6G-Enabled Internet of Things:Vision,Techniques,and Open Issues
Mehdi Hosseinzadeh,Atefeh Hemmati and Amir Masoud Rahmani
1Pattern Recognition and Machine Learning Lab,Gachon University,Seongnam,13120,Korea
2Department of Computer Engineering,Science and Research Branch,Islamic Azad University,Tehran,1477893855,Iran
3Future Technology Research Center,National Yunlin University of Science and Technology,Yunlin,64002,Taiwan
ABSTRACT There are changes in the development of wireless technology systems every decade.6G(sixth generation)wireless networks improve on previous generations by increasing dependability,accelerating networks,increasing available bandwidth,decreasing latency,and increasing data transmission speed to standardize communication signals.The purpose of this article is to comprehend the current directions in 6G studies and their relationship to the Internet of Things(IoT).Also,this paper discusses the impacts of 6G on IoT,critical requirements and trends for 6G-enabled IoT,new service classes of 6G and IoT technologies,and current 6G-enabled IoT studies selected by the systematic literature review(SLR)method published from 2018 to 2021.In addition,we present a technical taxonomy for the classification of 6G-enabled IoT,which includes self-organization systems,energy efficiency,channel assessment,and security.Also,according to the articles reviewed,we consider the evaluation factors in this domain,including data transmission,delay,energy consumption,and bandwidth.Finally,we focus on open issues and future research challenges in 6G-enabled IoT.To mention important future challenges and directions,we can point to migration,data storage, data resource, data security, data sharing, data offloading, availability, scalability, portability, user experience,reliability,authentication,and authorization.
KEYWORDS Internet of Things;6G;wireless network;machine learning;artificial intelligence
1 Introduction
The International Telecommunication Union (ITU) standardizes wireless generations every decade.The next generation of wide-area wireless technology,6G,will impact IoT technologies.Many sensors,vehicles,automobiles,drones,and robots may be connected in the IoT era,making the world sharper and smaller.
6G is the replacement of 5G technology.6G networks will utilize greater frequencies than 5G networks,resulting in significantly increased capacity and reduced latency.One of the 6G internet aims will allow one-microsecond latency communication[1].The possibility of 5G to allow a significant shift of the IoT has been an important selling point.However,many of these applications are thought to be at least a few decades away since they rely on 5G requirements yet to be defined.Another roadblock to 5G has been the speedvs.distance issue of the high-frequency or millimeter-wave spectrum.It can transmit vast amounts of data at high speeds but struggles to travel long distances and penetrate certain materials due to its shorter wavelength[2].
Future 6G communication systems would also significantly outperform the current 5G communication system.IoT can be a critical component of 5G and beyond communication systems[3].IoT and Mobile Edge Computing(MEC)technologies play an essential role in people’s daily lives by allowing them to control and monitor objects, changing how people interact with the physical world.Due to its decentralized nature, blockchain can be a valuable tool for addressing IoT issues.Blockchain technology is critical for realizing the promise of 6G networks and meeting current and future needs[4].
Unmanned aerial vehicles(UAVs)are getting very popular,opening up new commercial opportunities for cellular networks.6G networks have significantly increased data transmission rates and system capacity.Furthermore,existing technologies such as transmission use distinct communication protocols to create IoT-enabled UAVs that meet 6G standards.The combination of UAV and satellite provides a potential solution to technological limitations, system integration, and network complexity[5].
IoT is one of the industries that will benefit the most from deploying 6G networks.Many IoT applications are prevented from becoming a reality due to current mobile network limitations in latency, throughput, and device density.IoT is a technology that connects physical devices to and from the Internet to collect and share data.Washing machines, cell phones, refrigerators, wearable devices, headphones, self-driving cars, televisions, and other products are examples of these devices.5G networks are not expected to meet all future requirements in the next decade and beyond, and 6G networks are estimated to deliver worldwide coverage,improved spectral,energy,cost efficiency,higher intelligence,greater security,and other benefits.
Even if these IoT-enabled applications improve people’s lives,supporting them will be a difficult challenge for 5G.6G investigates novel communication methods in the absence of existing network technology.It contains new ideas,methods,and solutions to support current and future applications.A smart connection,deep connectivity,holographic connectivity,and normal connectivity distinguish the 6G system[6].
6G enables IoT devices to wirelessly transmit data collected from their neighborhoods to support several new applications.A 6G network solves some of the shortcomings of the 5G network;as a result,advancements in non-public communications increase smart platforms in the 5G networks, such as industry Internet,remote education,healthcare,and smart homes and cities.IoT plays a critical role in enabling these new platforms throughout this paradigm shift[7].
In the field of 6G and IoT,many published articles can be divided into several subgroups,which are as follows: Security of 6G in IoT [8-10], IoT applications of healthcare using 6G technology[11-13], IoT applications of the smart city using 6G technology [14-16], IoT applications of smart transportation using 6G technology [17-19], IoT applications of wearables using 6G technology[20,21],integration of machine learning and 6G-enabled IoT[22,23],6G and IoT networks[1,24,25]and energy-efficient effect on 6G enabled IoT[26-28].
Several survey papers are available, but they are not systematically focused on 6G-enabled IoT[3-5].Therefore,in this paper,we presented an SLR method for a high-level overview of 6G-enabled IoT to address the following weaknesses: Most existing studies do not offer any taxonomy for 6Genabled IoT.In most of the reviewed articles, the method of research selection was not mentioned.Also,some studies do not mention factors or metrics in IoT domains used to evaluate the impact of 6G-enabled IoT.
The paper’s main contributions are as follows:
• Drawing a taxonomy to organize various aspects of 6G-enabled IoT
• Presenting some Research Questions(RQs)and answering them about 6G-enabled IoT
• Discussing future research directions and open issues in the 6G-enabled IoT domain
The remainder of the article contains the following sections: the overviews of related work are mentioned in Section 2.Section 3 discusses the purpose of this study and provides further details on how to choose relevant work and how to categorize the content.Section 4 presents various analytical comparisons of previous research articles.Section 5 summarizes current research activities,trends,and outstanding topics for further study.Section 6 is the conclusion.
2 Definition and Related Work
The related definitions are presented in Section 2.1,and a summary of the associated studies on 6G and IoT is presented in Section 2.2.
2.1 Related Definitions and Review of Concepts
2.1.1 Related Definitions
Table 1 defines important evaluation factors and basic terms definitions used in 6G-enabled IoT research.
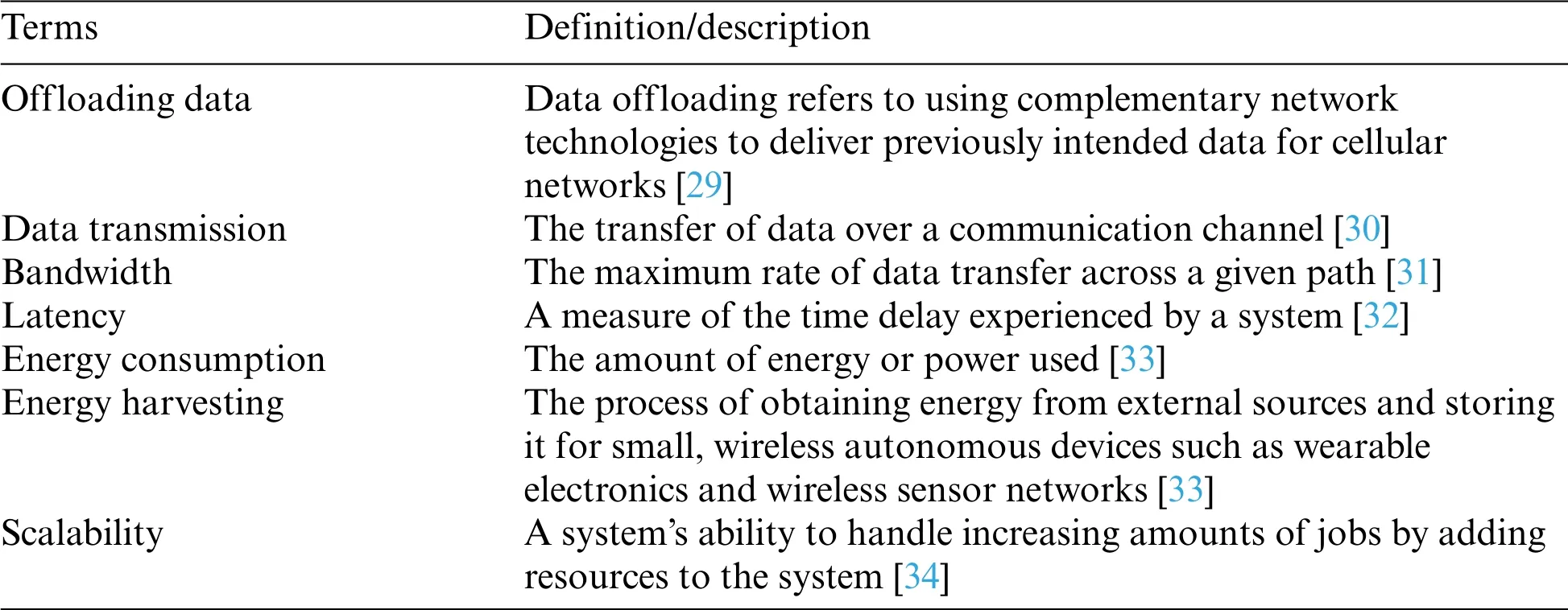
Table 1: Definition of evaluation factors and essential terms definitions in the 6G-enabled IoT
2.1.2 Review of Concepts
Special features are required for communicating with smart devices.With the growth of the connections impacting the world around us these days,we will soon have a new aspect of life to use.Different generations of information transmission technologies in mobile networks include 1G, 2G,3G,4G,5G,and,shortly,6G.The“G”stands for“Generation”,and as the number increases with the letter,the concept is that the technology used in the previous generation of G has been enhanced,and we are now faced with new features[35-37].
Fig.1 shows a history of communication networks that; in the following, we summarize each generation of communication networks.
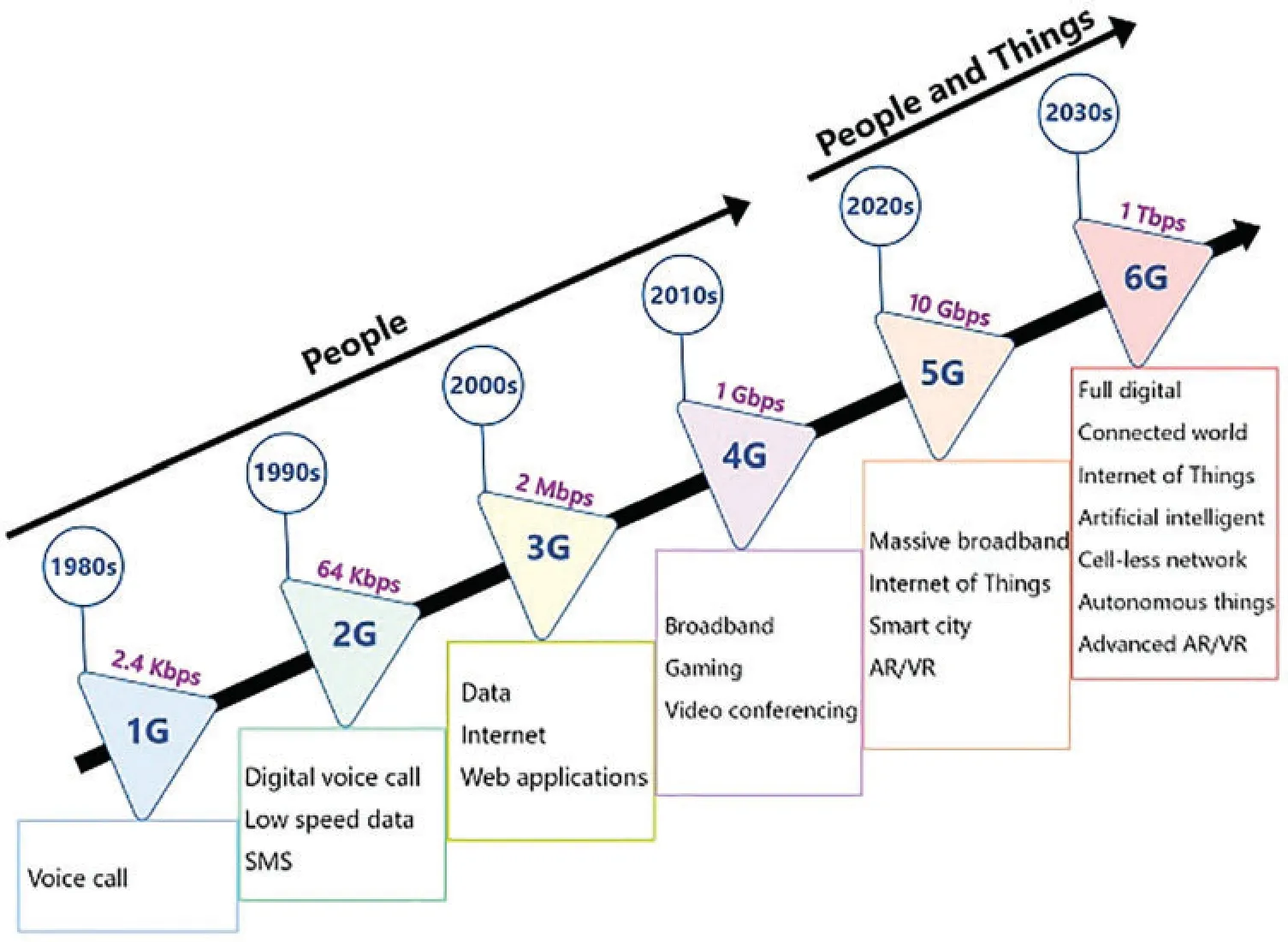
Figure 1:Development of communication networks
First Generation(1G)
1G was an analog-based technology that first appeared in the 1980s.1G was the first generation of wireless cellular technology,and it could only enable voice calls,with no simple messaging services(SMS) or data transfer capabilities.The main disadvantage of this service was that it received noise from its surroundings,resulting in poor data transfer quality and speed.The maximum speed of 1G technology was only 2.4 kbps[6].
Second Generation(2G)
Instead of analog,2G focused on digital technologies.2G capabilities were achieved by allowing the user to channel into a channel via multiplexing.We can mention protected digital phone calls,more efficient in the long-distance spectrum for probe-level mobile phones, SMS, video messaging,and multimedia messaging services(MMS)as 2G advancements and advantages.The maximum speed of 2G technology was only 64 kbps[38].
Third Generation(3G)
With the passing of time and growing requirements such as transmitting and receiving huge multimedia files, video conferencing, playing online games, and so on, the 3G wireless mobile communications technology was created with a multimedia approach.The 3G improvements over the previous generation include high-speed Internet connection, making a video call with someone,video download, mobile phones with the ability to receive TV images, and making a wide range of digital content available on the mobile network platform.The maximum speed of 3G technology was only 2 Mbps[38].
Fourth Generation(4G)
In addition to all of the standard 3G features, 4G can provide users with bandwidth-enhancing services for Internet access.So that using a wireless modem in laptops can be connected to smartphones and other mobile devices.Other services offered in the 4G generation include improved mobile browsers, IP technology, high-quality mobile TV, high-quality video conferencing, enhanced online gaming services,3D TVs,and cloud computing technology.The main goal in launching the 4G was to increase the capacity,speed,and quality of services,expand the covered areas and reduce costs[39-41].The maximum speed of 4G technology was only 1 Gbps[38].
Fifth Generation(5G)
After 4G,5G is the next generation of wireless communication.It can connect everything,such as humans, robots, cars, and even everyday things.5G technology provides tremendous speed, very low latency,a more secure network,more access,and improved performance,resulting in a new and perfect user experience[40-42].
Usage of 5G technology includes:
• High-speed download and upload
• More stability in sending and receiving files
• Development of self-driving cars
• Possibility of remote surgery
• Development of IoT
• Network slicing
• Less and more efficient energy consumption
The maximum download speed on the 5G network is up to 20 Gbps,and the maximum upload speed is up to 10 Gbps[38].
