Analysis and Simulations of Open-Source Intelligence Process System Dynamics from User’s Perspective
Huan Liu,Zhenyu Tang,Ning Zhao,★and Wei Qian,★
1Northeast Agricultural University,Harbin,150030,China
2Harbin Institute of Technology Library,Harbin,150001,China
ABSTRACT In today’s society with advanced Internet, the amount of information increases dramatically with each passing day, which leads to increasingly complex processes of open-source intelligence.Therefore, it is more important to rationalize the operation mode and improve the operation efficiency of open-source intelligence under the premise of satisfying users’needs.This paper focuses on the simulation study of the process system of opensource intelligence from the user’s perspective.First, the basic concept and development status of open-source intelligence are introduced in details.Second,six existing intelligence operation process models are summarized and their advantages and disadvantages are compared in focus.Based on users’preference, the open-source intelligence system simulation theory model is constructed from four aspects:intelligence collection,intelligence processing, intelligence analysis, and intelligence delivery.Meanwhile, the dynamics model of the open-source intelligence process system is constructed based on the open-source intelligence system simulation theoretical model, which specifically includes five parts:determination of system boundary, construction of causal loop diagram,construction of stock flow diagram,writing of mathematical equations,and system sensitivity test.Finally,the system simulation results were analyzed.It was found that improving the system of intelligence agencies,opening up government affairs, improving the professional level of intelligence personnel, strengthening the communication and cooperation among personnel of various intelligence departments,and expressing intelligence products through diverse forms can effectively improve the operational efficiency of the open-source intelligence process system.
KEYWORDS Open-source intelligence;system dynamics;feedback;user demand deviation
1 Introduction
Data and information, as the basis and original carrier of intelligence, have greatly enriched the content of intelligence work; and new technologies such as artificial intelligence techniques have changed the traditional intelligence operation [1].Recently, obtaining intelligence from opensources has gradually become hot topic among intelligence agencies and academics.Nowadays,opensource intelligence has transformed from an isolated effort by a few to a partially open, networked and collaborative project [2].However, the development of intelligence work in China still lags behind, in which open-source intelligence agencies still suffer from many problems such as chaotic business processes,low efficiency of intelligence operations,and low credibility of intelligence products.Under such circumstances,strengthening the development and utilization of open-source intelligence,improving the institutional mechanism of intelligence work, and improving the professional level of intelligence personnel and the communication and cooperation among staff members have become important issues that need to be solved[3].
The existing literature on open-source intelligence mainly covers three aspects:the conceptual definition of open-source intelligence,the analysis of open-source intelligence processes,and the application of open-source intelligence.The first is the definition of the concept of open-source intelligence.The Central Intelligence Agency(CIA)considers open-source intelligence as“information collected from open sources such as media, commercial data, and other processed information” [4].NATO believes that only resources obtained within the scope of the public license provided by law can be called open-source intelligence.Ding B.T., a Chinese scholar [5] showed that the concept of opensource intelligence should be understood in both narrow sense and broad sense.The narrow sense mainly refers to the openness on the“source”of intelligence,but the content of intelligence still has a certain degree of confidentiality;the broad sense mainly refers to the openness on the“work”,that is,anyone can participate in the intelligence work and realize the sharing of intelligence.The authors of this paper agree more with the viewpoint of Ding B.T.scholars that open-source intelligence is an intelligence model with feedback loop,where the source of information is open and transparent,and anyone can participate in the intelligence work, but the intelligence content is only provided to the target users.In fact,as long as the source of information is open and transparent,the intelligence processed from this information is open-source intelligence regardless of its presentation[1].Secondly,for the analysis of the open-source intelligence process, existing studies point out that open-source intelligence, while following the established intelligence generation laws, also goes through several specific links such as user requirements, intelligence collection, intelligence processing, intelligence analysis, and intelligence feedback, which in turn form a certain feedback loop.The research of Bo-Tao Ding scholars shows that the application of artificial intelligence in various aspects of the open-source intelligence process greatly improves the efficiency of information collection,processing,and analysis,saves a lot of Labor,capital and time,improves the operational efficiency of the opensource intelligence process[6].Zhong[7]summarized the shortcomings of the traditional intelligence process and introduced two methods,Meta-analysis and ACH,to construct a new intelligence process model.Li et al.[8] constructed an intelligence process model based on multiple types of decision support;meanwhile,they divided the existing intelligence process models into two categories:process models emphasizing structure and process models emphasizing function,analyzed the limitations of the two types of process models, and constructed a decision-driven intelligence process model [9].Zhang et al.[10]constructed a theoretical model of cyber financial crime intelligence process of multichain blockchain based on the basic principles and basic features of blockchain and analyzed the operation process in detail.Huang et al.[11]constructed a workflow model of enterprise competitive intelligence with network multi-source information,which includes several links of demand analysis,information source selection, information collection, information processing, information analysis,and intelligence result output.Finally, there are two main areas of applied research on open-source intelligence.On the one hand, there are applications to government-led military, national security,public safety, and other law enforcement sectors.for example, Ju et al.[12] analyzed the use of open-source information such as social media in the field of military intelligence.Li [13] detailed the application of open-source intelligence in the field of cyber security.Tan et al.[14] repositioned the role and path of open-source intelligence to serve the overall national security concept.Benedict et al.[15] used artificial intelligence technology combined with intelligence to predict and research the early information of China COVID-19.Hong et al.[2]showed that in the era of big data,opensource intelligence is used in government departments to better implement government information disclosure and promote epidemic prevention and control.Wang et al.[16]described the positive role of open-source intelligence in the detection work in the Internet environment.The second is the use of competitive intelligence in enterprises dominated by private organizations.For example,Zheng et al.[17] constructed an enterprise competitive intelligence system based on the ACP theory, which provides intelligent support for enterprise decision making.Wang et al.[18]constructed a competitive intelligence early warning mechanism for small and micro enterprises based on big data thinking,which significantly avoided the possible risks faced by small and micro enterprises.Based on big data thinking, Wang et al.[19] used a system dynamics approach to simulate the early warning mechanism of competitive intelligence for small and micro enterprises.Wang et al.[20]constructed a model of competitive intelligence collection system for SMEs based on the theory of particle swarm optimization algorithm.Liao et al.[21]analyzed the competitive intelligence service business models of different types of enterprises and empirically verified the effectiveness of improving the competitive intelligence service model of enterprises.
Of course,some scholars have also studied the dynamic mechanism of information systems using system dynamics methods,for example,Li et al.[22]constructed a system dynamics model of Baidu Encyclopedia by analyzing causality and system flowcharts,and proposed the dynamic mechanism of Baidu Encyclopedia based on the simulation results.Abdallah[23]describe the mechanism of optimal control theory applied to stochastic elliptic systems.All these literatures have greatly guided the study of this paper.
