Adaptor Reconfiguration Analysis in Web Services Composition
FAN Da-juan(范大娟),HUANG Zhi-qiu(黄志球),XIAO Fang-xiong(肖芳雄),PENG Huan-feng(彭焕峰)1,
1 School of Computer Engineering,Nanjing Institue of Technology,Nanjing 211167,China
2 College of Computer Science and Technology,Nanjing University of Aeronautics and Astronautics,Nanjing 210016,China
3 School of Software Engineering,Southern China University of Technology,Guangzhou 510006,China
Adaptor Reconfiguration Analysis in Web Services Composition
FAN Da-juan(范大娟)1,2*,HUANG Zhi-qiu(黄志球)2,XIAO Fang-xiong(肖芳雄)3,PENG Huan-feng(彭焕峰)1,2
1 School of Computer Engineering,Nanjing Institue of Technology,Nanjing 211167,China
2 College of Computer Science and Technology,Nanjing University of Aeronautics and Astronautics,Nanjing 210016,China
3 School of Software Engineering,Southern China University of Technology,Guangzhou 510006,China
Most of the existing approaches focus on identifying m ismatches and synthesizing adaptors at design-time or recently at run-time.However,few works have been proposed to support adaptor reconfiguration when services in the composition evolve due to changes in business needs.To address the deficiencies,the problem of adaptor reconfiguration is targeted in the context of service composition.Firstly,the formal models for describing services and adaptors are presented.Then,under this formalization,the notion of reconfiguration com pliance is proposed to determ ine the validity of an adaptor instance with respect to its history executions and future executions.Based on the notion,the algorithm for reconfiguration analysis of adaptors is presented and it can be used for determ ining them igratability of an adaptor instance and the corresponding target state of reconfiguration if m igratable.Finally,feasibility of the proposed approach is validated on a realistic case study.The proposed approach im proves the flexibility of adaptor-based service composition by equipping adaptors with reconfiguration capabilities.
web services;adaptor;reconfiguration;trace compliance
Introduction
In service-oriented architectures[1],Web services are loosely coupled and black-box software components that are published,discovered,and invoked across theweb through their interfaces.The composition of Web services wiring together multiple Web services often fails because services developed by different third-parties are offered through incompatible interfaces,including both signature and behavioral interfaces[2-3].The typical approach to resolve incompatibilities in such a heterogeneous setting is through developing adaptors thatmediates the interactions among services with incompatible interfaces so that interoperability at signature and behavioral levels can occur[4].A service composition with the aid of an adaptor can be called an adaptor-based service composition.
In the last few years,mostadaptation proposals focused on solving mismatches between software components or recently Web services.In Ref.[5],the authors first defined the minimum receive distance and the m inimum send distance.Then,they proposed a m inimal adaptor construction algorithm for two incompatible services based on the two kinds of distances.Theminimaladaptor only tackled themessageswhich caused incompatibilities and could therefore effectively reduce communication overhead between incompatible services.In Ref.[6],the authors defined several adaptation templates based on BPEL codes.For each adaptation template there corresponds a m ismatch pattern input.Developers can utilize adaptation templates to generate BPEL codes of adaptors according to themismatches between twoWeb services.In Ref.[7],the authors identified m ismatches at signature and behavioral levels by using schema matching and generated a m ismatch tree to help developers in generating adaptor specification in presence of deadlock.The above approaches assume that the services to be composed have been fixed in advance and only focus on m ismatch analysis and adaptor generation at design-time.
Due to the dynamic characteristics in Web services environments,servicesmay evolve at run-time for adapting to changes in business needs[89].Thus,several run-time adaptation approaches have recently been presented to complement the approaches for design-time adaptation[10].In Ref.[11],each mismatch pattern corresponded to an adaptation logic.The authors leveraged aspect-oriented programming paradigm and weaved the adaptation logics as adaptation aspects into the runtime service instances instead of introducing an independent adaptor.In Ref.[12],the authors also classified incompatibilities into m ismatch patterns and designed the corresponding adaptations to solve each kind of incompatibility.They relied on an event-based technology and would trigger a specific adaptation action when catching an incompatibility event.In Ref.[13],the authors proposed a runtime adaptation approach by exploring a service adaptation machine.The machine acted as an adaptor between incompatible services at runtime,by selecting and chaining mapping rules to resolve mismatches as they arised.Besides,some researchers focused on how to re-generate or re-adjust the adaptor while dynamically evolving services.In Ref.[14],they presented an example in which possible changes were successively applied and sketched some solutions to adaptor readjustment issues on this example.In Ref.[15],the authors presented the incremental adaptation supporting evolving component-based systems.The incremental integration process could be viewed as several re-generations.To do so,they proposed some techniques to deal with two cases:(1) generated an adaptor for the added component,(2)suppressed the adaptor for the removed component and upgraded all the adaptors interacting with the suppressed one.However,no solution is proposed in these approaches to equip the adaptor with reconfiguration capabilities when service evolution occurs in the running adaptor-based service composition.
