IRS Assisted UAV Communications against Proactive Eavesdropping in Mobile Edge Computing Networks
Ying Zhang,Weiming Niu and Leibing Yan
1School of Electronic Information Engineering,Henan Institute of Technology,Xinxiang,453003,China
2Houde College,Henan Institute of Technology,Xinxiang,453003,China
ABSTRACT
In this paper,we consider mobile edge computing(MEC)networks against proactive eavesdropping.To maximize the transmission rate,IRS assisted UAV communications are applied.We take the joint design of the trajectory of UAV,the transmitting beamforming of users,and the phase shiftmatrix of IRS.The original problem is strong non-convex and difficult to solve.We first propose two basic modes of the proactive eavesdropper,and obtain the closed-form solution for the boundary conditions of the two modes.Then we transform the original problem into an equivalent one and propose an alternating optimization(AO)based method to obtain a local optimal solution.The convergence of the algorithm is illustrated by numerical results.Further,we propose a zero forcing(ZF)based method as sub-optimal solution,and the simulation section shows that the proposed two schemes could obtain better performance compared with traditional schemes.
KEYWORDS
Mobile edge computing(MEC);unmanned aerial vehicle(UAV);intelligent reflecting surface(IRS);zero forcing(ZF)
1 Introduction
With the development of communication technology,security issues have received more attention[1–3].Due to the broadcast characteristics of wireless channel,the information transmitted can be easily obtained by non target users[4–6].Due to its unique advantages,namely mobility and flexibility,UAV communication plays a very important role in supporting safe communication.Where traditional base stations cannot cover,UAVs can use their flexibility to provide more effective services[7,8].
Traditional physical layer security technologies focus on improving the confidentiality of received information [9,10],for example,by changing the coding method,using redundant information in the coding to check and interfere,or changing the amplitude and phase of the transmission signal to carry additional information[11–13].Physical layer security technology can improve the security transmission rate of information through pre-designed policies.In recent years,researchers have become more and more aware of possible eavesdroppers in communication scenarios [14–16].More and more eavesdroppers are studying physical layer security technology.At this time,the ability of the eavesdropper is limited to (1) eavesdropping channel; (2) the transmission rate of the sender.As the research on security continues to expand,eavesdroppers have more forms.
However,the security of communication does not only include the above parts,but also the ability of eavesdroppers is evolving.In recent research,the concept of active monitoring was first proposed in [17,18],which aimed to improve the eavesdropping rate through the transmission of Gaussian noise by the eavesdropper; Huang et al.[19] further proposed that the eavesdropper can choose to send Gaussian noise to improve its eavesdropping ability.For the situation of the above intelligent eavesdroppers,a lot of research has not been carried out to counter them[20,21].
IRS is a passive device,which can reconstruct the sender’s signal and enhance or weaken the specific user by changing the channel parameters [22,23].Because of the excellent characteristics of IRS,it has been widely used and studied in secure communication.For example,in[24],the authors proposed to use IRS to assist multi-user communication.By designing the transmission beam and IRS phase shift matrix,the minimum secrecy rate among users was improved.In [25],the authors considered that the IRS would recode the new source transmission signal,that is,the user’s receiving rate and the eavesdropper’s receiving rate could be improved at the same time,it broken through the traditional upper bound of safe rate[26,27].
IRS assisted UAV communication also has a wide range of application scenarios.When UAV is used as air base station,IRS can be used as a ground equipment to improve the effective speed between UAV and users;When the UAV is used as a relay,the communication rate can be improved by adjusting the flight path of the UAV and the phase shift matrix of the IRS.
In this paper,we consider using IRS assisted UAVs to promote the safe communication of ground users.The specific contributions of this paper are as follows:
1.We consider the security in mobile edge computing.We use the IRS auxiliary computing tasks carried by UAV to unload,with the goal of reducing the system delay on the premise of ensuring safe transmission.
2.We preset the working mode of the eavesdropper and propose to control the eavesdropper’s transmitting beam in the form of maximum ratio transmission through the joint design of the transmitting beam of the base station,the flight path of the UAV,and the phase shift matrix of the IRS.
3.We propose an algorithm based on interior point method and alternate optimization,and propose a sub-optimal scheme based on zeroing method with low complexity.
