in figure 4. When the cycle begins, the optimal switching thresholds and transmission thresholds for different users will be quickly determined (we will discuss in section V). After that, the DL transmission starts from U1.
RCtdivides the assigned slot of each user into m mini-slots and estimates channel at the very beginning of each mini-slot, according to which the instantaneous SNR can be acquired.If the SNR at a mini-slot exceeds the pre-set switching threshold, RCttransmits confidential information, otherwise transmits public information. When finishing all the mini-slots,RCtturns to the next user and executes the same process.
The UL transmission will not start from U1until all the access users have accomplished their DL slots. The user whose turn it is compares the energy stored in its battery to the pre-set energy threshold, and transmits its UL information to RCtif larger; otherwise turns off the transmission in this mini-slot and the UL information will be transmitted in the next cycle.
IV. PERFORMANCE EVALUATIONS
In this section, we first derive ITP, COP and SOP to measure the delay, reliability and security of information transfer in the DL transmission, which further obtains DL STP to characterize the overall secrecy performance of DIPS protocol. Then, similarly, TP, COP and SOP are derived and utilized to characterize the UL performance with user-led on-off transmission protocol. In the following analysis, we assume there are k users served by RCtand take Ui(1≤i≤k ) as an example for analysis without loss of generality.
4.1 Dynamic information-power switching protocol

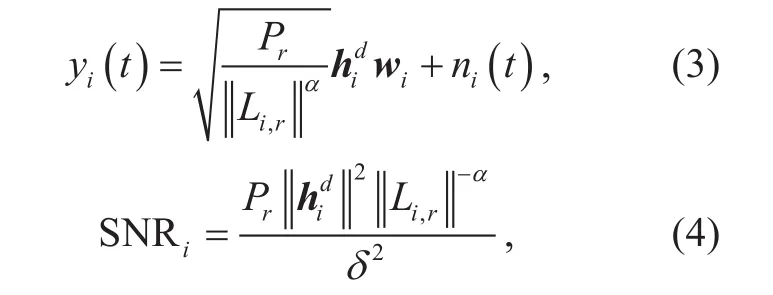
Meanwhile, internal non-target users may also decode this signal. The received SNR at other EH users can be expressed as
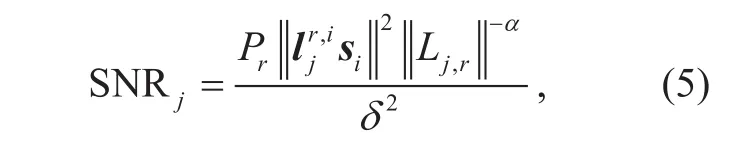
In addition, the passive eavesdroppers densely deployed in clusterare also interested in ci(t), the received signal and SNR at theeavesdropper inare given by
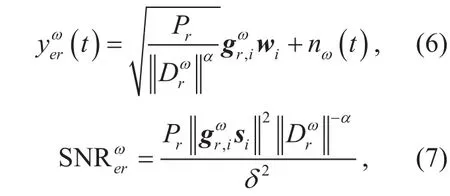
Based on the DIPS protocol, RCtdetermines the content of transmission signal by comparing SNRiwith the switching threshold γiin each mini-slot.
A) Information transfer:
If SNRiexceeds γi, RCtstarts the transmission of confidential information. For the sake of secrecy, we pay attention to the quality of transmission (delay, reliability and security)in information transfer.
Lemma 1: The ITP that RCtturns on information transfer at a mini-slot in tidcan be calculated as
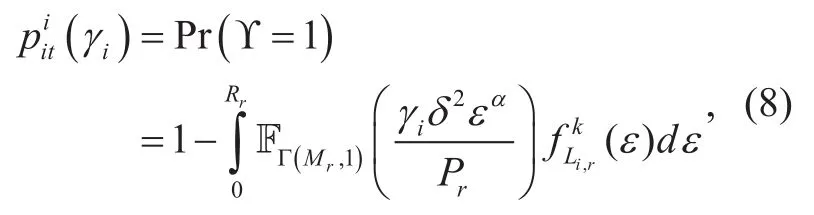
Since γiserves as the condition of information transfer, it can be inferred that ITP is a monotonous decreasing function of γi.
Lemma 2:The COP when RCttransmits confidential information to Uiis derived as(9) shown in the bottom at this page, where
It is noteworthy that the derived COP is a conditional probability on the condition related to γi. As γiconfines the worst quality of channel that can be utilized for information transfer, the transmission becomes more reliable as γiincreases.
Except for the intended user Ui, two kinds of malicious users are aiming at the confidential information as well. However, since internal users do not collude with external eavesdroppers, the secrecy outage event occurs when either eavesdroppers or curious users decode the information without error. The SOP of the information transfer incan be expressed as
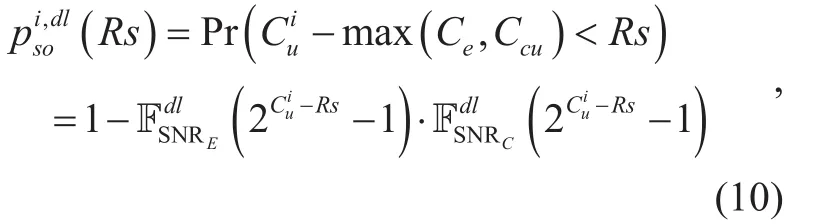
The difficulty of obtaining SOP lies inas well asand, hence the derivations of them are primarily presented in the following lemmas. Since the exact average achievable ergodic rate is relatively complicated, we consider its lower bound in this paper, which has little impact on the design of scheme.