Sixth Generation(6G)
The sixth generation of wireless communication technologies supporting mobile data networks is 6G technology.This technology is considered to be a 5G replacement.6G networks,like previous generations,are broadband cellular networks with small geographic service areas.5G was introduced in 2019, and by 2030, it is predicted to be the most widely used mobile communication technology.Although this is an estimate, an initial 6G deployment might begin between 2030 to 2035.The maximum speed of 6G technology is predicted to be 1 Tbps[41-43].
The IoT will be characterized as the internet of everything shortly, resulting in tremendously vast connections that will put 5G networks in the investigation.Users are searching for 6G wireless communication networks because they hope they will be human-centered, full-bandwidth, highly secure, and smart everywhere.6G networks were intended as the disruptive technology in the next generation of wireless communication systems, meeting the constraints of limiting data speeds encountered by many data apps on present 5G networks.Some of the essential radical technologies in 6G,in conjunction with the existing 5G option concepts,provide the quality of desired experience for establishing universal wireless Internet connection from the communications sector to the digital smart industry.The IoT has begun to convert the present industry into an intelligent infrastructure with a 6G data-driven architecture.Presently,6G technology is in adolescence,with many unresolved challenges.
The most obvious difference between the 5G and 6G technologies is speed.6G uses higher-tech radio hardware and more volume and bandwidth than 5G,including ultra-high frequency spectrum,which offers ultra-high speed and,across short distances,large capacity.
While the 5G of artificial intelligence is used to optimize, allocate dynamic resources and data processing, the delay is lower than a millisecond.Because of its distributed design, 6G will provide complete intelligence.
Due to the challenges of developing IoT devices for 5G networks,we will experience 6G networks in the coming decade.Some of the challenges are as follows: First of all, the need for bandwidth increases with the demand and use of cloud computing, the need for bandwidth, and the speed of the Internet.Failure to address these requirements with the revelation of 6G may lead to many problems.Second,there is big data management.As IoT technologies gain acceptance and demand,data management for 5G networks is becoming more sophisticated.Industrial IoT devices are expected to last for many years,even under challenging conditions,and the increasing demand for bandwidth and security from these devices alone is driving this trend.As time passes,the 6G network should pay attention to this issue.Finally,as 5G technology enhances device mobility with IoT technologies,data security becomes more sensitive than ever[6,39,42].
In the following years, the influence of IoT devices on 5G networks will become increasingly apparent.The mentioned challenges demonstrate how the IoT might disrupt 5G networks.
Fig.2 shows 5G and 6G interaction with IoT,just like 5G and IoT today are considered together,6G will most likely give us a whole new viewpoint on wireless Internet.6G networks look to be another revolution,much as 5G networks were designed to develop the IoT platform and are likely to redefine Internet connectivity[44,45].Naturally,because there is still a long way to go until 6G networks are established and commercialized,the primary purposes and functions of this sort of high-speed network are unknown.Because 6G is significantly more efficient than 5G,low-power IoT devices may even be charged through the network,an established economy.Changes the mass and helps to keep the network stable.As 4G and 5G have been together for a while and contain a central network,6G and 5G will likely work together for a while[6,42].
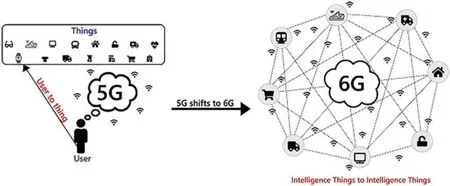
Figure 2:6G and IoT interaction
With the advancement of IoT and the emergence of 5G networks,as shown in Fig.2,5G starts to connect users with things.As a result, 5G’s ability to deliver communication services to people and things has been enhanced.Also,with the advancement of 6G technology,intelligence things and intelligence things will be able to communicate in the future.
2.2 Related Studies on 6G and IoT
Guo et al.[7]presented a study on 6G-enabled massive IoT that mention the following goals:
1.To summarize the requirements for developing IoT-enabled applications, as well as the limitations of 5G.
2.To demonstrate 6G visions for use cases,essential needs,and trends.
3.To create an innovative network architecture for 6G to allow massive IoT.
4.The motivations, applications, and outstanding issues of 6G technologies, such as ML and blockchain,were discussed.
5.A completely autonomous driving sample was provided to demonstrate how 6G enables massive IoT.
Deebak et al.[5] reviewed the integration of IoT wireless technologies, satellites, and UAVs to represent the IoT application paradigm.Significant concerns about future 6G technologies were thoroughly investigated to assess cellular networks’capabilities.This study has the advantage of introducing the concept of 6G communication systems by presenting a possible application scenario and the technology involved.The primary drawback of this survey is that the research taxonomy was not proposed.
Chowdhury et al.[3] presented widespread research on how optical wireless communication technologies can be used to deploy future 6G and IoT networks successfully.It also defined the terms 5G,6G,and IoT systems.Each 5G,6G,and IoT requirement was discussed in-depth and how optical wireless communication(OWC)systems support such functionality.The benefit of this study is that it provides valuable and comprehensive statistics on studies and efforts in the context of 6G and IoT.The study’s disadvantage is that there is no explanation of the related work.
Sekaran et al.[4] addressed the significant challenges in integrating Blockchain and IoT technologies with a 6G communication network to provide high-level solutions by overcoming IoT and Blockchain technology limitations.The study’s considerable point is that blockchain technology designed for IoT networks performs poorly due to increased communication overhead, energy consumption, and execution time.In some research approaches, data confidentiality and integrity are also insufficient.Also, they presented future research recommendations for blockchain-enabled IoT with 6G communication.The lack of taxonomy is the paper’s disadvantage.However,the article points to most of the necessary information from related works.
Barakat et al.[46]developed a novel approach by presenting various IoT use cases in the industry that demonstrate various performances.The use cases chosen from the most active research fields benefit from 6G and technologies enabled by 6G.Healthcare,smart grid,transportation,and industry are among these industries.The primary criteria of the scenarios were also discussed and how they relate to the main factors for the next generation of wireless networks.This review has the advantage of presenting open problems and challenges in the context of the 6G relation to IoT.
Zhang et al.[47]presented 6G visions with three parts:artificial intelligence,super IoT,and mobile ultra-broadband.They also reviewed key technologies to achieve each part.The basic principles,significant issues,and solutions for each technology were then presented.
Gupta et al.[48]examined the approaches for assessing dependability and predicting availability used in developed modeling 6G.Wireless systems are creating new wireless communication applications that make use of cloud computing,edge computing,and fog computing.In the recent decade,technologies such as IoT have been utilized to construct various consumer and provider networks.
Based on a comprehensive review of the literature and survey research, Table 2 summarizes the related survey studies on 6G-enabled IoT issues.Table 2 lists the main topic, publication year,publisher, covered year, open issues, paper review type, and main contributions and drawbacks for each study.
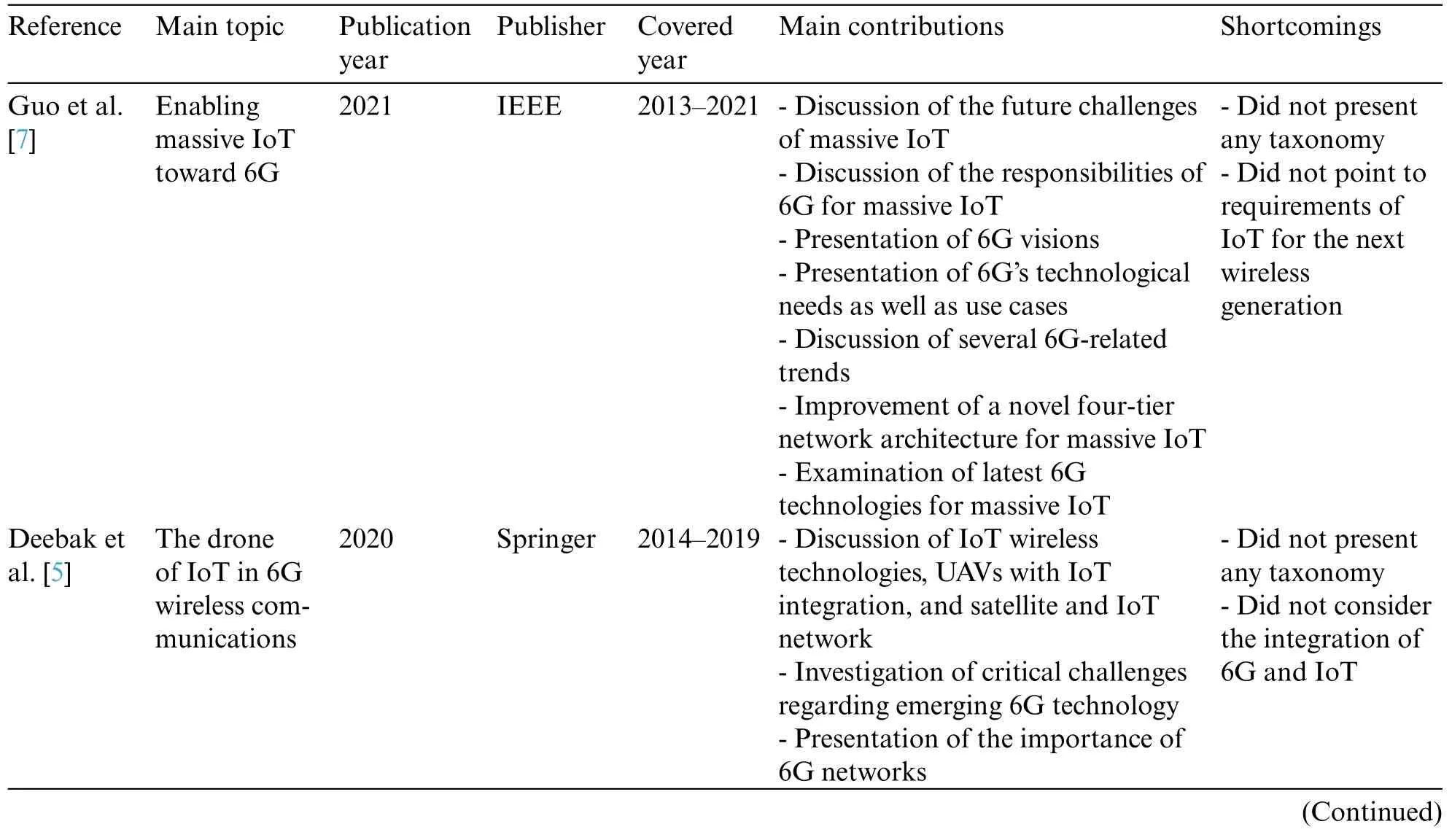
Table 2: Relevant studies of 6G-enabled IoT
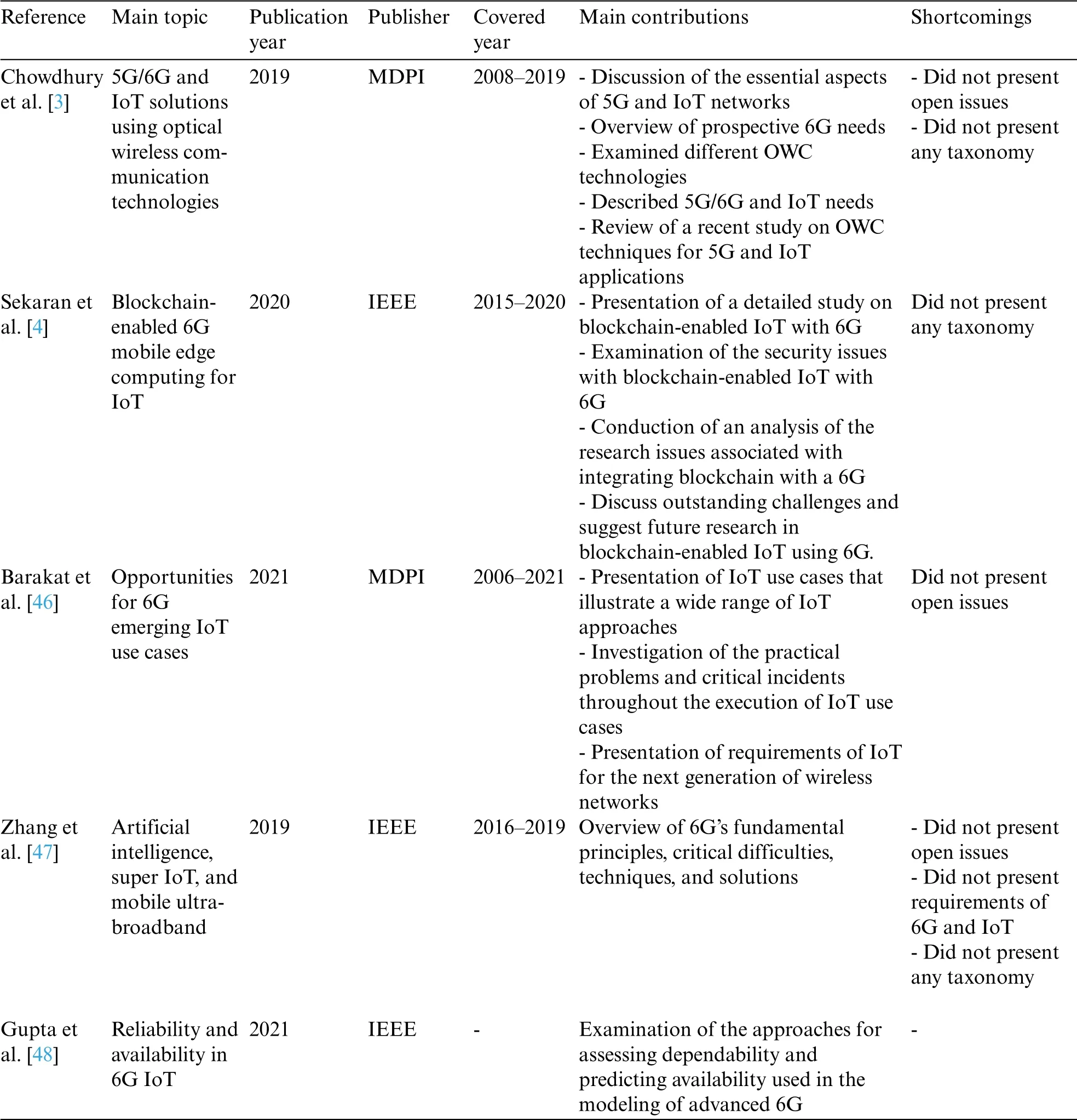
Table 2 (continued)
3 Method of Research Selection
This section provides an overview of the 6G-enabled IoT classification method based on the SLR process.
Sections 3.1 and 3.2 describe the research objectives and database selection and search terms,respectively.
3.1 Research Goals and Research Questions
The purpose of this section is to clearly state the RQs that are expected to be found in the area of“6G-enabled IoT”.This SLR paper aims to answer the following RQs because of the importance of the chosen topic and other factors,such as the lack of a comprehensive paper on the selected subject.
RQ1:What are the critical requirements and trends for 6G-enabled IoT?
RQ2:What are the most essential 6G enabling technologies for IoT that require further investigation?
RQ3: What new service classes are available in the 6G-enabled IoT domain? And why do these services need to be provided?
RQ4:What are the evaluation factors or metrics used in IoT domains to measure the impact of 6G in IoT?
RQ5:What are the future research directions and open issues in the 6G-enabled IoT domain that need to be addressed?
3.2 Database Selection and Search Terms
Fig.3 shows exploration string was defined in terms of synonyms and other alternatives for the required key components:

Figure 3:Search terms
When selecting the final articles,the following inclusion guidelines are taken into account:
• The relevant studies published after 2018
• All 2021 available articles
• More relevant articles
When selecting the final articles,the following exclusion guidelines are taken into account:
• Articles published before 2018
• The studies were not written in English
Finally,as described in Section 5,39 peer-reviewed articles were chosen to answer the previously specified RQs.The goal of our study,which is based on a systematic review,is to investigate the current strengths and achievements in the field of 6G-enabled IoT while also introducing open issues for future research.Fig.4 depicts the research strategy,which is divided into five stages.
Fig.5 illustrates a complete taxonomy of 6G-enabled IoT aspects, including self-organization systems,energy efficiency,channel assessment,and security.
