A Secure Three-Party Authenticated Key Exchange Protocol for Social Networks
Vivek Kumar Sinha,Divya Anand,,Fahd S.Alharithi and Ahmed H.Almulihi
1Department of Computer Science and Engineering,Lovely Professional University,Phagwara,Punjab,144411,India
2Department of Computer Science,College of Computers and Information Technology,Taif University,Taif,21944,Saudi Arabia
Abstract: The 3PAKE (Three-Party Authenticated Key Exchange) protocol is a valuable cryptographic method that offers safe communication and permits two diverse parties to consent to a new safe meeting code using the trusted server.There have been explored numerous 3PAKE protocols earlier to create a protected meeting code between users employing the trusted server.However,existing modified 3PAKE protocols have numerous drawbacks and are incapable to provide desired secrecy against diverse attacks such as manin-the-middle,brute-force attacks,and many others in social networks.In this article, the authors proposed an improved as well as safe 3PAKE protocol based on the hash function and the symmetric encryption for the social networks.The authors utilized a well-acknowledged AVISPA tool to provide security verification of the proposed 3PAKE technique, and findings show that our proposed protocol is safer in opposition to active as well as passive attacks namely the brute-force, man-in-the-middle, parallel attack, and many more.Furthermore, compared to other similar schemes, the proposed protocol is built with a reduced computing cost as our proposed protocol consumes less time in execution and offers high secrecy in the social networks with improved accuracy.As a result,this verified scheme is more efficient as well as feasible for implementation in the social networks in comparison to previous security protocols.Although multifarious authors carried out extensive research on 3PAKE protocols to offer safe communication,still there are vital opportunities to explore and implement novel improved protocols for higher safety in the social networks and mobile commerce environment in the future in opposition to diverse active as well as passive attacks.
Keywords: AVISPA tool; 3PAKE protocol; hash function; symmetric encryption;social networks
1 Introduction
Due to fast advancement in information as well as diverse networking technologies, pragmatic client authentication plays a vital role to safeguard services and multifarious resources from being cracked via unauthorized clients [1–5].The 3PAKE (Three-Party Password-Based Authenticated Key Exchange) protocol permits two diverse clients over unsecured channels to have a talk for safe session codes and set up a safe channel through an authenticated server to secure their consequential communication [6–9].Each of the legal clients stockpiles their scrutinizer calculated from their real key in the database of the isolated trustworthy servers and every client just needs to recall only words of identification i.e.,an authentication key with a trustworthy server[10–12].There have already been identified multifarious benefits of the 3PAKE protocols earlier by numerous researchers in past from security perspectives,however,one of the key benefits of this protocol recognized by some researchers is that it offers an easy method for a huge number of client-to-client communication settings,in addition,every client does not demand to recall numerous keys for diverse clients who converse with each other[13–15].Furthermore,the 3PAKE protocol has a wide scope to implement in diverse electronics applications as well as in the social networks to safeguard the confidential information of the clients as demanded in the modern world [16–18].There are multifarious benefits of the 3PAKE protocols usages in numerous applications,in addition to this,3PAKE protocols provide mutual authentication as well as a safe information exchange e.g., authenticated trusted server helps in communications among buyers as well as sellers in e-commerce,etc.
In this article, an inexpensive 3PAKE protocol is developed for social networks utilizing hash function and symmetric encryption jointly to increase performance by reducing protocol executing rounds yet maintaining the equivalent protection capabilities as previous methods without relying just on a secret key of the server.Our proposed 3PAKE protocol is inexpensive as well as more robust against diverse attacks such as replay assaults, cryptanalysis assaults as well as man-in-the-middle assaults.To aid in the creation of our enhanced 3PAKE protocol for authenticity as well as privacy validation,the AVISPA verification software was used.Our enhanced 3PAKE protocol is subjected to a quantitative effectiveness study.