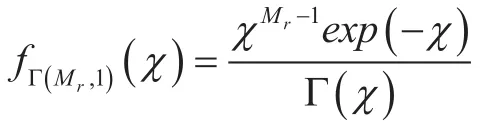
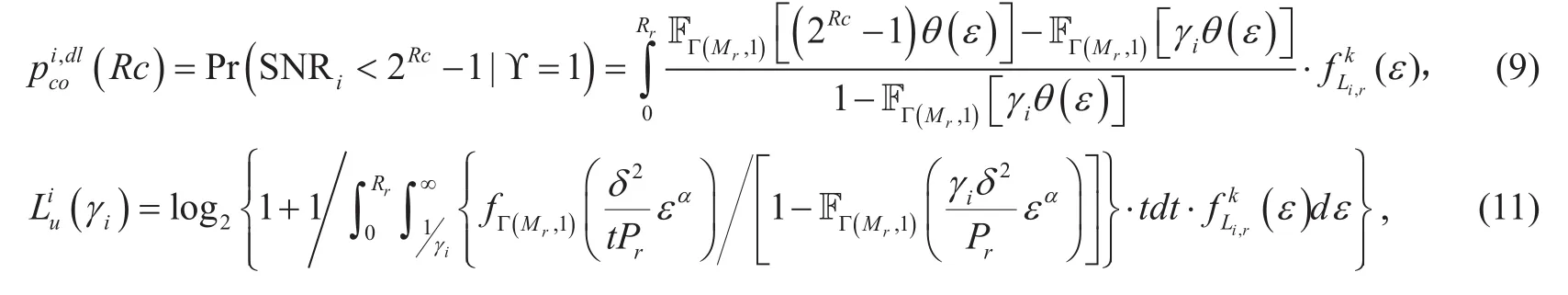
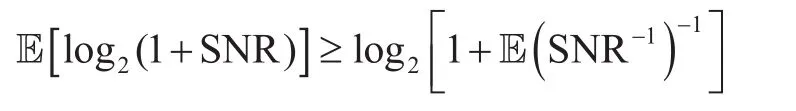
Then we have
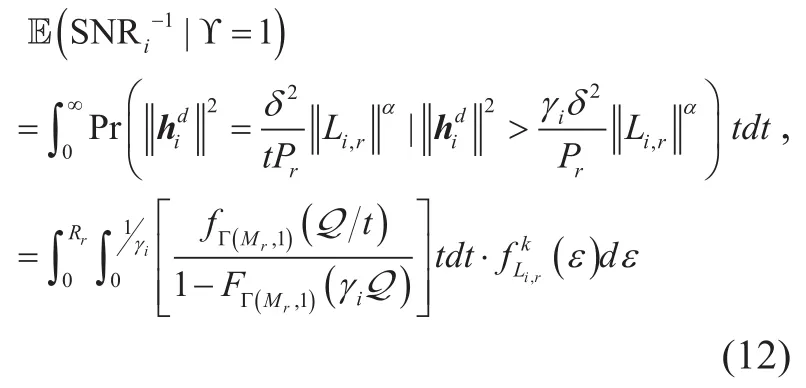
We assume that all the eavesdroppers in daughter processwork independently, thus the most dangerous eavesdropper EVEdangerousis the one with the largest SNR, which needs to be considered.
Lemma4:The CDF of SNR at EVEdangerouscan be expressed as
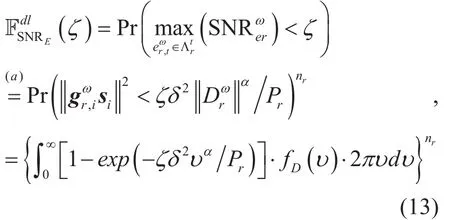
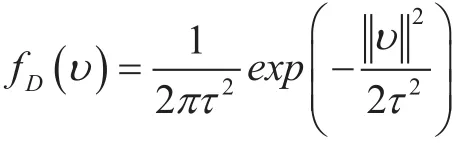
As for the internal curious users, we always notice they have requirements to transmit information in the UL, so the primary goal of non-target users in the DL is to harvest energy to ensure the successful transmission of their UL messages. Therefore, it is reasonable to assume that the internal user Ujturns curious only when it can harvest “sufficient” energy during its allocated slot
Lemma 5:The curiosity probability (CP)that an internal user turns curious can be expressed as (14) shown in the bottom at this page, where Ec serves as the threshold to judge whether the harvested energy is “sufficient” or not.
Similarly, we also consider the most dangerous curious user denoted as CUdangerouson assumption that all the internal users work independently.
Lemma 6:The CDF of SNR at CUdangerouscan be expressed as
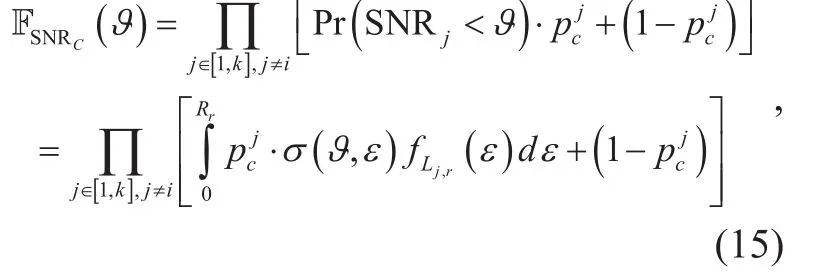
Proof:The random event that an internal user does not obtain confidential information of targeted user can be decomposed into two sub-events, one is that the user does not turn curious and thus no confidential information is decoded; the other is that the curious user attempts to overhear the targeted user, but it cannot decode the confidential information without error. Therefore, the above equation can be obtained by total probability formula.
Then substitute (11), (13), (14) and (15)into (10), the upper bound of DL SOP can be obtained. It can be inferred that the switching threshold influences the SOP by confining the lowest achievable rate of targeted user, which makes SOP a decreasing function of γi.
Furthermore, the overall performance of information transfer in the DL can be characterized by (16) shown in the bottom at next page,where β is the DL period partition coefficient.