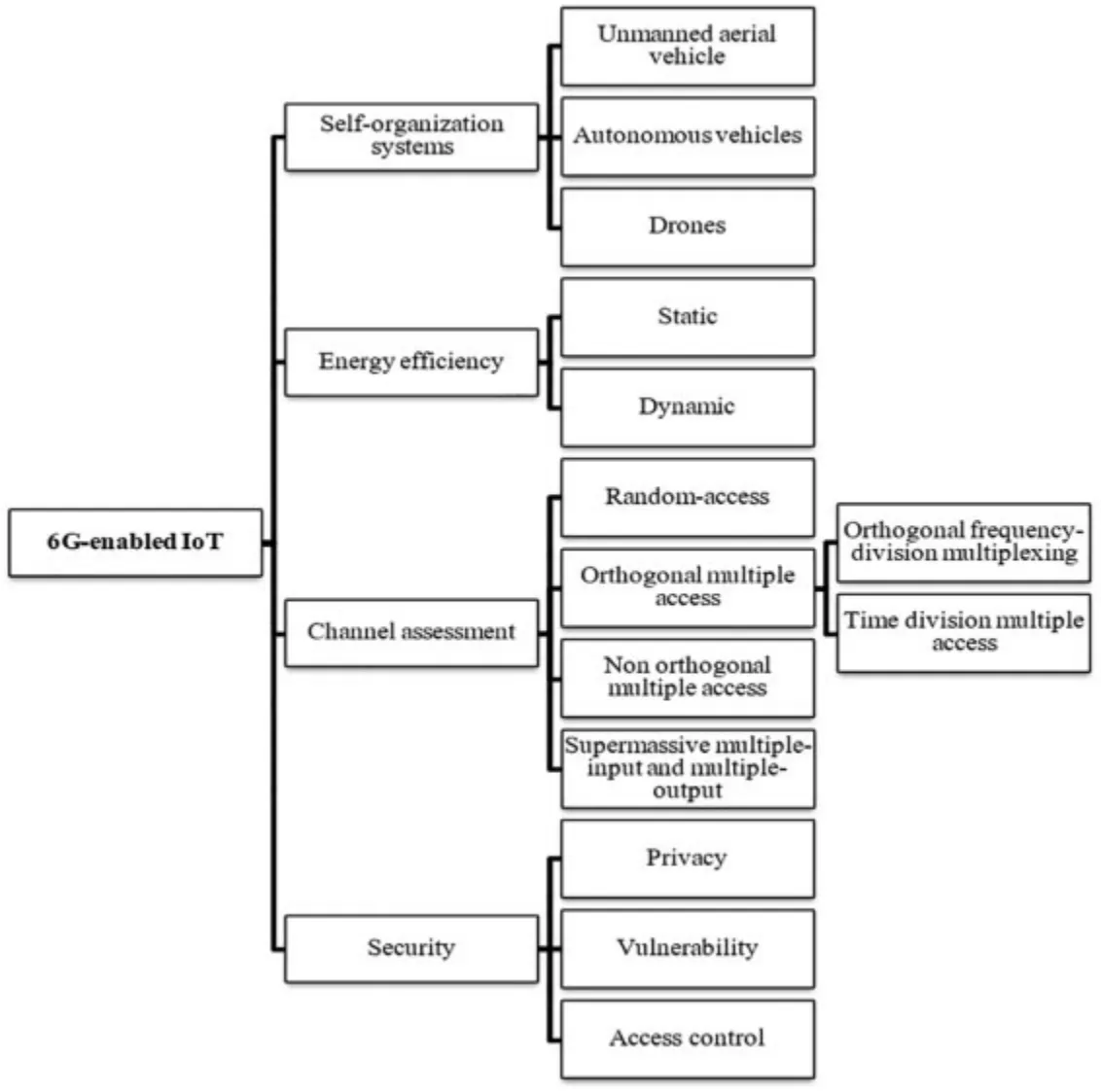
Figure 5:The taxonomy of 6G-enabled IoT
4 Organization of 6G-Enabled IoT
This section provides a technical overview of the 6G-enabled IoT chosen for recent studies using the SLR process.
The studies in this paper were classified into four categories: self-organization systems, energy efficiency,channel assessment,and security.Furthermore,the studies were compared with the main context,discoveries,app domain,case studies,benefits,and drawbacks.
4.1 Self-Organization Systems
Table 3 shows the classification of the analyzed articles of the self-organization systems category in 6G-enabled IoT,including the following subcategories:
• Unmanned aerial vehicle
• Autonomous vehicles
• Drones
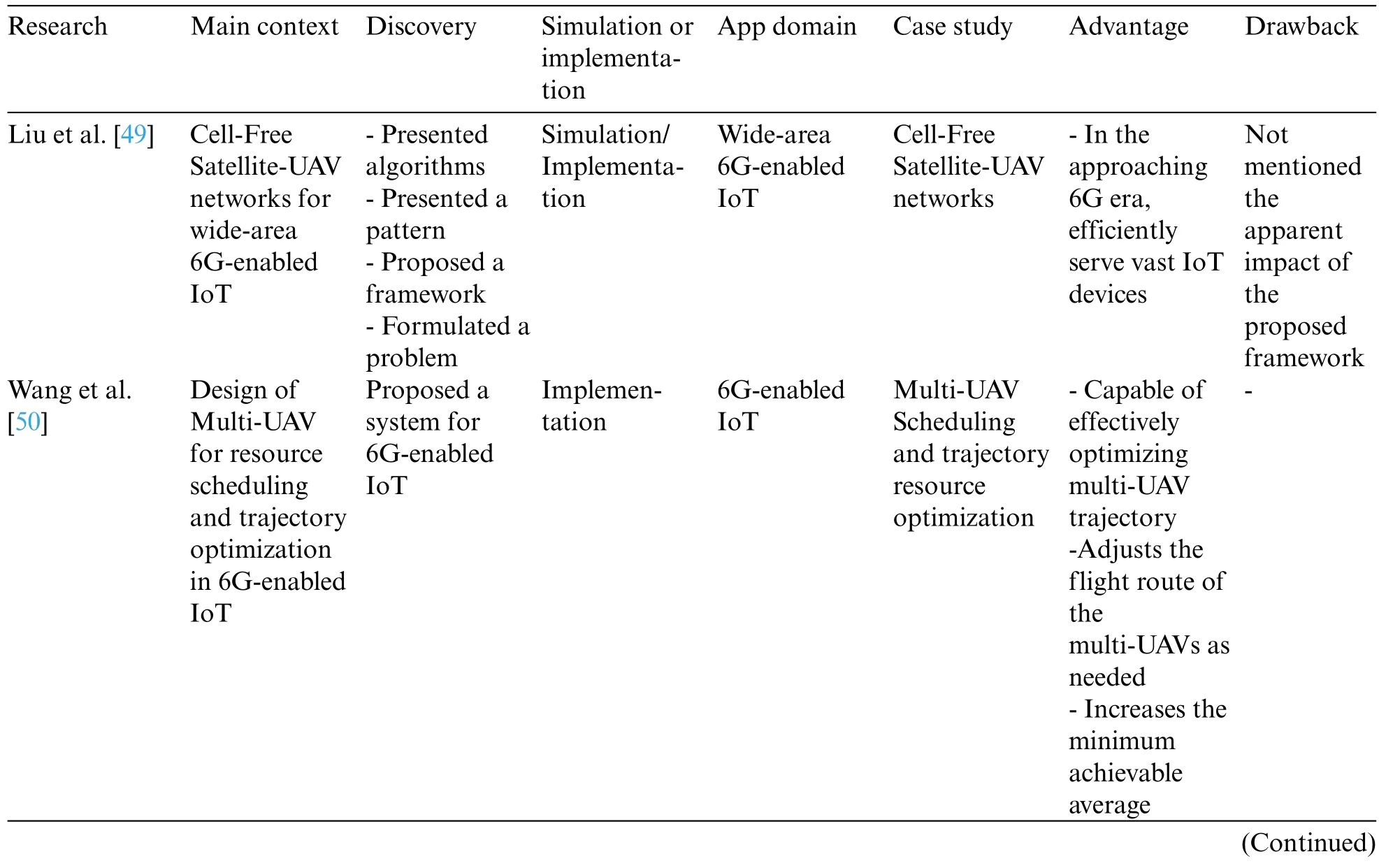
Table 3: Analyzed articles in the self-organization systems classification
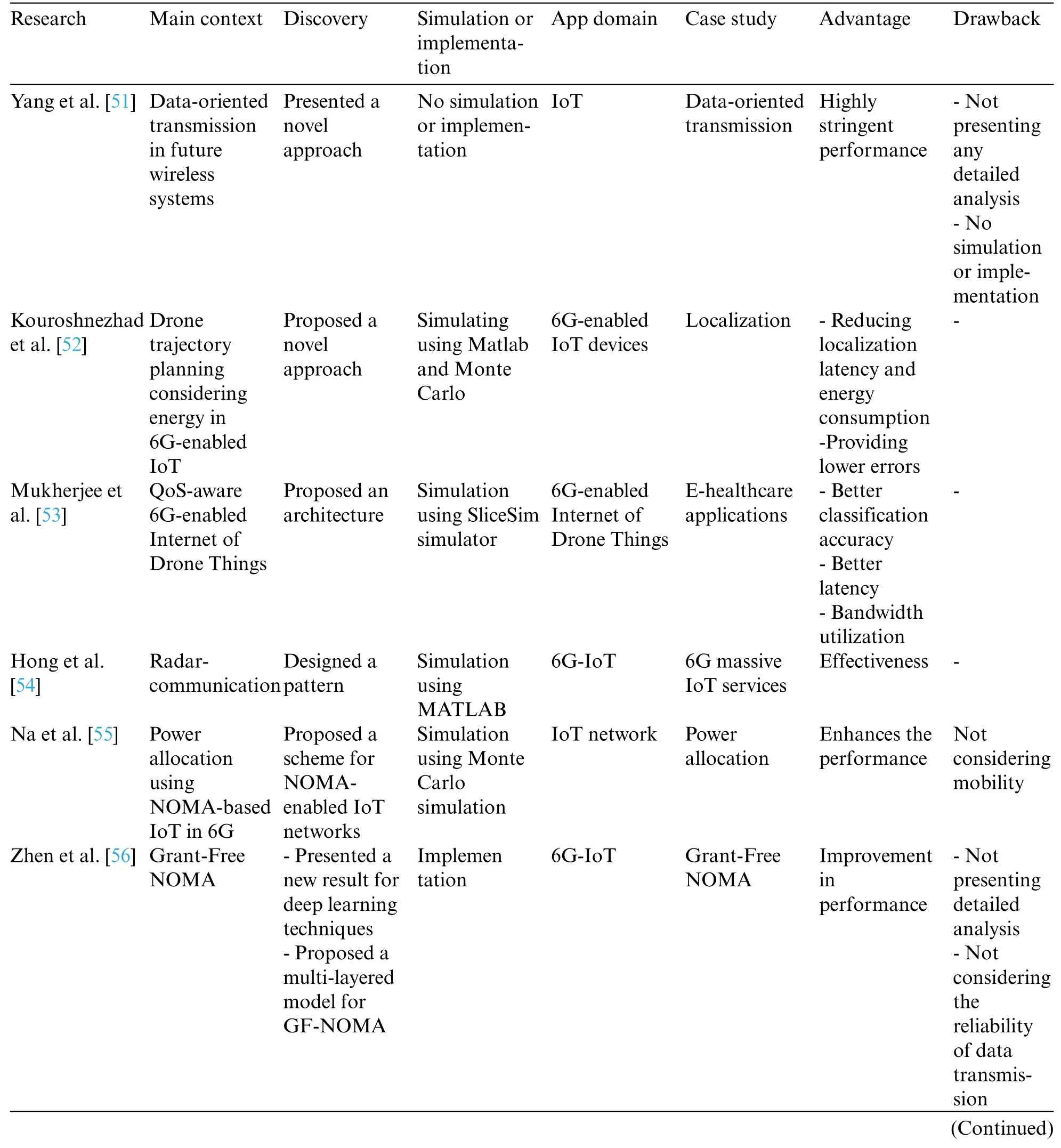
Table 3 (continued)
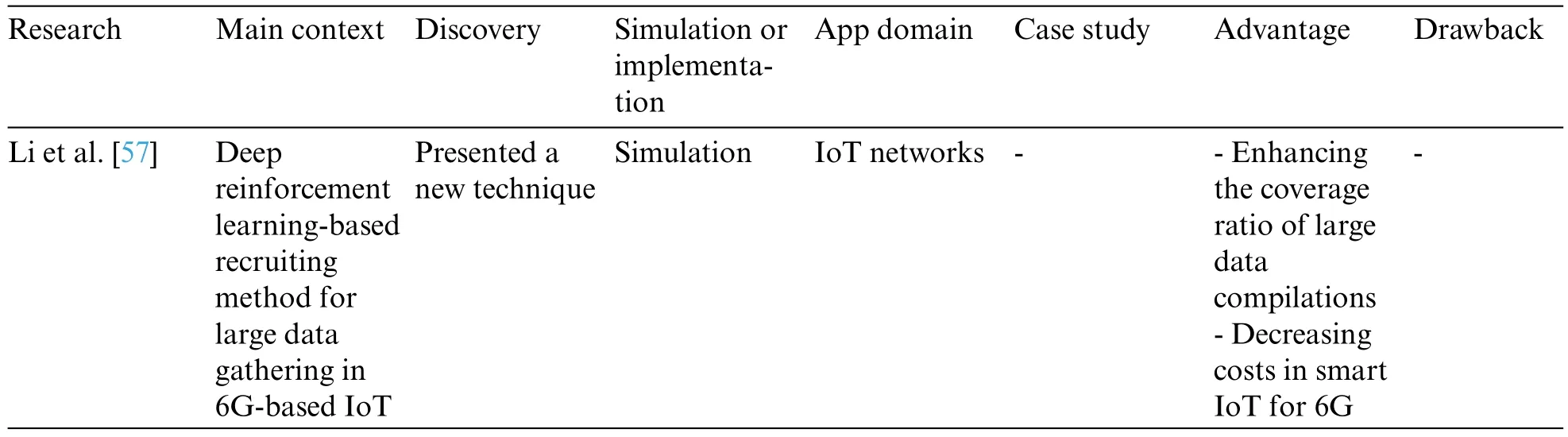
Table 3 (continued)
Liu et al.[49] investigated a multi-domain resource allocation algorithm using a satellite and a set of UAVs to enhance massive access effectiveness over large areas.Cell-free on-demand coverage,in particular,was designed to outperform traditional cellular architecture’s ineffectiveness.Opportunistic spectrum sharing was implemented to address the issue of spectrum scarcity.Iterative multi-domain resource allocation methods were also proposed to improve network effectiveness while ensuring user fairness.In addition,the adaptive cell-free coverage pattern was observed,indicating a suitable method for efficiently serving IoT devices with various applications in the upcoming 6G era.
Wang et al.[50] presented a multi-UAV cooperative scheduling and trajectory optimization method.The user transmitted power was optimized to achieve the highest average possible rate among all users by optimizing UAV-multi-UAV trajectory, sub-slot duration, and user association.The proposed algorithm, in particular, is capable of efficiently solving the non-convex optimization problem.The following findings were discovered as a consequence of the results:
1.The proposed collaborative design method may be used to successfully optimize multi-UAV trajectory and flexibility to alter multi-UAV flight path when user position changes.
2.The proposed iteration algorithm was robust and converged well.
3.The proposed method improves the minimum average achievable rate considerably.
The suggested algorithm’s significant advantages are that it can successfully optimize multi-UAV trajectory, adjust the flight route of the multi-UAVs as needed, and increase the minimal attainable average.
Yang et al.[51] proposed a novel data-oriented model for developing a wireless transmission approach,with the specific goal of improving IoT systems in future wireless networks.In particular,the fundamental design principle was proven and illustrated with novel performance metrics and their characterization for tiny means of data exchange with a perfect rapid rate and power adaptation.The data-driven design introduces novel design insights into wireless communications.The proposed data-oriented strategy was presented for 6G systems because its implementation involves a fully flexible transceiver structure that can change on the fly based on channel state and traffic type.The performance of the provided model is quite demanding.Unfortunately,they did not offer any detailed analysis of the suggested idea.
