Secure and Reliable Routing in the Internet of Vehicles Network:AODV-RL with BHA Attack Defense
Nadeem Ahmed ,Khalid Mohammadani ,Ali Kashif Bashir ,Marwan Omar ,Angel Jones and Fayaz Hassan
1School of Electronic Science,Beijing University of Post and Telecommunication,Beijing,100086,China
2Department of Computer Science,Huanggang Normal University,Huanggang,China
3Department of Computing and Mathematics,Manchester Metropolitan University,Manchester,UK
4Woxsen School of Business,Woxsen University,Hyderabad,502345,India
5Department of Computer Science and Mathematics,Lebanese American University,Beirut,Lebanon
6Information Technology and Management,Illinois Institute of Technology,Chicago,USA
7College of Computing,Capital Technology University,Laurel,USA
ABSTRACT Wireless technology is transforming the future of transportation through the development of the Internet of Vehicles(IoV).However,intricate security challenges are intertwined with technological progress:Vehicular ad hoc Networks (VANETs),a core component of IoV,face security issues,particularly the Black Hole Attack (BHA).This malicious attack disrupts the seamless flow of data and threatens the network’s overall reliability;also,BHA strategically disrupts communication pathways by dropping data packets from legitimate nodes altogether.Recognizing the importance of this challenge,we have introduced a new solution called ad hoc On-Demand Distance Vector-Reputation-based mechanism Local Outlier Factor (AODV-RL).The significance of AODVRL lies in its unique approach: it verifies and confirms the trustworthiness of network components,providing robust protection against BHA.An additional safety layer is established by implementing the Local Outlier Factor(LOF),which detects and addresses abnormal network behaviors.Rigorous testing of our solution has revealed its remarkable ability to enhance communication in VANETs.Specifically,Our experimental results achieve message delivery ratios of up to 94.25%and minimal packet loss ratios of just 0.297%.Based on our experimental results,the proposed mechanism significantly improves VANET communication reliability and security.These results promise a more secure and dependable future for IoV,capable of transforming transportation safety and efficiency.
KEYWORDS Black hole attack;IoV;vehicular ad hoc network;AODV routing protocol
1 Introduction
The rapidly evolving Internet of Vehicles (IoV) field encompasses a transformative paradigm that has revolutionized vehicular communication and connectivity.IoV integrates many technologies,enabling vehicles to interact seamlessly with each other and the surrounding environment [1].This interconnected ecosystem involves VANETs and extends its connectivity to sensor networks,cloud computing,and other emerging technologies.IoV is built upon leveraging advanced sensing capabilities,where sensors [2] in vehicles capture real-time data about their surroundings.These sensors enable vehicles to gather information regarding traffic conditions,road hazards,and other relevant parameters,fostering a comprehensive understanding of the transportation ecosystem.This rich sensory data is then processed and analyzed using cloud computing infrastructure,which enables intelligent decision-making and efficient resource allocation[3].Fig.1 provides a a holistic view of the inter-connectivity within the IoV framework.

Figure 1:Typical diagram of IoV
It illustrates the intricate network of communication links,each representing a distinct interaction between vehicle to sensors,vehicles to infrastructure,vehicle to vehicle,vehicle to internet clouds,and vehicle to personal devices [4].These links exemplify the seamless flow of information within the IoV ecosystem,demonstrating the collaborative efforts of sensors,cloud infrastructure,VANETs,and other technologies.Vehicular ad hoc Networks (VANETs) are a crucial component of the Internet of Vehicles (IoV) [5],enabling dynamic communication links between vehicles and infrastructure.VANETs facilitate two modes of communication:vehicle-to-vehicle(V2V)and vehicleto-infrastructure(V2I),utilizing the IEEE 802.11p standard for wireless connectivity[6].V2V communication involves the real-time exchange of information between nearby vehicles,enhancing safety and efficiency through collective awareness.V2I communication connects vehicles with Roadside Units(RSUs),forming the VANET infrastructure.RSUs provide access to traffic management information,signals,and navigation services,empowering vehicles to make informed decisions[7].
Fig.2 illustrates the interconnectedness between vehicles and infrastructure,demonstrating the seamless flow of information within the VANET infrastructure.This visual representation highlights the collaborative efforts between vehicles and the infrastructure to optimize transportation systems within the IoV framework By leveraging V2V and V2I communication,enabled by technologies like IEEE 802.11p,VANETs enhance collective awareness,improve road safety,optimize traffic flow,and deliver intelligent transportation services[8].As depicted in Fig.2,these communication links foster a connected and intelligent transportation ecosystem by facilitating the exchange of critical information between vehicles and the infrastructure.
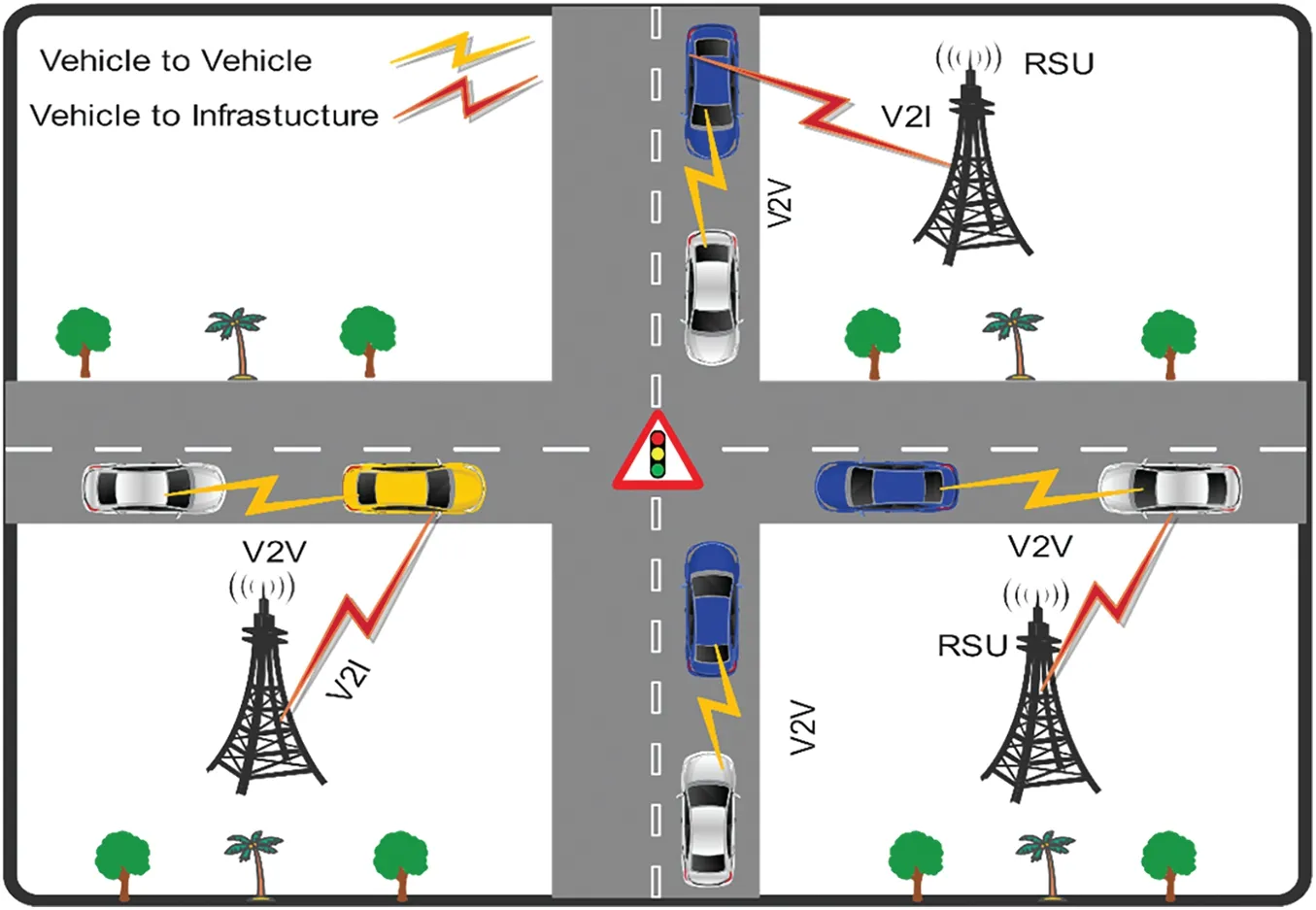
Figure 2:VANET diagram and its components
1.1 Challenges in Maintaining Reliable Message Transmission Quality in VANETs and Mitigation Strategies
Maintaining reliable message transmission in VANETs is critical for supporting various applications [9].Specialized routing protocols [10] and security procedures are necessary for VANETs to enable reliable and secure communication because of the rapid mobility of vehicles,frequent topology changes,and security threats [11].However,several other challenges affect message transmission quality [12],including high mobility [13],limited communication range,interference from other wireless systems,channel fading and shadowing,network congestion[14,15],and security and privacy threats [16].Addressing these challenges requires the development of efficient communication protocols,resource management strategies,security,and privacy mechanisms,and Quality of Service (QoS) mechanisms tailored to the unique characteristics of VANETs [17].Techniques such as adaptive modulation and coding,channel scheduling,and cooperative communication can also improve message transmission quality in VANETs [18].Message accuracy refers to the degree to which a message conveys the intended information without errors or distortions.However,maintaining message accuracy in VANETs is a challenging task due to numerous factors such as noise,signal interference,errors or distortions in the message,spoofing[19],jamming[20],relay attacks[21],and BHA [22],which can be caused by malicious attackers.Such factors can lead to inaccuracies in the message content,resulting in incorrect routing decisions,traffic congestion,and unsafe driving situations.To address these challenges,it is crucial to develop efficient communication protocols,error detection and correction mechanisms,and quality of service mechanisms tailored to the unique characteristics of VANETs.Additionally,it is essential to consider potential attackers and develop solutions to mitigate their impacts,such as intrusion detection systems [23],reputation-based trust management systems[24],and secure routing protocols.By implementing measures to ensure message accuracy and security,VANETs can provide a secure and reliable communication framework for various applications,such as traffic management,emergency response,and autonomous driving.Consistency of behavior is a significant challenge in dynamic environments such as VANETs.Nodes in VANETs can move in and out of the communication range [18],affecting their behavior over time.Additionally,nodes may have limited resources,such as battery power or processing capabilities,which can affect their behavior.Inconsistent behavior can lead to a lack of trust and affect the overall reliability of the network.In addition,inconsistent behavior can also lead to routing loops,incorrect routing decisions,and security threats[25].Therefore,it is essential to develop mechanisms to monitor and evaluate behavior consistency in VANETs and incorporate this factor into the trust score equation.By doing so,nodes that exhibit consistent behavior can be given a higher trust score,contributing towards the development of a secure and reliable communication framework in VANETs.The Table 1 contains the list of abbreviation.