4.In the simulation section,we set a communication environment based on Rayleigh channel,and the positions of users and eavesdroppers are randomly set in each simulation.Simulation results show that the proposed scheme can effectively reduce the latency of mobile edge computing.
In the second section,we establish the original optimization problem; In the third section,we first estimate the transmission strategy of the eavesdropper,and transform the original optimization problem;In the fourth section,we solve the transformed optimization problem and obtain the design scheme by using the interior point method and alternative optimization;In the fifth section,we carry out the simulation experiments,and then the sixth chapter summarizes the full text.
2 System Model and Problem Formulation
In this section,we first introduce the system model,then take the secrecy rate as our optimization goal,and establish the original optimization problem.
2.1 System Model
We consider that the system consists of one user,one proactive eavesdropper,a UAV and an IRS.As shown in Fig.1,the user and the eavesdropper are both equipped with multi-antennas.For the sake of generality,we assume that the channel between UAV and ground users is the superposition of LOS channel and NLOS channel.The IRS containsNIRS elements,each of which can be designed independently to change the channel of the IRS to the user; It is worth noting that the information transmitted by the UAV to each ground user is dual:the UAV itself will forward signals from the user;The IRS will also reflect the signal.The specific expression is proposed as follows:
where yurefers to the signal received at UAV.huand hiuspecifically represent the direct channels from user to UAV and the reflecting link,which defined as follows:
whereαurepresents to the proportion of LOS channels in mixed channels for the user,hu,1and hu,2respectively refer to the channel from the user to IRS and that from IRS to UAV,and G is the phase shift matrix of IRS expressed as
The gain of the LOS channel is only related to the physical distance between users and UAV,which conforms to the general assumption that the farther the distance is,the smaller the channel gain is.The specific formula is as follows:

Figure 1 :System model
Similarly,the channel between the physical distance is calculated as follows:
where (xi,yi) represents the position of UAV at time sloti,(xu,yu) represents the user position,and(xe,ye) represents the eavesdropper position.It is worth noting that the UAV can identify the exact location of users and eavesdroppers through cameras and other external devices,but the channels between users and eavesdroppers is NLOS channel,which is caused by ground shelters.
2.2 Problem Formulation
According to Shannon’s theorem,we can first obtain the user’s reception rate,which can be expressed as
The eavesdropper’s eavesdropping ability can be expressed by its eavesdropping rate,which is defined as
Here,it could be assumed that the information intercepted by the eavesdropper is redundant information used to fill in the received code,i.e.,the secrecy rate could be expressed as
Based on the above discussion,we formulate the optimization problem as
The first constraint indicates that the element dependencies of the IRS should satisfy the legitimacy.The second constraint restricts the transmission power of the base station in each time slot,and the total consumed power of the time slot in the entire communication cycle should also meet the constraint,which is shown in the last constraint.In addition,UAVs will also be constrained by their flight speed.
3 Proposed Solution
In this section,we first want to obtain the transmission strategy of the eavesdropper,that is,the relationship between the transmission vector of the eavesdropper and the optimization variables we propose(the transmission vector of the base station,the flight path of the UAV,and the dependency matrix of the IRS),and then substitute the closed expression into the original problem to realize the conversion of the equivalent problem;then,we solve the original problem by using the interior point method and alternative optimization method.
3.1 Active Eavesdropping Strategy Acquisition
In this section,we simulate the strategies taken by eavesdroppers.Note that we cannot directly design the strategy of the eavesdropper,because we cannot directly interfere with the strategy of the eavesdropper.However,we can potentially affect the sending strategy of the eavesdropper by changing the receiving state of the eavesdropper.
Lemma 1:The transmission beam of the eavesdropper conforms to the following form:
αandβare both parameters and could be obtained via the following equations:
The eavesdropping rate is thus expressed as
Proof.Please refer to Theorem 1 in[18].
According to Lemma 1,it is obvious that the transmission rate of the eavesdropper depends on the received signal and the channel from the UAV to the eavesdropper.When the eavesdropper has a chance to eavesdrop successfully,it maximizes the eavesdropping rate while ensuring the transmission rate;When the eavesdropper is unable to eavesdrop,it will maximize the user’s reception rate,and then the eavesdropper will degenerate into a malicious attacker.