Kouroshnezhad et al.[52]proposed a novel approach for UAVs that aims to enhance the energy efficiency of large IoT systems.Localization delay and energy waste were reduced at the cost of some localization errors using a graph reduction strategy and a search algorithm.It reduces complexity while lowering the drone’s energy consumption and positioning latency.The simulation results were performed to confirm the advantage of the presented approach—it benefits from reduced lower errors,energy consumption,and localization latency.
Mukherjee et al.[53]presented a ubiquitous computing and networking architecture by combining the healthcare Internet with the Internet of Drone Things(IoDT)using a 5G and 6G communication infrastructure.Stride data was collected using a smart shoe,and the data were processed on a group of edge-enabled UAVs.A software-defined network transport data between the edge and cloud levels.Furthermore,a classifier is created at the edge level to assess the recordings and predict likely neurological illnesses.The experimental results indicated that the classification accuracy for abnormal stride detection improved when the CPU was fully utilized.The suggested IoDT-based ultra-low latency health care environment may open up new research avenues to implement fully mission-critical and social IoT applications.
Hong et al.[54] designed a pattern antenna array comprised of several sub-arrays separated at periodic times.The pattern antenna array employs flexible material,which allows for changes in the physical design to obtain adaptable efficiency.Following that,they look at the micro-movement of IoT objects.The simulation results indicate the usefulness and the effectiveness of the suggested strategies for identifying UAVs in an IoT context.
Na et al.[55]presented a synergistic method for UAVs to optimize the uplink average attainable sum rate of IoT terminals while preserving high-speed uplink and UAV mobility limitations.Because the formulated problem is non-convex and complex, an effective iterative method is offered to handle it.Initially,all terminals are clustered for a specific UAV trajectory,and a sub-slot allocation mechanism based on the bisection method and the Lagrange multiplier is proposed.After that, the UAV trajectory was optimized for a given clustering state and sub-slot duration.Finally,the two subproblems were solved alternately until the goal function converged.The numerical results validate the efficacy of the suggested method in the C-NOMA system supported by UAVs.
Zhen et al.[56] presented a robust design of high-efficiency satellite-assisted for 6G-enabled IoT.Convolving concatenated and circumferentially altered clones of a single root sequence allowed for one-step computation, eliminating the need for extra detection processes and communication overhead.Formerly, a new timing metric with immunity and noise mitigation was presented, and finally, statistical analysis confirmed its superiority at the proper timing index.The proposed idea’s fundamental weakness is that it does not address data transmission reliability.It would also be helpful if they described their work in greater detail.
Li et al.[57]developed a unique machine learning-based technique in IoT for collecting data from numerous sensing devices through collaboration among vehicles and UAVs.A genetic algorithm was used to pick vehicle collectors to gather vast amounts of data from sensor devices to maximize the collection period while minimizing costs.They create a new Deep Reinforcement Learning (DRL)-based route strategy to strategize routing of UAVs with limited fuel,which streamlines the network,expedites training speeds,and enables dynamic flying routing.Experimental results showed that the presented technique could significantly enhance the coverage ratio of large data compilations and decrease costs in smart IoT for 6G.
4.2 Energy Efficiency
Table 4 shows the classification of the analyzed articles of the energy efficiency category in 6Genabled IoT,including the following subcategory:
• Static
• Dynamic
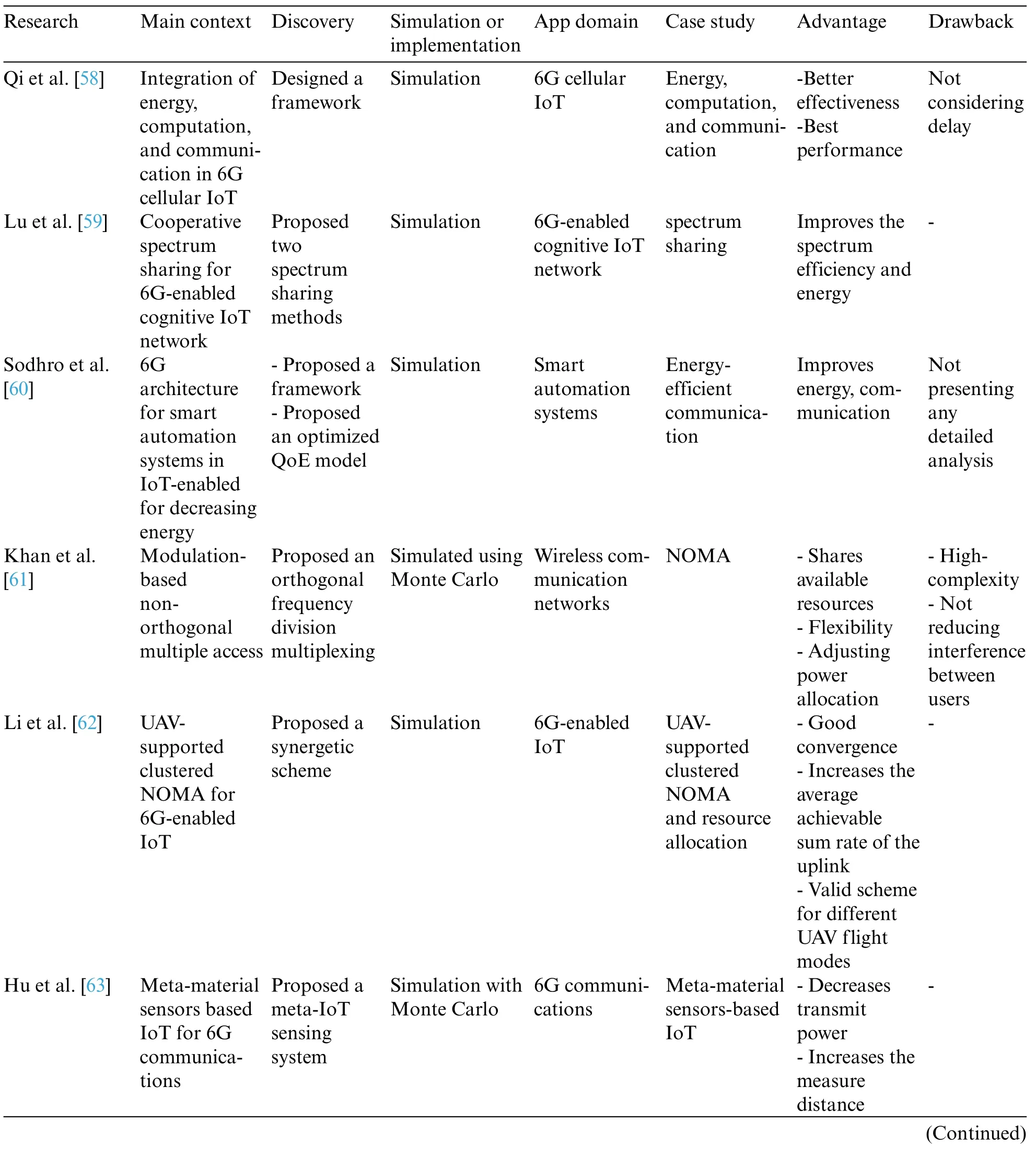
Table 4: Analyzed articles in the energy efficiency classification
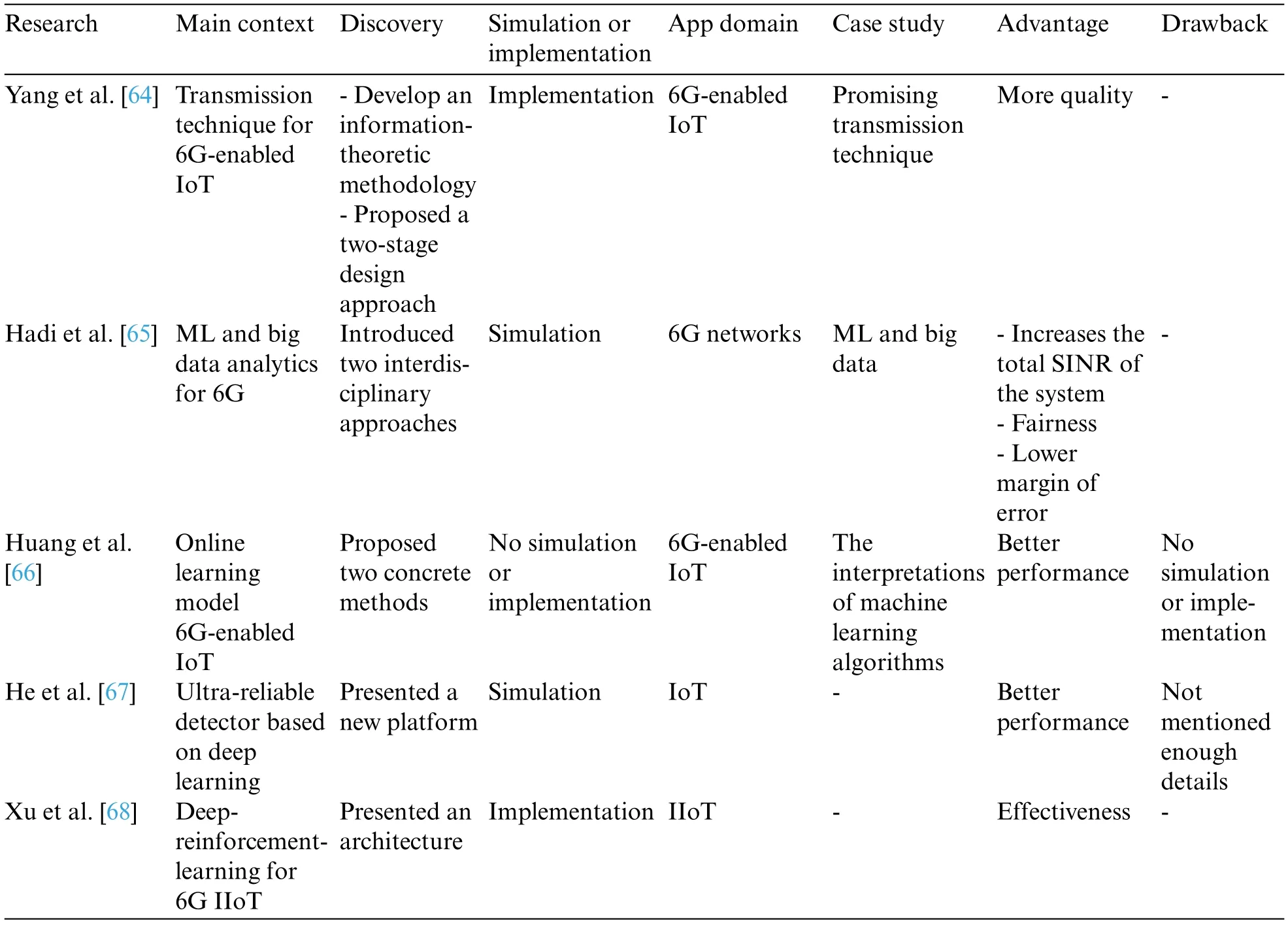
Table 4 (continued)
Qi et al.[58] developed a framework that combines communication, computation, and energy criteria to address the major challenges of 6G cellular IoT.First,the base station charges multiple IoT devices concurrently via wireless power transfer in the downlink.The collected energy was then used by IoT devices to perform computing and communication tasks in the uplink across the same frequency,and a combined beamforming design technique for base station and IoT devices was proposed to improve overall performance.Finally,simulation results confirm the proposed algorithm’s efficacy in 6G cellular IoT.The main disadvantage of their work is that they did not consider a delay.
To improve the effectiveness of a 6G-enabled cognitive IoT(CIoT)network,Lu et al.[59]proposed two collaborative spectrum sharing strategies.In particular,in phase 1,the CIoT network’s transmitter decodes and harvests energy from the incoming signal.The transmitter uses orthogonal subcarriers with gathered energy to deliver signals from the primary system to the matching receiver in phase 2 to avoid interference.The rates of a CIoT network with amplify-and-forward and decode-andforward relaying modes are optimized.As opposed to, the primary system’s goal rate is maintained by optimizing power and subcarriers simultaneously.The benefit of recommended techniques is that they improve spectrum efficiency and save energy.
Sodhro et al.[60] concentrated on four steps for capturing energy-efficient communication and user QoE level during multimedia transmission via UT device:
1.Based on QoS,a joint energy and entropy optimization method was proposed.
2.A model and framework for modeling 6G-driven multimedia data structures and assessing QoE with acquisition time were developed.
3.A link was established between test results and performance metrics and the speed and mobility of IoT devices used for multimedia services.
4.A correlation model was suggested for integrating QoS and estimated QoE parameters.
Integration of QoE and QoS parameters was modeled and assessed with acquisition time during multimedia transmission in 6G networks to improve customer satisfaction.The advantage of the proposed model is improved energy-efficient communication,and the disadvantage is not presenting any detailed analysis.
Khan et al.[61]proposed a three-step power allocation method for NOMA-enabled IoT networks that is energy-efficient.It operates as follows:
1.Power allocation was formulated as a non-convex optimization problem.
2.The SQP-based scheme presented here was used in NOMA-enabled IoT networks to discover a trustworthy answer to the non-convex power allocation problem.
3.The suggested method’s efficacy was compared to standard KKT-based NOMA and OFDMA techniques.
They used the Monte Carlo simulation to implement their idea.The proposed method’s advantage was that the performance evaluation revealed that it outperformed the benchmark KKT-based NOMA scheme.
Li et al.[62]presented a multilevel programming approach to minimize energy efficiency,divided into three sub-problems:power allocation,time slot scheduling,and offloading task assignment.These subproblems must be addressed by wisely examining their convexity and monotonicity.Furthermore,the multi-user scenario was investigated, and a near-optimal method with minimal complexity for dividing users into distinct categories with different time slots was presented.The benefits of the paper include good convergence, increasing the average achievable sum rate, and offering an approach for different UAV flight modes.
Hu et al.[63] proposed a meta-IoT sensing system (RMSE), including IoT sensors built with specially designed meta-materials.There was no need for a power supply because the meta-IoT sensors perform simultaneous sensing and transmission.The authors investigated both the sensing and transmission of meta-IoT sensors to develop a meta-IoT sensing system with optimal sensing accuracy.
They demonstrated an effective method for optimizing both the meta-IoT structure and the sensing function at the system’s receiver.The simulation results validated the proposed algorithm’s effectiveness in minimizing the sensing RMSE of the meta-IoT sensor for temperature and humidity levels and the trend that sensing accuracy declines as transmit power or measure distance increases.As advantages of the proposed idea,we can point to transmission power reductions and measurement distance increases.
Yang et al.[64] examined spatially coupled protograph systems.First, an information-theoretic approach was developed that can be used to assess the performance limitations of various layers in systems.Furthermore, a two-stage approach was proposed to create a new constellation called structural quadrant celestial objects.In addition, a tool known as the multi-stream-based extrinsic information transfer method was developed to analyze the effectiveness of the systems for estimating all separate coded-bit streams’decoding thresholds.
Hadi et al.[65] proposed an interdisciplinary strategy in a 6G network that involved big data analytics,healthcare,and radio resource optimization.Three machine learning methods were used to forecast the risk of an imminent stroke to analyze stroke outpatient medical data and body-worn IoT sensors.The benefits include increasing the system’s total SINR,improving fairness,and lowering the margin of error.
Huang et al.[66] investigated machine learning algorithm implementations to optimize the efficiency of 6G-enabled IoT networks.They generally concentrated on the current design GBDT2NN,which summarizes the information obtained by gradient boosting decision tree(GBDT)models into a neural network(NN)models to keep the learning capacity of numeric values while also enhancing the capacity of online learning, although it loses comprehensibility.They conducted an empirical investigation on understanding individual forecasts of GBDT2NN using the selected features learned from GBDT and then investigated whether the explanation may enhance the approximation method.Furthermore,two strategies for obtaining interpretations were presented in this paper:
1.the Independent method
2.the Joint method
Investigations on various datasets of IoT networks reveal that the suggested approaches perform better on both performances.