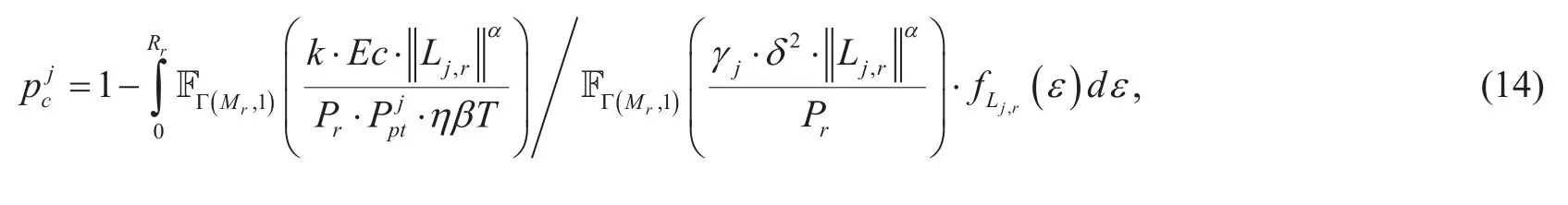
We highlight that the DL STP can be decomposed into two factorsand, where the former represents the achievable secrecy rate when information transfer turns on (later referred to as ASRO)and the latter represents the ADIT. Combined with the monotonicity analysis of ITP, COP and SOP, γiincurs a trade-off between the ASRO and ADIT in DL STP.
B) Power transfer:
As for the cases where SNRicannot meet the switching threshold γi, power transfer will be turned on. The PTP is given bywhich serves as the complementary probability of ITP. In power transfer, the transmitted messages are all public and there is no need to care about the secrecy,hence we only focus on the energy gain at EH users. With TDMA, access users utilize the power transfer period in its own slot as well as the slots assigned to other users to accomplish battery charging.
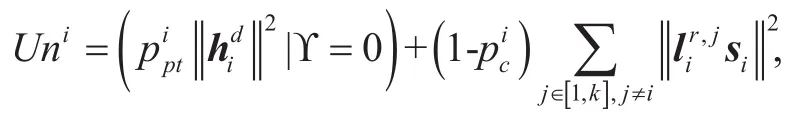
In H-T working mode, all the harvested energy is utilized to transmit UL information. So next, we analyze the secrecy performance of UL transmission.
4.2 User-led on-off transmission protocol
As assumed in Section II, Uitransmits UL message ri(t ) to RCtinwith its harvested energy Ei. With the user-led on-off transmission protocol, ri(t ) will be transmitted only when the energy stored in the battery of Uiis “sufficient” compared to the transmission threshold vi, otherwise the UL transmission will be interrupted.
Lemma 8:The energy outage probability(EOP) that Uidid not harvest “sufficient” energy for UL transmission can be expressed as
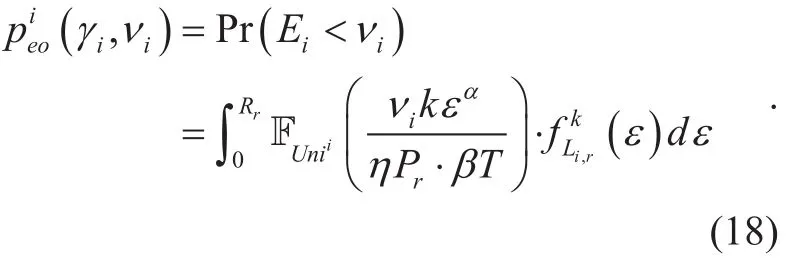
The Transmission Probability (TP) of Uiis given byconfines the minimal energy required for transmission, so TP decreases with the increase of vi.
When Uiturns on the UL transmission, the SNR at RCt, Ujand eavesdroppers around Uican be expressed asandrespectively, where
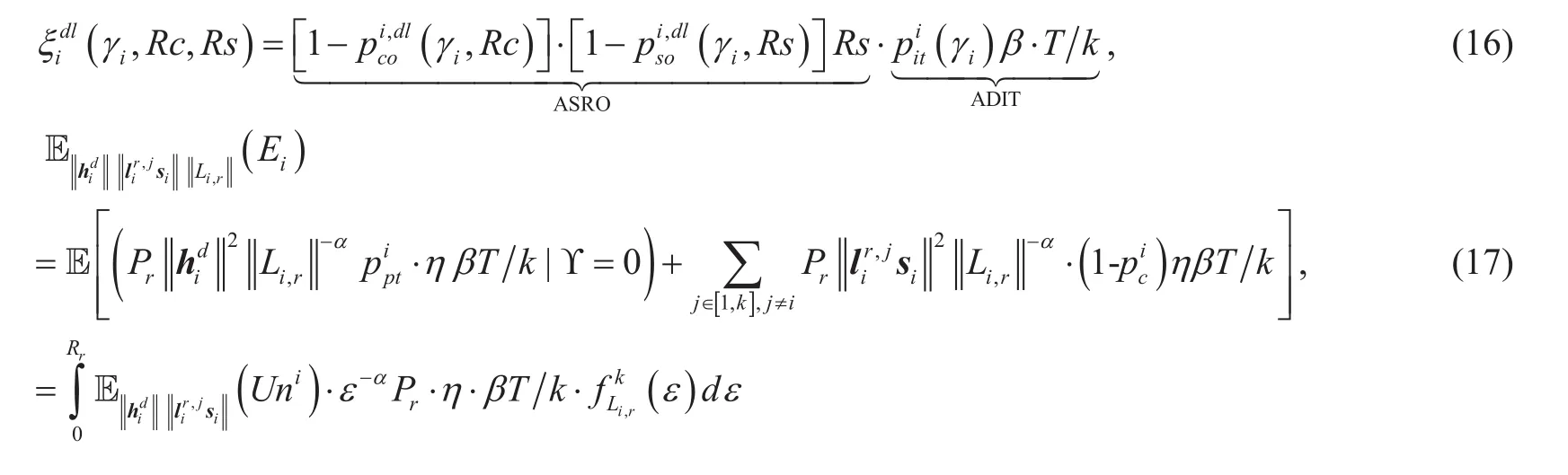
Lemma 9 :The COP of UL transmission incan be expressed as (19) shown in the bottom at this page, where

For the sake of deriving UL SOP, the achievable ergodic rate of RCtand the CDF of SNR at EVEdangerous(around Ui) and CUdangerousinare presented in the following lemmas.