By substituting the results in Lemma 1 into the original problem,we construct the following problem:
In (18),the eavesdropper could successfully eavesdrop on this MEC network.Meanwhile,the user’s secrecy rate is 0.
In the above two problems,we also pay attention to two different situations.The first is that we cannot prevent eavesdroppers from acquiring information.This extreme situation occurs when the channel quality of eavesdroppers is much higher than the receiving channel,and the number of IRS elements is small.Normally,this kind of situation will not happen.Because as long as the transmission beam is controlled in the null space of the eavesdropping channel,eavesdroppers can be completely avoided.Therefore,we will only discuss such cases briefly and then focus on the second case,namely maximizing the security transmission rate.
3.2 Trajectory Design
In this section,we focus on the trajectory design of the UAV when the IRS phase shift matrix and the transmitting beam of the base station are fixed.Let’s first transform the question into the following format:
Note that we can solve the problem iteratively.To be specific,we first set up an initial trajectory,such as the constant speed straight flight of UAV.Then on this basis,we optimize the trajectory step by step,and the iteration method is proposed as follows:
where
Then the original problem could be solved by iterations.
3.3 Beamforming Matrices Design
In this subsection,we would like to obtain the beamforming matrix design for the base station.In specific,we set the trajectory of the UAV and the phase shift matrix of the IRS as fixed setting,and put forward the following problem:
We introduce two variables defined as
The power send by the user could be expressed as
whereh[n]refers to the channel gain innth time slot.
(27)is convex and could be solved by CVX[28].
3.4 Phase-Shift Matrix Design
In this section,we optimize the transmitting beam of the user.We first transform the following problem:
In addition,the above problem is a non-convex objective function composed of coupling variables.In order to convert the molecules of the objective function into concave functions,we consider introducing relaxation variables and using the SCA method.By introducing relaxation variables,the throughput can be rewritten as

Algorithm 3.1:Proposed algorithm
Note that the problem (29) is still non-convex,we choose the lower bound of the optimization objective function[29].At this time,the problem can be transformed into
In order to solve the problem (32),we use the method of first order Taylor expansion and continuous convex approximation.
3.5 Alternate Optimization Algorithm Design
In this subsection,we summarize the above algorithm process and propose an overall algorithm based on alternative optimization.In our algorithm,we mainly include the nesting of three subproblems.In the trajectory optimization of UAV,we use a small iterative method.After iterative convergence,it is added into the loop composed of the phase shift matrix of the IRS and the transmitting beam of the base station.
Due to the high coupling between variables,the convergence of the algorithm is given by simulation experiments.
4 Sub-Optimal Solution
In this section,we propose a suboptimal solution based on the zeroing method and analyze its computational complexity expenditure,which has a lower computational cost compared with the iterative algorithm.
4.1 Zeros-Force Method
In this subsection,we propose a suboptimal solution to the original problem,that is,by controlling the transmitting beam of the base station and the phase shift matrix of the IRS,the eavesdropper’s receiving beam is limited to its zero space.At this point,an additional constraint needs to be added and the optimization problem needs to be rewritten as follows:
To solve this problem,we divide the problem into two sub-problems.In the first sub-problem,we focus on the design of the transmission beam of the base station and the phase shift matrix of the IRS,and rewrite it as
In the second sub-problem,we focus on the flight path design of UAV.It is worth noting that we only need to pay attention to its impact on the safety rate when designing the flight path of UAV.
We finally get a simplified problem,and then we can use the interior point method to solve it by iteratively solveMiandθas in the AO-based scheme.
Further,we obtain the following algorithm with ZF based method.
5 Complexity Analysis
We focus on the complexity of proposed schemes and two traditional schemes:MRT scheme and OA algorithm.As shown in Table 1,note that MRT scheme gets the minimum complexity since it has a closed-form solution.The proposed sub-optimal get less complexity than the optimal scheme.