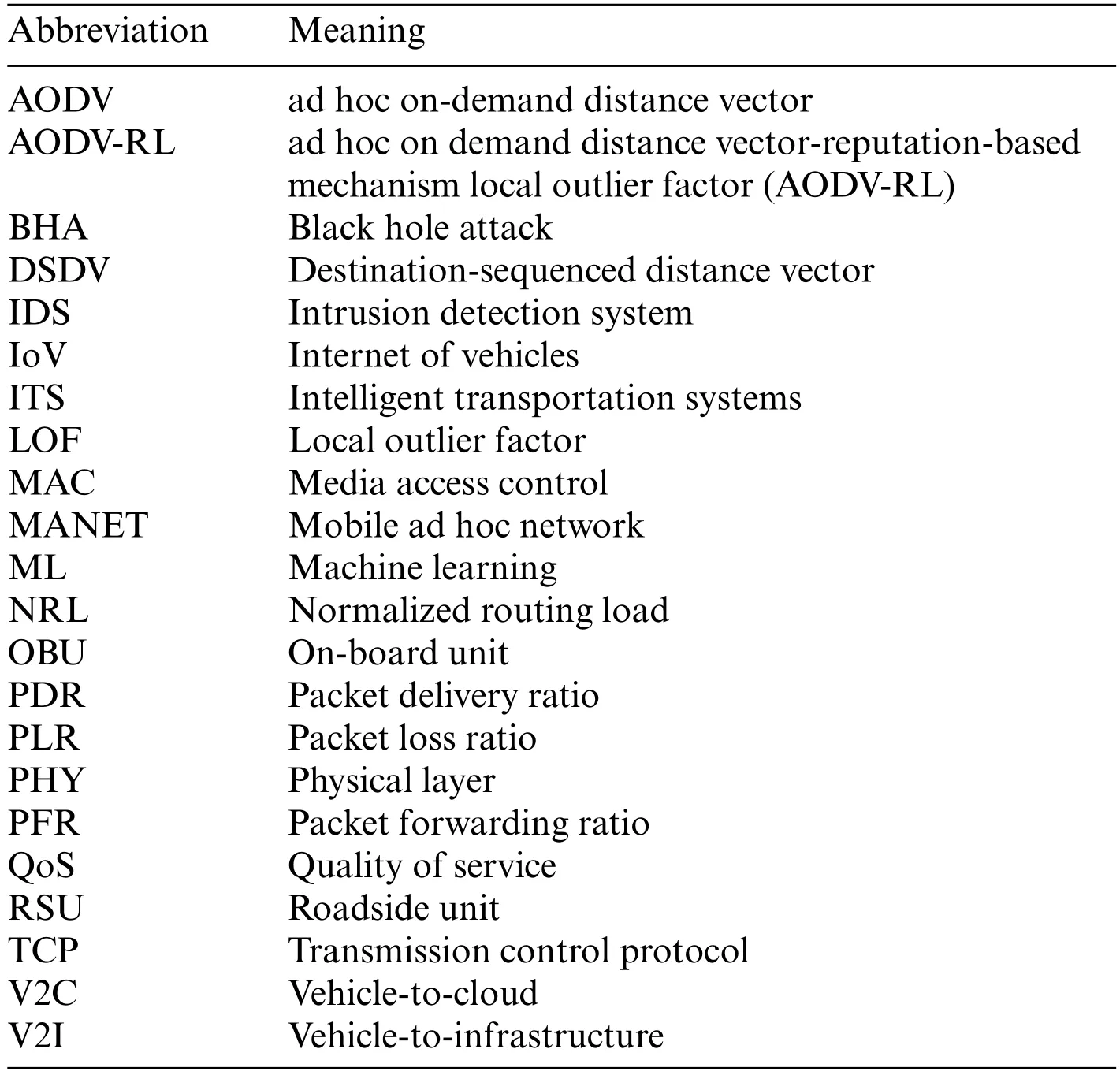
Table 1: List of abbreviation
1.1.1ChallengesandVulnerabilitiesAddressedbyAODV-RL
ad hoc On Demand Distance Vector-Reputation-based mechanism Local outlier factor(AODVRL)addresses the challenges and vulnerabilities associated with securing communication in VANETs[8],which are related to the presence of malicious nodes that can launch attacks such as BHA[17],causing communication disruptions in the entire network [17].To mitigate these risks,AODVRL uses a reputation-based mechanism that assigns reputation scores to nodes based on their past behavior.Nodes with low reputation scores or flagged as potential outliers by the LOF algorithm are avoided as potentially malicious.This mechanism enhances the security of communication in VANETs by identifying and avoiding potentially malicious nodes.AODV-RL effectively mitigates the risks associated with BHA attacks and other malicious activities in VANETs by using a reputationbased mechanism and LOF algorithm,ensuring the security and reliability of communication in the network.
1.2 Unique Contributions and Implications
Different from traditional routing protocols,our research is novel that enhances the security and reliability in VANET using reputation-based and Local Outlier Factor(LOF)based mechanism.The key contribution of our proposed research are given below:
a) The study proposes a new secure and modified version of the AODV routing protocol for VANET secure communication.The proposed protocol,called AODV-RL,enhances the existing AODV protocol with reputation and Local Outlier Factor(LOF)-based mechanisms to improve the reliability and security of communication in VANETs.
b) The novelty of AODV-RL lies in its ability to address the limitations of existing routing protocols in VANETs.By considering the dynamic topology changes and trustworthiness of nodes (Node Trust Score),AODV-RL provides a more effective and efficient routing solution for detecting malicious nodes in VANET applications.Additionally,the integration of reputation and LOF-based mechanisms allows AODV-RL to identify and isolate malicious nodes in the network,enhancing the security and reliability of communication in VANETs.
c) The significance of AODV-RL is in its potential to enable reliable and secure communication in VANETs for various safety-critical applications.The protocol has been evaluated using simulation experiments under dynamic traffic load scenarios.
d) We compare different AODV-based routing protocols;results are analyzed with our designed routing protocol.The results show that AODV-RL outperforms existing routing protocols regarding Packet Delivery ratio,packet loss ratio,network routing load,and throughput,demonstrating its effectiveness in improving the reliability and security of communication in VANETs.
1.3 Background of Routing Protocols Used in VANETs
Routing protocols are a crucial aspect of wireless networks [6],as they allow for efficient data communication across the network.These protocols determine the optimal path for data to travel across the network based on network topology,link quality,and traffic congestion.Routing protocols intended for VANETs,such as AODV(ad hoc On-Demand Distance Vector)and OLSR(Optimized Link State Routing),are specifically designed to address challenges such as high mobility and frequent changes in network topology such as VANETs and Mobile ad hoc Networks (MANETs) [26],with distinctive features and requirements reflected in their routing protocols [27,28].Below are the two main types of routing protocols;there are two types of routing protocols,one is proactive routing protocol,and other is the reactive routing protocol.