Through reading the existing literature,we also found that most of the existing research on opensource intelligence focuses on three aspects:concept definition, process analysis, and intelligence application, and the research is more comprehensive and in-depth.As such, this paper constructs a theoretical model of open-source intelligence process system based on the users’perspective as critical feedback.We gradually screened the chaotic open-source intelligence by intelligence collection, intelligence processing, intelligence analysis, and intelligence delivery processes, which finally transformed to theoretical intelligence model as valid intelligence products.Nevertheless, during information transfer processes,many factors can affect the transmission rate of the system as well as the final intelligence products.Therefore,by using system dynamics method,we attempted to simulate the actual information flow operation pattern by optimizing important parameters in the process;we then revealed the effects of such parameters on the efficiency of intelligence operation.The biggest innovation of this paper is:first,in the research process of open-source intelligence,many scholars have constructed corresponding theoretical models of intelligence processes according to specific problems,and the constructed models may be too complex or even not operable in reality, and more costly to run.In this paper, based on re-examining the existing six types of intelligence process models, we reconstruct the theoretical model of open-source intelligence process from the perspective of user thinking at the macro level, which is more operable in reality compared with the existing literature.Second,most of the existing literature analyzes the process model of open-source intelligence based on the theoretical level, without clarifying the intrinsic reasons for the inefficient operation of the intelligence process model.Based on the theoretical analysis,this paper combines the system dynamics approach,uses the drawing tool that comes with Vensim-PLE software to draw causal loop diagrams and flow stock diagrams,and simulates the open-source intelligence process under user thinking based on the corresponding functions of the software Third,this paper constructs a theoretical model of the open-source intelligence process,which can test the rationality and feasibility of the system dynamics model of the open-source intelligence process.
2 Construction of Theoretical Model for Open-Source Intelligence Process
Regarding the study of intelligence process,intelligence scholars and related scholars believe that it can be divided into seven links, six links, five links, four links, etc.There is a certain logical order among the various links of the intelligence process,and different scholars consider different problem contexts and construct different models of the intelligence process.Peng[24]summarized the existing intelligence process models, mainly the linear propulsion model, intelligence cycle model, multiple cycle model, goal-oriented model, decision-driven model, etc.Each intelligence process model has certain advantages and disadvantages,which are shown in Table 1.
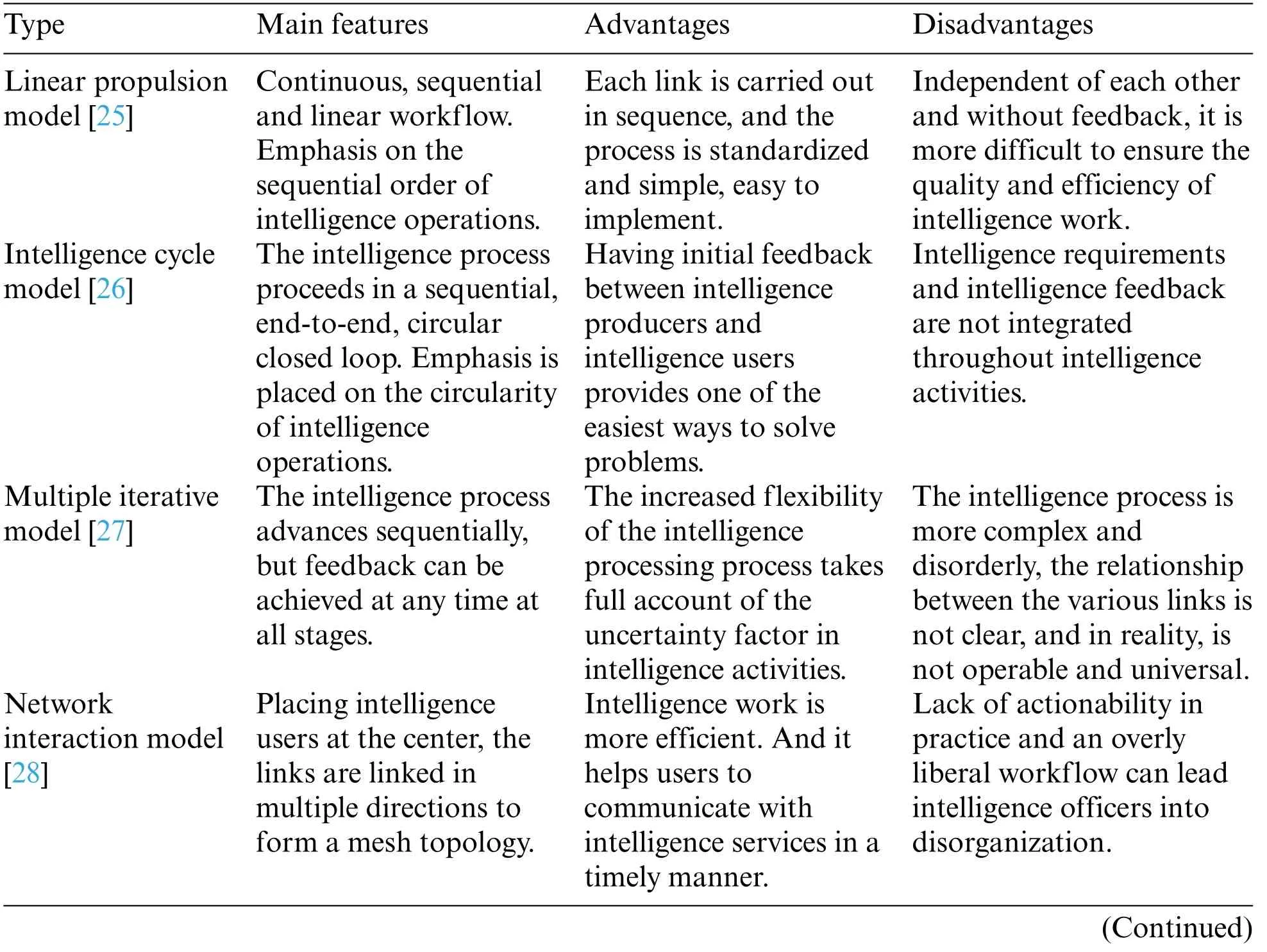
Table 1:Longitudinal comparison of various intelligence process models
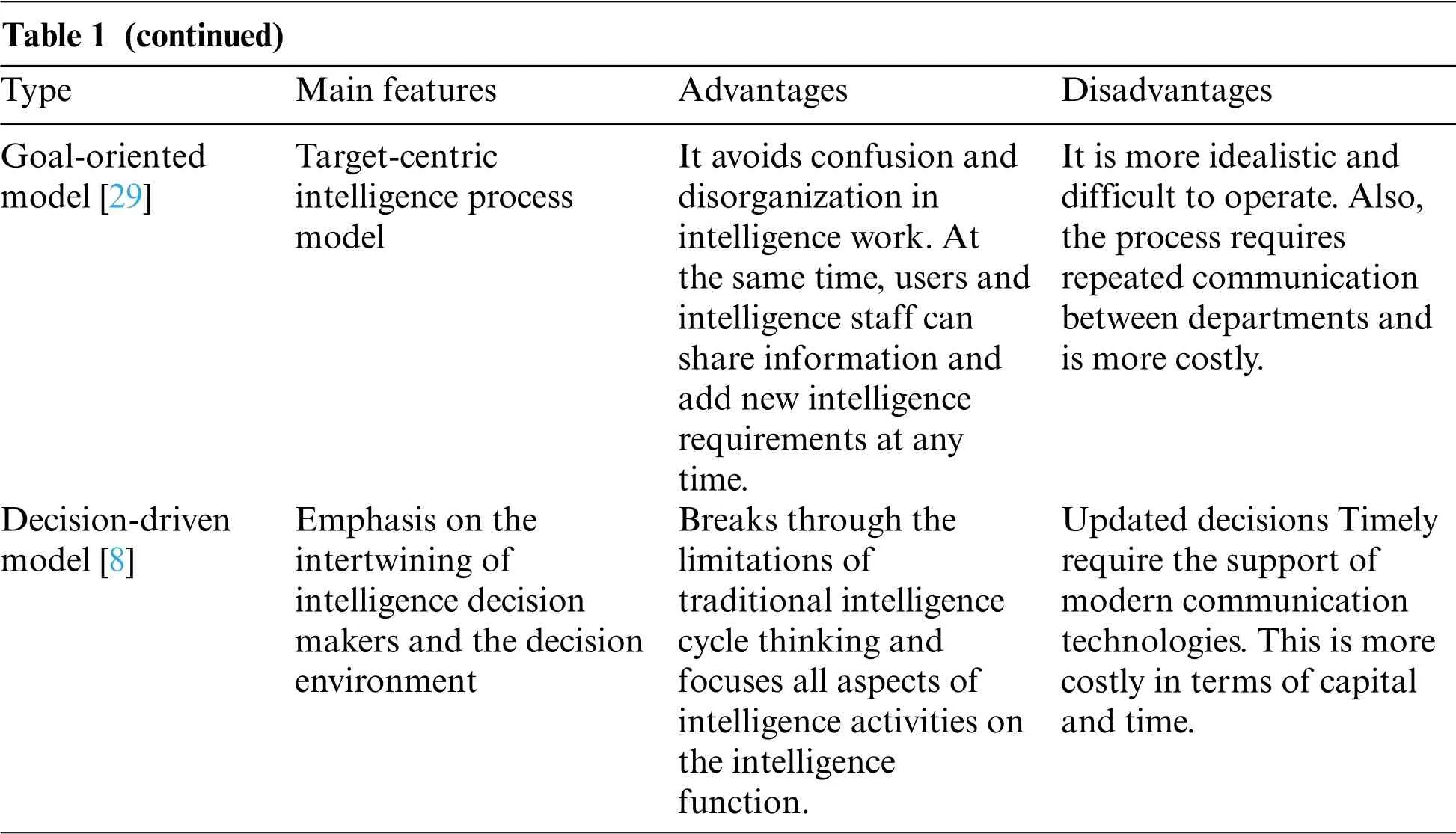
Table 1 (continued)Type Main features Advantages Disadvantages Goal-oriented model[29]Decision-driven model[8]Target-centric intelligence process model Emphasis on the intertwining of intelligence decision makers and the decision environment It avoids confusion and disorganization in intelligence work.At the same time,users and intelligence staff can share information and add new intelligence requirements at any time.Breaks through the limitations of traditional intelligence cycle thinking and focuses all aspects of intelligence activities on the intelligence function.It is more idealistic and difficult to operate.Also,the process requires repeated communication between departments and is more costly.Updated decisions Timely require the support of modern communication technologies.This is more costly in terms of capital and time.