Lemma 10:The lower bound of the achievable ergodic rate of RCtincan be expressed as (21) shown in the bottom at this page.
Lemma 11:The CDF of the SNR at EVEdangerousin daughter processinis given by (22) and (23) shown in the bottom at this page.
In the UL transmission, internal users do not need to harvest energy for storage. Hence we consider the worst case for legitimated users wheretry their best to overhear the UL information of Uiwith pcj=1.
Lemma 12:The CDF of CUdangerousincan be expressed as
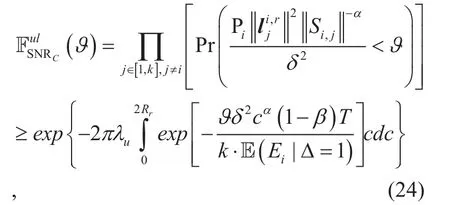
Remarks:Since the distribution ofis rather hard for us to derive, the exact CDF of the largest SNR among all access users is unreachable. We consider an approximate solution. As the service radius of RCtis Rr,the largest distance between any two internal users is 2Rr, thus the circle, radius of which is 2Rrand origin of which is Uican definitely cover all the access users. Whereas some users accessing other RCs may be also involved in the circle, the probability that the SNRs of all the users in this area are inferior toϑshould be lower than, which serves as a lower bound.

In the UL transmission, v influences COP and SOP via the effect onwhich is an increasing function of v, thus it can be inferred that both COP and SOP decrease with v. Substitute (21)-(24) into (10), the upper bound of UL SOP can be obtained, and then the UL STP is given by (25) shown in the bottom at this page, which serves as a lower bound. With UL STP decomposed into two factors, v incurs a trade-off between ASRO and ADIT, which is similar to the case in DL transmissions.
Through above analysis, we discover that the thresholds can promote the secrecy rate(reliability and security) by improving the condition of transmission, which accompanies the reduction in average duration of transmission.While in transmissions, neither too low rate nor too short duration is acceptable, hence the thresholds should be designed carefully to ensure the performance with proposed scheme.
V. SECRECY THROUGHPUT MAXIMIZATION
From previous section, we notice that both the switching and transmission threshold play very important roles in the scheme. To optimize the performance of proposed scheme,in this section, we first design the optimal switching-transmission threshold pair that maximizes the secrecy throughput.
5.1 Optimal algorithm for thresholds design
As mentioned before, the switching threshold γiincurs a trade-off between ASRO and ADIT. Besides, there is also an obvious tradeoff between ADIT and ADPT as they share a common DL period. In view of the positive correlation between ADPT and harvested energy as well as the impact of harvested energy on UL STP, γishould be optimized by considering DL and UL STP simultaneously.

To solve this problem, we have (27) shown in the bottom at this page.
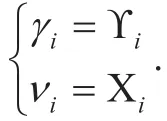
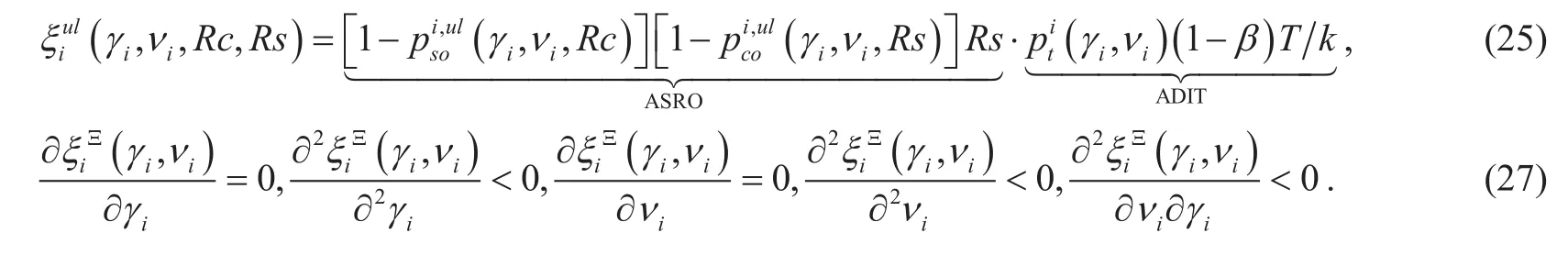

The optimal algorithm of dual-thresholds can be summarized in Table 2.
5.2 Simplified algorithm for thresholds design
With Algorithm 1, we pick out the optimal pair of thresholds by solving a group of quadric inequalities with double unknowns, which still demands the consumption of much computing resource. In order to further release the stress on processing and computing, we simplified previous algorithm at the cost of little loss in secrecy performance.
In this simplified algorithm, we maximize the balanced sum of DL STP and harvestedenergy with due regard to the positive correlation between UL STP and harvested energy.As a result, only the DL transmission needs to be considered when optimizing γi, and the design problem of thresholds can be decomposed into solving two groups of quadric inequalities with only single unknown.