The origins of computing networks as well as the Internet may be found dated in the 1960s as well as early 1990s,correspondingly.Cellular phones began to link to the Internet through wireless channels in the 20thcentury,and WiFi connections,numerous websites including several mobile apps are now available on a variety of gadgets,including smart mobiles,global positioning systems(GPS)gadgets,and many more.Access control has been recognized as the fundamental data protection problem in social network infrastructure that comprises authentication as well as authorization.Cyber-security threats are the most serious obstacles which computing systems, as well as social networks, face,in addition, access control has been identified as a key secrecy threat in the social networks.The authentication process is recognized as a vital element that provides safety to an apparatus, system,or application from illegal access directly or indirectly.Nowadays,security and privacy are becoming a key challenge due to diverse assaults over a network during information exchange particularly in social networks environment around the world.
However, earlier various researchers have been provided multifarious strategies to prevent various assaults such as man-in-the-middle assault, replay assault, and cryptanalysis assaults over the networks.But, existing protocols and strategies have certain limitations such as high computation complexity and more time-consuming that demands more attention towards novel cost-effective protocols that take minimal communication steps and search time.To commence with, just one element was utilized to validate participants in the network; although, such a method, especially in the scenario of credentials,may be readily hacked.Users often utilize similar credentials across many platforms,namely Gmail,Twitter,and Facebook.An unauthorized client may immediately hack any customer’s profile,as well as a hacker may employ well-known techniques like gusting as well as social engineering to get entry to diverse system’s resources and applications rather than the authorized client.To safeguard the customer’s profile against unwanted assaults, password authentication techniques based on the hash function and symmetric encryption must be utilized jointly to provide additional secrecy as demanded nowadays against diverse assaults.
2 Related Work
There has been done extensive research earlier on 3PAKE protocols to provide desired secrecy and confidentiality against diverse assaults.The following discussion would provide an overview of the limitation of existing protocols.
Chang et al.in[19],described an effective 3PAKE protocol rooted on LHL-3PAKE suggested by the author’s Lee et al.This protocol does not need any public key as well as symmetric cryptosystems.This scheme has numerous limitations like in case of a missing session key,this would never disclose alternative session key as well as lack of mutual authentication among users and authenticated servers.Ruan et al.in[20],described another LR eCK secrecy prototypical for 3PAKE as well as suggested an improved LR 3PAKE scheme,after that presented formal secrecy evidence in the typical model.This approach is suitable and easy to implement in numerous applications and wireless networks,however,this protocol has certain restrictions namely high computation complexity,and offers secrecy only in conventional prototypical wherein no outflow assaults exist.Li et al in[21],analyzed Farash-Attari’s scheme and depicts how their scheme does not provide resistance against secure code disclosure assault if the secure data is kept on the authenticated server side.The authors eliminated existing threats of Farash-Attari’s scheme in this work, however, the suggested method provides secrecy only in the communication overhead scenario and in computation complexity environment.
Farash et al.in [22], disclosed the drawbacks of the Lee et al.secrecy scheme suggested earlier and analyzed the need for further improved 3PAKE protocols for enhancement in a more pragmatic manner.The authors proposed a modest countermeasure that preserves computation as well as communication efficacy of existing protocol suggested earlier,however,this proposed scheme does not provide enough secrecy against multifarious assaults namely man-in-the-middle and several others in social networks scenario.Zhang et al.in [23], investigated verified-rooted 3PAKE scheme analyzed its design,wherein authenticated server keeps secure code verifier in comparison to plain secure code.However,the suggested approach does not offer required secrecy against directory assaults and manin-the-middle assaults in the model of the social network.Xie et al.in [24], suggested an enhanced 3PAKE scheme that is rooted in chaotic maps.This protocol offers certain advantages over existing secrecy schemes that are based on authenticated server public secrecy keys, however, the proposed protocol is less efficient and has more computation complexity in the social networks.