He et al.[67]suggested an ultra-reliable multiuser multiple-input multiple-output(MU-MIMO)sensor based on deep learning for 5G/B5G enabled IoT.They employed an incremental detecting architecture of a traditional signifier detector and a deep neural network(DCNN)to reduce the radio interference by collecting the properties via deep learning for this system.Consequently,the suggested MU-MIMO detector can minimize the effect of related disruptions while requiring little computing complexity,eventually improving the dependability of practical MU-MIMO systems in the presence of relevant interactions.To improve system detection accuracy even further,user scheduling was used,in which different user selection processes were presented to pick the best user from several candidates.Finally,simulation results confirm the effectiveness of the suggested sensor.
Xu et al.[68] presented the architecture of the machine-learning-based cyber twin for 6GIIoT.Furthermore, the cyber twin concept uses deep reinforcement learning (DRL) to execute the integration framework through methodical experimentation,which was otherwise expensive and risky in actual industrial facilities.Furthermore,they developed the adaptable observing window for deep Q-network(AOW-DQN),which provided the system’s status that is adaptable to the actual dynamics of the controller.Finally,the test findings proved the usefulness and efficiency of the given technique.
4.3 Channel Assessment
Table 5 shows the classification of the analyzed articles of the channel assessment category in 6G-enabled IoT,including the following subcategories:
1.Random-access
2.Orthogonal multiple access
• Orthogonal frequency-division multiplexing
• Time division multiple access
3.Non orthogonal multiple access
4.Supermassive multiple-input and multiple-output
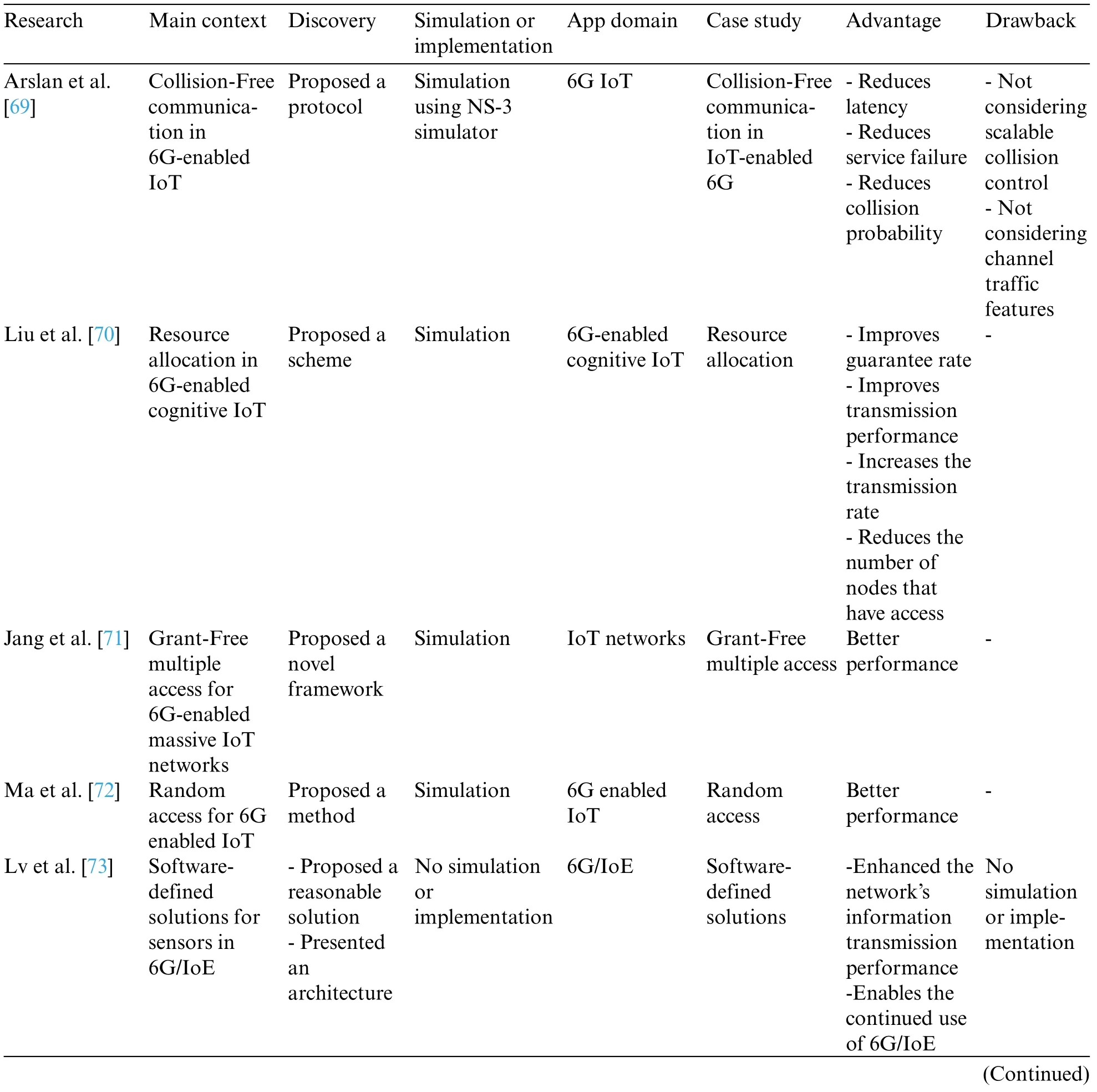
Table 5: Analyzed articles in the channel assessment classification
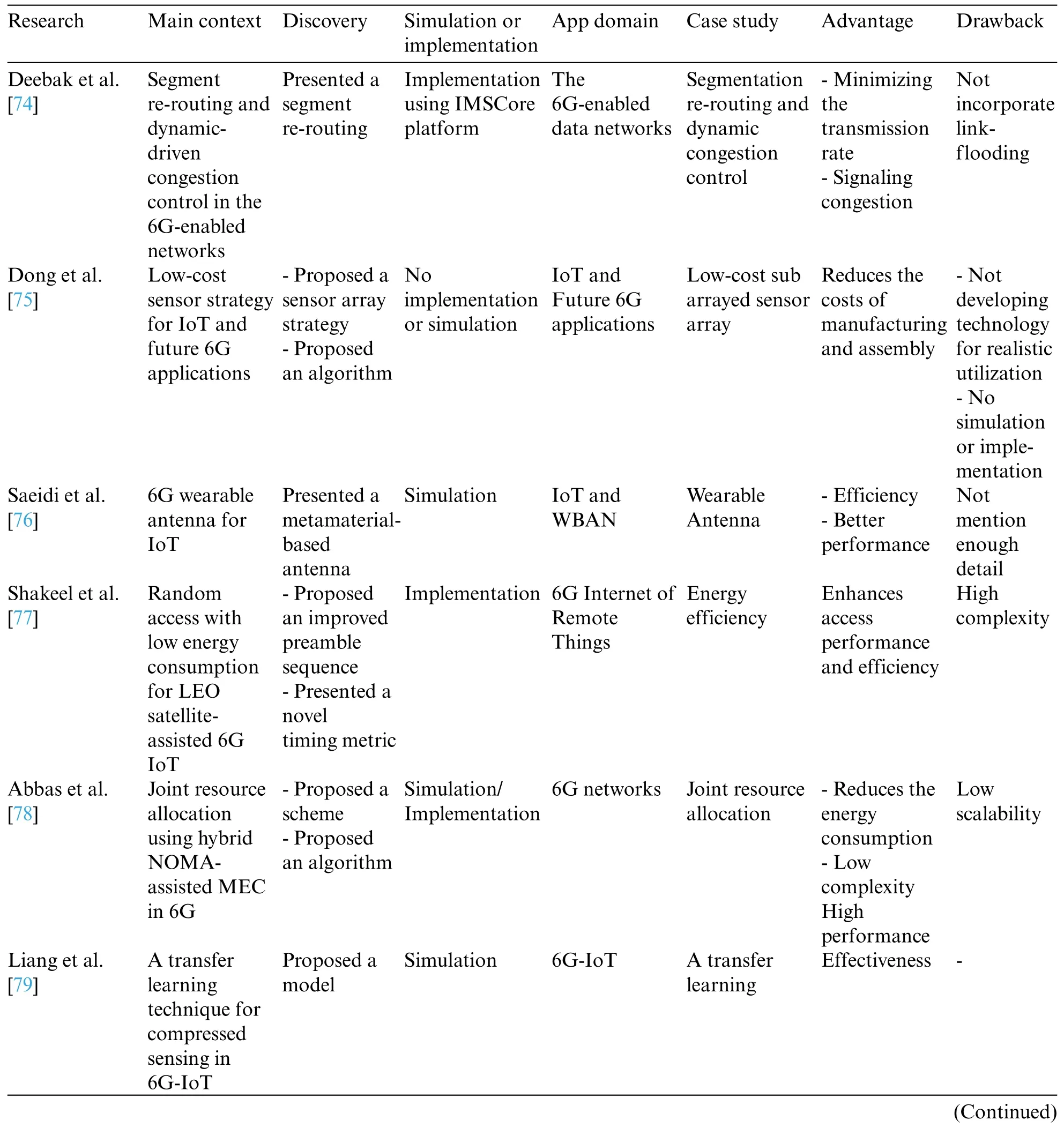
Table 5 (continued)
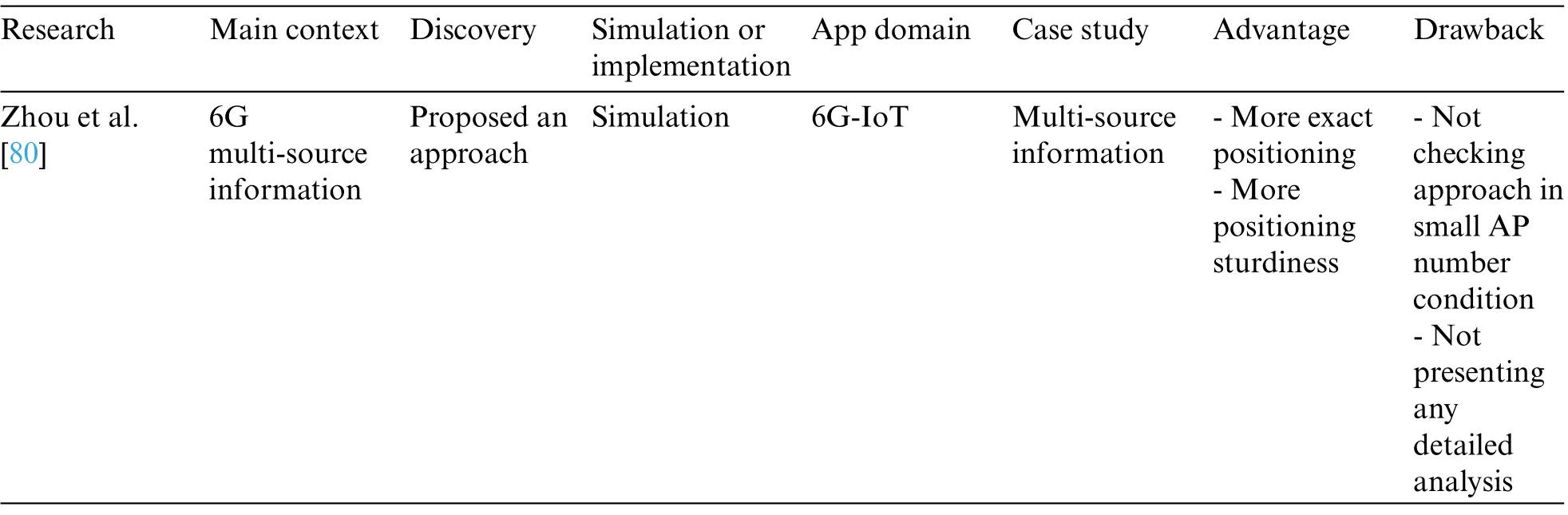
Table 5 (continued)
Arslan et al.[69] proposed OFDM-IM NOMA, a new method for multi-user communication systems in the future.The newly proposed method enabled many users to share resources more effectively.It was shown that by adjusting their subcarrier activation ratios, OFDM-IM NOMA could support both high and low data rate users concurrently.The benefits include reduced latency,service failure,and collision probability,while the drawbacks include not addressing scalable collision management and not taking channel traffic characteristics into account.
Liu et al.[70] presented a NOMA-based hybrid spectrum access strategy for 6G-enabled CIoT.The approach improved CIoT resource allocation by increasing the CIoT’s average overall transmission rate while ensuring each node’s minimum rates.The presented approach has the advantages of enhancing the guaranteed rate,improving transmission performance,increasing transmission rate,and reducing the number of nodes with access to the network.
Jang et al.[71]proposed a new resources-based GFMA(RH-GFMA)framework with resource hopping schemes for supplying adequate bandwidth in 6G cellular IoT networks.In this architecture,every IoT device might observe physical radio resources by utilizing a pre-assigned resource pattern with no need for a resource request or a permission process.They calculate the pattern traffic load, maximum permitted packet delay, and intervention efficiency of the system quantitatively.Furthermore, they calculate the proposed framework’s accommodation capacity, described as the projected number of IoT devices hosted in a cell with a maximum permissible packet delay and an intervention limitation.According to simulation results, the Latin-square group approach outperforms the suggested RH-GFMA strategies throughout a diverse variety of activating chances for a given number of IoT devices.
Ma et al.[72] offered to spread slotted ALOHA (SSA), a NOMA SA approach that does not require any sensing or power regulation.The outage paradigm,rather than the collision framework,was recommended to be utilized for NOMA SA,and both physical and medium access control layers were examined.Because a wide variety of codes might be used,SSA employs random non-orthogonal code distribution to lessen collisions.The code domain has much higher freedom than the power domain.With invisible detecting techniques,it may be used with no cooperation.In addition,collision correction variety SSA (CRDSSA) was utilized to enhance user loading even more.The simulation results verify the study in most situations, demonstrating that the suggested SSA-based approaches offer a larger user load and significantly greater flexibility than conventional NOMA SA works.
Lv et al.[73] investigated the dual-channel architecture in 6G and the Internet of Everything(IoE), then proposed a viable approach to reduce signal interference so that related signals could be transmitted more effectively.Furthermore, node data from sensors, fog, and edge computing were evaluated, and transmission energy usage and packet loss rate were used to assess network communication quality.A disadvantage of the analysis is that no simulation or implementation is used,whereas improving information transmission performance benefits.
Deebak et al.[74]proposed a segment re-routing and dynamic-driven congestion control to meet the standard limits of 6G networks.It performs two critical functions:
1.To alleviate signal congestion and flow rate.
2.To improve the path adjustment and monitoring process.
They used the IMSCore platform to implement and configure forward-backward interface and segment re-routing,focusing on efficiency parameters such as transmission delay and throughput rate.The benefits of the suggested approach include reducing transmission rates and signaling congestion,but the disadvantage is that it does not have link-flooding.
Dong et al.[75] developed an intense method for breaking down the practical implementation challenge into on-scene subproblems.A user-specified DoF control approach for small-size cases was freely designed and created an appropriate transfer.In addition,a hierarchical subarray design method for large-size situations was provided.Both design techniques successfully ensured acceptable sensor radiation performance while remaining engineering-friendly.Several tests were used to demonstrate the efficacy and potential of the proposed technique.This technique has the advantage of lowering manufacturing and assembly costs.
Saeidi et al.[76] demonstrated a metamaterial-based foldable wearable ultra-wideband antenna for IoT and wireless body area network (WBAN) applications in sub-6G frequency bands.In addition, the ellipsoidal update has an L-shaped slot, a stub at the back, and chamfered ground to eliminate stopbands and increase bandwidth(BW).The antenna was then combined with six arrays of modified grain rice shapes in a split ring resonator(SRR)to improve bandwidth,gain,and directivity.Furthermore,the antenna has a high degree of agreement between the predicted and measured data,providing outstanding quality than equivalent current antennas despite having smaller sizes.