Table II Pseudo-code of the optimal algorithm for designing thresholds
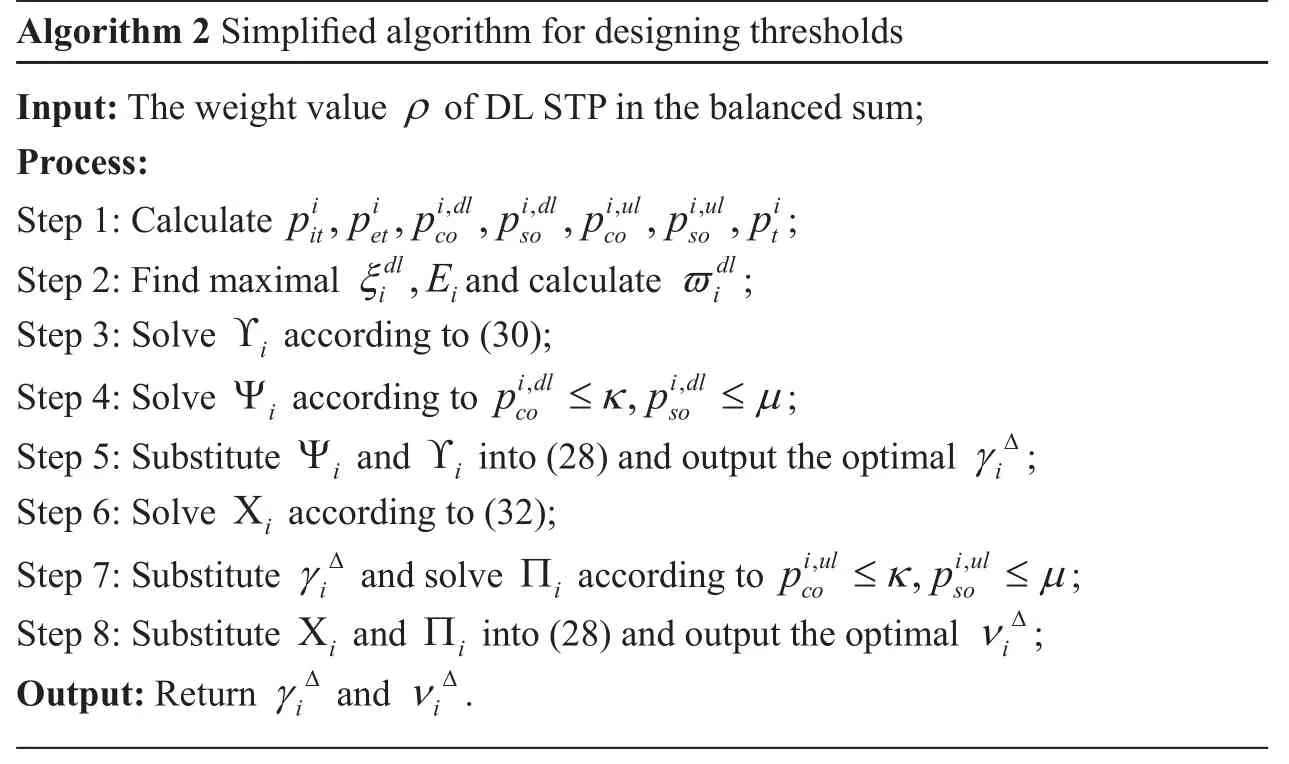
Table III Pseudo-code of the optimal algorithm for designing thresholds
Then the optimization problem of γican be formulated as
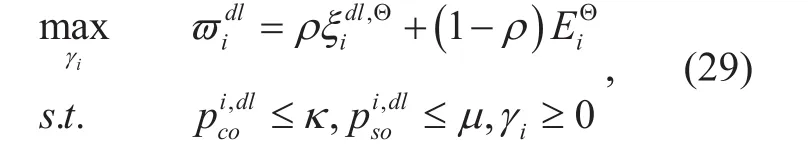
To solve this problem, we have

Based on the determined optimal switching threshold vi, the optimization problem of vican be formulated as

To solve this problem, we have

The simplified algorithm can be summarized in Table 3.
As solving two groups of quadratic inequations with single unknown would be much easier than solving a quadratic inequations group containing two variables, this algorithm is suitable for the cases where the processing capacity of the system is really poor.
Furthermore, we notice that ADIT not only depends on γibut also β according to its definition in section IV, which indicates the partition coefficient of DL-UL period should be carefully considered as well. Therefore,based on the optimal thresholds obtained above, we propose the algorithm for DL-UL partition optimization.
5.3 Algorithm for DL-UL partition design
With the definition of STP modified, the partition coefficient has obvious effects on both DL and UL STP. Specifically, in the DL, the portion of DL period β influences DL STP through ADIT only, so DL STP is a monotonous increasing function of β. While in the UL, β has impacts on UL STP from two different aspects. On the one hand, increasing β can prolong the harvesting time of each user.It will further increase the transmission power in UL and promote the ASRO as a result; on the other hand, lager β leaves shorter time for the UL transmission, which has a reducing effect on UL STP. Therefore, β incurs a tradeoff between ASRO and ADIT in the UL transmission, so we optimize β to further improve the STP.
For the sake of global optimization of β,both DL and UL STP should be considered because they both are functions of β. Meanwhile, taking the equilibrium of DL and UL into account, we still adopt the balanced sum of STP as OPT. However, not like the thresholds that may be diverse at different users, the optimal partition coefficient of DL-UL period should be unique in at least a cycle period and thus should be optimized via comprehensive analysis of all access users. Then the optimization problem can be formulated as

where the constraint L≤β≤U is set to keep it within acceptable ranges.
To solve this problem, we have
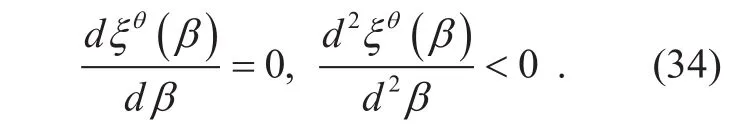
The algorithm of optimizing β can be summarized in Table 4.
VI. SIMULATION RESULTS AND DISCUSSIONS
In this section, we first compare the optimization results of two thresholds with optimal and simplified algorithms to analyze the difference of their performance. Then, we present the numerical results of secrecy throughput toshow the performance improvement by the optimal DL-UL allocation at different users.Finally, we provide the simulation results of both proposed scheme and traditional scheme,to illustrate the validity of our scheme. The results shown in this section are all for the SWIPT system with α=3, Pr=20, Mr=5,Rr=2, δ2=1, λu=0.1, η=0.5, Ec=2,T=1, Rc=4, Rs=1, where the parameters are adopted with full reference to [12], [14],[17] and [22] to keep them within reasonable ranges. When designing the distribution variance of eavesdroppers, we select a relatively small value τ2=0.5 to ensure the dense deployment of eavesdroppers around legitimated nodes, which fully reflects the characteristic of PCP model. As for the value of k, we analyze the PDF of Ntand find that k=5 is most likely to occur with λu=0.1 and Rr=2,which is a representative case and should be considered carefully.