When some service evolves in the execution process of a certain adaptor-based service composition,the original adaptor will be replaced by a new one for the evolved service accordingly.Thus,automated techniques are needed in order to reconfigure adaptors without stopping their execution.The adaptors reconfiguration refers to how to determ ine whether a certain running adaptor instance ismigratable from the original adaptor-based service composition to the new one,in which both a service and the adaptor are evolved into a new service and adaptor.To address the deficiencies,in this paper the adaptor reconfiguration problem is targeted in the context of a service composition involving incompatible services for which an adaptor is executed.Firstly,formal models that describe services and the adaptor are presented.Then,with thisframework the notion of reconfiguration compliance(combining the notion of backward trace compliance and the notion of forward trace compliance)is proposed and then utilized to decide if the reconfiguration scenario that allows the running adaptor instancemigrates from the former adaptor-based service composition to the new one is correct.The proposed approach equips adaptors with reconfiguration capabilities to ensure the flexibility of adaptor-based service composition at run-time.
1 Prelim inaries
1.1 Services
Services are often described by signature and behavior interfaces.They may include non-functional(i.e.,Qos) apsect.In the paper,wemainly focus on the functional aspect of services described by signature and behavior interfaces.The signature declares both the operations that the service provides,and those it requires from other services.Each operation in WSDL specifications of services receives a message(oneway),receives and sends amessage(request-response),sends and receives amessage(solicit-response),or sends amessage (notification).Thus,a signature is often represented by a set of actions,relative to the emission and reception of messages corresponding to operation calls.Moreover,the behavior represents the order in which the operations in the signature are performed.
A service is modeled by means of a finite state machine (FSM)model.The reason for using FSM model is that this formalism is intuitive,simple,and fairly easy to understand for users.
Definition 1(FSM)An FSM model is a quintuple M=(S,L,T,I,F),where S is a setof states,L isa setof labels,T⊆S×L×S is a setof transitions,I∈S is the initial state,and F⊆S is a setof final states.The transition t=(s,l,s')can also be denoted as
In the FSMs,transtions are labelled with operations(i.e.,actions in the set L that indicate messages to be sent or received).When amessage is sentor received by a service,the corresponding transition is fired.Actions in the FSMs represent the signature interfaces of services,and transitions in the FSMs depict the behavior interfacesof services.Thus,using the FSMs is a simple yeteffective approach tomodel service signature and behavior interfaces.
Definition 2(Trace)Let M=(S,L,T,I,F)be an FSM model.A trace of M is aσ∈(L*∪{ε})defined in such a way thatσ=ε∨(∃s0,s1,…,sN∈S:σ=l1l2…lN∧s0whereεdenotes the empty trace.The set of traces of M is denoted as Tr(M).A traceσwhich is the concatenation of two tracesσ1andσ2isw ritten asσ=σ1σ2.Definition 3(Backward trace and forward trace)Let M be an FSM model andσa trace of M.The traceσis a backward trace of M if and only if∃s0,s1,…,sN∈S,s0=I:σ=The set of backward traces of M is denoted as BTr(M).The traceσis a forward trace of M if and only if∃s0,s1,…,sN∈S,sN∈F:σ=The setof forward traces of M is denoted as FTr(M).
The traces of an FSM model are the sequences of labels that can be observed according to its transitions.Backward and forward traces are the special cases which start from its initial state and end at its final state respectively.The symbols EN(σ) and ST(σ)are used to respectively denote the stateswhich the traceσstarts from and ends at.
Based on the above definitions,we will represent services just by FSM models that describe their signature and behavior interfaces.
Definition 4(Service)A service can be described by an FSM model c=(S,L,T,I,F),where S is a setof service states,I∈S is the initial state,F⊆S is the set of final states,L⊆{!,is a setof service actions,and T⊆S×L×S is a set of transitions triggered by service actions.