The above limitations of the intelligence process are mainly manifested in:(1) The traditional intelligence process model is not consistent with the actual intelligence work, the actual intelligence work is not a simple linear advance or a single cyclical cycle,the links are likely to produce duplication,jump.(2)The traditional intelligence process is complex to run,and the source of information is not open and transparent,which will significantly increase the cost of intelligence work in the process of advancing.(3)The user’s needs and timely feedback in the operation of the intelligence process is not prominent enough.
In view of the shortcomings of the current intelligence process, this paper proposes a userdriven intelligence process model, which does not simplify the content of intelligence links and sever the links between intelligence links because of excessive emphasis on efficiency, and does not overemphasize the function of intelligence, which makes the intelligence process too detached from reality and complicated.The model mainly starts from the feedback of users’needs,incorporates useful information from various aspects into the intelligence process, and provides the most satisfactory intelligence to users through the repeated operation mode of intelligence departments’screening and circulation.Compared with the existing intelligence process model,this model has certain innovation and realistic guidance.The innovation is mainly reflected in the fact that the model is driven by the feedback of user needs, and the intelligence process will advance with the change of user needs to realize the cycle of each intelligence link.Realistic guidance is mainly reflected in the fact that the model runs a relatively simple process without much crossover,and the intelligence work emphasizes internal and external linkage and open and transparent information sources.The theoretical model of the open-source intelligence process constructed in this paper is shown in Fig.1.
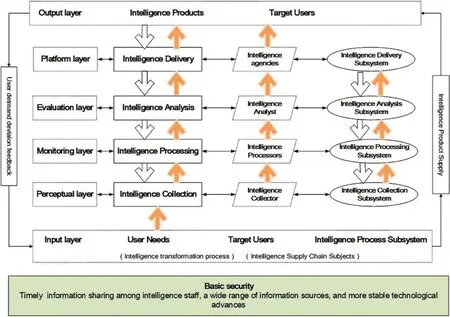
Figure 1:Theoretical model of open-source intelligence process
According to the different data and intelligence content flowing in each intelligence link, the theoretical model of open-source intelligence process is divided into four stages,namely,the demand confirmation stage based on user feedback,the preliminary screening stage based on demand-related open-source information, the intelligence processing stage based on intelligence professionals, and the intelligence transmission stage based on relevant transmission platforms.New intelligence needs are discovered through user feedback, intelligence needs generate a large amount of open-source information converted into preliminary key information that can be used,intelligence agency professionals carry out key content analysis of intelligence information,and the final intelligence products generated are transmitted to specific users, and new data are generated to facilitate the revision of existing intelligence content by combining user feedback and collaborative communication of intelligence personnel at various stages.The cycle is repeatedly progressed to achieve the improvement of intelligence work and the satisfaction of user needs.The four stages of the theoretical model correspond to the four stages of intelligence collection, intelligence processing, intelligence analysis and intelligence delivery.
1.The demand confirmation stage based on user feedback:This stage mainly relies on user feedback to start intelligence collection, which is an important basis for carrying out other aspects of intelligence work, and at the same time, extensive open-source information and timely and accurate communication with users becomes the basis for this stage to be carried out smoothly.The process of clarifying requirements in the context of open-source information,mainly based on user feedback as the starting point to obtain requirements,collect information from various public channels,including electronic media,social networking sites,government meeting reports,academic reports,etc.,combined with feedback information or data generated in the process of intelligence delivery, and finally collect a large amount of relevant or usable data.