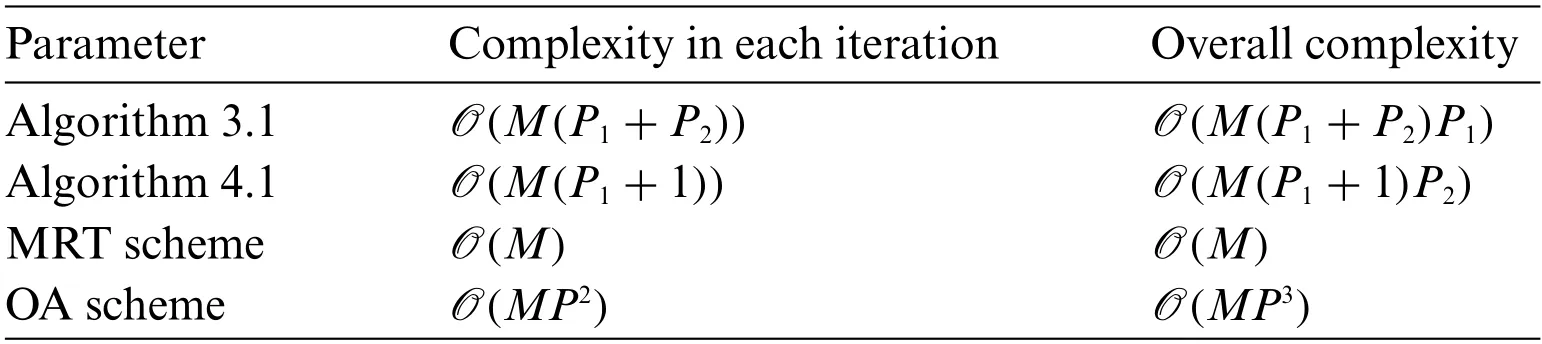
Table 1 : Complexity analysis
6 Discussion
We designed the transmission power of the base station,the flight path of the UAV,and the reflection matrix of the IRS to maximize the safety rate for scenarios with intelligent eavesdroppers.In view of the different working modes of the eavesdropper,we first analyze the rationality of the design scheme and then propose the scheme based on the interior point method and alternative optimization,as well as the sub-optimal scheme based on zero space.
The reason why we are targeting the scene of intelligent eavesdroppers is that with the development of communication technology,especially the widespread concern about secure communication,more and more emerging technologies may also be used by criminals.We need to guard against such active eavesdroppers.

Algorithm 4.1:Proposed algorithm
There is still much to be learned about the confrontation of intelligent eavesdroppers.Although we only focus on some idealized scenarios in this article,we still put forward many constructive suggestions,such as adopting different strategies for the working mode of eavesdroppers and how to design a low-complexity scheme.With regard to multi-user design and more working modes of eavesdroppers,we leave the work for the future.
7 Numerical Results
In this section,we first list the parameters required for the simulation environment as shown in Fig.2,then simulate the results under different settings,and analyze the advantages of the proposed algorithm.
7.1 Simulation Parameters
In this subsection,we build the simulation environment.The UAV flies at a fixed altitude,and its starting and ending points are fixed.The air-to-ground channel is composed of NLOS and LOS channels.The ground channel is NLOS channel,and the location of users and eavesdroppers is known.The specific parameters are shown in Table 2.

Table 2 : Simulation parameters

Figure 2 :Simulation area
7.2 Simulation Results
In this section,we conducted simulation experiments on the proposed scheme,mainly including(1)the proposed scheme;(2)the proposed sub-optimal scheme;(3)the maximum rate scheme;(4)the scheme against potential eavesdroppers; (5) no IRS scheme; (6) the fixed IRS scheme.The specific results are as follows.
We first pay attention to the convergence of the proposed algorithm,that is,the proposed iterative algorithm.As we stated earlier,the convergence of the algorithm is obtained through simulation experiments.As shown in Fig.3,the convergence rate of our proposed algorithm is slightly different at different initial points,but they all converge within 10 times.The convergence speed is equivalent to the scheme for dealing with silent listeners.However,the figure shows that the safety rate of convergence is higher than that of the comparison scheme.We will conduct more simulation experiments in the future to prove the superiority of our proposed scheme.