1.2 M essagemappings and adaptors
While composing existing services,they do not always fit one another,and m ismatches arise because of differentmessage names,a message without counterpart or with several ones in the partner service,etc.The presence of mismatch results in a deadlocking execution for these incompatible services and thus needs adaptors to reconcile incompatibilites.Adaptors are often automatically generated from an abstract adaptation description[16],called message mapping,expressing the correspondences betweenmessagesand indicating how m ismatch situations can be solved.Themessagemapping is composed of a finite set ofmapping rules and eachmapping rule in itgives a correspondence between receive actions and send actions involved in the adaptation.
From a set of incompatible services and a message mapping,an adaptor is automatically generated according to adaptor generation algorithms[17- 18]to orchestrate deadlock-free interactions among incompatible services.
Definition 6(Adaptor)Let a setof services be ci=(Si,Li,Ti,Ii,Fi),i∈{1,2,…,N}.The adaptor can be described by an FSM model A=(S,L,T,I,F),where
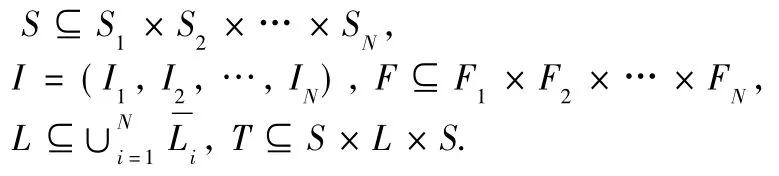
The states in the adaptor correspond to combinations of states of N services,i.e.,the adaptor is in its state(s1,s2,…,sN),if and only if each service i is in its state si.The formula Lmeans that every action in the adaptor has the corresponding complementary action in a certain service.Specially,for each action?m in the adaptor,there exists the send action!m in a certain service,and for each action!m in the adaptor,there also exists the receive action?m in a certain service.Therefore,the tracereflects the interaction of N services involving in the adaptor-based service composition,whereσis the trace of the adaptor.
The actions of each of the N services performing incan be derived by projecting the traceover the action set Li.
Definition 7(Projection)Letσbe a trace,the projection of σover an action set L(w rittenσ↓L)is defined as:
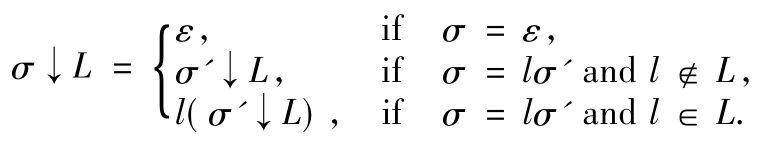
Analogously,an operator over a trace that hides the particular actions is defined,leaving the rest of the actions in the trace.
Definition 8(Hiding)Letσbe a trace,and the hiding ofσ over an action set L(w rittenσL)is defined as:
(187)瓦鳞苔 Trocholejeunea sandojcensis(Gottsche)Mizt.马俊改(2006)
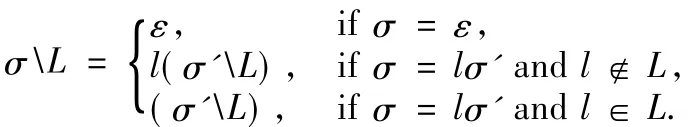
2 Reconfiguration Analysis of Adaptors
2.1 Problem of adaptor reconfiguration
When the evolution of one or more services which participate in an adaptor-based service composition occurs,it will lead to modification of the old adaptor into a new adaptor by utilizing the adaptor generation algorithm.Therefore,such a service evolution raises a critical issue is how to handle instances running under the old adaptor when it has been changed.
Simple solutions,such as aborting them or allow ing them to continue to run according to the old adaptor are inapplicable formany reasons(e.g.,the loss of work already done or the consequence of error execution).How to reconfiguration of adaptor,i.e.,dynam ically m igrate ongoing instances that have already executed under old adaptor to the new adaptor is a critical issue,especially for long running business processes.