1.4 AODV Routing Protocol
AODV is a reactive routing protocol for wireless ad hoc networks with no fixed infrastructure or centralized control[29,30].AODV is designed to establish and maintain routes on demand,as needed,in response to specific requests from source nodes.AODV establishes the communication links by using route discovery procedures.The route discovery steps of AODV are as follows,when a source node needs to send data to a destination node,it first broadcasts a Route Request (RREQ) packet,which contains the address of the destination node [31].Each node that receives the RREQ packet forwards it to its neighbors until the packet reaches the destination node or a node that has a route to the destination node in its routing table.When the destination node receives the RREQ packet,it sends a Route Reply (RREP) packet back to the source node,containing the address of the nexthop node on the route to the destination.Once the source node receives the RREP packet,it sends data packets to the destination node using the route specified in the RREP packet [26].The nodes along the route update their routing tables to reflect the new route,and the route is maintained if data packets are sent.If the route is not used for a certain period,it is removed from the routing tables.In the context of VANET,the traditional AODV routing protocol is considered unsecured due to its lack of a monitoring mechanism for security[31].While AODV has a route-maintained procedure that identifies broken links,it does not monitor the behavior of nodes,leaving the network vulnerable to attacks.Therefore,new novel secure techniques are required to ensure secure communication in VANETs,such as the use of cryptographic methods to authenticate and encrypt messages,intrusion detection systems,an anomaly detection method,e.g.,Local Outlier Factor (LOF),and trust management systems to monitor the behavior of nodes and ensure the reliability of the network.By employing these new techniques,VANETs can become more secure and reliable for their intended applications.
The rest of this paper is organized as follows:Section 2 introduces the related work,providing an overview of existing research in the field.Section 3 presents the materials and methods employed in this study,including a detailed explanation of the system model.Section 4 describes the experimental design and simulation setup used to validate our approach.Subsequently,Section 5 presents the results obtained from our experiments,offering comprehensive data analysis.Finally,in Section 6,we draw conclusions based on our findings and discuss future directions for research.
2 Related Work
This section consists of two subsections.The first subsection includes background information on routing protocols in VANETs,focusing on the AODV protocol.The AODV protocol is frequently used in VANETs[32];however,its drawbacks render it susceptible to assaults and lower its dependability in dynamic network situations.The second part examines the current research on secure routing techniques for VANETs.The literature study underlines the problems of building safe and reliable routing protocols for VANETs and explores many ways to meet these issues.These methods include reputation-based processes,trust management systems,and machine learning strategies [33].The literature study offers valuable context for the proposed AODV-RL protocol,which upgrades the current AODV protocol with reputation and Local Outlier Factor(LOF)-based methods to increase the reliability and security of communication in VANETs.
2.1 Literature Review on Secure Routing Protocols for VANETs
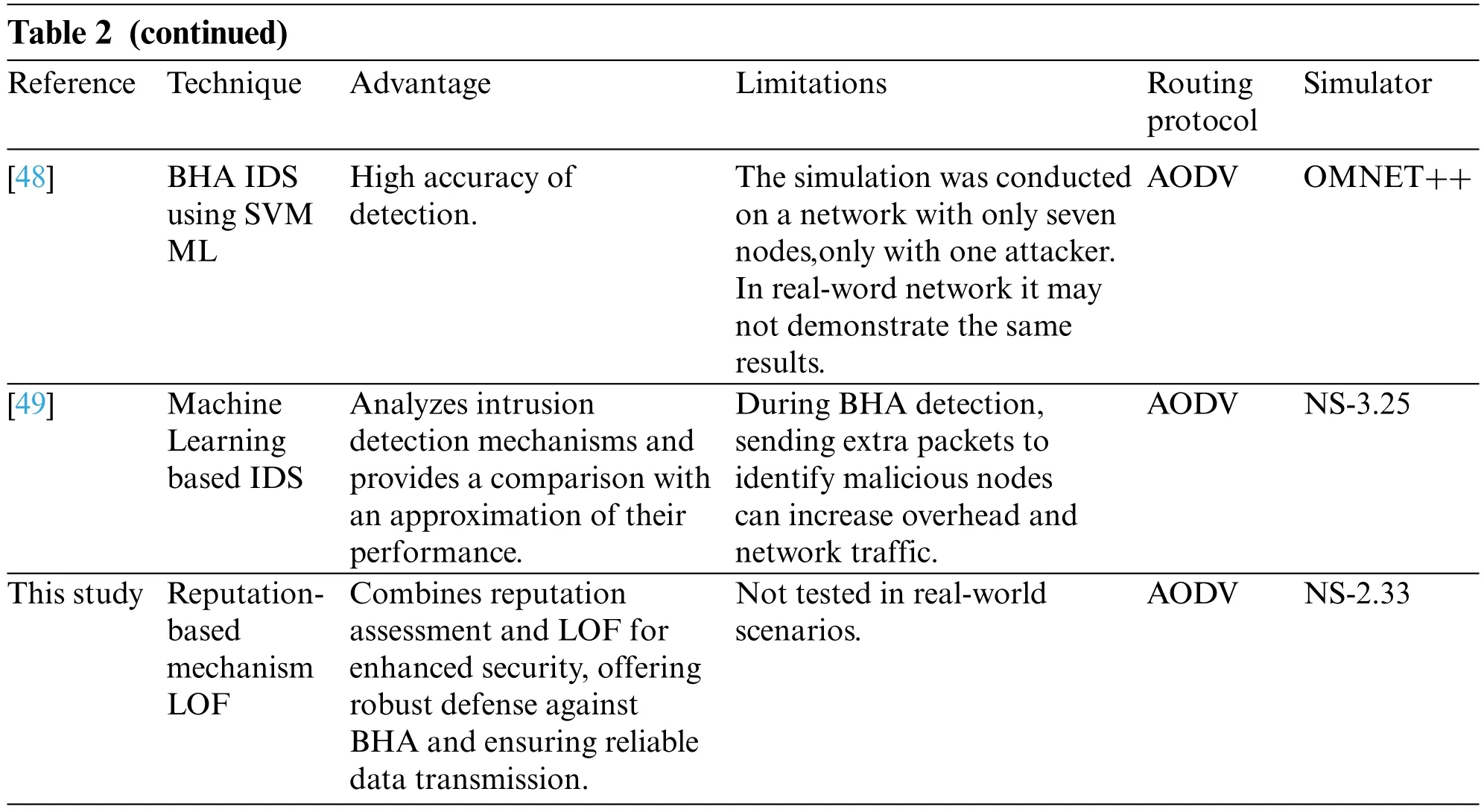
VANETs,including BHA,are highly vulnerable to attacks due to their dynamic and open nature.BHA are particularly severe as they can cause significant disruption to the network’s communication and routing protocols [34,35].Several studies have been conducted to detect and prevent BHA in VANETs,focusing on the widely used AODV routing protocol.Proposed detection mechanisms rely on detecting inconsistencies in the nodes’routing tables or using cryptographic mechanisms to prevent the insertion of false routing information [36].However,these mechanisms often suffer from high overhead and reduced network performance [37].Therefore,there is a need for more efficient and effective detection and prevention mechanisms that can be integrated with the AODV routing protocol to mitigate the impact of BHA in VANETs.In [38],the authors proposed a secure AODV routing protocol to detect and prevent single and cooperative BHA in VANETs.To achieve this,they added a validity value to the RREP without altering the fundamental mechanism of AODV.Simulation results showed that the proposed protocol outperformed the original AODV against BHA.However,the method was ineffective against intelligent adaptive black hole nodes that could falsely claim to have the shortest route by setting the validity value similarly.The authors in[39]proposed modifying the AODV routing protocol for VANETs to enhance its security against BHA.Their modification involved adding a neighbor credit table to each node in the network.