Lin et al.in[25],proposed another lightweight as well as lower computational complexity 3PAKE scheme rooted on exclusive OR (XOR) operation to provide secrecy against impersonation assaults and many others.This protocol is suffered from the shared key loss over authenticated servers due to the fast enhancement of numerous services namely cloud as well as ubiquitous computing,gadgets comprising lower computation power,and many more.Amin et al.in[26],suggested another effective 3PAKE scheme utilizing the smart card and rooted on cryptography hash function.The authors explored existing literature to identify the key challenges related to information loss during communication due to various assaults.Although, this investigated protocol is best fit only in the mutual authentication among clients and servers but has huge computation complexity in practical implementations in multifarious applications.Shu et al.in[27],proposed another enhanced 3PAKE that offers gigantic communication efficacy and provides enhances secrecy level in numerous scenarios and applications.However, this protocol comprises certain limitations related to the secrecy of the social network.Chen et al.in[28],suggested another improved 3PAKE scheme that is rooted on the chaotic-map for the enhanced secrecy level.But the suggested scheme is vulnerable in the environment of the social network due to multifarious assaults such as man-in-the-middle assaults and relay assaults.Lone et al.in [29], discussed the OTP (One Time Password) based user authentication approach in their research.The suggested scheme was implemented and validated using the androidrooted mobile phones to attain the desired secrecy.However, the suggested method has certain drawbacks such as user data leakage in case of OTP misuse and not much reliable in case of confidential data exchange over social networks.
3 Research Contributions
In this paper,a novel 3PAKE protocol has been developed for the social networks which utilize the hash function as well as symmetric-key encryption technique to enhance the performance parameters such as parseTime,searchTime,depth of plies,and visited nodes by minimizing the protocol executing rounds and offers higher secrecy against diverse attacks such as brute-force, man-in-the-middle,and parallel attack.The major contributions of our research are to design an improved and novel 3PAKE protocol that takes less time in execution, lowest computation complexity, as well as robust against diverse attacks,and is communication efficient in a pragmatic manner.However,multifarious researchers have done pragmatic work to design various secrecy protocols during the last decade to provide offer the desired secrecy to the users during the communication,but the existing protocol has certain disadvantages and does not offer the required secrecy in the modern world against various attacks such as man-in-the-middle,brute-force attacks,and several others.Therefore,considering this issue we designed a novel 3PAKE protocol that is based on the hash function and symmetric key encryption technique to offer the higher secrecy as well as consumes very little time that is required to manage the high-volume traffic over the social networks.
4 Research Methodology
When the medium of transmission is public networks, the major goals of networks privacy are verification of interacting users as well as the secrecy of sent information.As a result, numerous 3PAKE algorithms have already been created to accomplish such security standards at the same time.The 3PAKE algorithms permit two diverse users to validate one another by a secure server and further evaluate a confidential session code through a public network.In this work,the authors utilized the under-mentioned parameters to design the proposed 3PAKE protocol based on the hash function and symmetric encryption for higher secrecy and privacy of the social networks.
4.1 Notions Used
Sarepresents a trusted server.CAand CBare two diverse users who want safe communication with one another with the assistance of the Sa.In this work,the authors utilized Diffie-Hellman Key Exchange(DHKE)scheme to design the suggested 3PAKE protocol based on the hash function and symmetric encryption.The DHKE is a way of safely interchanging cryptographic codes via a public channel.Our suggested protocol has been constructed utilizing the DHKE scheme,therefore,a definite cyclic cluster(CG,e,f)must be chosen,that is originated via a component e of prime order f.Nuis a number that is arbitrarily chosen through user CBfor assurance of the newness.The Nuis frequently a pseudo-random or an arbitrary number allotted in a verification protocol to confirm that the previous message could not be utilized again under diverse assaults.Tab.1 illustrates the notations used and their definitions.