2.The preliminary screening stage based on demand-related open-source information:this stage involves the cleaning of a large amount of information,and the integration of cluttered data is an important part of data transformation into intelligence.In the context of open-source information, the scale of data is huge, data types are complex, structured and unstructured data coexist, and data sources are extensive and disorganized.Therefore, this stage needs to rely on the professional level of intelligence processors,the level of development of information technology,etc.,to determine as soon as possible the effective scope of data,the timeliness of intelligence and the authenticity and availability of intelligence content.
3.The intelligence processing stage based on intelligence professionals:This stage involves the normalization of data.In the era of information open-source, intelligence analysis is more manifested in the format transformation of various data types into data that can be stored and have value.Through data extraction technology,natural language processing technology,etc.,the required data are stored and extracted,and indexes are established and data permissions are set to ensure that the data can be accessed quickly and accurately by users or related personnel,and turned into readable normative data.At the same time,intelligence staff and related experts conduct research and judgment to examine the processing speed of data,the security of storage,the standardization of data,the value of intelligence,etc.
4.The intelligence transmission stage based on relevant transmission platforms:This link produces regulated intelligence products.Through data translation technology,data is accurately reduced to its represented content to achieve data content integration; through natural language processing technology,semantically effective understanding of data content is achieved to achieve data semantic integration.At this point, intelligence agencies submit intelligence products to users in various readable forms, such as documents, videos, voice, etc.After receiving the intelligence products,the user puts forward a new round of demand feedback,and each link of the process is repeatedly cycled,which eventually makes the intelligence products gradually meet the needs of users.
3 Dynamics Model Construction for Open-Source Intelligence Process System
As we all know,the reality of the open-source intelligence system is a large and complex system,in this large system not only involves a number of links and a variety of information collection and processing, and links and elements also exist between the inextricable links.On the one hand, the current research only through theoretical models to roughly express the process system and the analysis of the internal structure of the system is still very unclear; on the other hand, the development of China’s open-source intelligence is more serious problems and intelligence-related laws and regulations are not sound, intelligence agencies are more fragmented, less cooperation and communication between departments,in the process of information transfer,there will inevitably be information delays and loss.However, system dynamics software comes with a smoothing function that can visually represent this phenomenon, which is of great value for solving this problem.Therefore, this paper constructs a system dynamics simulation model of open-source intelligence process, and uses the advantages of system dynamics in many aspects to simulate a realistic open-source intelligence process system as much as possible,and find the factors affecting the operation efficiency of the system through parameter adjustment to improve the efficiency of intelligence delivery.
3.1 Determination of System Boundary and Prerequisite Assumptions
In this paper, we first consider rate variables such as intelligence collection rate, intelligence processing rate,intelligence system output rate,and state variables such as the amount of information at the perception level, the amount of information at the monitoring level, the total amount of intelligence products, and some auxiliary variables as endogenous variables of the system, while the degree of institutional perfection of intelligence agencies,the level of infrastructure construction,the user target demand, the level of government policy restrictions, the professional level of intelligence personnel, etc., are identified as the exogenous variables of the system.The following are the basic assumptions of this model.