This table records the credit value of a neighbor node each time it sends or forwards a data packet,with genuine nodes receiving higher credit values than untrustworthy ones.Before utilizing a neighbor node for message transmission,a node checks its credit value in the table;if it lacks sufficient credit,the neighbor node is considered untrustworthy,and an alternative hop is used.This approach aims to increase the security of AODV in VANETs.This study introduces the Neighbor Credit Valuebased AODV(NCV-AODV)algorithm to mitigate selfish behavior.It accurately detects misbehavior in active networks using neighbor credit values.False positives are prevented by simulating dummy traffic black.In[40],the authors proposed an extension to the acknowledgment-based approach for securing communication in VANETs.The proposed method includes selecting energy-efficient intermediate nodes for communication,establishing session key agreements,implementing a counter-based endto-end acknowledgment cycle,and authenticating acknowledgment packets using message digest.The approach offers the benefit of differentiating between malicious,selfish,and low-energy nodes.However,the increased network load due to additional acknowledgment packets is a disadvantage that may lead to network congestion black.In [41],the authors introduced a new routing protocol based on TOR for VANETs.This protocol dynamically creates groups of vehicles around specific locations to act as cryptographic onion relays.Its primary objective is to maintain source,destination,and route anonymity.However,the efficacy of this approach relies on the existence of a trusted entity responsible for generating and distributing asymmetric keys in the form of certificates.The study presents a novel anonymous onion-based routing protocol.A new concept of dynamic relay groups that form around specific locations to enhance privacy and anonymity.Vehicle anonymity is maintained through the anonymity of source,destination,and route.black The authors in [42]proposed a technique for detecting black hole nodes in VANETs using bait timers in all nodes.This technique involves setting a random timer,called a baiting timer,which launches broadcasts with fake IDs once it reaches the set time.The black hole node responds to all requests regardless of authenticity and will reply to these fake requests.The sending node can then identify the black hole and record its information in a specific table.Subsequently,when legitimate requests are launched,malicious nodes can be identified and disregarded based on the information in the black hole node table.This paper introduces an enhanced AODV routing protocol with timers and baiting techniques for detecting and isolating black hole attacks.Black hole nodes can be countered through dynamic integration,maintaining network functionality.Effective detection is demonstrated while Maintaining throughput,Delay,and PDRblack.Table 2 provides a summary of the pertinent literature contributed by different researchers.Moreover,it offers a comparison of our research findings with those of various researchers,highlighting the advantages and limitations.

Table 2: Comparison of our work with related studies
3 Material and Methods
This section discusses the proposed research methodology and background of VANET-based routing protocols,including AODV routing protocols and their types.Also,we discuss the BHA.The AODV protocol faces several security weaknesses and difficulties,mainly due to the source node’s lack of knowledge about the intended destination.This feature makes VANETs more vulnerable to different security attacks,including the specific type known as BHA.BHA is categorized as a Denial of Service(DoS) attack aiming to disrupt network services [50,51].A BHA stands out as a highly aggressive cyber attack.Within VANETs,it is recognized as a complete packet drop attack.In the context of a BHA,routing protocols are exploited to steer data toward the malicious node.Regardless of whether the routing table is scrutinized,active nodes expose the presence of alternative routes [52].In this situation,a malicious node can constantly intercept a routing request.Consequently,there is a need to either alter or discard the data packets.Moreover,flood-dependent protocols introduce a vulnerability where the requesting node receives deceitful responses from malicious nodes before receiving legitimate replies from actual nodes.This leads to the creation of fabricated and harmful routes.Once a route is established,the node must decide whether to transmit the packet to an unfamiliar destination or discard it[53,54].Despite lacking a legitimate route to the destination,the black hole node successfully deceives the source node by falsely claiming to possess a valid,efficient,and recently updated route to the intended destination node[55].As shown in Fig.3,when the black hole node assumes the identity of the source node,it positions itself along the path connecting the actual source node and its intended target.To determine whether a path has been established,the source node begins transmitting data packets to the black hole node[56,57],eventually dropping all data packets without forwarding them to the destination node.
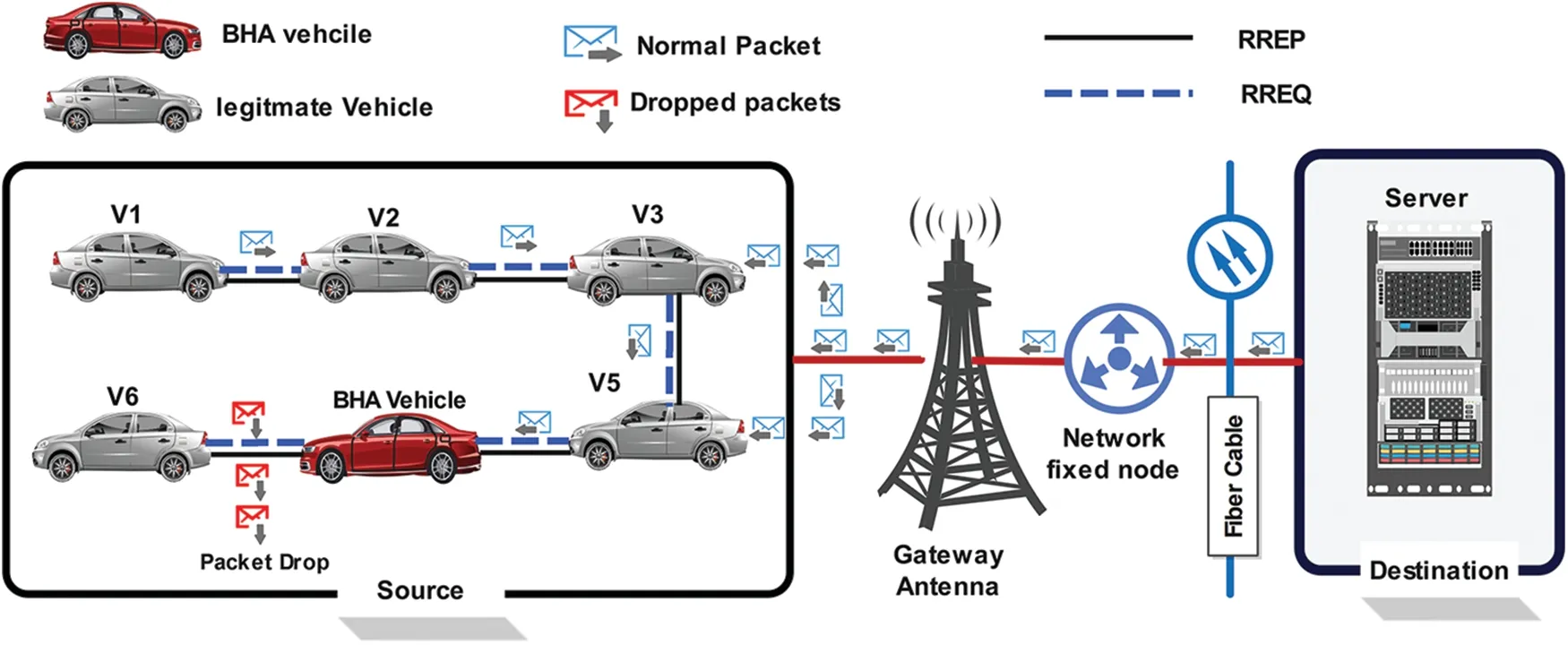
Figure 3:Black hole node attack in VANET
3.1 Node Trust Score Calculation and Proposed Reputation-Based Routing Protocol
The trust score of a node is calculated based on three factors: message transmission quality,message accuracy,and consistency of the node’s behavior in the network.(a) Message transmission quality: This factor reflects the ability of a node to transmit messages accurately and reliably in the network.The weight assigned to this factor should reflect its importance in achieving the goals of the trust-based routing algorithm.(b) Message accuracy: This factor reflects the accuracy of the information in messages transmitted by a node.The weight assigned to this factor should reflect the importance of message accuracy in achieving the goals of the trust-based routing algorithm.(c)Consistency of behavior:This factor reflects the consistency of a node’s behavior in the network over time.The weight assigned to this factor should reflect the importance of consistency in achieving the goals of the trust-based routing algorithm.The trust score is typically calculated as the product of these three factors,with an additional weighting factor applied to each factor to reflect its relative importance.As Eq.(1) shows,where w1,w2,and w3 are weighting factors that reflect the relative importance of each factor.These factors can be adjusted to give weight to each factor based on the network’s requirements.
Each weighting factor should be a value between 0 and 1,and the sum of all weighting factors should be equal to 1.The exact values assigned to each weighting factor will depend on the specific requirements of the network and the goals of the trust-based routing algorithm.
3.2 Integrated Flowchart:Detecting Malicious Nodes through Combined Algorithmic Approaches
Fig.4 presents a table and a flowchart that describe the working principle of the proposed AODVRL routing protocol.As AODV-RL is a modified version of the traditional version of AODV,we skipped all other working procedures and only focused on the main part of the modified AODV for our proposed work in Fig.4.The table lists the parameters and their descriptions used in the protocol and their descriptions used in the protocol.

Figure 4:Visual representation of algorithmic workflows
The M node is assumed to be a Reply Node,and the source node is supposed to receive a route reply message(RREP)from the M node.The Trust Score Threshold is assumed to 4 times the RREP with the same hop count.The AODV-RL employs a double check by utilizing the Local Outlier Factor (LOF) algorithm to calculate a score threshold of 25.5% to identify potentially malicious nodes.The flowchart shows the working principle of the proposed algorithms used in the AODV-RL routing protocol.Algorithm 1 is used to calculate the Trust Score Value,which is used to evaluate the trustworthiness of nodes based on their historical behavior.The protocol monitors the behavior of the M node for further evidence of malicious activity and decreases its Trust Score if necessary.Algorithm 2 calculates the LOF Score,which is used to double-check the behavior of nodes flagged as potentially malicious by the reputation-based mechanism.Overall,the proposed AODV-RL protocol enhances the security and reliability of communication in VANETs by identifying and avoiding malicious nodes and providing a secure and reliable communication framework for various applications,such as network traffic management,emergency response,and autonomous driving scenario.