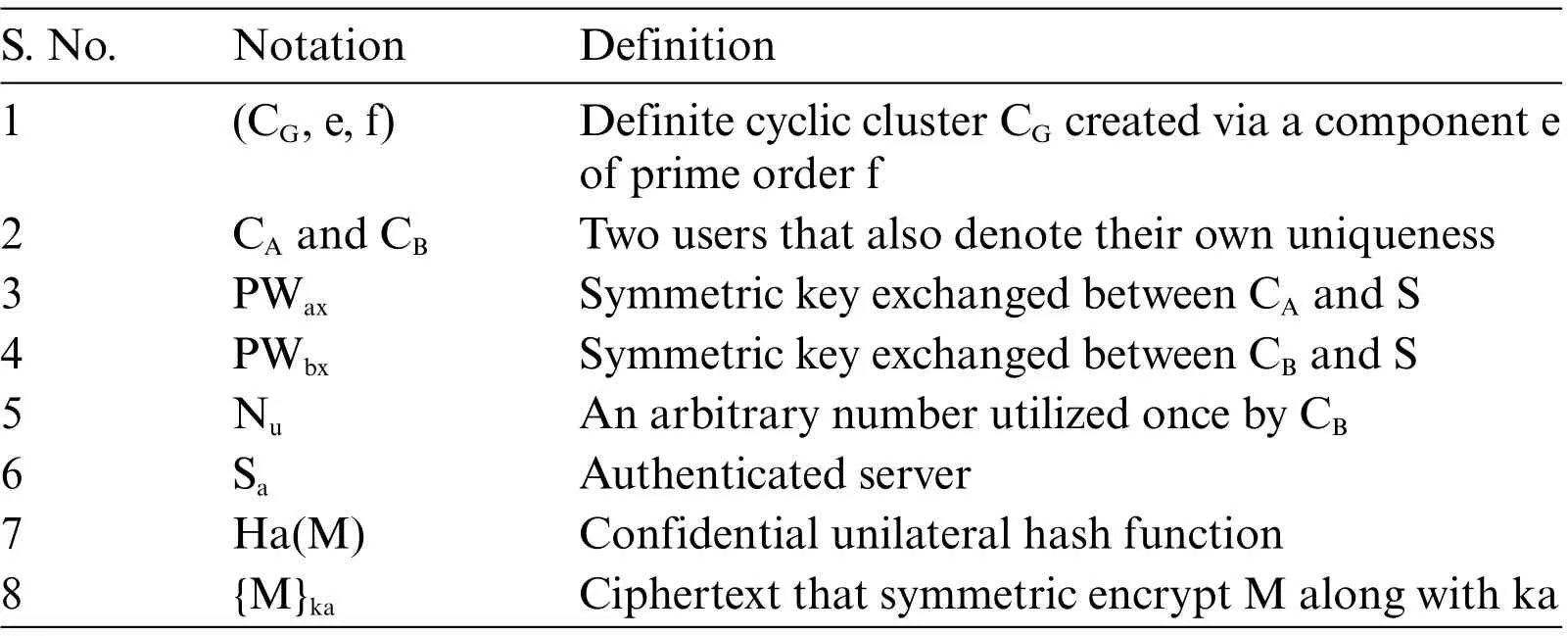
Table 1: Illustrates the notations used and their definitions
4.2 Enhanced 3PAKE Protocol
Using our enhanced protocol two users CAand CBdesire to exchange a fresh session code Ckwith aid of server Safor the next message.There is no direct authentication between user CAand user CB.They have to recourse to authenticated server Safor the contract of sessions secure codes.
Fig.1 illustrates the flow diagram of our enhanced 3PAKE protocol for the social networks using a hash function and symmetric encryption.The description of the steps of our suggested 3PAKE protocol are given in detail as follows:
Step 1:CAselects an arbitrary number an∈Tp,evaluatesdanas well as one instance code Ha(CA,dan,PWax),obtains,REQA=CA,dan,{CA,dan}Ha(CA,dan,PWax)then forwards REQAto CB.
Step 2:By obtaining a piece of information from CA,CBinitially verify the uniqueness ofdanand after that CBselects an arbitrary number bn∈Tpand number utilized once Nu,evaluatesdbnand one instance code Ha(CB,dbn, PWbx), obtains, REQB= CB,dbn, {CB,dbn}Ha(CB,dbn,PWbx)then forwards REQAand REQBto the authenticated server Sa.
Step 3:By obtaining REQBand REQA,authenticated server Sainitially verifies the uniqueness of thedananddbn, after that authenticated server Sautilize obtaineddananddbnto evaluate Ha(CA,dan, PWax) and Ha(CB,dbn, PWbx) order by and after that decrypts the REQAand REQBto verify and validatedananddbn.In case of,failed authentication,this session stopped,otherwise authenticated server Saselects an arbitrary number vn∈Tp,evaluatesdanvn=(dan)vn,dbnvn=(dbn)vnand obtains CAKa={dan,CB,dbnvn,Nu}Ha(CA,dan,PWax),CAKb={dbn,CA,danvn,Nu}Ha(CB,dbn,PWbx),and lastly forwards CAKaand CAKbto the CA.