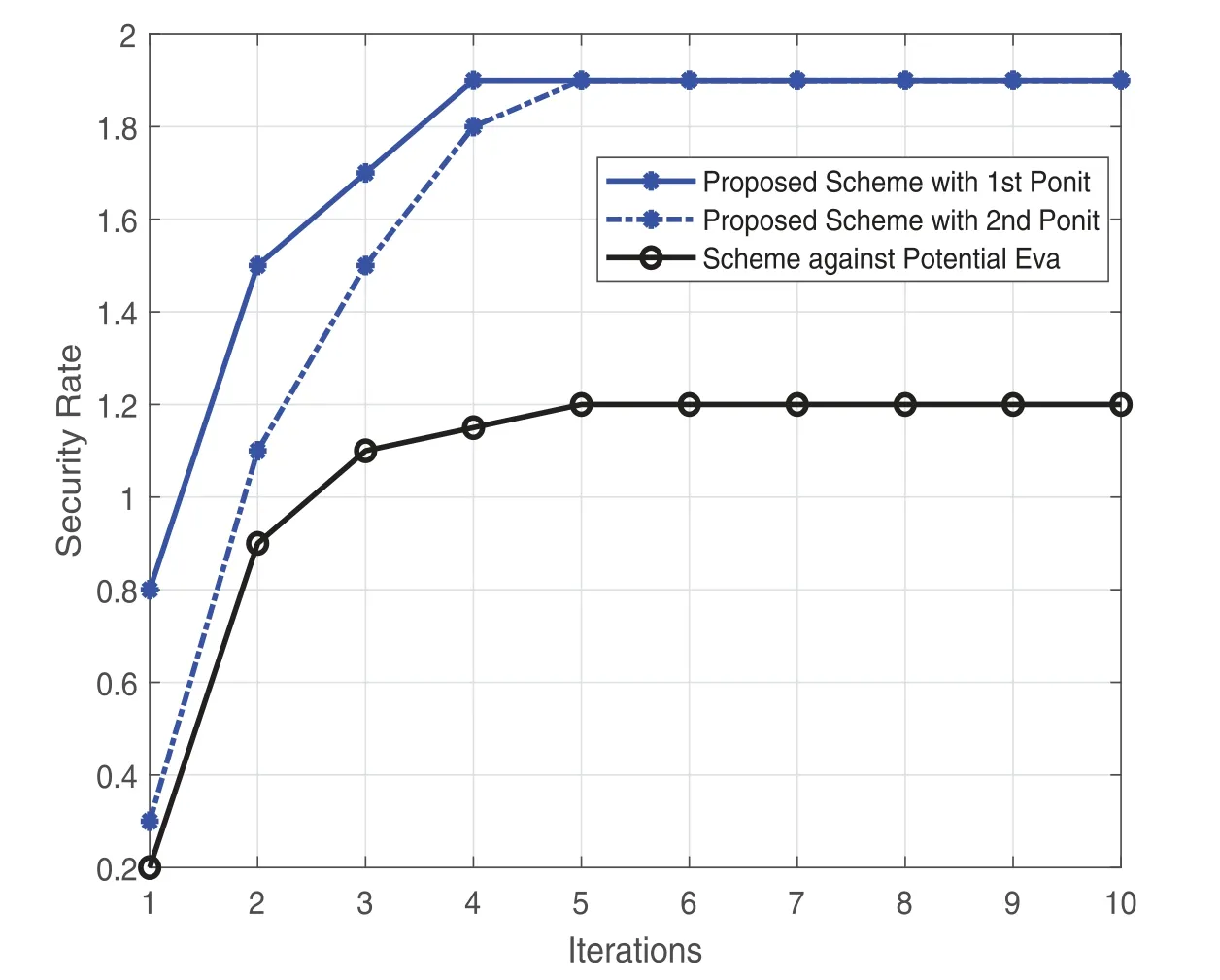
Figure 3 :Convergence of the proposed algorithm
We focus on the flightpath of the UAV in Fig.4.Since the initial point and end point of the UAV are not the same points,we limit the UAV path to a straight line.At this time,the UAV is dense at some points and sparse atother places.Specifically,when the position of the UAV can be adapted to the phase control of the IRS,its flight speed will be reduced to extend the time it stays in the dominant area.It is worth noting that the UAV cannot stay at a certain point for a long time,and hovering will consume more energy andlose the ability to face multiple users.