In the field of traditional workflow,Ref.[19]proposed inheritance-preserving transformation rules for instance migration.The transformation rules can be used to restrict changes in workflow process definitions and ensurem igration of workflow instances without introduing errors.The approach in Ref.[20]introduced the concept of change region(i.e.,the part of the workflow that was affected by changes).If workflow instances are in the change region,the migration of them is postponed until they exit the region.For the cases in which workflows before and after evolution do not meet the inheritance relationship or workfow instances are in the change region,the instances under orginal workflow are considered to be non-migrated in Refs.[19- 20].In the web services area,Ref.[21]aimed at dynam ic management for adaptor-based service composition,and proposed the execution model of adaptor to realize the dynamic adjustment of adaptors at runtime.The approachmainly focused on correctness check which was suitable for themediator instance aftermigration and did not consider the aspect on determining whether an adaptor instance wasmigratable.
In order to determine whether an instance can be correctly migrated to the new adaptor,two notions of reconfiguration compliance are proposed in the paper,corresponding to different requirements that may impose on the reconfiguration process: backward trace compliance and forward trace compliance.
In this paper,for simplicity,we just consider simple scenarios where only one service in a certain adaptor-based service composition evolves at run-time.This is nota lim itation becausemultiple services evolution can be viewed as one service evolution happen several times.
Service evolution can take place anytime in the execution,so the problem of reconfiguration includes two aspects:(1)for a given source reconfiguration statewhere the evolution occurs,analyzing if the instance under the old adaptor ism igratable or non-migratable;(2)whenever the instance ismigratable in the given source reconfiguration state,it should also be defined the target reconfiguration state under the new adaptor from which the instance will resume.
A source reconfiguration state defines when a reconfiguration is allowed.Moreover,a target reconfiguration state indicates that the starting state in the new adaptor to resume the execution.We will show how to determ ine whether the instance at a given source reconfiguration state ismigratable or not and how to obtain the target reconfiguration state if migratable.
Let C and C'be a set of services before and after evolution,M and M'be themessagemappings for the services in C and in C',respectively.Assum ing thata certain service ckevolved into another service c'ksuch that∃ck∈C,∃c'k∈C': ck≠c'k∧C/{ck}=C'/{c'k},the adaptor AC,Mgenerated according to the message mapping M for services in C is replaced by the adaptor AC',M'generated according to M'for services in C',where k∈{1,2,…,N}.
2.2 Reconfiguration analysis based on the trace com pliance
The notion of backward trace compliancemeans that after migration to the new adaptor,the backward trace of an instance (i.e.,the action sequence performed by the instance so far) must be compliance in the context of the new adaptor.This reconfiguration compliance is aware of the past interactions,up to the time of evolution,corresponding to a valid interaction as defined in the new version of adaptor.
We assume that the sequence of actions an instance has been performed under the old adaptor AC,Mis the backward trace σC,M.For each service cisuch that ci∈C∩C',i.e.,ci≠ck,ci≠c'kwhere i∈{1,2,…,k-1,k+1,…,N},it is not affected by the reconfiguration from the old adaptor AC,Mto the new adaptor AC',M'since it remains unchanged after evolution.If service ciis not obliged to abort nor rollback its current execution andon running under the new adaptor,the backward tracerepresenting the sequence of actions already performed by the service ciis valid in the new adaptor AC',M',where Lidenotes the action set of service ci.
Therefore,for reconfiguration compliance under the notion of backward trace compliance,we have to ensureeach service cisuch that ci∈C∩C',the backward tracealready performed by service ciis also contained in the backward traces of the new adaptor AC',M'.
Let us formalize this notion of backward trace compliance with the follow ing definition.
Definition 9(Backward trace compliance)LetσC,Mbe a backward trace executed by an instance under an adaptor AC,M.The adaptor AC',M'is the backward trace compliance to the adaptor AC,MgivenσC,Miff there exists a backward traceσC',M'in the tracessuch that∀ci∈C∩C',and we have thatwhere i∈{1,2,…,k- 1,k+1,…,N}.
Let s be the state of the adaptor AC,Mafter performing the backward traceσC,Mand it is called the source reconfiguration state where the instance under the adaptor AC,Mneeds to be migrated to the new adaptor AC',M'due to service evolution.For the traceσC,M,assumeσC',M'is the backward trace of the adaptor AC',M'satisfyingDefinition 9.Let s'be the state of the adaptor AC',M'after perform ing the backward traceσC',M',and it is exactly the target reconfiguration state from which the instance will resume under the new adaptor AC',M'.
Therefore,based onDefinition 9,we can not only determine if the instance under the old adaptor ismigratable or not for a given source reconfiguration state where the evolution occurs,but also define the corresponding target reconfiguration state ifmigratable.