Step 4:CAdecrypts CAKa,obtainsdanvnand Nu,evaluates CK=(dbnvn)an=danbnvn,then obtains{CA,Nu,dan}CK,and forwards CAKb,{CA,Nu,dan}CKto CB.
Step 5:By obtaining CAKb,{CA,Nu,dan}K,initially CBdecrypts CAKbto obtaindanvnand after that authenticatedbn,furthermore,CBevaluatesCK=(danvn)bn=danbnvnand after that decrypts{CA,Nu,dan}CKto authenticate Nu.
Step 6:Finally,the user CAand user CBidentify the fresh session codeCKfor further conversation and eliminate the chances of information losses in social networks during communication.
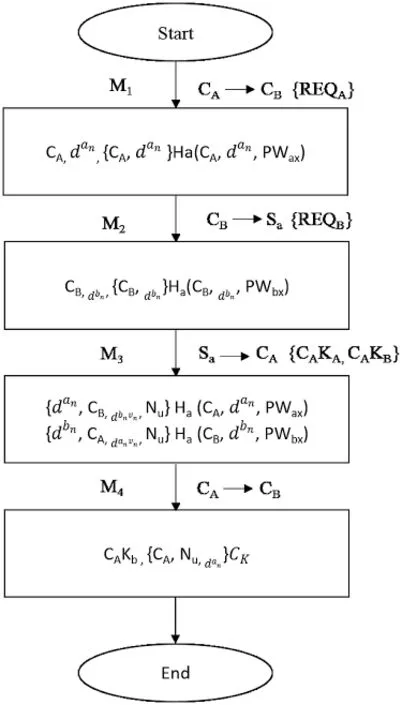
Figure 1:Illustrates the flow diagram of our enhanced 3PAKE protocol for the social networks using a hash function and symmetric encryption
The overall procedure of the proposed 3PAKE protocol is summarized as follows.The client CAcan authenticate the server Saand the client CBcan authenticate the server Sarespectively by individual authentication invitations REQAand REQBand the response CAKa,CAKb.The client CAand client CBvalidate each other name with the help ofdanand Nu.In all the transferred messages,information despatcher individuality is involved for the client CAand client CB.The accurate client authentication is the first priority in the communication over social networks in order to provide the desired secrecy to the clients via authenticated server Sa.In order to provide the required secrecy to each and every client, a unique code word is assigned to all clients during the communication that is embedded in the distributed information which is transferred over the networks in the form of distributed messages via authenticated server.The suggested 3PAKE protocol is more robust against diverse attacks such as brute-force,man-in-the-middle,parallel attack,because our protocol mutually authenticates the client CAand CBas well as authenticated server Sa.
4.3 The AVISPA Tool
Our enhanced 3PAKE protocol for social networks is modeled and validated in the most popular AVISPA(Automated Validation of Internet Security Protocols and Applications)tool to authenticate diverse secrecy and privacy properties that our enhanced 3PAKE protocol was modeled to own.AVISPA toolkit is simply working using the push button to verify the internet secrecy and privacysensitive multifarious applications as well as protocols.HLPSL (High-Level Protocol Specification Language)is linguistic in which the diverse secrecy protocols are written in widely popular AVISPA software.Within HLPSL,numerous security protocols parameters are separated among roles.There are basic roles that are used to define the activities of a stand-alone agent during the execution of protocols or numerous sub-protocols.Several termed the composed roles, use such fundamental roles that describe a full protocol cycle, as well as protocols session among several agents, or the protocols models itself.Such a job is frequently referred to as an environmental role.In this article,authors specified their security goals using a collection of roles that describe protocol as well as an environmental role to define particular sessions which performance researchers want to evaluate.
5 Results and Discussion
By utilizing the AVISPA toolset to do privacy assessment as well as validation,authors prove that their suggested 3PAKE algorithm is trustworthy and therefore can operate appropriately for the social networks for higher secrecy and privacy as needed.
5.1 Enhanced 3PAKE Protocol Specifications
In the suggested 3PAKE protocol design that is defined in the HLPSL language,the basic roles are three namely the pekc_CA,pekc_CB,pekc_Sa,which represent the user CA,CB,and the authenticated server Sa, respectively.Herein we are presenting the one basic role that is Saas illustrated in Fig.2.The authenticated server Sastands by to obtain the REQB,REQAfrom the user CBand then forwards CAKAand CAKBto CA.At the similar instance state Stof the authenticated server,Sawill be altered via 0 to 1.There are certain symbols utilized in the basic role Saare described in Tab.2.