H1:The“level of Internet development”in the model is represented by the“Internet penetration rate”in the 47th Statistical Report on the Development Status of the Internet in China, and as of December 2020, the Internet penetration rate in China has reached as of December 2020, China’s Internet penetration rate has reached 70.4%, so it is assumed that the Internet development level is 0.7,which indicates that China’s Internet development has reached a medium to high level.
H2:The “degree of policy restriction”in the model indicates the degree of restriction of public information by the Chinese government,which is expressed by the indicator of“number of microblogs of government agencies”.Therefore, it is assumed that the degree of information restriction by government policies is 0.2, which indicates that the degree of government restriction on public information is relatively small.
H3:Open-source intelligence agencies in China are relatively scattered and do not form a more centralized and unified intelligence system,and there is a large amount of wasted resources.Therefore,it is assumed that the degree of perfection of open-source intelligence agencies is 0.1,which indicates that the degree of perfection of open-source intelligence agencies in China is low.
H4:The“level of infrastructure construction”in the model affects the processing rate of intelligence,and the level of infrastructure construction is assumed to be 0.7,which indicates that the level of computer equipment infrastructure in China reaches a medium level.
3.2 Causal Loop Diagram Construction of the System
In this paper, we strictly follow the principles of Vensim-PLE software for drawing causal loop diagrams for open-source intelligence development and exploitation systems,as shown in Fig.2.
Important feedback loops.
B1:User demand deviation →Intelligence collection rate →Amount of information in the perceptual layer →Perception layer value →Effective information output from the perceptual layer→Intelligence processing rate →Amount of information in the monitoring layer →Monitoring layer value →Effective information output from the monitoring layer →Analysis rate of intelligence→Total assessment layer information →Assessment layer value →Valid information output at the evaluation level →Intelligence transfer rate →Total platform level information →Platform layer value →Effective information output at the platform level →Output rate of intelligence systems →Total Intelligence Products →User demand deviation
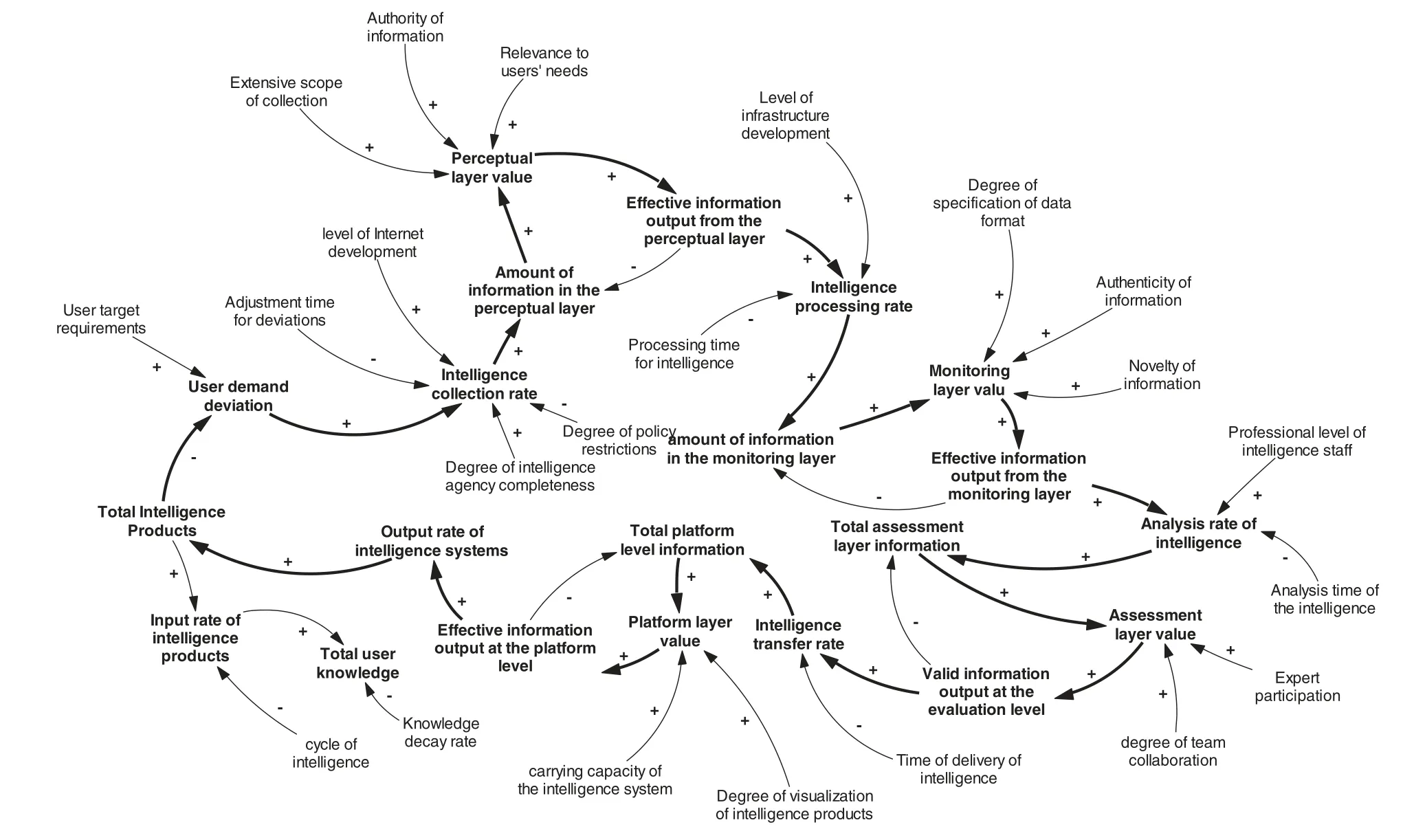
Figure 2:Causal loop diagram of the system
B2:Amount of information in the perceptual layer →Perception layer value →Effective information output from the perceptual layer →Amount of information in the perceptual layer
B3:Amount of information in the monitoring layer →Monitoring layer value →Effective information output from the monitoring layer →Amount of information in the monitoring layer
B4:Total assessment layer information →Assessment layer value →Valid information output at the evaluation level →Total assessment layer information
B5:Total Platform layer information →Platform layer value →Effective information output at the platform layer →Total Platform layer information
3.3 Flow Diagram Construction of the System
In this paper, after constructing the causal loop diagram to express the causal relationship and feedback loop, the flow stock diagram of the system was drawn in order to better establish the mathematical relationship between the variables,as shown in Fig.3.
Next, the state variables, rate variables, constants, and auxiliary variables within the system are organized according to the flow stock diagram drawn,as shown in Table 2.The remaining variables not listed in Table 2 are all auxiliary variables of the system, and there are a total of 26 auxiliary variables in the system.
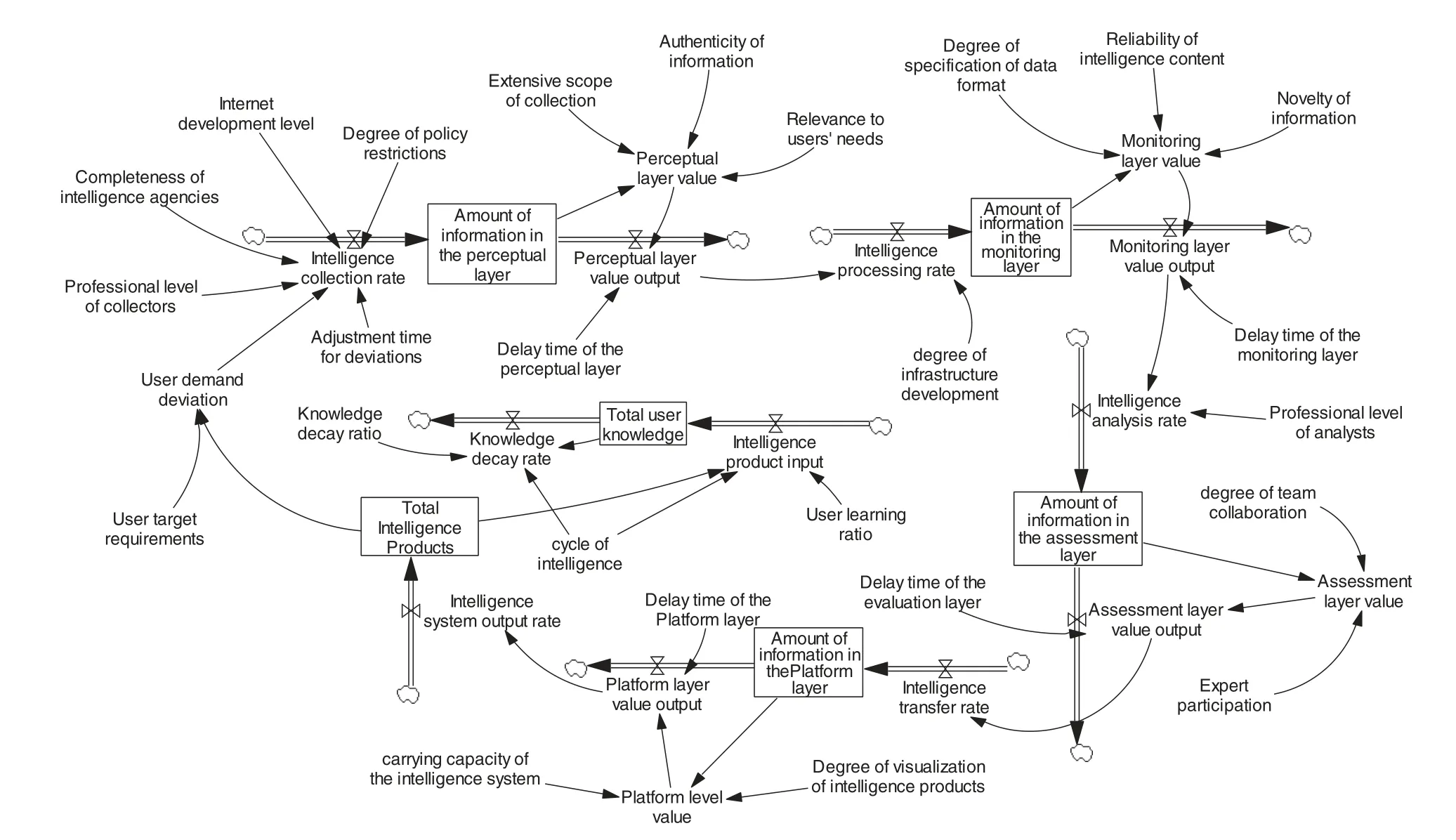
Figure 3:Flow stock diagram of the system
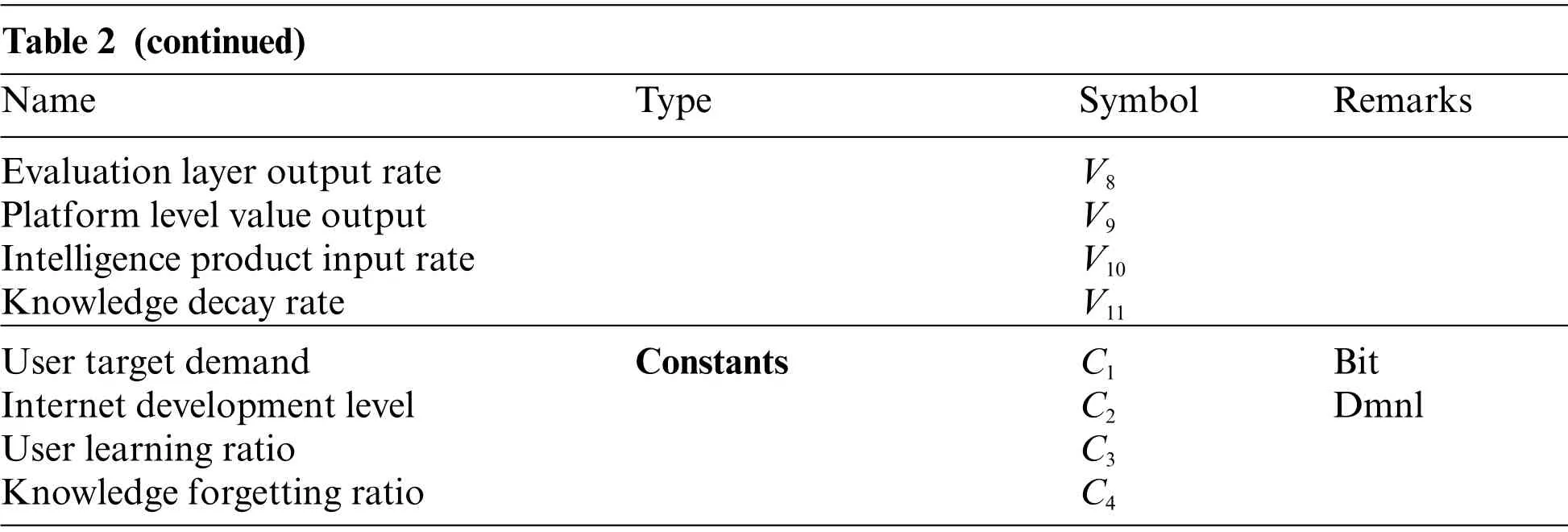
Table 2 (continued)Name Type Symbol Remarks Evaluation layer output rate V8 Platform level value output V9 Intelligence product input rate V10 Knowledge decay rate V11 User target demand Constants C1 Bit Internet development level C2 Dmnl User learning ratio C3 Knowledge forgetting ratio C4
3.4 Construction and Description of the Equation