The backward traceσC',M'satisfyingDefinition 9can alsobe used for initializingservice c'k.As the actions of the services are disjoint,gives us the trace for initializing the service c'k.
Definition9establishes the conditions for the adaptor AC',M'being the backward trace compliance to the adaptor AC,MgivenσC,M.However,it does not give us how to find the backward traceσC',M'that satisfies the conditions ofDefinition 9.
The algorithm below gives us a way to compute the backward traceσC',M'for the new adaptor AC',M'that fulfills the conditions ofDefinition9.
Algorithm1The algorithm for computing the backward trace σC',M'that fulfills the conditions ofDefinition9.
Input:the new service c'k=(S'k,L'k,T'k,I'k,F'k),the new adaptor AC',M'=(S',L',T',I',F')and the backward traceσC,Mof the old adaptor AC,Mperformed by the instance.
Output:the backward traceσC',M'.
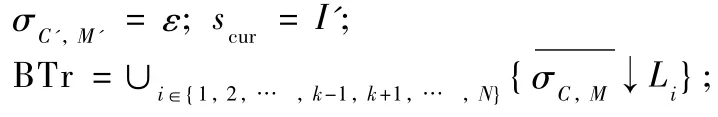
while(∃σi∈BTr∶σi≠ε)do
σC',M'=
elseif(then
σc',m'=
else
return(ε);
endif
endwhile
return(σC',M').
According toDefinition9,the backward traceσC',M'to be computed is the interleaving of the backward traces in BTr already performed by services in the set C∩C'under the old adaptor AC,Mand the backward trace of the new service c'k.Hence,the algorithm tries to make new adaptor AC',M'advance w ith the complementary actionfrom a certain traceσin BTrj(initiallyw ith its first action l1.If this is not possible,it checks if an complementary action in L'kcan make the adaptor AC',M'advance.If neither of the two conditions above holds,the algorithm returns an empty traceεwhich indicates the backward trace that fulfills the conditions ofDefinition9does not exist.The algorithm stops when all traces in BTr are empty(success)and it returns the backward traceσC',M'.According to the conditions of the if statement,the time complexity of the while loop body is O (N).Supposing that the transition numbers of the traceσC,Mis |T|,we can conclude that the execution times of thewhile loop body is|T|.Hence the time complexity ofAlgorithm1is deduced to be O(N|T|).
Backward trace compliance focuses on the backward trace (also called history)of the instance.In such a way,the services not involved in the evolution are able to continue working on from their current states.However,backward trace compliance says nothing about forward trace(also called future)of the instance to bemigrated.Therefore,wewill deals w ith the future actions of an instance by introducing the notion of forward trace compliance.
The notion of forward trace compliance refers to the ability for all the services unchanged to continue interacting under the new adaptor as itwould have done under the old version of the adaptor.
Let us consider again the serviceswhich remain unchanged after evolution(i.e.,services in the setof C∩C').Unlike the notion of backward trace compliance presented above,the future actions which can be performed by these services are focused on.
Again,we assume that the sequence of actions an instance has been performed under the old adaptor AC,Mis the backward traceσC,M.In order to determine if the adaptor AC',M'is the forward trace compliance to the adaptor AC,Mgiven the trace σC,M,we shall check if any possible forward trace that continuesσC,Mis possible in the forward traces of the adaptor AC',M',by hiding the traces over actions performed by the services ckand c'k,where services ckand c'kare the original and new versions of the service involved in the evolution.Let us formalize the notion of forward trace compliance by the follow ing definition.
Definition10(Forwardtracecompliance)LetσC,Mbe a backward trace executed by an instance under the old adaptor AC,M.The adaptor AC',M'is the forward trace compliance to the adaptor AC,MgivenσC,Miff there exists a backward traceσC',M'in the traces of the adaptor AC',M'such that∀∈ FTr(AC,M):∃∈FTr(AC',M'):= EN(σC,M))∧(ST(=EN(σC',M'))∧(Lk=,where L and L'are the sets of actions for serviceskkckand c'k,respectively.
Based onDefinition10,the target reconfiguration state under the notion of forward trace compliance can also be decided.Assume there exists a traceσC',M'which satisfies the conditions ofDefinition10.Let s be the state of the adaptor AC,Mafter performingσC,Mand s'the state of the adaptor AC',M'after performingσC',M'.This state s'is the target reconfiguration state to which the instance is allowed to reconfigure from the source reconfiguration state s.