5.2 Security Analysis of Suggested 3PAKE Protocol
Initially, the authenticated server Saobtains a message (CB.Gy’.{CB.Gy’.Nb’}_Hash (CB.Gy’.PWbx).CA.Gx’.{CA.Gx’}_Hash(CA.Gx’.PWax)via Rcv()function.After that,authenticated server Sa, selects an own arbitrary number Nz’ as well as evaluates Gxz’.Lastly, authenticated server Saforwards message {Gx’.CB.Gyz’.Nb’}_Hash (CA.Gx’.PWax).{Gy’.CA.Gxz’}_Hash (CB.Gy’.PWbx)via Snd ( ) function.In this article, the authors utilized the DHKE scheme for the designing of the suggested 3PAKE protocol based on the hash function and symmetric encryption for the social network’s privacy and secrecy.After defining basic roles instantly,there is a requirement to describe the composed roles that further define the new sessions for the suggested 3PAKE protocol.Fig.2 illustrates the role of the authenticated server Safor the suggested 3PAKE protocol for the social networks secrecy verification.Fig.3 illustrates the session role for the suggested 3PAKE protocol for the social networks secrecy verification.

Figure 2:Illustrates the role of the authenticated server Sa for the suggested 3PAKE protocol for the social networks secrecy verification
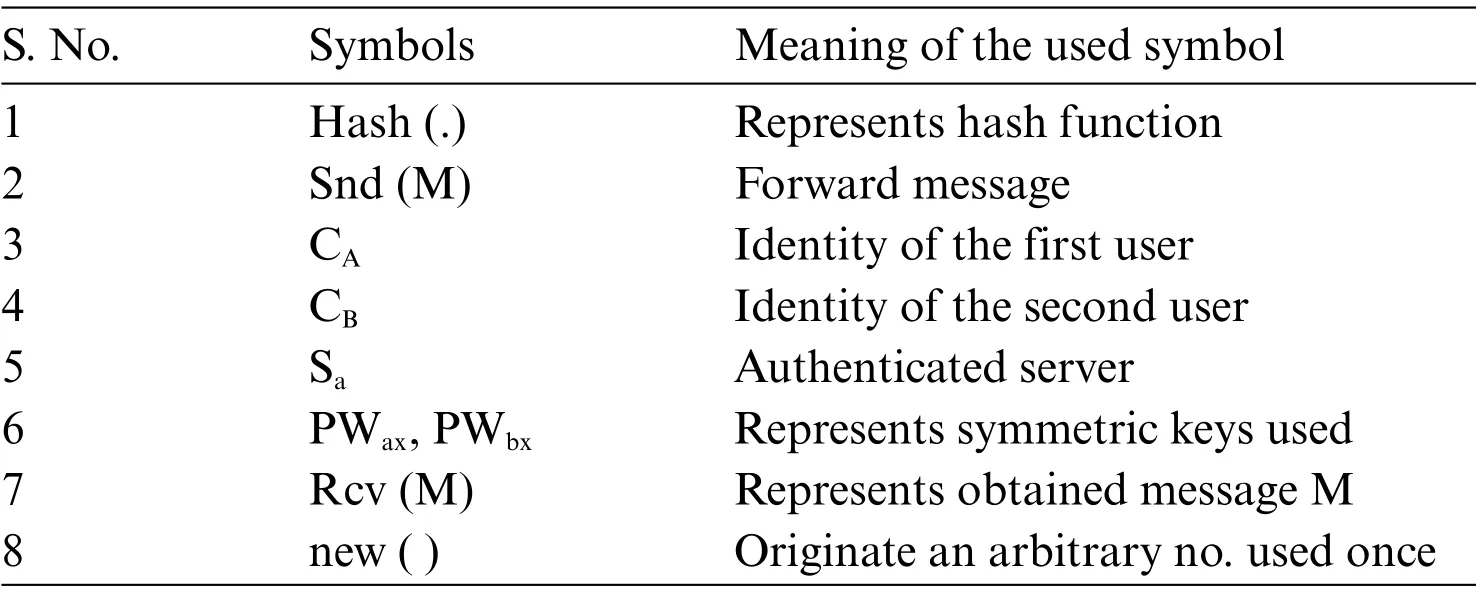
Table 2: Illustrates the symbols used in the Sa role
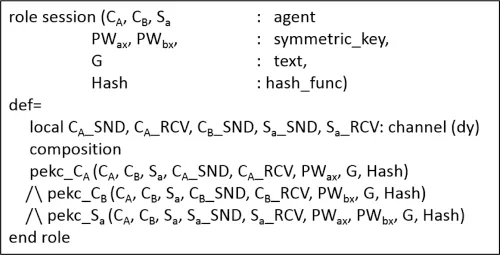
Figure 3:Illustrates the session role for the suggested 3PAKE protocol for the social networks secrecy verification
5.3 Informal Security Analysis
Within all session’s fragments,every basic role namely the pekc_CA,pekc_CB,as well as pekc_Sahave been instanced with solid logic.In the end, a high-level role is an environment at all times described.The environment role comprises universal constants as well as an arrangement of one or further sessions.Fig.4 illustrates the environmental role of our suggested 3PAKE protocol for the social networks secrecy verification.Herein,i is utilized to represent the intruder that takes part in the implementation of the suggested 3PAKE protocol utilizing a solid session.It is utilized for the detection of man-in-the-middle assaults.Herein,statement category channel(dy)symbolizes the intruder prototypical namely the Dolev-Yao model.By utilizing