Cause and effect diagrams and flowcharts are used to succinctly describe the logical relationships between the elements of a system, while equations are used to quantitatively analyze the dynamic behavior of the system.Constructing equations is a transformation of the model structure, which can be simulated by computer to study the dynamic characteristics implied in the model and find the methods and countermeasures to solve the problem.Therefore,referring to Soliman et al.[30]for nonlinear and linear differential equations,the main mathematical equations constructed in this paper are as follows.
3.4.1 Construction of Mathematical Equations
1.Amount of information in the perceptual layer = INTEG (Intelligence collection rate -Perceptual layer output rate,0),the symbols are expressed as:S1=Integ(V1-V6,0)
2.Amount of information in the monitoring layer = INTEG (Intelligence processing rate -Monitoring layer output rate,0),the symbols are expressed as:S2=Integ(V2-V7,0)
3.Amount of information in the assessment layer = INTEG (Intelligence analysis rate -Evaluation layer output rate,0),the symbols are expressed as:S3=Integ(V3-V8,0)
4.Total intelligence products=INTEG(Intelligence output rate,10),the symbols are expressed as:S5=Integ(V5,10)
5.Total user knowledge=INTEG(Perceptual layer output rate-Knowledge decay rate,0),the symbols are expressed as:S6=Integ(V10-V11,0)
6.Intelligence collection rate = User demand deviation * ln (1 + Internet development level * Completeness of intelligence agencies * Professional level of collectors/Degree of policy restrictions)/Adjustment time for deviations, the symbols are expressed as:V1=
7.Intelligence processing rate= Perceptual layer output rate *ln(1 + degree of infrastructure development),the symbols are expressed as:V2=V6×ln(1+D12)
8.Intelligence analysis rate = Monitoring layer output rate * ln (1 + Professional level of analysts),the symbols are expressed as:V3=V7×ln(1+D17)
9.Perceptual layer output rate=Smooth(Perceptual layer value,Delay time of the perceptual layer)/perceptual layer delay time,the symbols are expressed as:V6=smooth(D9,D10)/D10
10.Monitoring layer output rate = Smooth (Monitoring layer value, Delay time of the monitoring layer)/Delay time of the monitoring layer, the symbols are expressed as:V7=smooth(D24,D16)/D16
11.Evaluation layer output rate = Smooth (Evaluation layer value, Delay time of the Evaluation layer)/Delay time of the Evaluation layer, the symbols are expressed as:V8=smooth(D25,D20)/D20
12.Platform level value output = Smooth (Platform layer value, Delay time of the Platform layer)/Delay time of the Platform layer,the symbols are expressed as:V9=smooth(D26,D23)/D23
13.Perceptual layer value=Max(Amount of information in the perceptual layer,0)*ARCTAN(Relevance to users’needs*Reliability of intelligence content*Extensive scope of collection),the symbols are expressed as:D9=max(S1,0)×arctan(D7*D6*D8)
14.Monitoring layer value = MAX (Amount of information in the monitoring layer, 0) *ARCTAN (Degree of novelty of information * Degree of truthfulness of information *Degree of specification of data format), the symbols are expressed as:D24=max(S2,0) ×arctan(D13*D14*D15)
15.Assessment layer value = MAX (Amount of information in the assessment layer, 0) *ARCTAN (Expert participation * Degree of team collaboration), the symbols are expressed as:D25=max(S3,0)×arctan(D18*D19)
16.Platform layer value=MAX(Amount of information in the platform layer,0)*ARCTAN(degree of intelligence product visualization * intelligence system carrying capacity), the symbols are expressed as:D26=max(S4,0)×arctan(D21*D22)
17.Intelligence product input=Total intelligence products*User learning ratio/Cycle of intelligence,the symbols are expressed as:V10=(S5×C3)/D11
After several weeks, Kelly made it all the way to the yard! She positively18 glowed as the children congratulated her with gentle pats on the back and warm hugs
18.User demand deviation=IF THEN ELSE(User target demand-Total intelligence products>0,User target demand-Total Intelligence Products,0),the symbols are expressed as:D1=IfThenElse(C1-S5>0,C1-S5=0)
3.4.2 Description of Equations
Eqs.(1)–(5) set the initial values of the perception layer information volume, monitoring layer information volume,evaluation layer information volume,and total user knowledge volume to 0,and the initial value of the intelligence product volume to 10 bits.the perception layer information volume,monitoring layer information volume, evaluation layer information volume, intelligence product volume,and total user knowledge volume are all stock quantities,so they are expressed by the integral function integ(-).