Similar to the case under the notion of the backward trace compliance,the tracecan be used for initializing the new service c'k.
These two kinds of reconfiguration compliance are important in managing the adaptor reconfiguration.Backward trace compliance is required if we need the past interaction of the instance under the old adaptor to be a valid interaction under the new adaptor to which it is migrated,while forward trace compliance is necessary in order to guarantee the future interaction of the instance under the old adaptor to be valid in the context of the new version of the adaptor.
Definition11(Correctreconfiguration)The reconfiguration from adaptor AC,Mto adaptor AC',M'is correct given the backward trace executed by an instance under the old adaptor AC,Miff there exists a backward traceσC',M'in the traces of the adaptor AC',M'satisfying the two notions of reconfiguration compliance,i.e.,the backward trace compliance inDefinition9 and the forward trace compliance inDefinition10.
Therefore,in order to check the reconfiguration from adaptor AC,Mto adaptor AC',M'is correct,we need first find whether there is a backward traceσC',M'of adaptor AC',M'making the condition ofDefinition9hold.In that case,wewill then check if that trace also satisfies the condition ofDefinition 10.If some reconfiguration scenario is incorrect for a given source state,we will rollback or resume the execution of the instance into a state from which it can be correctly reconfigured.
3 Case Study
This section presents an online shopping case study to illustrate the proposed approach.There are three services: Client service(w ritten S1),Store_A service(w ritten S2),andStore_B service(w ritten S3).The Client service plays the role of buyer while the two services Store_A and Store_B play the role of seller.
The Client service can buy goods and query the order as shown in Fig.1(a).The two services Store_A and Store_B are depicted in Figs.1(b)and(c),respectively.Store_A can only sell goods,while Store_B can sell goods and provide order query.
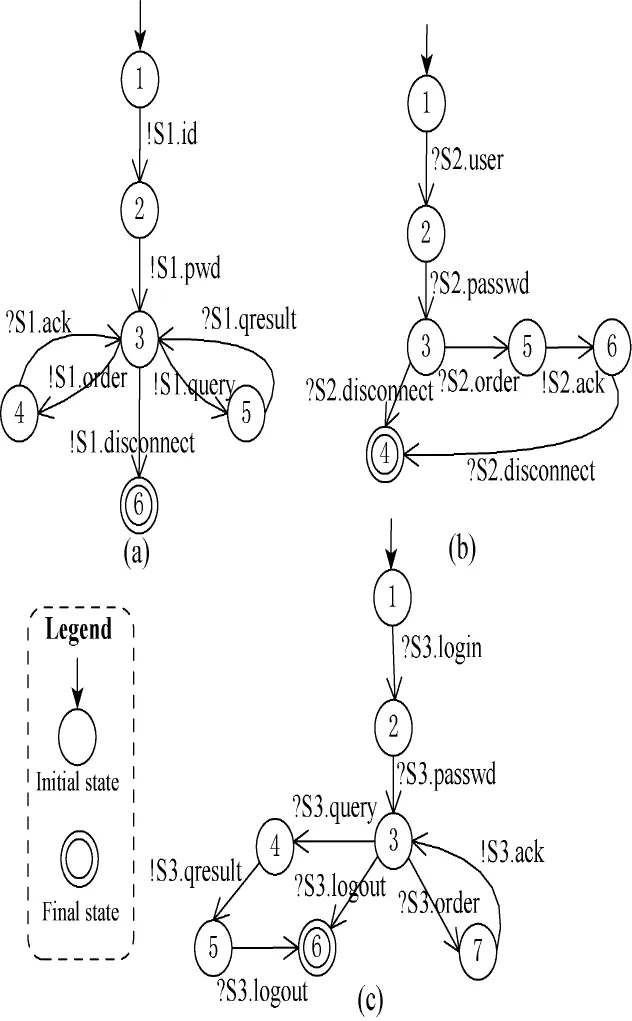
Fig.1 Services in the online shopping example
Initially,the Client service interactswith Store_A service.During the period that a client service interacts with Store_A service,Store_A service evolves into Store_B service.Several changes take place in the new service Store_B.For instance,operations query and qresult are added and operations login and logout are renamed in the signature of Store_B service.Possible modifications of the behavior aremore important.For instance,the addition of several interactions(three new successive transitions(s3,?query,s4),(s4,!qresult,s5),(s5,? logout,s6))are modifications of pieces of behavior in the model of Store_B service.