this model,the interloper has overall control of the network in such a manner that every message forwarded by the users would pass via the interloper.This interloper can analyze or enhance coming messages as soon as get to know demanded codes.As a result, users can transmit as well as receive data on any route they wish; the intended relationship among specific channels characteristics is preserved.
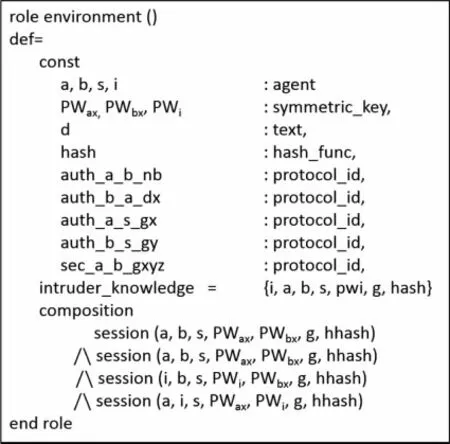
Figure 4:Illustrates the environmental role for the suggested 3PAKE protocol for the social networks secrecy verification
Fig.5 illustrates the analysis goals for the suggested 3PAKE protocol for the social networks secrecy verification.We have analyzed the under-mentioned properties that are considered within the goal section.Herein symbol auth_CA_SA_gx means user CAvalidates Saover gx.Fig.6 illustrates the simulation outcomes by OFMC back-end for the suggested 3PAKE protocol for the social networks secrecy verification.

Figure 5:Illustrates the analysis goals for the suggested 3PAKE protocol for the social networks secrecy verification
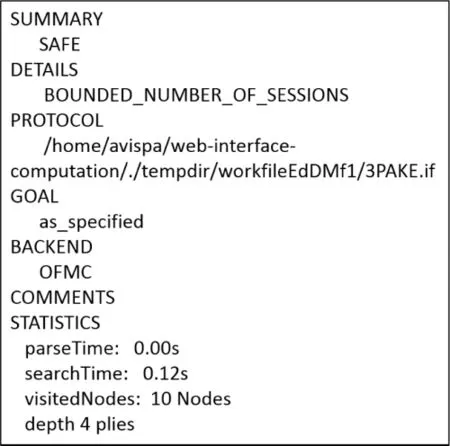
Figure 6:Illustrates the simulation outcomes by OFMC back-end for the suggested 3PAKE protocol for the social networks secrecy verification
Several 3PAKE protocols have been investigated in the past to generate a secure meeting code between users using a trustworthy server.However,existing modified 3PAKE protocols have various flaws and are unable to guarantee necessary anonymity in social networks against a variety of attacks such as man-in-the-middle, brute-force assaults, and others.In this article, the authors developed an enhanced and novel 3PAKE protocol that offers additional secrecy in social networks to offer higher secrecy as well as privacy as demanded in the modern world from various assaults between communications.All the experimental work was carried out on a personal computer installed with window 10 and comprising of a 64-bit operating system, 16 GB RAM (Random Access Memory),and an i7 processor.For the performance validations of the suggested 3PAKE protocol for social networks,we utilized a widely popular AVISPA toolset for the simulation.