3.3 Algorithms of Reputation-Based Routing Protocol
The use of the trust score in VANETs can provide several potential benefits,including improved routing efficiency,reduced vulnerability to attacks,and increased resilience to network failures.By identifying the network’s most reliable and trustworthy nodes,routing algorithms can be optimized to select the most efficient and secure paths between nodes,improving overall routing efficiency.By blacklisting nodes with low trust scores,the network can be protected against potential attacks or malicious nodes,reducing vulnerability to security threats.Finally,by using the trust score to identify the most reliable nodes,the network can be more resilient to node failures or other types of network failures,ensuring that the network continues functioning even if some nodes are unavailable.
The efficiency of Algorithm 1(see Appendix A)in big O notation is analyzed as follows:Lines 2-5 initialize the reputation and routing table for each node,resulting in a time complexity of O(n).The RREQ function(Lines 6-17)broadcasts a message to all neighbors,and its time complexity depends on the number of neighbors.Assuming a fully connected network,this function’s time complexity is O(n2).The RREP function(Lines 18-36)involves updating the routing table and reputation scores,and its time complexity is also dependent on the number of neighbors.Assuming a fully connected network,this function’s time complexity is also O(n2).The RRSE function (Lines 37-45) involves selecting the best route based on reputation score and distance,resulting in a time complexity of O(nLogn)due to the use of sorting algorithms.Therefore,the computational time complexity of the proposed algorithm is O(n)+O(n2)+O(n2)+O(nLogn),which simplifies to O(n2).
3.4 Local Outlier Factor(LOF):A Machine Learning-Based Algorithm for VANET Security
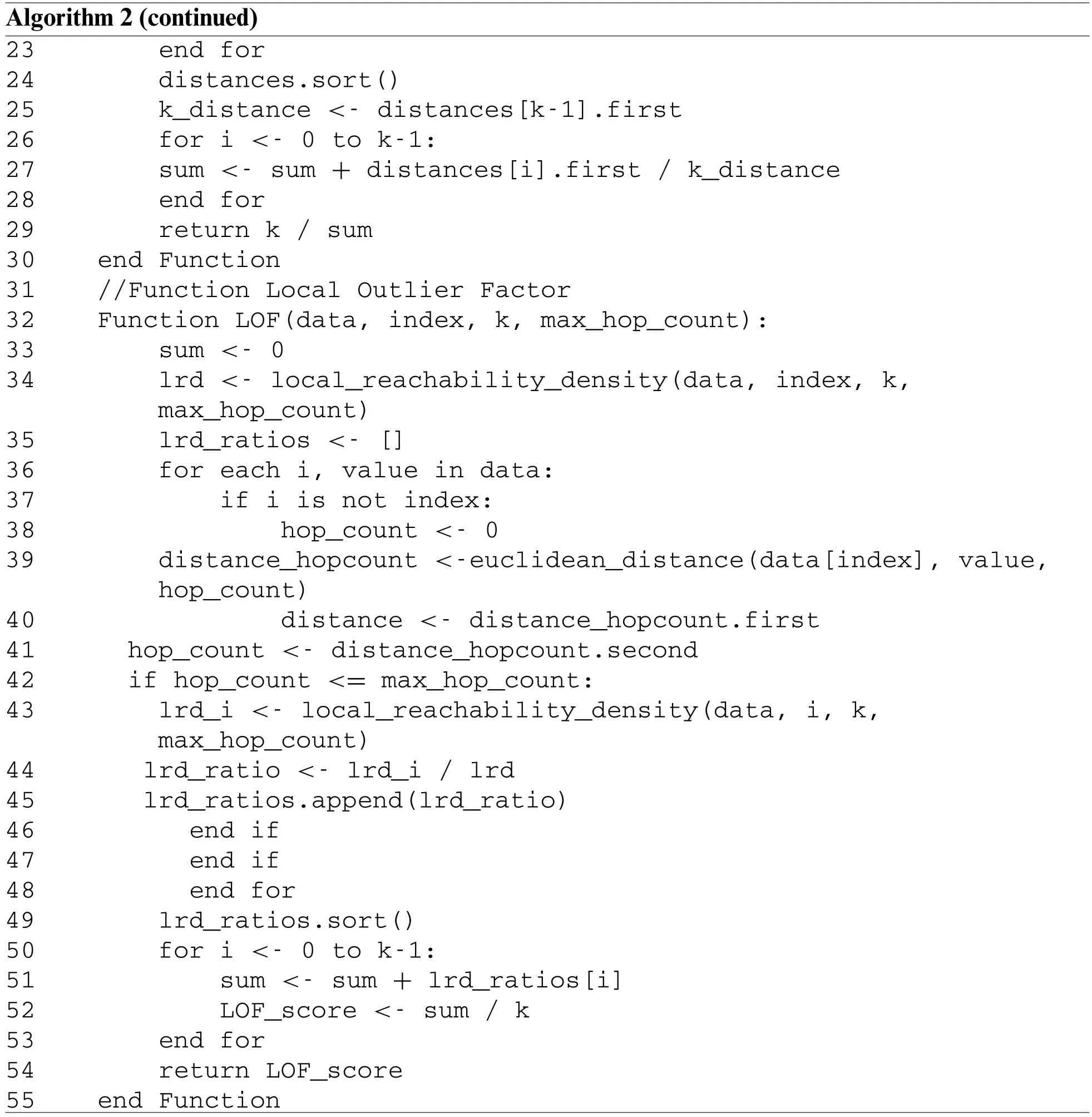
In VANETs,identifying nodes that exhibit abnormal behavior or may be potentially malicious is crucial for enhancing network security and reliability.Local Outlier Factor(LOF)is a widely used machine learning algorithm that can effectively detect such nodes.LOF evaluates the local density of each node by comparing it to the local densities of its k-nearest neighbors.The algorithm 2 (see Appendix B)can be divided into two primary steps:calculating the local reachability density of each data point and calculating the local outlier factor of each data point.To accomplish these steps,LOF relies on four equations.Eq.(1) calculates the Euclidean distance between two data points(Nodes),which is used to determine the k-nearest neighbors of a data point x.Eq.(2)increments the hop count variable by 1 each time the Euclidean distance function recursively calls itself to search for the knearest neighbors within a certain hop count h.Eq.(3)calculates the local reach-ability density of a data point,which is used to measure the local density around the point.Eq.(4) calculates the local outlier factor of a data point,which is used to identify potential anomalies or malicious nodes in the dataset.
The integration of LOF in AODV-RL enhances the security of VANETs by providing an additional layer of detection for potentially malicious nodes beyond the reputation-based mechanism.LOF evaluates the local density of each node and can identify nodes that exhibit abnormal behavior or deviate significantly from their neighbors in terms of their network behavior.LOF plays a specific role in detecting previously unknown or undetected malicious nodes that may have been missed by the reputation-based mechanism.By calculating the local outlier factor of each data point,LOF can identify nodes with high LOF values as potential outliers or malicious nodes that require further investigation or isolation from the network.Therefore,the integration of LOF in AODV-RL provides an effective way to enhance the overall security and reliability of VANETs.
The Euclidean distance function has a time complexity ofO(d),wheredis the number of dimensions of the data points being compared.The LRD function loops through all data points,which results in a time complexity ofO(n2),wherenis the number of data points.However,since it only considers theknearest neighbors,the actual time complexity can be lower,roughlyO(nklog(k)).The LOF function also loops through all data points,resulting in a time complexity ofO(n2).Similar to the LRD function,the actual time complexity can be lower,roughlyO(nklog(k)).Overall,the time complexity of the algorithm can be estimated asO(n2·k·log(k)·d),wherenis the number of data points,kis the number of nearest neighbors to consider,anddis the number of dimensions of the data points.
4 Experimental Design and Simulation Setup
In this section,we have discussed the experimental design and simulation methodology.
4.1 Simulation Tools Description
The simulation setup section describes the experimental environment and the tool used to evaluate the performance of the VANET scenario [58].In this study,we used Network Simulator Tool version 2.33 [59] to simulate the VANET scenario.NS-2.33 is a widely used open-source network simulator that allows researchers to evaluate the performance of various network protocols and algorithms in different network scenarios.We configured NS-2.33 with the appropriate protocols and parameters for the VANET scenario to ensure our simulation was accurate,specifically,the AODV-RL routing protocol for packet forwarding and the network interface type WirelessPhyExt with 5.9 GHz frequency.We also set the simulation parameters based on the characteristics of the VANET scenario.For example,we set the simulation time to 1000 s to allow for a sufficient amount of data to be collected,and we set the packet size to 1000 bytes to simulate realistic network traffic.Table 3 shows Simulation Parameters for the proposed work.The simulation parameters table summarizes the key parameters used in the VANET scenario simulation.These parameters include the network simulator version,routing protocols,MAC protocol,network topology,number of nodes,simulation time,signal bandwidth,packet size,and QoS metrics.