To provide an effective interaction mechanism in the context of the 6G IoT, Shakeel et al.[77]proposed a new collision carrier avoidance protocol using multiple machine access learning.Terahertz(THz) network synchronization is accomplished using the media access control protocol based on Media Access Control (MAC).The simulation results demonstrated the stability of the suggested protocol by increasing service usage while decreasing collision probability,service failure,and latency.High complexity is the main drawback of the presented protocol.
Abbas et al.[78]presented a new deep learning technique for simultaneous user identification and decoding.The need for resource allocation and grant-free coexistence NOMAs with other orthogonal or grant-based systems was also discussed.After some time, research techniques for enabling 6GIoT were made available.According to the findings, deep learning can reach the optimal decoder with significantly reduced complexity.The advantages of the presented technique are reduced energy consumption,low complexity,and high performance,and Its disadvantage is its lack of scalability.
Liang et al.[79] proposed a convolution-based transfer compressed sensing (CTCS) model based on transfer learning to recover the compression signals.To assess CTCS effectiveness, an ultra-wideband (UWB) radar echo signal and a hand-written dataset from Mnist were used.It was demonstrated that the suggested model exceeds existing standard reconstructing techniques in 6G-IoT under various noise levels,measure numbers,and signal sparsities.This research revealed how transfer learning may be used to spectrum sensing in signal reconstruction and demonstrates its benefit in 6GIoT.Future studies may extend the CTCS methodology to critical technologies in 6G-IoT.
Zhou et al.[80]proposed a three-step Gaussian kernel density estimation approach:
1.A Gaussian kernel density estimate was used in this approach to computing the standardized dispersion density of the signal propagation distance.
2.The multi-source RSS information was integrated using the proof synthesis criteria,and the trust function was used to select the best-matching RPs for placement.The proposed technique was found to be superior when its performance was compared to the other three current positioning approaches.
Their idea has the advantages of more accurate positioning and more positional sturdiness,but presenting a more detailed analysis would be preferable.
4.4 Security
Table 6 shows the classification of the analyzed articles of the security category in 6G-enabled IoT,including the following subcategories:
• Privacy
• Vulnerability
• Access control
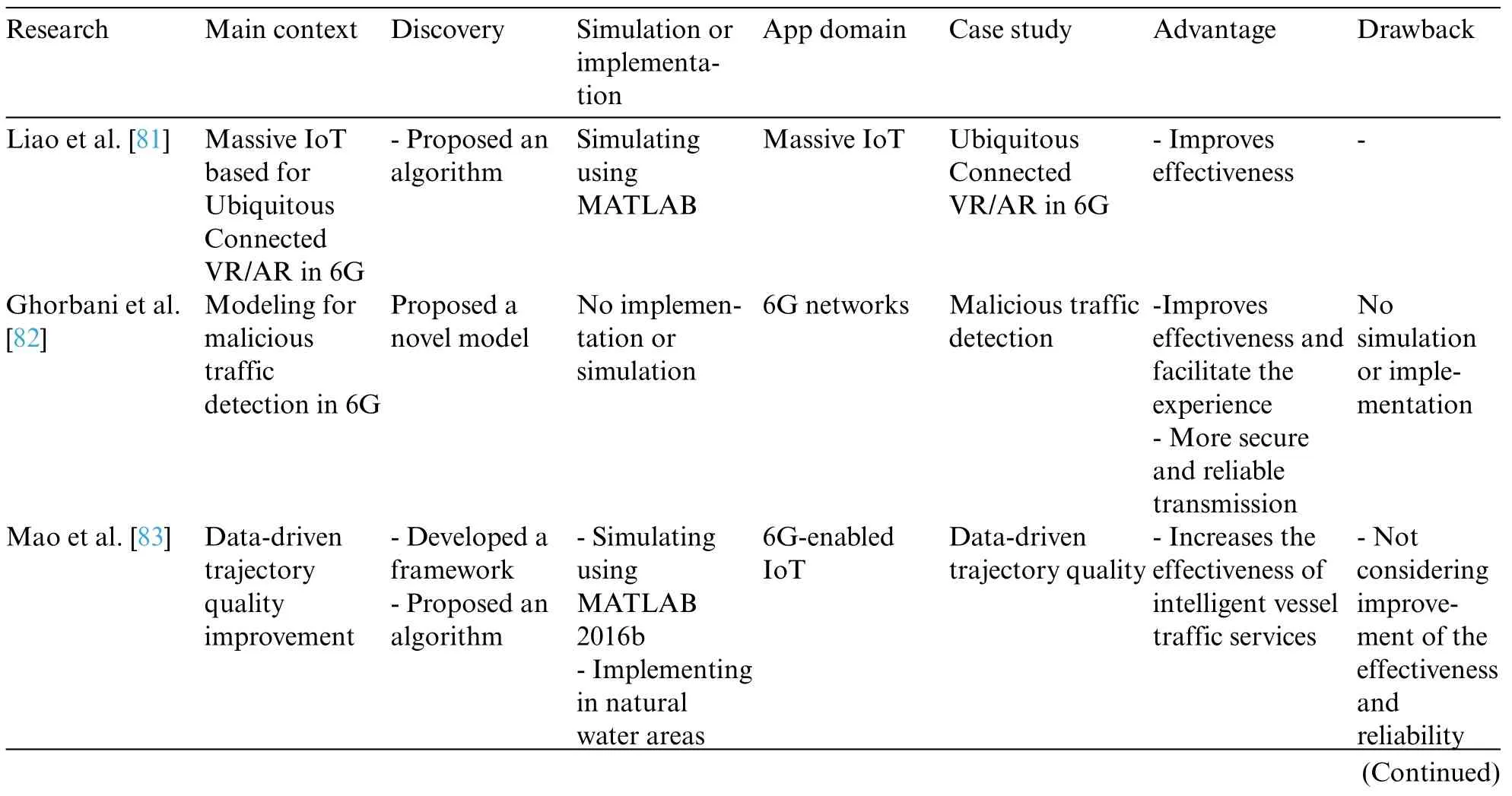
Table 6: Analyzed articles in the security classification
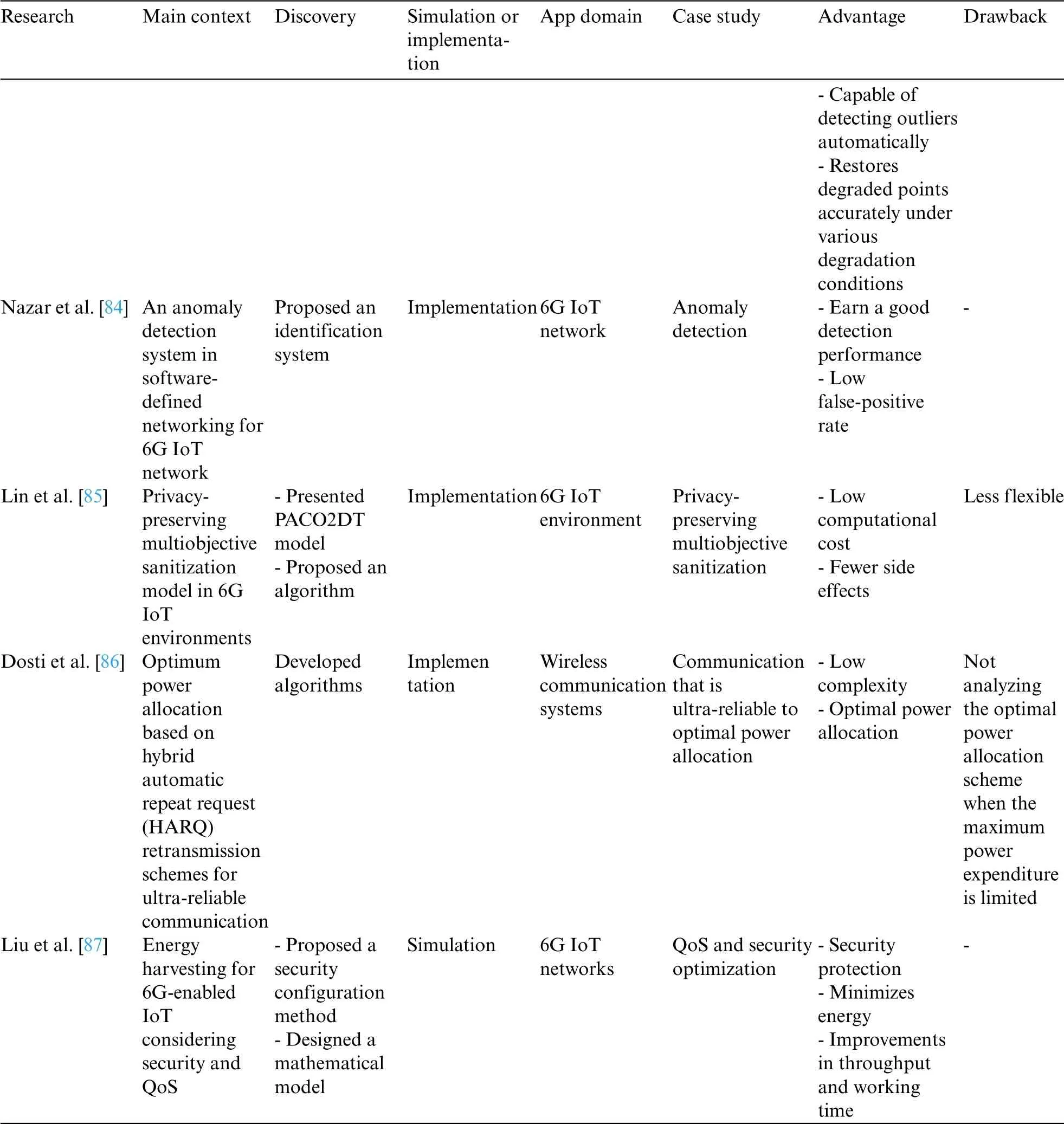
Table 6 (continued)
Liao et al.[81]presented the Information-centric massive IoT,which enabled large-scale VR/AR content delivery over 6G networks.It increases the effectiveness of the proposed system in the three below steps and ultimately ensures user QoS:
1.Developed a blockchain for IC-mIoT nodes and a new Proof-of-Cache-Offloading consensus mechanism.
2.Demonstrated a blockchain-based VR/AR architecture based on IC-mIoT.
3.A Stackelberg game structure and a technique for selecting and computing cache indexes were developed for blockchain-enabled memory offloading.
The results show that the proposed system was superior and more effective than previous ones.
Ghorbani et al.[82] proposed a hypothesis for potential work and effort on developing hostile traffic detection modeling in 5G and 6G networks.Finally,they may devise a method to improve future security.A novel approach for detecting malicious traffic inside a 6G network has been presented,enhancing effectiveness and allowing for more dependable and secure transmission.The advantages of the proposed work include increasing efficacy and ease of experience and more secure and reliable communication.
Mao et al.[83]presented an AI-based security definition approach for 6G-enabled IoT networks,which uses cellular networks for IoT devices via various frequency bands, including THz and millimeter-wave.The Extended Kalman Filtering technique was used to forecast future harvesting power.A mathematical model was created for each energy-conscious cycle, using a mathematical formula to determine the energy needed for various security techniques.The benefit of the model is to obtain the highest protection level that meets service requirements while reducing energy consumption.
Nazar et al.[84]described malicious activity on SDN switches that cause network disruption.The suggested approach is based on attack patterns and can detect malfunctioning switches that discard and shift packets for malicious reasons instead of connection failure.Each attack has a signature,and these attacks are distinguished by preset signatures and distinct behavior.Three separate attacks are identified to analyze network performance:
1.Traffic diversion attack.
2.Port scanning.
3.DDoS attack.
Finally,the experimental findings showed anomaly detection and analyzing network performance.The empirical results confirm the efficacy of the presented work.Many concerns will be studied in the future to increase attack detection efficiency.
Lin et al.[85] presented an ant colony optimization-based multi objective model that conceals sensitive private information by deleting transactions.The results demonstrated the efficacy of the pointed model in the various measures studied.Offloading some computing activities to the edge of IoT networks may become necessary in the future.The advantages of the proposed approach include low computing cost and fewer side effects,but the downside is that it is less flexible.
Dosti et al.[86] used Karush-Kuhn-Tucker situations to develop algorithms that allow hyper operation at any failure probability target while consuming the least amount of power in the finite block length domain.To begin,they demonstrated that using an open-loop system to achieve a low packet loss probability requires high power consumption.To mention a few benefits of this study,we can indicate low complexity and optimal power allocation.It was better to investigate the best power allocation strategy when the maximum power consumption is limited.
Liu et al.[87]suggested a machine learning framework based on data in two phases to improve the effectiveness of the vessel’s network tracing records.In the first phase,a density-based clustering technique was used to discover unwanted outliers automatically.The second phase demonstrated learning under supervision using long-term and short-term memory that works in both directions to recover timestamped points from vessel trajectory data impacted by random outliers.The benefits include increased security,increased throughput and working time,and reduced energy consumption.
Table 7 list the evaluation factors for 6G-enabled IoT.The evaluation factors are data transmission,delay,energy consumption,and bandwidth.
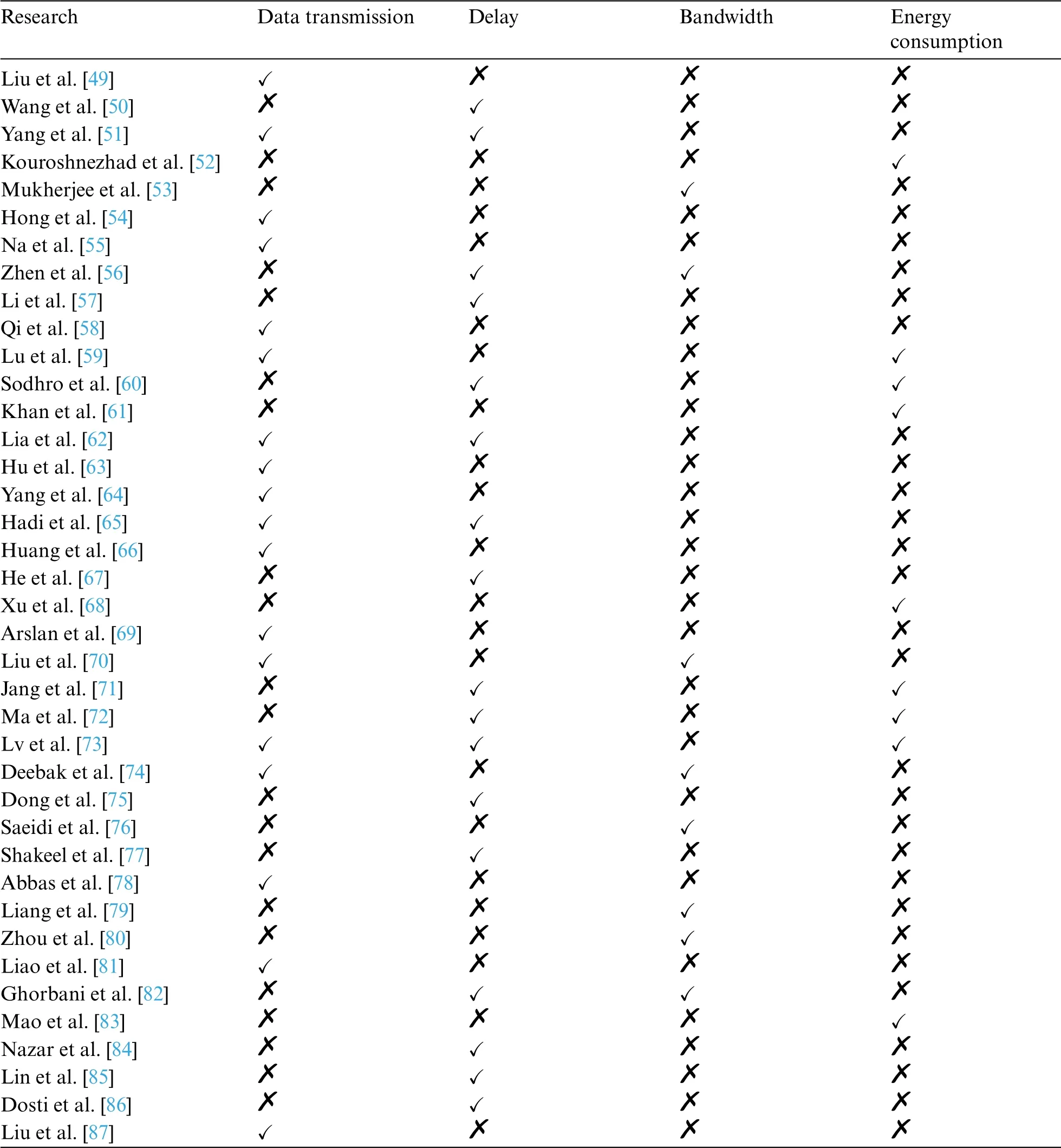
Table 7: Evaluation factors in 6G-enabled IoT
5 Discussion and Comparison
Previous sections described the method for analyzing the selected studies in 6G-enabled IoT.Furthermore,we classified and compared the studies based on various criteria, such as the primary context,simulation/implementation,application domains,benefits,drawbacks,evaluation factors,etc.This section provides a statistical and comparative breakdown of 6G-enabled IoT categories.