Figure 4 :Trajectory of UAV
We also focused on the impact of the number of IRS elements on the security rate in Fig.5.IRS plays a very important role in our proposed scheme.As an important indicator that directly affects the performance of IRS,the number of IRS elements deserves our further attention.Of course,the more elements of the IRS,the better.However,because there is a certain distance between the elements of the IRS,more elements may bring load pressure and security risks.We consider a reasonable range,that is when the number of IRS elements increases from 20 to 100.

Figure 5 :Security rate vs.the number of elements of IRS
In Fig.6,we show the curve of the secrecy rate changing with user power.When the user power increases,the security rate also increases.It is worth noting that the MRT scheme in the curve crosses the curve without IRS.This is because when the user power is low,the MRT scheme can ensure a higher transmission rate,thus achieving better security.When the user power increases,the MRT scheme is not flexible enough.Although the scheme without IRS can not gain from IRS,it can gain ga by adjusting the user’s transmitted beam.
We show the relationship between safety rate and noise power in Fig.7.Noise power is the background white noise that cannot be avoided in the communication process.It will not only reduce the rate of legal communication but also reduce the eavesdropping ability of eavesdroppers.However,in our proposed scheme,with the increase of noise power,the decrease in secrecy rate is the smallest,which shows that our proposed scheme can still ensure a higher safety rate in a very noisy and harsh environment.
In traditional eavesdropping scenarios,the power of the eavesdropper is not concerned,because when the eavesdropper is silent,the power of the eavesdropper cannot affect the entire communication system.However,when the eavesdropper is proactive eavesdropping,the increase of eavesdropping power will reduce the security of the system.As shown in Fig.8,with the increase in eavesdropper power,the security rate will also decrease.It is worth noting that when the power of the eavesdropper increases,it will increase the interference to the communication link,thus reducing the security rate.

Figure 6 :Security rate vs.power of base station
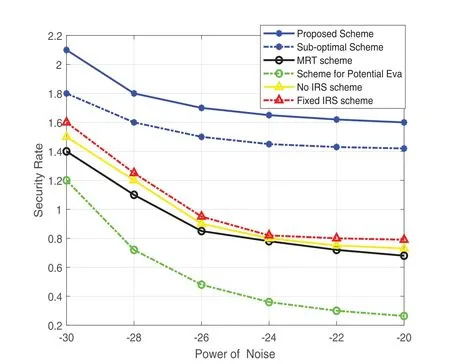
Figure 7 :Security rate vs.power of noise
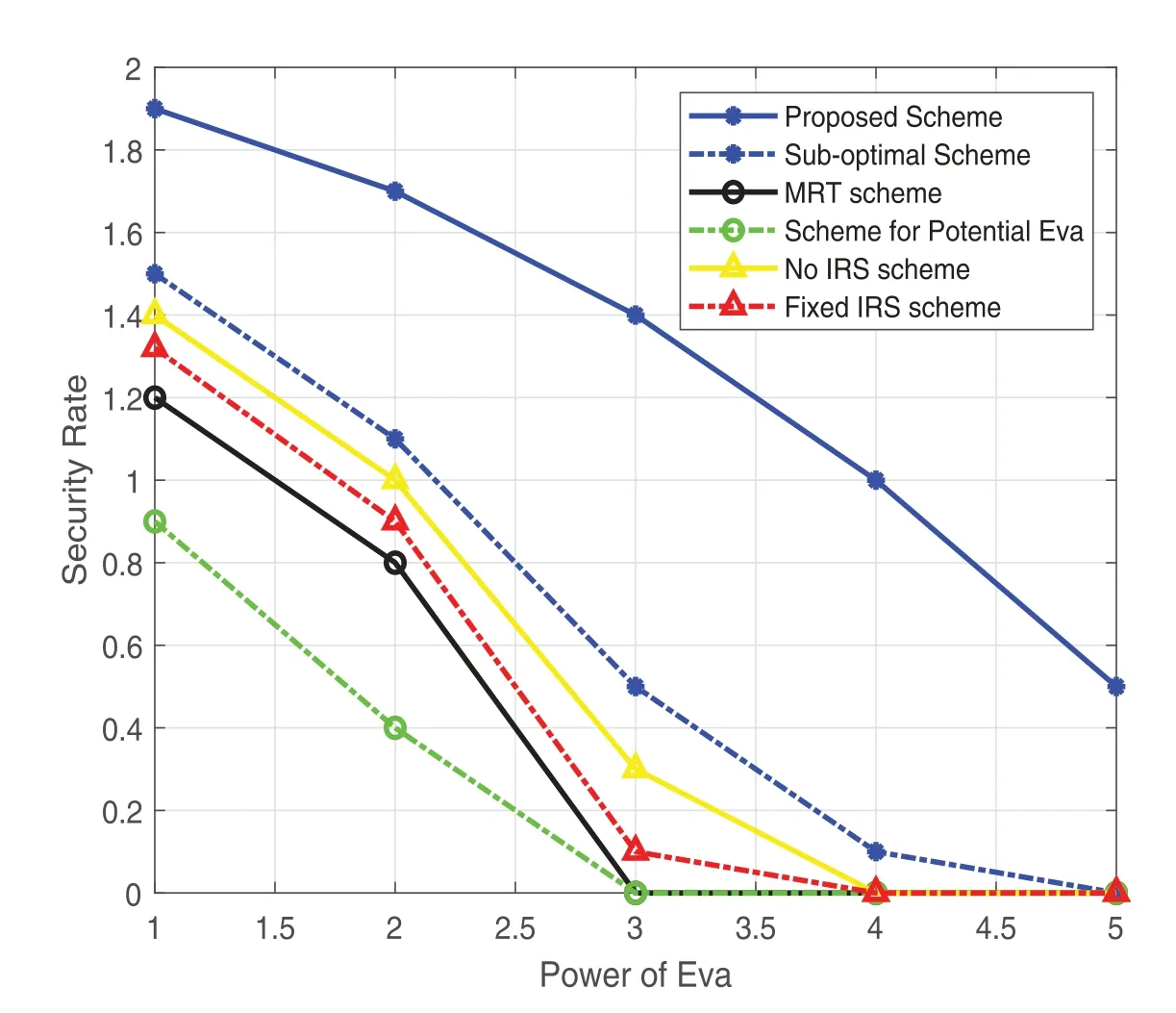
Figure 8 :Security rate vs.power of eavesdropper