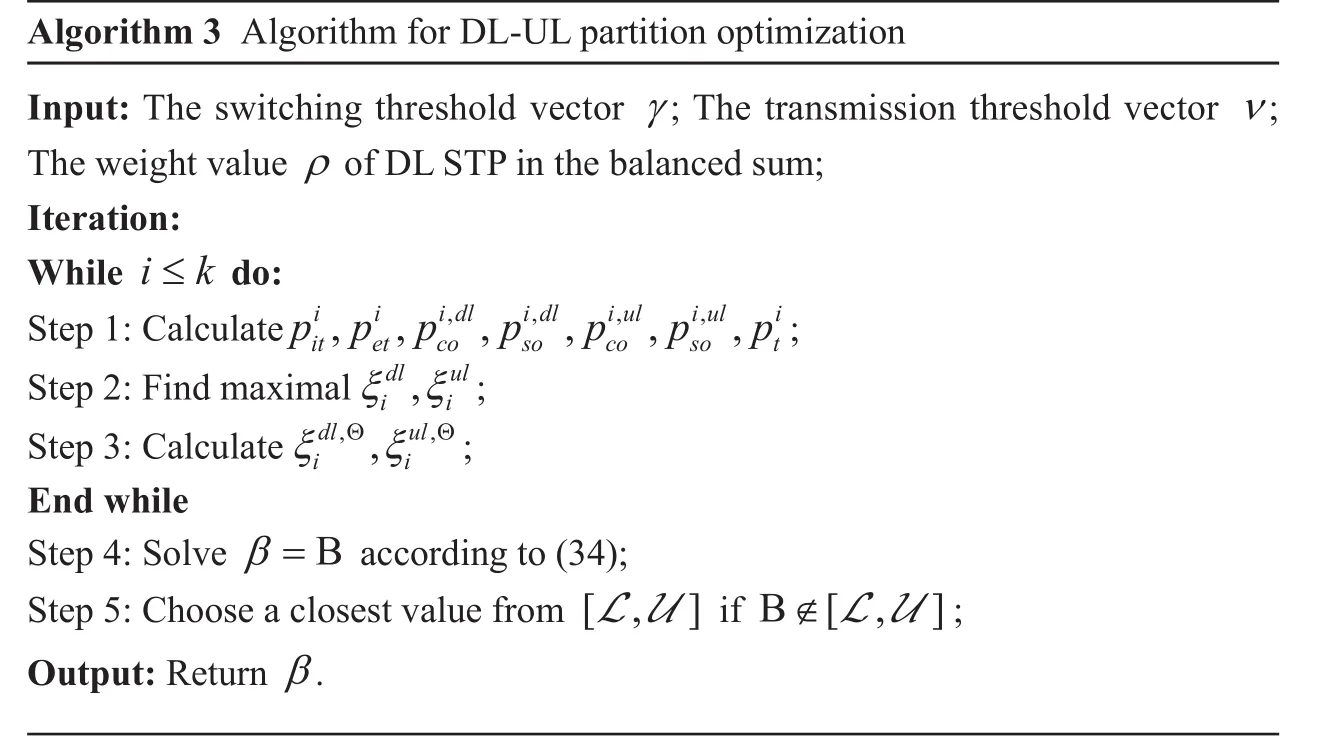
Table IV Pseudo-code of the optimal algorithm for designing DL-UL period coefficient
6.1 The optimization results with the optimal and simplified algorithm
Taking U4as an example, we first plot figure 5 to show the impacts of two thresholds on the balanced sum of normalized STP, which serves as the OPT in algorithm 1. As can be observed, there exists an optimal pair of thresholds (12.5, 0.28) that can achieve the best secrecy performance. From the numerical results shown in figure 6, the theoretical DL STP and UL STP with (12.5, 0.28) set are 5.354×10−3and 6.629×10−3respectively,which add up to 1.1983×10−2.
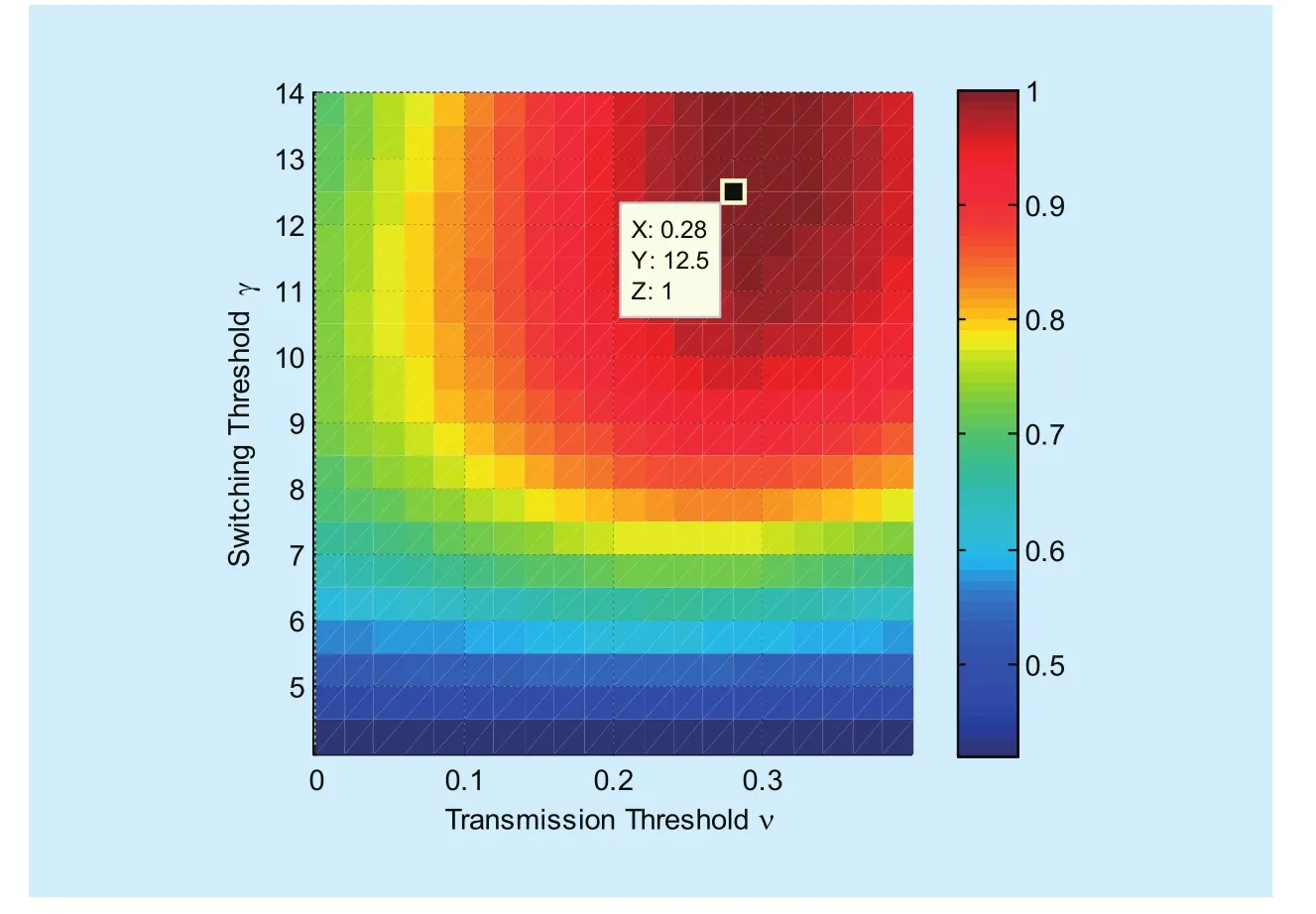
Fig. 5 Optimization results with algorithm 1
While in algorithm 2, we pick out the optimal thresholds due to different OPTs respectively. The switching threshold is optimized in consideration of DL transmission only. As shown in figure 7, the OPT reaches its maximum as γ4=11, and the DL STP arrives 5.607×10−3when setting switching threshold to 11. With switching threshold determined,the transmission threshold is selected according to the UL STP (serving as the OPT in UL) only, which arrives at the maximum 6.049×10−3as v4=0.28. As a result, the sum of STP equals to 1.165×10−2, which indicates a loss of 3% in performance compared to Algorithm 1.
The differences of optimization results can be attributed to that we adopt the tradeoff between harvested energy and ADIT to replace the trade-off between ADIT and UL STP in algorithm 2. Though the harvested energy is positively correlated with the UL STP,their varying rate versus v4may not be quite the same, thus the optimal trade-off may be achieved with differences.
6.2 The eff ect of DL-UL partition coeffi cient
The effects of β on the balanced sum of normalized STP are presented in figure 8. Due to the fact that large-scale fading of wireless channels shows a stronger effect on power transfer than information transfer in the DL transmission, the users that are farther away form RCtare more likely to be lack of power compared to rate, thus they tend to require longer DL durations for harvesting energy to ensure their UL transmission.

Fig. 6 STP versus the two thresholds
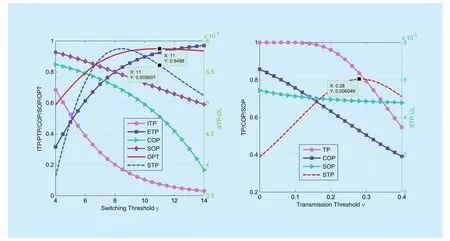
Fig. 7 Optimization results with algorithm 2
6.3 The performance improvement with proposed scheme