Table 3: Simulation parameters
The VANET scenario used five routing protocols: Normal AODV,AODV-RL,D_BH_AODV,FAAODV,and OEAODV.The MAC protocol used in the simulation was 802.11p,designed for vehicular networks.The simulation was conducted with 375 nodes and one roadside unit(RSU),with a topology area of 3000 × 3000 square meters.The simulation time was set to 750 s,and the signal bandwidth was set to 10 MHz.The simulation used a noise level of-99 dBm,a carrier sense threshold(CSThresh) of -94 dBm,and power transmission of 20 dBm.For traffic patterns,Pascal language developed a traffic generator[60],and the following are employed;it has been used in several previous studies [61,62].This traffic generator can create a traffic pattern in TCL format,supporting enduser coding in NS2.Furthermore,we have used SUMO[63]and open-street MAP[64]for mobility generating of VANET,as shown in their capturing images.Different vehicles were simulated in the VANET scenario,as shown in the OpenStreetMap Fig.5.A move-able attacker node was also assumed in the simulation,represented by a bicycle node Fig.6.SUMO simulation scenario of 375 Loaded vehicles and other parameters.
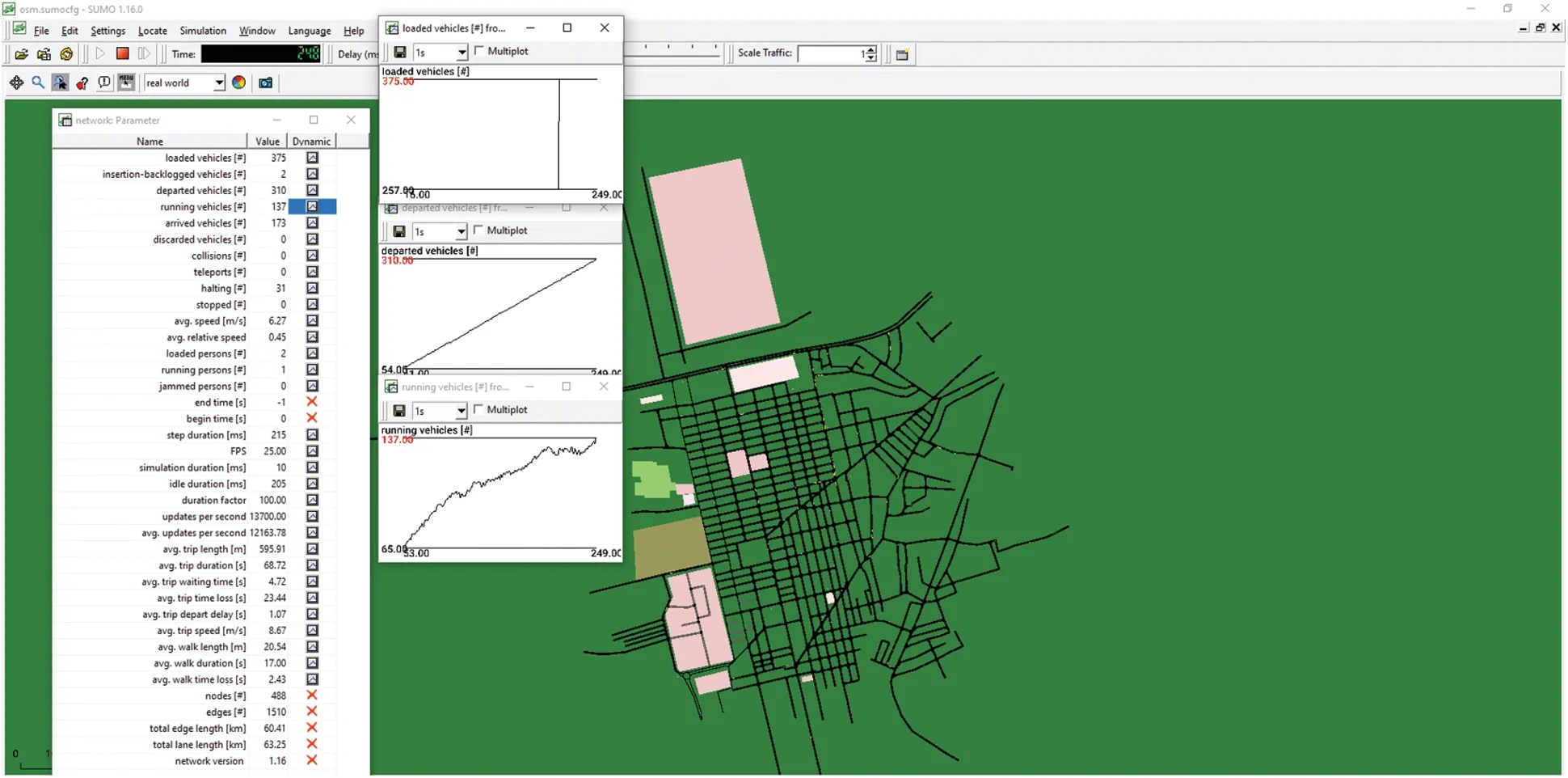
Figure 6:SUMO simulation scenario of 375 vehicles and other parameters
4.2 Performance Metrics
To thoroughly evaluate the performance of the VANET scenario and compare the effectiveness of different routing protocols,we conducted 200 simulation runs.During each simulation run,we varied the quality of service(QoS)metrics,other routing protocols,and traffic load to ensure comprehensive coverage of the simulation space.The quality of service metrics used in this study included throughput,Packet Delivery Ratio(PDR%),Normalized Routing Load(NRL%),and packet loss ratio(PLR%).
Throughput:Throughput is the measure of the amount of data that can be transmitted or processed within a given time,and it is commonly expressed in bits per second(bps),kilobits per second(Kbps),megabits per second(Mbps),or gigabits per second(Gbps).It can be calculated using the following equation:
PacketDeliveryRatio%: PDR% is a key performance metric used to assess the reliability of a communication system in terms of packet transmission[65].In the context of our research work based on AODV-RL,PDR% refers to the percentage of successfully transmitted packets out of the total number of packets sent.Eq.(7)presents the calculation of PDR in percentile(%)because it is a ratio.
NormalizedRoutingLoad: NRL% measures the network’s ability to maintain connectivity and ensure reliable communication.NRL is evaluated to assess the impact of routing protocols overhead on the overall network performance.NRL%is calculated as in Eq.(8):
PacketLossRatio%:PLR%is a metric used to evaluate the reliability of a communication system,and it represents the percentage of packets lost during transmission.PLR measures the percentage of packets lost during transmission,calculated by Eq.(9).
5 Results
The simulation experiments revealed essential insights into the performance of different routing protocols in the VANET scenario and compared their effectiveness in achieving reliable and efficient communication among vehicles and internet servers.We evaluated the performance of five routing protocols for different traffic loads and QoS metrics,including Normal AODV,AODVRL,D_BH_AODV,FA-AODV,and OEAODV.The simulation results show that the choice of routing protocol significantly impacts the performance of the VANET scenario,with some protocols consistently outperforming others across all QoS metrics.In this section,we present the detailed results of our simulation experiments,and we also compare our results with those of existing protocols in the literature to provide a comprehensive evaluation of the effectiveness of protocols in the VANET scenario.
5.1 Throughput vs.Traffic Load in Pair
Fig.7 shows the results of throughput for five different routing protocols,AODV-RL,D_BH_AODV,FA-AODV,Normal AODV,and OEAODV,under different traffic loads.The throughput values represent the total data transmitted over the network per unit of time(per second)in kbps.The graph shows that the highest throughput values are achieved by AODV-RL,and OEAODV achieves the lowest values.As the traffic load increases,the throughput values increase for all routing protocols.However,the rate of increase varies between the different protocols.Under a traffic load of 1 pair,Normal AODV has the highest throughput value of 338.96 kbps,while OEAODV has the lowest value of 40.933 kbps.However,as the traffic load increases,our proposed AODV-RL consistently outperforms the other routing protocols,achieving the highest throughput across all traffic loads.When we look under a traffic load of 50 pairs(i.e.,100 vehicles connected simultaneously),AODVRL has a throughput is 36.18%higher than OEAODV(5,321.56 kbpsvs.3,907.815 kbps).The study’s results demonstrate that the performance of routing protocols varies significantly across different traffic loads.D_BH_AODV exhibits strong performance under low traffic loads but deteriorates considerably under high traffic loads.Conversely,FA-AODV performs well under moderate to high traffic loads but experiences poor performance levels under low traffic loads.A comparison of the performance of these protocols to the proposed AODV-RL,under a traffic load of 50 pairs,indicates that AODV-RL attains the highest throughput value among all protocols.Specifically,D_BH_AODV and FA-AODV achieve 6.03%and 26.86%lower total throughput values than AODVRL,respectively.Notably,under the same traffic load,Normal AODV achieves a total throughput of 5,524.13 kbps,3.77%higher than the total throughput achieved by AODV-RL.Two main reasons for lower throughput in VANET networks are congestion and attacks,which can block or drop data,preventing it from reaching its destination[66].In this study,a traffic load of 50 pairs is insufficient to fully congest the network,as only 100 nodes were communicating,and the remaining nodes were forwarding data due to the open nature of VANET networks.However,attacks can significantly impact network performance,leading to lower throughput.A more secure routing protocol,such as the proposed AODV-RL,can prevent attacks and enable successful data transmission,resulting in higher throughput.The proposed AODV-RL is more robust than other existing protocols due to its double-check mechanism for identifying and preventing attackers,as evidenced by the lower packet loss ratio in Fig.7.