Let C be the setof services composed of Client service and Store_A service,and C'be the set of services composed of Client service and Store_B service.Themessagemapping M for the services in C is as follows:!id→?user,!pwd→? passwd.
The message mapping M'for the services in C'is as follows:!id→?login,!pwd→?passwd and!disconnect→?logout.By utilizing the existing adaptation approaches,the adaptor AC,Mfor the services in C and the adaptor AC',M'for the services in C'are automatically generated respectively based on themessagemappings M and M',(see adaptors AC,Mand AC',M'in Figs.2(a)and(b)).
For instance,let us suppose that the backward trace performed so far by an instance under the adaptor AC,Mis:σC,M=?S1.id!S2.user?S1.pwd!S2.passwd.
Hence,the trace performed by the Client service is:=!S1.id!S1.pwd.
In order to keep the Client service unaware of the reconfiguration,itmustnotabort its ongoing execution.Only if the traceis valid in the new adaptor AC',M',Client service could continue its execution as if it has been interacting with Store_B service from the very beginning.

Fig.2 Adaptors AC,Mand AC',M'in the onlineshopping example
Using the proposedAlgorithm 1,the traceσC',M'=?S1.id!S3.login?S1.pwd can be obtained.
According to the traceσC',M',the formulaS1.id!S1.pwd holds and this indicates the traceperformed by the Client service is valid in the new adaptor AC',M'.The traceσC',M'makes the new adaptor AC',M'be backward trace compliance to the original adaptor AC,MgivenσC,Mbased onDefinition 9.
In the follow ing,we will check if that traceσC',M'also satisfies the conditions ofDefinition 10.
The forward traces continuing the backward traceσC,Mare:
and
So we can decide that the reconfiguration from adaptor AC,Mto adaptor AC',M'is correct given the backward traceσC,Min the example.Furthermore,for the source reconfiguration state s5in the adaptor AC,M,the target reconfiguration state is s4which is the state of the adaptor AC',M'after performingσC',M'.
4 Conclusions
This paper has presented a novel approach that supports adaptor reconfiguration when services in the composition have evolved due to changes in business needs.Firstly,formal models that describe services and the adaptor are presented.Then,with this framework,the notion of backward trace compliance and the notion of forward trace compliance are proposed respectively.The former focuses on the history actions of the instance,while the latter deals with the future actions of an instance.Based on the two notions of reconfiguration compliance,the algorithm is given to decide if the reconfiguration scenario that allow the running instancem igrate from the former adaptor-based service composition to the new one is correct.If it is correct for a given source reconfiguration state,it also defines the target reconfiguration state from which the instance will resume.
The reconfiguration problem presented in this paper assumes the adaptor is a centralized one.So in the future,we will plan to deal with the reconfiguration problem when the adaptor is distributed across different locations in a distributed setting.Moreover,in the case where a service is evolved into a more restricted functionality one,preserving certain temporal properties may be sufficient for the reconfiguration of the adaptor.Hence,the approach to deal with these situations will be another perspective of our future work.
[1]Wei Y,Blake M B.Service-Oriented Computing and Cloud Computing:Challenges and Opportunities[J].IEEE Internet Computing,2010,14(6):72-75.
[2]Li X T,Fan Y S,Sheng Q Z,et al.A Petri Net Approach to Analyzing Behavioral Compatibility and Sim ilarity ofWeb Service[J].IEEE Transactions on Systems,Man,and Cybernetics—Part A:Systems and Humans,2011,41(3):510-521.
[3]Durána F,OuederniM,Salaün G.A Generic Framework for nprotocol Compatibility Checking[J].Science of Computer Programming,2012,77(7/8):870-886.
[4]Eslam ichalandar M,Barkaoui K,Motahari-Nezhad H R.Service Composition Adaptation:an Overview[C].Proceedings of the 2nd InternationalWorkshop on Advanced Information Systems for Enterprises(IWAISE'12),Constantine,Algeria,2012:20-27.
[5]Kumar A,Shan Z.Algorithms Based on Pattern Analysis for Verification and Adapter Creation for Business Process Composition[J].Lecture Notes in Computer Science,2008,5331:120-138.
[6]Benatallah B,Casati F,Grigori D,et al.Developing Adapters forWeb Services Integration[C].Proceedings of the International Conference on Advanced Information Systems Engineering (CAiSE'05),Porto,Portugal,2005:415-429.