5.4 Performance Evaluation
Fig.6 illustrates the simulation outcomes by OFMC back-end for the suggested 3PAKE protocol for the social networks secrecy verification.Tab.3 illustrates the outcomes and comparative analysis of the suggested 3PAKE protocol along with other existing protocols for the social networks.Islam et al.[30]protocol takes 0.00 s parseTime,communication steps 5,search time 0.66 s,depth plies 6,and the visited nodes 16.Pak et al.[31]protocol consume parse time 0.00 s,communication steps 5,search time 8.94 s,depth plies 6 and visited nodes number 1690.After simulation,the proposed 3PAKE protocol offers parseTime 0.00 s,searchTime 0.12 s,depth of 4 plies,visited nodes 10,and communication steps 2 that shows all parameters are reduced from the existing protocols,therefore our suggested 3PAKE protocol provides very little computation complexity along with reduced search time for the client’s authentication over the server Sa.The parseTime gives the information regarding the initialization time of protocol execution for the authentication of clients and server.Initially, it is set to be 0.00 s to count the searchTime of clients and authenticated server in an efficient manner.Moreover, our proposed algorithm is more robust against diverse assaults namely the man-in-the-middle,replay,and cryptanalysis assaults, and many more.Our suggested 3PAKE protocol for social networks offers forward security.Any agreed code would not be compromised in case of even agreed codes derived via similar long-term coding substances throughout the succeeding run have been compromised.In our suggested 3PAKE protocol,components an,bn,and vnare arbitrarily chosen as well as self-governing to proposed 3PAKE protocol execution.Hence,compromised secret code PWax,PWbx,as well as CKcould not disclose the earlier session codes.
6 Conclusion
In this article,the authors proposed a novel and low-cost 3PAKE protocol based on the hash function and symmetric encryption for social networks that offer additional secrecy for the confidential key as well as a session key, shared verification between users including the uniqueness of conveyed message and lastly faultless forward security for the session key.Our suggested 3PAKE protocol shows that it is highly efficient in comparison to the earlier modified protocols and provides less computation complexity along with reduced computations steps.This proposed 3PAKE protocol is simulated and a formal verification was done by using a widely popular AVISPA toolset.The proposed 3PAKE protocol takes parseTime 0.00 s,searchTime 0.12 s,depth of 4 plies,visited nodes 10,and communication steps 2,indicating that all parameters have been reduced from existing protocols.As a result,our proposed 3PAKE protocol is more robust and offers a very low computation complexity.Our recommended 3PAKE protocol is appropriate in a wide range of applications,particularly in resourceconstrained situations as well as in real-time systems.However, several researchers have modified 3PAKE protocols for diverse applications in past but there are vital possibilities of more investigation on 3PAKE protocol in the future for further modification for mobile commerce environment for optimal outcomes.
Acknowledgement:This project was supported by the Taif University Researchers Supporting Project Number(TURSP-2020/347),Taif Unversity,Taif,Saudi Arabia.
Funding Statement:This project was funded by the Taif University Researchers Supporting Project Number(TURSP-2020/347),Taif Unversity,Taif,Saudi Arabia.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computers Materials&Continua2022年6期
Computers Materials&Continua2022年6期
- Computers Materials&Continua的其它文章
- Echo Location Based Bat Algorithm for Energy Efficient WSN Routing
- Rainfall Forecasting Using Machine Learning Algorithms for Localized Events
- Coronavirus Detection Using Two Step-AS Clustering and Ensemble Neural Network Model
- Human Faces Detection and Tracking for Crowd Management in Hajj and Umrah
- Optimal Hybrid Feature Extraction with Deep Learning for COVID-19 Classifications
- Exploration of IoT Nodes Communication Using LoRaWAN in Forest Environment