Eqs.(6)–(8) set the initial values of Internet development level, open-source intelligence agency perfection,professional level of collectors,government policy restrictions,infrastructure development water,and professional level of analysts as 0.7,0.5,0.75,0.2,0.7,and 0.65,respectively,with deviation adjustment time of 2 days.Multiplication is used to indicate positive impact,and division is used to indicate negative impact.For example,the level of Internet development,the improvement of opensource intelligence agencies, and the professionalism of collectors will make the rate of intelligence collection faster,and government policy restrictions will make the rate of intelligence collection slower.The LN function is introduced to indicate that the influence of these factors on the intelligence collection rate and intelligence processing rate is not infinitely growing, and the growth rate will gradually slow down after reaching a certain level.
Eqs.(9)–(12)let the delay time of perception layer,monitoring layer,evaluation layer,and platform layer are all 1 day.There will be delay effects when intelligence is delivered in each link,for example,after intelligence collectors collect the information, they need to make preliminary screening of the information,and intelligence processors need some time to process the information to output to the next link,etc.Therefore,the information smoothing function smooth(-)is introduced.
Eqs.(13)–(16)set the initial values of relevance to user needs,authority of intelligence content,and breadth of collection to 0.8,the initial values of novelty of information,truthfulness of information,and standardization of data format to 0.9, 0.9, and 0.8, respectively, the initial values of expert participation and teamwork to 0.2 and 0.55, and the initial values of visualization of intelligence products The value of the value of the perception layer is non-negative, and the maximum function max(-) is introduced to indicate that the relevance to user needs, the authority of the intelligence content,and the wide range of collection will make the effective information of the perception layer increase,that is,the increase of the value of the perception layer,but this effect is not infinite,and there will be a peak,so Introduce the arctan(-)representation of the arctangent function.
Eq.(17) let the user learning ratio be 0.85 and the knowledge decay ratio be 0.21.After the intelligence products are handed over to customers,customers are limited by their own knowledge level and cannot completely transform the products into knowledge,so the amount of intelligence products is multiplied by the user learning ratio to represent the input amount of intelligence products,and the knowledge mastered by users will be gradually forgotten with the extension of time,so the knowledge decay ratio is multiplied by the total amount of user knowledge indicates the amount of knowledge decay.
Eq.(18) the user demand deviation amount is the user target demand minus the intelligence product amount, and the operation of the system will make the user demand deviation amount gradually decrease, and the introduction of IF THEN ELSE function makes the system stop when the user demand deviation amount is zero.
3.5 System Sensitivity Test
1.The professional level of intelligence collectors and analysts are set as(0.625,0.5),(0.75,0.65)and (0.82, 0.7) in turn, and the values of other elements remain unchanged.The simulation results are shown in Fig.4a below.
2.The degree of perfection of open-source intelligence is set to 0.4,0.5 and 0.6 in turn,and the values of other elements remain unchanged.The simulation results are shown in Fig.4b.
3.The degree of teamwork and expert participation are set as(0.3,0.1),(0.55,0.2),and(0.7,0.3)in turn,and the values of other elements remain unchanged.The simulation results are shown in Fig.4c.
4.The visualization degree of the intelligence product is set to 0.7,0.9,and 0.95 in turn,and the values of other elements remain unchanged.The simulation results are shown in Fig.4d.
The sensitivity test results in Figs.4a–4d show that the output rate of the intelligence system also changes from low to high and changes more obviously when the professional level of intelligence collectors and analysts is adjusted from low to high with the same values of other elements.The faster the output rate of the intelligence system,the more the system can meet the user’s needs in a shorter period of time, but the change is less sensitive when the values of the two parameters are reduced.Similarly,the lower the degree of teamwork and expert participation,the lower the output rate of the intelligence system,and the more significant the increase in the output rate of the intelligence system with the gradual increase in the degree of teamwork and expert participation,with a slight oscillation,while the values of other factors remain unchanged.With the same values of other elements,increasing the visualization of intelligence products,disseminating intelligence products in various ways,such as music,WeChat,videos,etc.,and presenting them to the target customers imaginatively,will make the output rate of intelligence system faster, and the more user needs can be satisfied in a short time.5 Results and analysis of the simulation
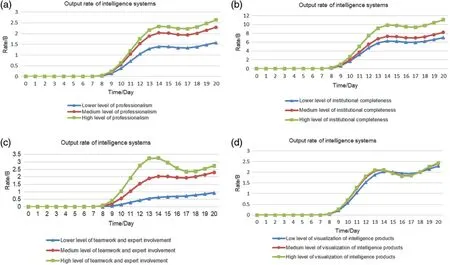
Figure 4:Graph of sensitivity test results
3.6 Simulation Results
In this paper,Vensim-PLE software is used to simulate the open-source intelligence process system model,assuming that the user’s target demand is a constant 20 bits,the intelligence cycle is 7 days,the simulation step is 1 day, and the simulation time is 20 days; the initial values of other variables are derived from the statistical almanac and multiple simulations,and the specific simulation results are shown in Table 3,Where the unit of time is day and the unit of information is bit.
From Table 3,it can be concluded that the intelligence system carries out intelligence collection work after receiving the user’s demand feedback, which makes the amount of information in the perception layer gradually increase from zero, but after one intelligence cycle, it starts to gradually decrease.The information collection link to the intelligence processing link,the information transfer of the staff in both departments and the intelligence processing itself need time, so the amount of information in the perception layer starts to increase from the second day and then gradually shows a decreasing trend.Similarly,both intelligence analysis and intelligence transmission itself take some time, so the amount of information in the evaluation layer gradually increases from the fourth day and then gradually decreases,and the amount of information in the platform layer gradually increases from the sixth day and then gradually decreases.The amount of user demand deviation is equal to the user target demand minus the amount of intelligence products, the user target demand is constant,the initial value of intelligence products is 10 bits, with the operation of the intelligence process, it gradually shows a growth trend,so that the amount of user demand deviation starts from 10 bits and gradually decreases;at the same time,after the intelligence products are generated,the user receives new intelligence knowledge so that the total amount of knowledge it has gradually increases,but the knowledge does not increase infinitely.However,the knowledge does not increase infinitely,and there exists a certain proportion of forgetting, so that the total amount of user knowledge shows a slow growth trend,and gradually reaches the peak with the growth of time.