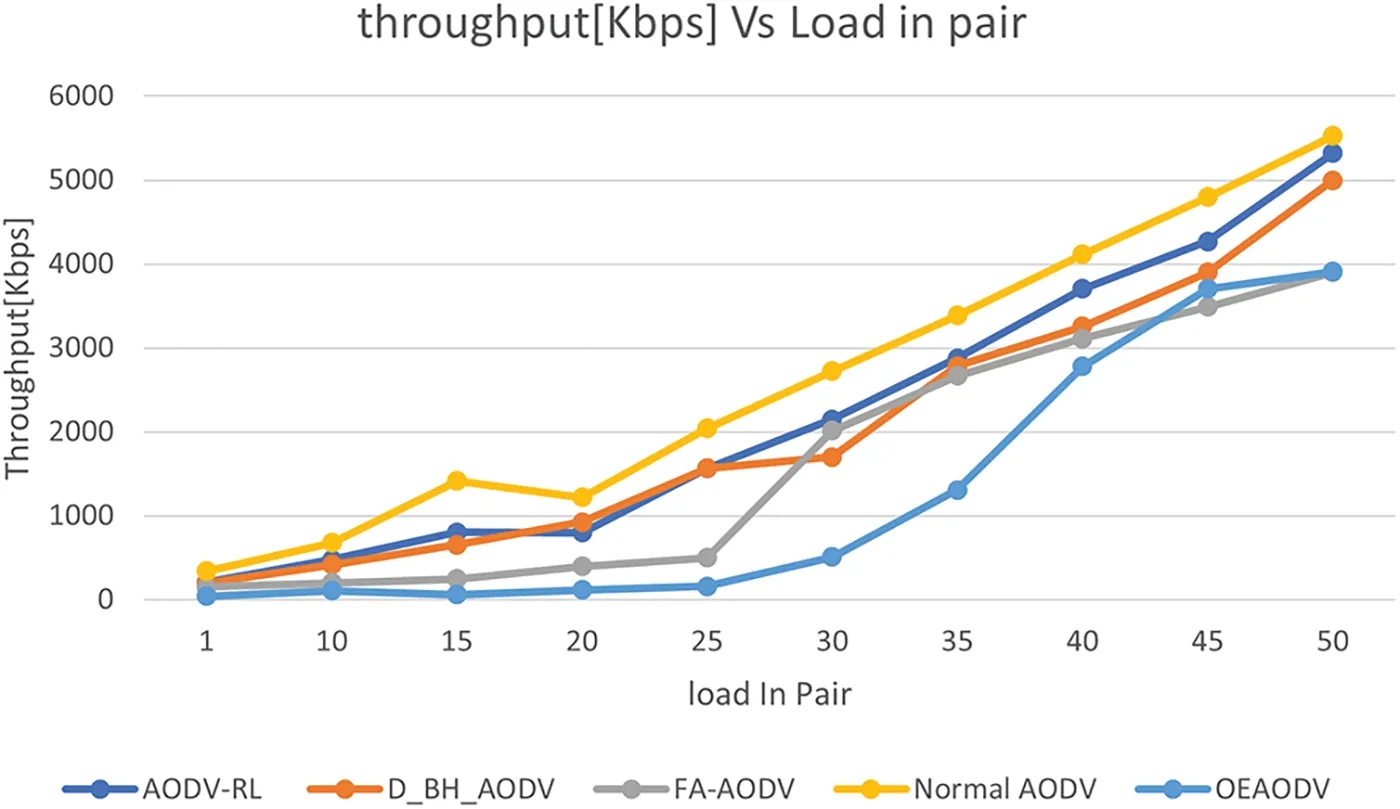
Figure 7:Throughput vs.load in pair
5.2 PDR%vs.Traffic Load in Pair
Fig.8 shows the PDR% results of packets successfully delivered to their intended destination for each routing protocol under different traffic loads.Fig.8 shows that AODV-RL achieves the highest PDR% across all traffic loads,with the lowest value achieved by OEAODV.As the traffic load increases,the PDR%values for all routing protocols tend to decrease.Under a traffic load of 1 pair,Normal AODV has the highest PDR% value of 96.22%,while OEAODV has the lowest value of 68.37%.However,as the traffic load increases,our proposed AODV-RL consistently outperforms the other routing protocols,achieving the highest PDR%across all traffic loads.When we look under the highest traffic load of 50 pairs,AODV-RL has a PDR% of 94.25%,which is 4.75% higher than OEAODV (89.5%).The PDR% results of the study demonstrate that the performance of routing protocols varies significantly across different traffic loads.D_BH_AODV exhibits strong performance under low traffic loads but deteriorates considerably under high traffic loads.Conversely,FA-AODV performs well under moderate traffic loads but experiences poor performance levels under low and high traffic loads.Comparison of the performance of these protocols to the proposed AODV-RL,under a traffic load of 50 pairs,indicates that AODV-RL attains the highest PDR% among all protocols.Specifically,D_BH_AODV and FA-AODV achieve 2.94%and 5.29%lower PDR%values than AODV-RL,respectively.The reasons for the higher and lower PDR% values are related to the mechanisms used by each routing protocol to ensure reliable data transmission in VANET networks.A more robust and secure routing protocol,such as AODV-RL,can prevent attacks and enable successful data transmission,resulting in higher PDR%.In contrast,less secure protocols,such as OEAODV,may experience packet loss due to not preventing attacks in the network,resulting in lower PDR%.

Figure 8:PDR vs.load in pair
5.3 NRL%vs.Traffic Load in Pair
Fig.9 shows the normalized routing load generated by each routing protocol under different traffic loads.Based on the results of Fig.9,we observe that AODV-RL consistently achieves the lowest NRL%across all traffic loads,indicating that it is more efficient in routing protocol overhead than other routing protocols.Under a traffic load of 1 pair,Normal AODV has the lowest NRL%value of 0.070%,while OEAODV has the highest value of 0.067%.However,as the traffic load increases,our proposed AODV-RL consistently outperforms the other routing protocols,achieving the lowest NRL%across all traffic loads.When we look under a traffic load of 50 pairs,AODV-RL has an NRL%of 0.333%,which is 1.46%lower than D_BH_AODV(0.338%)and 4.99%lower than OEAODV (0.352%).The NRL% results of the study demonstrate that the performance of routing protocols varies significantly across different traffic loads.D_BH_AODV exhibits strong performance under low traffic loads but deteriorates considerably under high traffic loads.Conversely,FA-AODV performs well under moderate to high traffic loads but experiences poor performance under very low traffic loads.Comparison of the performance of these protocols to the proposed AODV-RL,under a traffic load of 50 pairs,indicates that AODV-RL attains the lowest NRL% among all protocols.Specifically,D_BH_AODV and FA-AODV achieve 1.51% and 2.59% higher NRL% values than AODV-RL,respectively.Notably,under the same traffic load,Normal AODV performs an NRL%of 0.834%,which is 0.501%higher than the NRL%achieved by AODV-RL.The reasons for the lower NRL%values in the table are related to the mechanisms used by each routing protocol to minimize the routing protocol overhead in VANET networks.A more efficient and optimized routing protocol,such as AODV-RL,can reduce the number of control packets generated and transmitted,resulting in lower NRL%.The lower NRL% achieved by AODV-RL compared to other existing protocols demonstrates its ability to minimize routing protocol overhead,resulting in a more efficient and optimized communication system.