The proposed idea has been implemented in 23% of the research studies.Furthermore, we discovered that simulation methods were used in 56% of the studies published to evaluate the proposed idea.As simulation tools,we can mention MATLAB and Monte Carlo simulation platforms.Furthermore,as shown in Fig.6,13%of the papers did not include any implementation or simulation,but 8%of articles used both implementation and simulation methods.
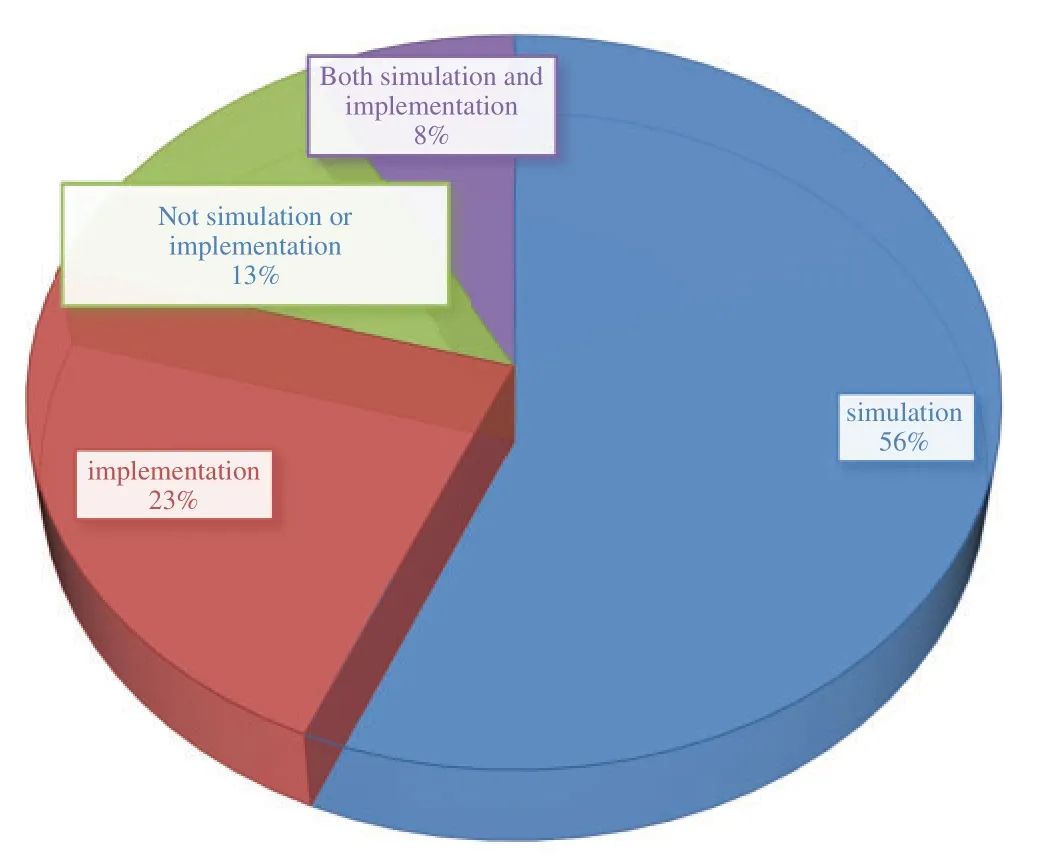
Figure 6:Percentage of evaluation environments presented
Furthermore,the following analytical reports on the RQs from Section 2 were presented:
RQ1:What are the critical requirements and trends for 6G-enabled IoT?
Scalability: IoT connects many devices to the Internet, including high-end gadgets, sensors,actuators,smartphones,tablets,wearables,household appliances,automobiles,and many others.Such connected devices generate massive amounts of data.Machine learning is required to extract the relevant hidden information[88].
In reality,compared to the 5G cellular networks,the 6G mobile networks are expected to provide more coverage and greater scalability to support IoT connection and delivery of services[89].
The evolution of IoT towards IoE: IoT aspires to create worldwide interconnected objects and equipment networks.As a result of the growth of applications such as Industrial IoT,an estimated 24 billion IoT devices are expected to be in use by 2030.IoE is estimated to broaden the reach of IoT,resulting in a highly linked world, easing business and industrial processes while improving human lives[73,90].
Even while the 5G may support a range of IoT devices,it may not fully meet the needs of IoE new devices.As a result,6G is designed to overcome the limits of 5G.IoE-based smart services necessitate the deployment of 6G.They are comprised of four pillars: data, things, people, and processes that are intelligently connected and depict a world in which billions of items have sensors to differentiate measurement and assess their state[91].
Integration with satellites: Satellite telecommunications are widely regarded as an essential support technology for meeting IoT service needs in the 6G[92].6G employs satellite communication technology for worldwide coverage.6G satellites include communication satellites, ground imaging satellites,and navigation satellites for localization,distribution,and Internet access.Satellites can be used to expand terrestrial 5G penetration.On the other hand,Satellites are limited by their high latency and comparatively low data throughput.Merging satellite and terrestrial networks to use satellite’s extensive coverage and terrestrial networks’high capacity in the 6G era is of significant interest[93].Energy less IoT:IoT devices with no energy can collect energy from their surroundings and generate infinite electricity.Energy collaboration allows nodes to share their excess energy with other nodes.It is expected that as destiny communication technologies and applications advance, the remaining devices will be connected in an energy-efficient manner as well[60].
6G will be substantially higher energy-efficient,turning off equipment and scaling down capacity when demand is low.Energy efficiency will be a key design consideration in 6G [94], with capacity,peak data rate,latency,and reliability.
RQ2: What are the most important 6G enabling technologies for IoT that require further investigation?
6G innovation can occur at multiple layers, including network architecture, communication protocols,network intelligence,and so on.The answer to this question is dedicated to 6G technology,which impacts IoT.
Non-Terrestrial Technologies:The advancement of 5G systems has resulted in a paradigm change utilizing sophisticated technology,projected to extend with 6G technologies[95].Wireless technologies of the next generation are proliferating,connecting everything and humans.IoT connects many devices and makes the world around us more intelligent.IoT devices will be required to wirelessly communicate a wide collection of environmental data to support a plethora of new implementations.The ultimate goal is to gain insights from this data and create services that enhance people’s lives while generating new revenue.The main challenge in enabling a wearable world is to provide large-scale, long-term,reliable,and near real-time communication[96].
Current cellular networks built on legacy terrestrial technology have solved the difficulties of providing widespread wireless coverage to remote locations and a lack of availability, dependability,and weakness to natural and manufactured actions.6G networks are integrated with non-terrestrial technologies such as satellite connectivity to tackle these challenges,providing comprehensive coverage and high-capacity connectivity[83,88].
• UAV-assisted wireless communications: UAV-assisted communications are expected applications for 6G-enabled IoT networks.UAVs can prevent biogeographic wireless communication limitations such as ships at sea, sensors in remote locations, and areas outside of terrestrial connectivity zones[88]
• Satellite connectivity: Satellite connectivity is expected to be an alternative to grounded and UAV-supported communication technologies for providing the purpose of the system for electronic objects on the ground and may thus be used in IoT scenarios.Some companies are developing dedicated satellites for IoT networks,encouraged by the major benefits of satelliteassisted IoT communications[88]
Transmission without a grant: Grant-free transmission technology is a key trend in upcoming mobile networks.This technique is a medium access control method for using massive IoT connections via mobile networks.Given the growing number of intelligent devices on the market and the attraction of these various systems,more effective grant-free transmission solutions for 6G networks are required.Because of NOMA’s lower latency, GF-NOMA, a hybrid of NOMA and grant-free transmission,could be a feasible alternative for 6G-enabled IoT devices.Most previous NOMA approaches utilized a centralized scheduling strategy in which IoT devices are attached before, and various network characteristics are predefined[56,70,88].
Sparse signal processing:Although 5G is in its early stages,there is a growing interest in telecommunications beyond 5G in the research.Sparse signal processing techniques can be used in the grantfree transmission approach to detect active IoT devices reliably and effectively.Identifying the active IoT devices for data decoding is one of the most difficult challenges with grant-free IoT connections.Due to the low data rates,sparse signal processing is also required for THz communications over 6G networks.Because THz networks are sparse,THz channels can be estimated using compressive sensing techniques for sparse channel restoration[97,98].
RQ3: What new service classes are available in the 6G-enabled IoT domain? And why do these services need to be provided?
In the IoT domain, new service classes for 6G are intended to improve on service classes of the 5G core, such as enhanced Mobile Broadband (eMBB), massive Ultra-Reliable Low Latency Communications (mURLLC), massive Machine Type Communications (mMTC), extremely high Reliability and Low Latency with Security (eRLLCS), eMBB-Plus and Secure ultra-reliable lowlatency communications (SURLLC).This subsection goes over the newly discovered service classes of 6G-enabled IoT.
eMBB: Certain communication technologies, such as augmented reality, virtual reality, and virtual meetings, may be used in 5G applications.Communications with high transmission speeds,high reliability, and low latency are typically required [81].Compared to eMBB and URLLC in 5G technologies, this anticipated service class must be capable of significantly improving digital communication systems in switching,interference,and huge data transmission.Moreover,the security risks and privacy issues associated with enhanced mobile broadband URLLC communication services must be considered[84].6G expands the consumer IoT industry in its early deployments by providing high-speed,low-latency,dependable,and secure enhanced mobile broadband(eMBB).eMBB allowed for the delivery of high-definition consumer video(such as TV and gaming),augmented and virtual reality,video calling,and smart city services such as IoT video cameras in a secure manner[99,100].6G benefits,which apply to IoT,are not currently available with 5G or previous technologies.5G will continue to be used by consumers and commercial IoT businesses,but 6G offers several advantages for IoT that 5G and other technologies do not[101].One of the 6G’s abilities is to handle many static and mobile IoT devices with varying QoS requirements.As the IoT grows,the flexibility of 6G will become increasingly crucial for businesses desiring to meet the strict needs of essential communications[88].
Massive eMBB:Tactile Internet is the most common 6G use case,requiring high data speeds,ultralow latency,and dependable communications.Massive eMBB in 6G replaces its 5G partnership and offers excellent experience(QoE)in information consumption and guidance.Surprisingly,additional critical components of the remote correspondence of organization development, handover, and impedance should have the alternative to promote these activities by utilizing big data concepts[88].
mURLLC:URLLC applications are projected to be widespread,and 6G is supposed to maintain its functioning in the mURLLC scenario.URLLC causes significant problems for many devices in communication systems [98].6G must significantly expand the 5G URLLC service, creating a new service class called mURLLC, integrating 5G URLLC and traditional mMTC [88].Today’s IoT and networks support various services by providing pervasive all-purpose connectives.To meet the demands of IoT applications, mURLLC of 6G must provide high throughput, dependability, data rate,massive connection,and complete mobility[6,88].
mMTC:6G is still in its early stages and needs to envision and improve its concept,development,distribution, and use cases [101-103].MMTC technology aims to connect many devices, such as sensors, that send and receive tiny amounts of data on an irregular basis.An mMTC network is designed to be latency-tolerant,efficient for the transfer or reception of small data blocks,and capable of being delivered over low bandwidth pipes.The key success need for an mMTC network service is a high connection density.mMTC is available in MTC networks for 6G-enabled IoT applications such as smart cities[104,105].
eRLLCS:High dependability and ultra-low latency will be required in smart mobiles and robotics communications development.Smart homes,smart vehicles,smart industries,smart schools/universities,and smart industries will become a component of future cities.Planes,fast trains,and UAVs will all be linked to smart cities.Healthcare systems,military,tracking,and security are just a few of the key applications that call for ultra-reliability and low latency.In 6G wireless systems,the Extremely high reliability and low latency with security(eRLLCS)will merge security capabilities with mMTC and URLLC in 5G with higher accuracy needs.Autonomous cars will be linked to one another,and connectivity among them must be extremely dependable, else people may be killed in incidents.Many houses and other sensors will connect with one other in 6G networks,which necessitates ultrareliability to avoid accidents[13].
eMBB-Plus: In addition, the IoT includes mMTC and uRLLC.Other essential aspects of 6G networking will include URLLC, which will enable ideal data speeds for critical device connections for robotics, human-machine interfaces, UAVs, and other devices.6G will also rely significantly on mMTC+ to build IoT throughout smart cities, transportation, agricultural, and other public infrastructure.The eMBB-Plus in 6G replaces the eMBB in 5G, supporting traditional mobile communications with substantially higher needs and standards.It must also improve cellular networks in terms of interruption,touch,and large data transfer and analysis.Other capabilities,such as exact indoor location and worldwide interoperable connectivity across various mobile operating networks,will also be made available to customers at a low cost.Most significantly,extra attention will be devoted to the eMBBPlus communication services regarding security,secret,and confidentiality[106].
SURLLC:With enhanced quality and durability,the SURLLC in 6G is a merged improvement of the URLLC and mMTC in 5G.In the 6G era, the SURLLC primarily supports industrial and military connections,such as a range of robots,high accuracy machine tools,and conveyor systems.Furthermore,vehicle telecommunications on 6G might benefit substantially from the SURLLC[106].
RQ4:What are the evaluation factors or metrics used in IoT domains to measure the impact of 6G in IoT?
According to the classification in Section 4,the percentage of evaluation shows that data transmission has the highest rate in the analyses of the recommended techniques by 35%.Fig.7 shows that it is 33%related to delay,17%related to energy consumption,and 15%related to bandwidth.
RQ5:What are the future research directions and open issues in the 6G-enabled IoT domain that need to be addressed?
Below are listed several future research directions and open issues in the 6G-enabled IoT domain.Also,Table 8 shows a summary of potential significant challenges,research directions,and open issues for future research efforts in 6G-enabled IoT based on the studies reviewed in Section 4.