Figure 9 depicts the curves of STP (DL, UL and sum) versus the distribution variance of external eavesdroppers, where both theoretical derivations and simulation results are presented. As can be observed, the varying trends of the simulation results are quite consistent with the numerical results, which illustrate the accuracy of our derivations. Meanwhile the simulation results are a little higher than the theoretical curves, which can be contributed to the adoption of lower bounds in our derivations.In addition, the gap between simulation and theoretical curves of UL STP is more obvious than that of DL STP, which is because we use the lower bounds twice as the exact CDF of UL SNR at the most dangerous “Cu” is hard to derive.

Fig. 8 Balanced sum of normalized STP versus the portion of DL period β

Fig. 9 STP versus the distribution variance of eavesdroppers τ2 in dense clusters
Comparing the simulation results of proposed scheme with the thresholds acquired by different algorithms, we notice that two curves are quite close to each other, and algorithm 2 can achieve the subtotal secrecy gain with computational complexity reduced, hence the simplified algorithm is regarded to be a sub-optimal choice when the computational resources are limited. Furthermore, we compare the simulation results of proposed scheme to that of traditional scheme, it can be inferred that the proposed scheme can provide a secrecy gain of at least 57%.
VII. CONCLUSION
This paper studies the physical layer security in SWIPT with TS receivers. We model the random network as PCPs to focus on the severe case where external eavesdroppers hide around certain targets, and the communication model is established via TDMA to enhance energy gain. Based on the model, we propose a secure transmission scheme to improve the secrecy performance with low computational complexity, which includes an opportunistic DIPS protocol designed for the DL and a user-led on-off transmission protocol designed for the UL. Taking both internal curious users and eavesdroppers into account, we analyze the performance with proposed scheme. Then,we optimize the design parameters to achieve maximal STP. Finally, we present numerical and simulation results to illustrate the accuracy of theoretical derivations as well as the validly of proposed scheme. Simulation results show the STP can be promoted by at least 57% with our scheme.
ACKNOWLEDGMENT
This work is supported in part by China High-Tech RD Program (863 Program)SS2015AA011306 and National Natural Science Foundation of China under Grants No.61379006, 61401510, 61501516, 61521003.