Figure 9:NRL%PDR vs.load in pair
5.4 PLR%vs.Traffic Load in Pair
A lower PLR%indicates that a routing protocol is more efficient in delivering data packets with lower packet loss rates.Fig.10 compares the five routing protocols regarding the Packet Loss ratio,which is in percentile value(%)of data packets lost during transmission by each routing protocol under different traffic loads.Furthermore,in Fig.10,we also observe that AODV-RL consistently achieves the lowest Packet Loss ratio % across all traffic loads,indicating that it is more efficient regarding data packet delivery than other routing protocols.In contrast,different routing protocols FA-AODV,D_BH_AODV,and OEAODV,generate the highest Packet Loss ratio%values,indicating they have the highest data packet loss rates.Under a traffic load of 1 pair,Normal AODV has the highest Packet Loss ratio % value of 24.65%,while D_BH_AODV has the lowest value of 7.6%.However,as the traffic load increases,our proposed AODV-RL consistently outperforms the other routing protocols,achieving the lowest Packet Loss ratio%across all traffic loads.AODV-RL has a Packet Loss ratio% of 0.297%,which is 69.16% lower than OEAODV (0.961%) and 69.42% lower than FA-AODV(0.974%) at the highest traffic load.The study’s Packet Loss ratio % results demonstrate that the performance of routing protocols varies significantly across different traffic loads.D_BH_AODV exhibits strong performance under low traffic loads but deteriorates considerably under high traffic loads.Conversely,FA-AODV performs well under moderate to high traffic loads but experiences poor performance under low traffic loads.A comparison of the performance of existing routing protocols to the proposed AODV-RL,under a traffic load of 50 pairs,indicates that AODV-RL attains the lowest Packet Loss ratio%among all protocols.Specifically,D_BH_AODV and FA-AODV achieve 61.40%and 69.25%higher Packet Loss ratio%values than AODV-RL,respectively.Notably,under the same traffic load,Normal AODV reaches a Packet Loss ratio % of 25.98%,which is also lower than others.The reasons for the lower Packet Loss ratio%are related to the mechanisms used by each routing protocol to minimize the data packet loss rates in VANET networks.A more secure,efficient,and optimized routing protocol,such as AODV-RL,can reduce the data packet loss rates by selecting more reliable and secure routes.The lower Packet Loss ratio%achieved by AODV-RL compared to other existing protocols demonstrates its ability to minimize data packet loss rates,resulting in a more reliable and efficient communication system.
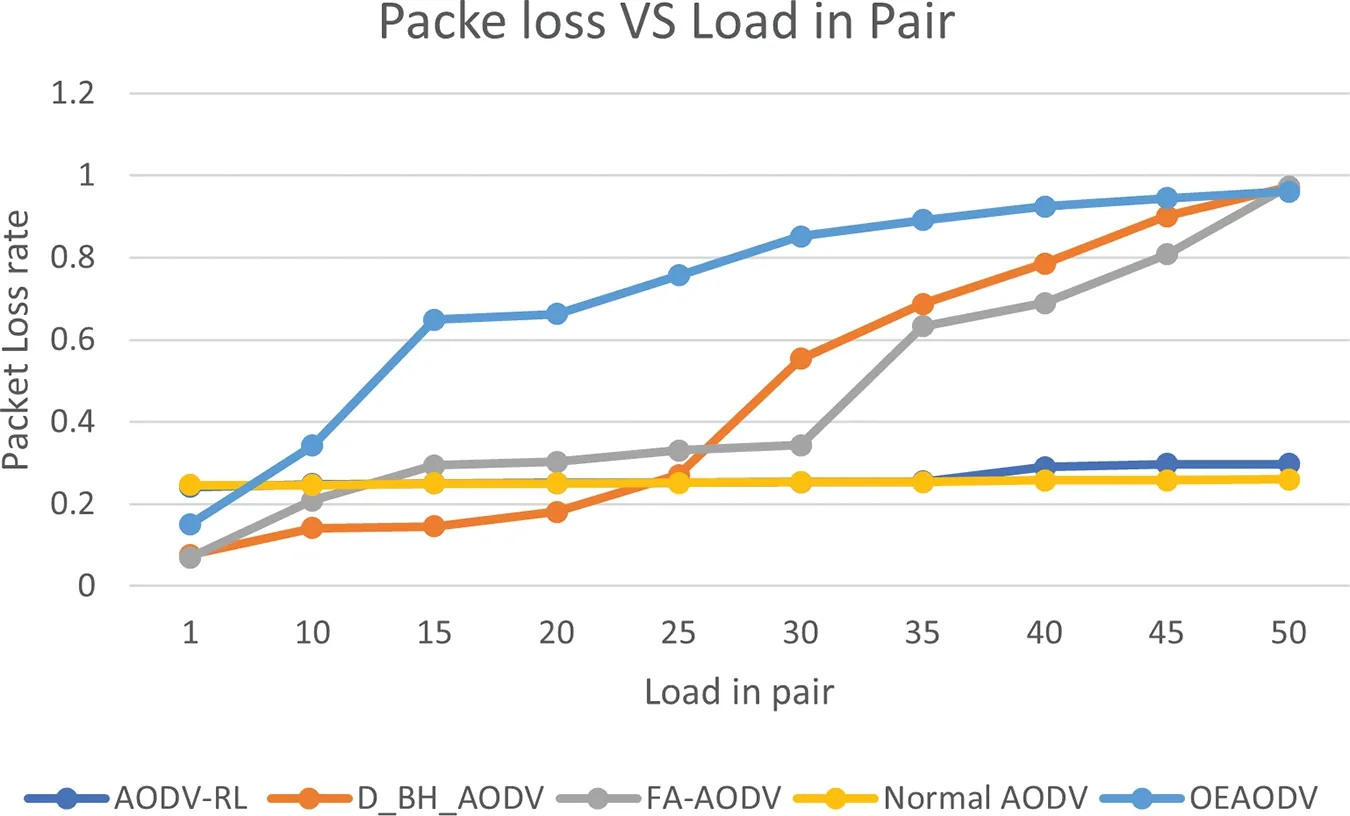
Figure 10:Packet loss rate vs.load in pairs
6 Conclusion,Limitations,and Future Directions
This article aims to introduce AODV-RL,a novel routing protocol designed to enhance the reliability and security of communication in VANET.By incorporating reputation and Local Outlier Factor (LOF)-based mechanisms,AODV-RL addresses the challenges posed by dynamic VANET environments,ensuring seamless and efficient communication between vehicles,infrastructure,and other entities involved in transportation.By evaluating AODV-RL under various scenarios,including different traffic loads and mobility speeds,extensive simulation experiments have yielded notable findings.According to our results,the message delivery ratio of AODV-RL is superior to existing routing protocols by as much as 94.25%,with a packet loss ratio of only 0.297%.AODV-RL demonstrates improved message delivery ratios compared to existing routing protocols,signifying its ability to facilitate reliable data transmission across the network.This enhancement in message delivery ratios contributes to the overall robustness and effectiveness of AODV-RL in VANETs.A further benefit of AODV-RL is its ability to identify malicious nodes and isolate them from the network,enhancing security.AODV-RL minimizes potential threats by evaluating the trustworthiness of nodes based on their historical behavior.AODV-RL routing protocol ensures the integrity of communication in VANETs.This contributes to the overall security and reliability of the protocol,making it suitable for various applications such as traffic management,emergency response,and autonomous vehicles.There are several limitations and practical considerations of AODV-RL to be considered.For instance,AODV-RL requires significant training data to optimize its routing decisions,which can be impractical in some scenarios.In addition,the training process for AODV-RL can be time-consuming,resulting in slower convergence times for routes than for traditional routing protocols.The AODV-RL is nevertheless configured to handle varying VANET traffic loads.The scalability of a network depends on several factors,such as its size and density,nodes’mobility,and computing resources.The AODVRL has shown promising results in simulation studies,but its practical implementation in real-world deployment environments requires careful consideration of these limitations and scalability concerns.
Acknowledgement:The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement:The authors received no specific funding for this study.
Author Contributions:The authors confirm contribution to the paper as follows:study conception and design: Nadeem Ahmed,Khalid Mehmodani,Ali Kashif Bashir,Marwan Omar,Angel Jones,and Fayaz;data collection: Khalid Mehmodani;analysis and interpretation of results: Nadeem Ahmed,Khalid Mehmodani,and Ali Kashif Bashir;draft manuscript preparation:Khalid Mehmodani,and Ali Kashif Bashir.All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials:Not applicable.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
Appendix A


Appendix B
 Computer Modeling In Engineering&Sciences2024年4期
Computer Modeling In Engineering&Sciences2024年4期
- Computer Modeling In Engineering&Sciences的其它文章
- Cloud Datacenter Selection Using Service Broker Policies:A Survey
- An Overview of Sequential Approximation in Topology Optimization of Continuum Structure
- A Review on the Security of the Ethereum-Based DeFi Ecosystem
- Exploring Deep Learning Methods for Computer Vision Applications across Multiple Sectors:Challenges and Future Trends
- Evolutionary Neural Architecture Search and Its Applications in Healthcare
- Deep Learning for Financial Time Series Prediction:A State-of-the-Art Review of Standalone and Hybrid Models