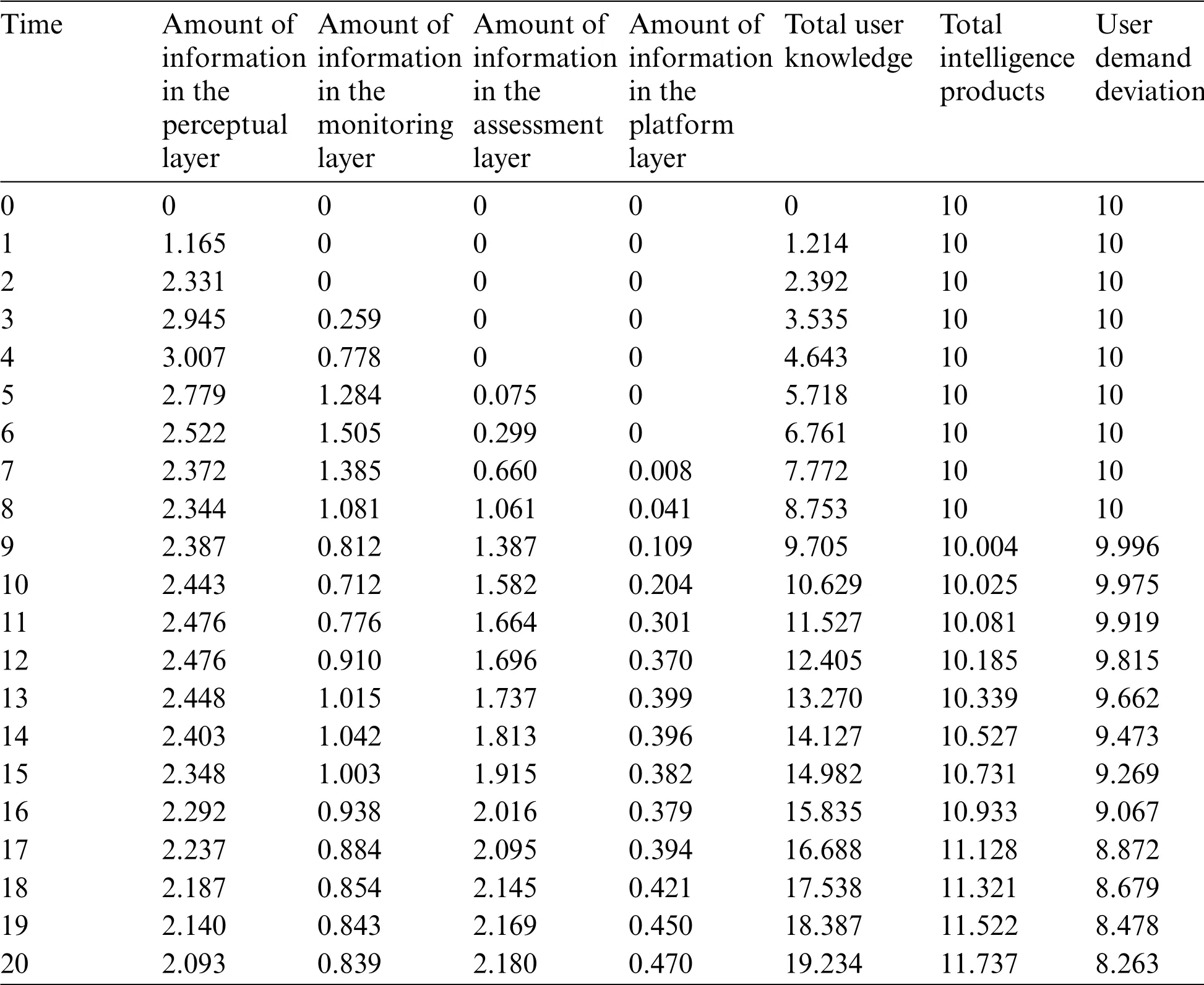
Table 3:Simulation results table
1.The degree of perfection of open source intelligence agencies,the degree of policy restrictions,the professionalism of intelligence staff and the degree of teamwork,expert involvement,and the degree of visualization of intelligence products play an important role in the intelligence process system,which improves the operational efficiency of the intelligence process system by influencing the rate of intelligence delivery in a fixed period of time,resulting in a rapid decrease in the amount of user demand deviation,and thus satisfying in a shorter time the user needs in a shorter period of time.Therefore, improving the institutional mechanism of intelligence agencies, making government affairs appropriately open, improving the professionalism of intelligence staff,strengthening the communication and cooperation among the staff of various intelligence departments,and presenting intelligence products in various forms can effectively improve the operational efficiency of the open-source intelligence process system.
2.The operation process of open-source intelligence process system is a process of creating intelligence value continuously,and this value creation occurs in all aspects of the intelligence process.The main outputs of the open-source intelligence process system are intelligence products and the total amount of user knowledge,of which the total amount of user knowledge is the total value created by the intelligence process system.
3.The extensive scope of collection, the authority of intelligence content, and the relevance to user needs are the main factors that lead to the generation of value in the intelligence collection subsystem;the degree of specification of data format,the degree of truth and novelty of information are the main factors that affect the generation of value in the intelligence processing subsystem; the degree of teamwork and expert participation are the main factors that lead to the generation of value in the intelligence analysis subsystem;the bearing capacity of the intelligence system and the degree of visualization of intelligence products are the main factors that lead to the production of value in the intelligence delivery subsystem.
4.There is a certain information delay effect in the open-source intelligence development and utilization process system due to the lack of communication and cooperation between personnel in the same department as well as across departments.
4 Conclusion
In this paper, the main factors affecting the operational efficiency of open-source intelligence systems are studied using a system dynamics approach.First, a theoretical model and a dynamics model of the open-source intelligence process system are constructed.Then, the amount of user demand deviation, the professional level of intelligence personnel, the degree of government policy restrictions, and the degree of expert participation as feedback conditions were added to the model and computer simulations were conducted; secondly, the values of some variables were changed to simulate their dynamic change curves to study the sensitivity and trend of their changes.Finally,based on the simulation results, the dynamic mechanism of the open-source intelligence process system is analyzed.In conclusion,this study reveals an efficient mode of operation of the intelligence process system in today’s rapidly developing Internet and information-exploding society, and then explores the important factors affecting the operational efficiency of the intelligence process and the dynamic mechanism of the intelligence system, so that the intelligence products can better meet the needs of users and provide some feasible suggestions for establishing a think-tank-based intelligence service system in China as soon as possible.
Data Availability:The data used in this paper is available in the paper.
Funding Statement:This paper was supported by the National Social Science Foundation of China under the project“Research on the mechanism of developing and utilizing domestic and foreign opensource intelligence under product-oriented thinking(20BTQ049)”.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computer Modeling In Engineering&Sciences2023年1期
Computer Modeling In Engineering&Sciences2023年1期
- Computer Modeling In Engineering&Sciences的其它文章
- A Fixed-Point Iterative Method for Discrete Tomography Reconstruction Based on Intelligent Optimization
- A Novel SE-CNN Attention Architecture for sEMG-Based Hand Gesture Recognition
- Analytical Models of Concrete Fatigue:A State-of-the-Art Review
- A Review of the Current Task Offloading Algorithms,Strategies and Approach in Edge Computing Systems
- Machine Learning Techniques for Intrusion Detection Systems in SDN-Recent Advances,Challenges and Future Directions
- Cooperative Angles-Only Relative Navigation Algorithm for Multi-Spacecraft Formation in Close-Range