[1] LR. Varshney, “Transporting information and energy simultaneously,” Proc. IEEE International Symposium on Information Theory, 2008, pp.1612-1616.
[2] R. Zhang et al., “MIMO broadcasting for simultaneous wireless information and power transfer,” IEEE Transactions on Wireless Communications, vol. 12, no. 5, 2013, pp. 1989-2001.
[3] Y. Zou et al., “A survey on wireless security:Technical challenges, recent advances, and future trends,” Proceedings of the IEEE, vol. 104,no. 9, 2015, pp. 1727-1765.
[4] J. Zhu et al., “Physical-layer security and reliability challenges for industrial wireless sensor networks,” IEEE Access, vol. 5, no. 5, 2017, pp. 5313-5320.
[5] M. Bloch et al., “Physical-layer security: From information theory to security engineering,”Cambridge University Press, 2011.
[6] X. Li et al., “Cooperative communications based on rateless network coding in distributed MIMO systems [coordinated and distributed MIMO],”IEEE Wireless Communications, vol. 17, no. 3,2010, pp. 60-67.
[7] Y. Zou, “Physical-layer security for spectrum sharing systems,” IEEE Transactions on Wireless Communications, vol. 16, no. 2, 2017, pp. 1319-1329.
[8] L. Liu et al., “Secrecy wireless information and power transfer with MISO beamforming”. IEEE Transactions on Signal Processing, vol. 62, no. 7,2014, pp. 1850-1863.
[9] R. Feng et al., “Robust secure beamforming in MISO full-duplex two-way secure communications,” IEEE Transactions on Vehicular Technology, vol. 65, no. 1, 2016, pp. 408-414.
[10] G. Pan et al., “On secrecy outage of MISO SWIPT systems in the presence of imperfect CSI,” Proc. 24th European Signal Processing Conference, 2016, pp. 818-822.
[11] B. Li et al., “Probabilistic-constrained robust secure transmission for energy harvesting over MISO channels,” Science China Information Sciences, vol. 61, no. 2, 2018, pp. 022303.
[12] Z. Chu et al., “Simultaneous wireless information power transfer for MISO secrecy channel,”IEEE Transactions on Vehicular Technology, vol.65, no. 9, 2015, pp. 6913-6925.
[13] W. Wu et al., “Robust downlink beamforming design for multiuser MISO communication system with SWIPT,” Proc. IEEE International Conference on Communications, 2015, pp. 4751-4756.
[14] H. Zhang et al., “Secure transmission scheme for SWIPT in MISO broadcast channel with confidential messages and external eavesdroppers,”Proc. 81stVehicular Technology Conference,2015, pp. 1-5.
[15] MRA. Khandaker et al., “Masked beamforming in the presence of energy-harvesting eavesdroppers,” IEEE Transactions on Information Forensics & Security, vol. 10, no. 1, 2015, pp. 40-54.
[16] Q. Shi et al., “Secure beamforming for MIMO broadcasting with wireless information and power transfer,” IEEE Transactions on Wireless Communications, vol. 14, no. 5, 2015, pp. 2841-2853.
[17] M. Tian et al., “Robust an-aided secure transmission scheme in MISO channels with simultaneous wireless information and power transfer,”IEEE Signal Processing Letters, vol. 22, no. 6,2015, pp. 723-727.
[18] Z. Zhu et al., “Joint optimization of an-aided beamforming and power splitting designs for MISO secrecy channel with SWIPT,” Proc. IEEE International Conference on Communications,2016, pp. 1-6.
[19] B. Li et al., “Secure transmission for heterogeneous cellular networks with wireless information and power transfer,” IEEE Systems Journal,vol. PP, no. 99, 2017, pp. 1-12.
[20] X. Zhang et al., “Enhancing secrecy with multi-antenna transmission in wireless ad hoc networks,” IEEE Transactions on Information Forensics & Security, vol. 8, no. 11, 2013, pp. 1802-1814.
[21] X. Zhang et al., “On the design of artificial-noise-aided secure multi-antenna transmission in slow fading channels,” IEEE Transactions on Vehicular Technology, vol. 62, no. 5, 2013, pp.2170-2181.
[22] PC. Pinto et al., “Secure communication in stochastic wireless networks–part II: Maximum rate and collusion,” IEEE Transactions on Information Forensics & Security, vol. 7, no. 1, 2012,pp. 139-147.
[23] Pillai et al., “Probability, random variables, and stochastic processes,” McGraw-Hill, 2002.
[24] YJ. Chun et al., “Modeling heterogeneous cellular networks interference using Poisson cluster processes,” IEEE Journal on Selected Areas in Communications, vol. 33, no. 10, 2015, pp.2182-2195.
[25] K. Xiong et al.,. “Time-switching based SWIPT for network-coded two-way relay transmission with data rate fairness,” 2014.
[26] H. Liu et al., “Amplify-and-forward full-duplex relay with power splitting-based SWIPT,” 2016.
[27] Q. Sun et al., “Joint beamforming design and time allocation for wireless powered communication networks,” IEEE Communications Letters,vol. 18, no. 10, 2014, pp. 1783-1786.
[28] N. Li et al., “Secrecy outage probability for the multiuser downlink with several curious users,”Proc. Wireless Communications and NETWORKING Conference, 2016, pp. 1-6.
[29] X. Xu et al., “Secure transmission design for cognitive radio networks with Poisson distributed eavesdroppers,” IEEE Transactions on Information Forensics & Security, vol. 11, no. 5, 2015,pp. 373-387.
- China Communications的其它文章
- Design and Implementation of a TDD-Based 128-Antenna Massive MIMO Prototype System
- Symbol Error Rate Performance Analysis of Non-Orthogonal Multiple Access for Visible Light Communications
- On Uplink Non-Orthogonal Multiple Access for 5G:Opportunities and Challenges
- Radio Access Network Slicing Based on C/U Plane Separation
- Contract-Based Content Delivery in 5G Converged Networks
- Clustering of Virtual Network Function Instances Oriented to Compatibility in 5G Network