8 Conclusion
In this paper,we designed the transmitting beam of the user,the trajectory of the UAV,and the phase shift matrix of the IRS to maximize the user’s secrecy rate.We analyzed the two working modes of the eavesdropper and potentially controlled its transmitting beam.We added the influence factor of the eavesdropper as an optimization variable into the design scheme and proposed a local optimization scheme based on the interior point method and alternative optimization.In addition,we designed a suboptimal scheme based on the zero forcing method to reduce the computational complexity.The simulation results showed that the proposed iterative scheme is superior to the suboptimal scheme and has a higher secrecy rate than the existing schemes.
Acknowledgement: The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement: This work was supported by the Key Scientific and Technological Project of Henan Province(Grant Number 222102210212),Doctoral Research Start Project of Henan Institute of Technology(Grant Number KQ2005)and Key Research Projects of Colleges and Universities in Henan Province(Grant Number 23B510006).
Author Contributions:The authors confirm contribution to the paper as follows:study conception and design:Ying Zhang;data collection:Weiming Niu;analysis and interpretation of results:Leibing Yan.All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials:All data is synthesized using MATLAB and the generation method is described in detail in the simulation section.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computer Modeling In Engineering&Sciences2024年1期
Computer Modeling In Engineering&Sciences2024年1期
- Computer Modeling In Engineering&Sciences的其它文章
- Review of Recent Trends in the Hybridisation of Preprocessing-Based and Parameter Optimisation-Based Hybrid Models to Forecast Univariate Streamflow
- Blockchain-Enabled Cybersecurity Provision for Scalable Heterogeneous Network:A Comprehensive Survey
- Comprehensive Survey of the Landscape of Digital Twin Technologies and Their Diverse Applications
- Combining Deep Learning with Knowledge Graph for Design Knowledge Acquisition in Conceptual Product Design
- Meter-Scale Thin-Walled Structure with Lattice Infill for Fuel Tank Supporting Component of Satellite:Multiscale Design and Experimental Verification
- A Calculation Method of Double Strength Reduction for Layered Slope Based on the Reduction of Water Content Intensity