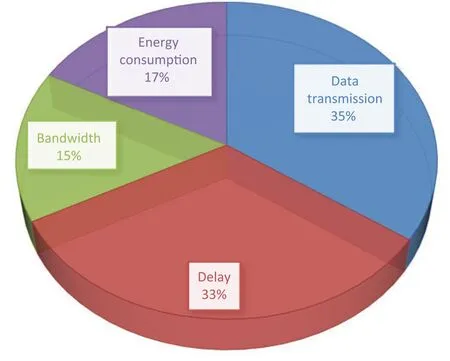
Figure 7:Evaluation factors in 6G-enabled IoT
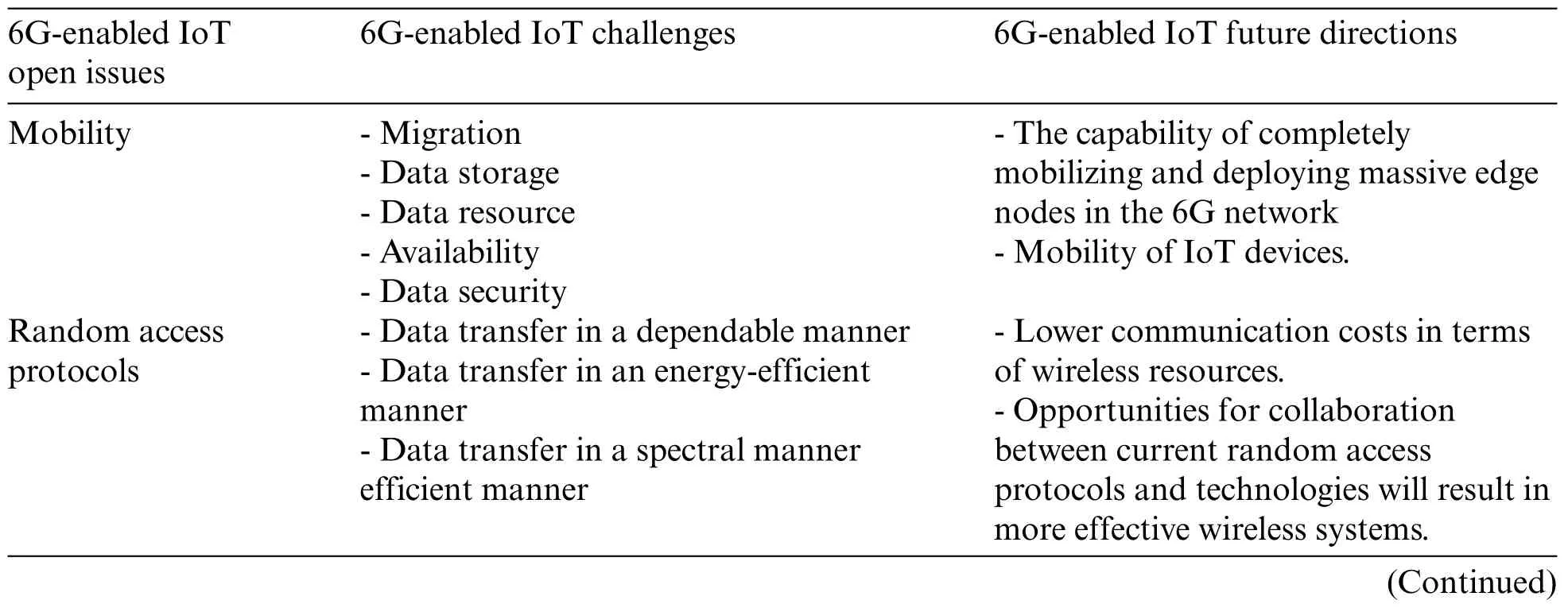
Table 8: Open issues,challenges,and future directions of 6G-enabled IoT
Table 8 (continued)
Mobility:Due to Fig.8,6G has been specified as a breakthrough concept to take the capabilities of 5G wireless networks.6G network structures have generally proved to be exceedingly varied,densely distributed,and dynamic.Furthermore,sophisticated mobility management and resource allocation will ensure that services are ultra-reliable and have minimal latency.The mobility of 6G devices,such as satellites,UAVs,and vehicles,would result in frequent handovers,rendering connections and communications unstable and unreliable.Furthermore,low latency and high transmission rate service standards would make effective mobility more difficult.For improving network connectivity in the upcoming 6G networks, numerous promising technologies will necessitate different critical mobility management systems.Legacy network architectures offer unique skills for smooth device mobility all over multiple networks.Still,they cannot adequately cover the huge deployment of new wireless networks that can provide advanced services for various vertical domains with varying requirements for mobile broadband rates,ultra-low end-to-end delays,and massive device interconnectivity[107,108].In order to accommodate high-frequency bands in the THz spectrum, 6G will have to move from existing microcells to tiny cells.This needs the creation of a new design methodology capable of allowing for bigger network deployments and mobility management at higher frequencies[109].The eMTC can deliver high bandwidth data rates and high mobility to numerous 6G-enabled applications,such as the Internet of Vehicles[110].The convergence of 6G,IoT,and artificial intelligence is expected to overcome several significant mobility concerns.6G systems should provide on-demand mobility ranging from high mobility,such as high-speed trains/airplanes,to low mobility or stationary devices,such as smart meters.The primary necessity for variable speeds, on the other hand, is based on the deployment and operating situations.In general,high mobility endpoints provide a variety of obstacles to 5G network modeling,architecture,analysis,and assessment.It is critical to enable high mobility while maintaining QoS provisioning and user satisfaction in high mobility scenarios[111].
Figure 8:Mobility in 6G-enabled IoT
Random access protocols: Random access asserts multiple access methods that enable users to compete for channel capacity without centralized planning,as shown in Fig.9.Random access helps in sharing radio resources assertively without precise scheduling.Modern random access protocols are developing as a practical but straightforward option for developing IoT in 6G systems[94,112,113].Bandwidth transfer and large connectivity define satellite-based IoT, necessitating effective multiple access systems for satellite communication.Because of its criteria,such as reduced overhead,satellitebased IoT will employ the random access method.The random access method enables many users’signals to be collinear and broadcast on the same physical resources at the chance.As a result,the satellite access demonstrates no orthogonal transmission features such as unpredictability and synchronization.It produces asynchronous time-frequency confusion and the random activating of many users.Satellite communications are widely regarded as a promising technological enabler for meeting IoT service needs in the 6G future [114,115].The present random access and NOMA technologies do not support the service prototype model of a satellite-based IoT platform to meet the complex transmission needs.Although attractive increases may be gained with current random access protocols,more research is required to comprehend their possibilities in 6G fully.While similar techniques have been successfully used in satellite communications,their application to local contexts brings new obstacles.Not only,recognizing the synergies of current random access with methods like massive MIMO,OFDM,NOMA,or sparse signal processing opens up the possibility of 6G-optimized system design.Specific channel and traffic characteristics also must be considered.The use of datadriven approaches allows for new generalized random access protocols in which the receiver knows specific additional features on the devices’brain activation.Given their capabilities and speed,the 6G ecosystem inherently necessitates contemporary random access schemes as primary facilitators for IoT use-cases[115,116].
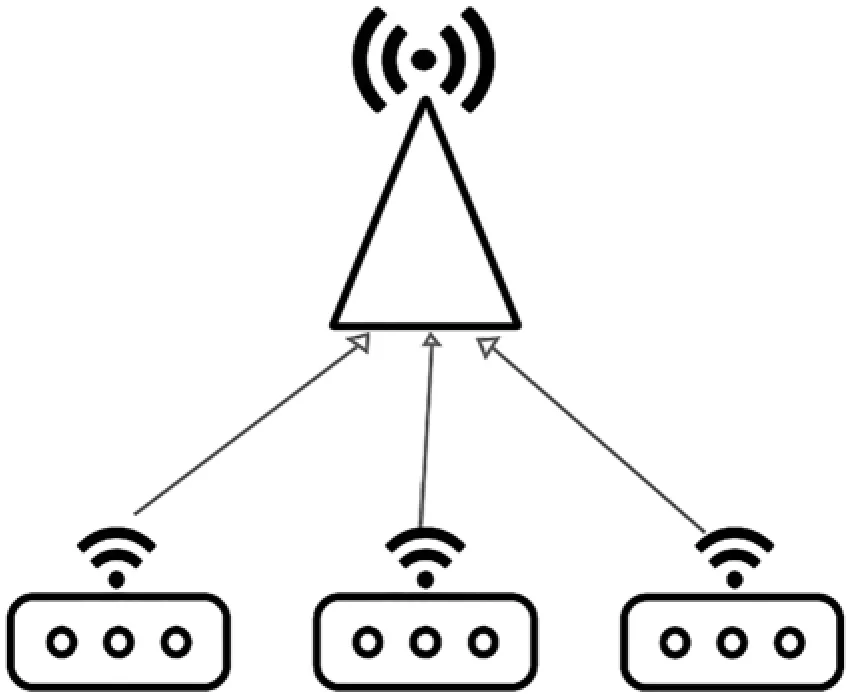
Figure 9:Random access protocols in 6G-enabled IoT
Energy and power utilization: Due to Fig.10, the emergence of 6G has made essential and industrial activities increasingly dependable, effective, and valuable, precipitating the emergence of the next-generation IoT.6G industrial equipment has many wireless sensors that gather essential data by monitoring the local environment [28].The 6G networks are predicted to increase energy efficiency over their predecessors, the 5G networks, and a highly complicated structure owing to extensive interconnections.Based on its ability to perform in higher frequency bands than previous generations,6G technologies require significantly more energy than previous generations.As a result,energy consumption and efficiency are critical concerns that should be handled immediately.Once different methods are introduced, energy efficiency will improve, and battery-free IoT devices will become a reality[117].6G will achieve and outperform a variety of energy-efficient communication standards, including enabling high-energy performance, particularly in the context of massive IoT use [118].6G will need the development of a comprehensive strategy for energy-efficient wireless communication.one of the goals of 6G is to run battery-free possible.To combine energy and IoT in 6G, various previous efforts were to create techniques to tackle different issues in wireless communications[119,120].
Security(including privacy,access control,etc.):3G and 4G had high vulnerability against cyberattacks.Therefore,5G and 6G technology providers should use more powerful security standards to eliminate previous defects and create a safe and functional technology.This is not consistent with the current security systems with the new 5G standards and the probability of middle male attacks in 6G networks,which is the leading cause of these concerns.Studies have shown that essential security gaps and the lack of security goals allow perpetrators to disrupt 5G communications and steal the data.The convenience and facilities provided by 6G also lead to many crises to leak information and violate individual privacy.IoT connects billions of devices to the Internet and includes the use of billions of data points that should all be safe.Due to the expansion of the attack level,IoT security and privacy are listed as the main concerns [8,10,121].Novel technologies allow 6G to interconnect all elements of human activity to the network,but this will also offer a significant challenge to network security.Essentially,today’s security is based on bit-level encryption technology and many degrees of security standards.There are several vulnerabilities to the 6G at the levels of identity authentication, access control, network communication, and data transmission [106,122,123].The development of 6G will necessitate the use of various technologies.Security will be a crucial aspect in developing 6G [124].Fig.11 shows several important security directions in 6G-enabled IoT.

Figure 10:Energy consumption in 6G-enabled IoT
Figure 11:Security in 6G-enabled IoT
Artificial intelligence: The 6G paradigm and the new generation of IoT are expected to move technology from related devices to the Smart Communication Network.The intelligent network has a broader meaning of automatic systems.The most important attribute is the continuous connection of the system with artificial intelligence and permanent decisions at the moment of the artificial intelligence system.The disconnection of this relationship can lead to any damage.IoT and artificial intelligence that is rapidly in progress can create intelligent machines that simulate intelligent behavior and make conscious decisions with little or no human intervention[47,83,125].6G networks will focus on wireless technology and artificial intelligence.In the 6G period, artificial intelligence technology will be equivalent to human brain analysis [126,127].6G infrastructure of mobile technology is like body veins.If we assume the human brain as artificial intelligence,different body organs are like robots and IoT.The current blood in the body is a metaphor for information and brain orders to these organs,and 6G is the same as the body veins, which are possible through information and communication,as shown in Fig.12.Such a system initially receives artificial intelligence in the 6G bed,then analyzes the data and sends its analysis in the form of specific commands on the 6G substrate[125,126,128].IoT has become more advanced and offers applications with more data and capabilities.Real-time artificial intelligence can transform robotics while expanding the 6G coverage to the seas,and the sky can help marine, aviation, and even connected environments.Since 6G is much more efficient than 5G,it may even be low IoT devices.Consumption is charged through the network,which changes the economic deployment economy and helps network sustainability[129].
Reliable communication:5G,which provides high-speed,low-latency,and reliable communication services, has had a significant influence on our everyday lives.Nevertheless, meeting the expanding needs of IoT based on current techniques may be problematic in the future;thus,the concept of 6G networks was proposed to improve existing 5G networks and further enhance the development of application domains [130,131].It is stated that 5G, the most complicated communication network,would promote the growth of the information revolution in the next years.However, 5G network applications are still in their early stages, and it is critical to improving essential technologies to build intelligent applications in the future.Due to Fig.13,as more trade agreements are thoroughly investigated, the number of IoT devices is expected to rise.An ecosystem with many elements frequently needs greater speed, lower latency, and more reliable wireless communication services,resulting in a series of insoluble challenges that 5G networks may not address[132-134].While uRLLC offers excellent reliability and delay effectiveness,many links and bandwidth are still insufficient.As a result, 6G networks are designed to deliver high speed and throughput, low latency, and reliable communication services.Many devices might link them at any time and from any location.With the further expansion of the 6G service,6G will substantially influence telehealth,particularly for remote patient monitoring.Telehealth tracking is one of the rising IoT-based applications.It is especially crucial for the elderly,where reliable communication is critical for relaying monitoring systems data to the cloud over the internet [8,134,135].One significant design aim of 6G networks is to adapt to complicated, diverse conditions while offering a steady and reliable communication channel for particular applications such as vehicular communication.Mobile communication technology has advanced considerably in recent years.With the widespread commercialization of 5G networks,research into 6G networks is also underway.Vehicular communication may soon become a key landing scenario for 6G networks[134-136].People anticipate that 6G networks would provide better capacity,more reliable transmission, broader adaptability possibilities, and more extensive coverage regions for vehicle communication.Adapting to complicated,diverse settings and providing consumers with a robust and reliable transmission channel has become an essential aim of 6G network research[60,137,138].
Figure 12:Artificial intelligence in 6G-enabled IoT
Hardware complexity: 6G communication is expected to outperform 5G in developing services and applications [70,121].Until then, massive 6G-IoT devices will be linked to enable sophisticated smart services like manufacturing robots,drones,and self-driving automobiles[139-141].Hardware complexity is critical for the future 6G-enabled IoT device,as shown in Fig.14.As new radio access techniques emerge, hardware restrictions will become crucial in designing 6G-enabled IoT communication systems [100,142,143].The fact is that the hardware, techniques, and novel components needed to successfully satisfy the enormous efficiency requirements necessary for future 6G services and network operators have yet to be built,verified,or even available.Currently,there is a lack of a clear perspective of the cost-benefit trade-offs of machine learning and artificial intelligence assistance for 6G network and service operation optimization.This comprises potential hardware performance,operational efficacy, and the incalculable cost of data acquiring.Due to the numerous transmission and receiving concerns, the new short-communication range concept and the requirement for new hardware and technology is a set design,which presents several challenges.To allow connections over 90 GHz,performance as a result hardware components and robust technologies must be devised.A key issue for the future 6G hardware strategy is obtaining cost-effective and practical downsizing elements for sub-Terahertz transmitting and receiving[144,145].
Figure 13:Reliable communication in 6G-enabled IoT
Figure 14:Hardware complexity in 6G-enabled IoT
6 Conclusion
This paper presented a thorough understanding of 6G-enabled IoT and perspectives on unresolved issues.An SLR-based approach is presented in this paper.Therefore,by filtering on 190 publications published between 2018 and 2021, we selected and reviewed 36 articles about 6G-enabled IoT.The trend demonstrates that 6G-enabled IoT has emerged as an essential research topic.Furthermore,the statistical analysis of 6G-enabled IoT studies was conducted, and results with the highest repetition were identified.According to the studies conducted in this paper,we can say that the most important 6G-based technologies in the IoT will include wider bandwidth,improved massive MIMO,evolution in network topology, and high accuracy.It can also be argued that in IoT, new 6G service classes are being developed to improve 5G core service classes,such as eMBB,mURLLC,and mMTC will consider.Finally, we conducted extensive research on 6G-enabled IoT concepts for more than 100 authors and studies.However, due to the growing number of studies in this field, it is impossible to review all studies.
Funding Statement:The authors received no specific funding for this study.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computer Modeling In Engineering&Sciences2022年12期
Computer Modeling In Engineering&Sciences2022年12期
- Computer Modeling In Engineering&Sciences的其它文章
- A Comparison of Shale Gas Fracturing Based on Deep and Shallow Shale Reservoirs in the United States and China
- Prediction of Photosynthetic Carbon Assimilation Rate of Individual Rice Leaves under Changes in Light Environment Using BLSTM-Augmented LSTM
- Systematic Approach for Web Protection Runtime Tools’Effectiveness Analysis
- Structural Optimization of Metal and Polymer Ore Conveyor Belt Rollers
- Prerequisite Relations among Knowledge Units:A Case Study of Computer Science Domain
- Frenet Curve Couples in Three Dimensional Lie Groups