[7]Motahari-Nezhad H R,Benatallah B,Martens A,et al.Semiautomated Adaptation of Service Interactions[C].Proceedings of the 16th International Conference on World W ide Web(WWW '07),Banff,Canada,2007:993-1002.
[8]Andrikopoulos V,Benbernou S,Papazoglou M P.Managing the Evolution of Service Specifications[C].Proceedings of the 20th International Conference Advanced Information Systems Engineering(CAiSE'08),Montpellier,France,2008:359-374.
[9]Wang Y.A Survey of Change Management in Service-Based Environments[J].Service Oriented Computing and Applications,2013,7(4):259-273.
[10]La H J,Kim S D.Static and Dynam ic Adaptations for Service-Based Systems[J].Information and Software Technology,2011,53(12):1275-1296.
[11]Kongdenfha W,Motahari-Nezhad H R,Benatallah B,et al.M ismatch Patterns and Adaptation Aspects:a Foundation for Rapid Development of Web Service Adapter[J].IEEE Transactions on Services Computing,2009,2(2):94-107.
[12]Taher Y,Ait-Bachir A,Fauvet M C,et al.Diagnosing Incompatibilities in Web Service Interactions for Automatic Generation of Adapters[C].Proceedings of the 23rd International Conference on Advanced Networking and Applications (AINA'09),Bradford,UK,2009:652-659.
[13]Wang K,Dumas M,Ouyang C,et al.The Service Adaptation Machine[C].Proceedings of the 6th European Conference on Web Services(ECOWS'08),Dublin,Ireland,2008:145-154.
[14]Poizat P,Salaün G,Tivoli M.On Dynam ic Reconfiguration of Behavioural Adaptation[C].Proceedings of the3rd International Workshop on Coordination and Adaptation Techniques for Software Entities(WCAT'06),Nantes,France,2006:61-69.
[15]Poizat P,Salaün G,TivoliM.An Adaptation-Based Approach to Incrementally Build Component Systems[J].Electronic Notes in Theoretical Computer Science(ENTCS)Series,2007,182:39-55.
[16]Cámara J,Salaün G,Canal C,etal.Interactive Specification and Verification of Behavioral Adaptation Contracts[J].Information and Software Technology,2012,54(7):701-723.
[17]Cámara J,Martín JA,Salaün G,etal.A Case Study in Model-Based Adaptation of Web Services[C].Proceedings of the 4th International Symposium on Leveraging Applications (ISoLA'10),Heraklion,Greece,2010:112-126.
[18]Mateescu R,Poizat P,Salaün G.Adaptation of Service Protocols Using Process Algebra and On-the-Fly Reduction Techniques[J].IEEE Transactions Software Engineering,2012,38(4):755-777.
[19]van der Aalst W M P,Basten T.Inheritance of Workflows:an Approach to Tackling Problems Related to Change[J].Theoretical Computer Science,2002,270(1):125-203.
[20]van der AalstW M P.Exterm inating the Dynam ic Change Bug:a Concrete Approach to SupportWorkflow Change[J].Information Systems Frontiers,2001,3(3):297-317.
[21]Qiao X Q,Chen W,Wei J.Implementing Dynamic Management for Mediated Service Interactions[C].Proceedings of the 9th International Conference on Services Computing(SCC'12),Hawaii,USA,2012:234-241.
TP311
A
1672-5220(2015)04-0648-06
date:2014-02-13
s:National Natural Science Foundationsof China(Nos.61272083,61262002,61170043);China Postdoctoral Science Foundation (Nos.20110491411,2014M 562177);The Science Foundations of Nanjing Institute of Technology,China(Nos.QKJB201304,YKJ201420)
*Correspondence should be addressed to FAN Da-juan,E-mail:fanbingjie523@126.com
 Journal of Donghua University(English Edition)2015年4期
Journal of Donghua University(English Edition)2015年4期
- Journal of Donghua University(English Edition)的其它文章
- Numerical Reality Method of the M icroburst Model
- Corporate Governance,Government Regulation and Bank Stability
- Cracking Patterns of Shear Walls in Reinforced Concrete Structure due to Strong Earthquake Based on Mohr-Coulomb Criterion
- Cooperative Compressive Spectrum Sensing in Cognitive Underwater Acoustic Communication Networks
- Numerical Simulation of Gas-Solid Two-Phase Flow in Reverse Blow ing Pickup Mouth
- Fuzzy Model Free Adaptive Control for Rotor Blade Full-Scale Static Testing
